Businesses lose millions every year from data leaks, with IBM reporting an average breach cost of $4.88M in 2024. The real question for IT leaders isn’t just “What is DLP?” but “Why is it essential today?” Without clarity, data protection risks being sidelined as a technical detail instead of a strategic priority. This guide unpacks DLP in practice—its role, use cases, challenges, and solutions—showing why it’s the first step toward lasting defense against data breaches.

What is DLP (Data Loss Prevention)?
Think of DLP as your company’s immune system. It constantly scans, detects, and stops sensitive information from leaking—whether that data is at rest on servers, in motion across the network, or in use on an employee’s laptop. By combining policies, technology, and automation, DLP ensures that confidential files—like payroll spreadsheets, customer records, or design blueprints—don’t end up in the wrong hands.
In today’s data-driven economy, information is more valuable than office real estate or hardware. A single leaked HR payroll file with 500 employee records could cost over $70,000—and that’s before fines or reputational damage kick in. Scale that to a server breach, and losses can climb into the six- or seven-figure range. That’s why DLP isn’t just an “IT tool.” For business leaders, it’s the difference between treating data protection as a line item in the budget—or as a shield for the entire enterprise.
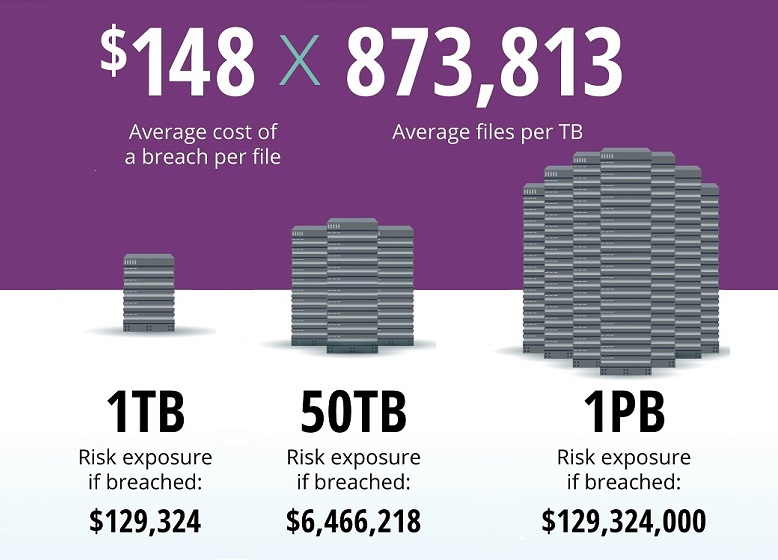
Source: Egnyte / The Hard Cost of Data Breaches. Accessed Sep 4, 2025.
How DLP Works in Practice
Wondering “How does DLP actually work?” Think of your company’s data as mail passing through a busy sorting center. Every file, email, or message is like an envelope—and DLP inspects each one to make sure nothing sensitive slips through.
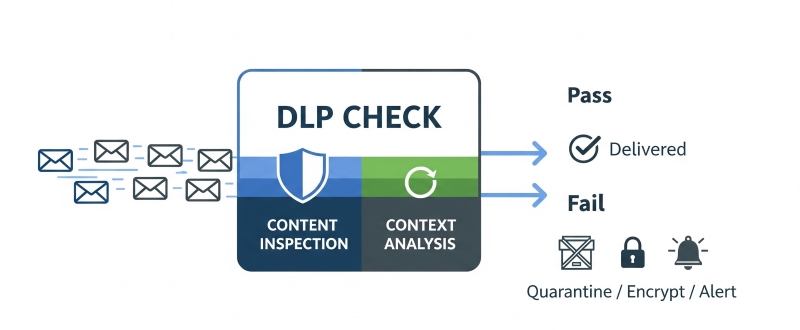
- Protected content detected: For example, a customer's social security number in a file.
- Unauthorized recipient: The data is being sent to someone not approved.
Behind the scenes, DLP combines two powerful techniques:
- Content Inspection – Scans files, emails, and messages for keywords, patterns, or file types that are considered sensitive.
- Context Analysis – Looks at who is sending the data, who the recipient is, and how the data is being transmitted.
Example:If an employee tries to email a spreadsheet containing credit card numbers to a personal account, DLP solution can automatically quarantine or encrypt the message before it leaves the company.
📑 With DLP, your data-handling rules are enforced automatically. It knows what’s sensitive, checks every transfer against policy, and stops any actions that violate your rules—without you lifting a finger.
What are DLP's Common Use Cases?
Effective DLP strategies are versatile, helping organizations tackle a wide range of security and compliance challenges. Here are the most common scenarios where DLP proves invaluable:

Regulatory Compliance (GDPR, CCPA, HIPAA)
Regulations like the EU’s GDPR, California’s CCPA, and HIPAA set strict rules on how personal data must be collected, stored, and processed. DLP systems help organizations stay compliant by discovering and classifying sensitive data such as Personally Identifiable Information (PII) and Protected Health Information (PHI), monitoring its movement, and preventing unauthorized transfers—avoiding costly fines and reputational damage.
Prevent Insider Threats
Not all threats come from outside. Many breaches originate internally, whether from a malicious employee or an accidental mistake. DLP monitors user behavior to detect anomalies, such as copying large volumes of sensitive files to a personal USB drive or emailing confidential reports externally, stopping potential leaks before they escalate.
Protect Intellectual Property (IP)
For most companies, IP is their most valuable asset—trade secrets, proprietary code, product designs, and research data. DLP protects this information with content-aware detection, blocking attempts to exfiltrate critical IP through email, cloud storage, or messaging apps, keeping it safely within the organization.
Secure Cloud Data and Shadow IT
The rise of cloud services introduces new risks. Employees often use unsanctioned apps (“Shadow IT”) to store or share company data, creating blind spots. Cloud DLP extends protection to these environments, monitoring data transfers across platforms like Microsoft 365, Google Workspace, and AWS, ensuring sensitive information stays secure and compliant.
Enhance Data Visibility
A common challenge is simply knowing where sensitive data resides and how it’s being used. DLP provides a comprehensive view of data flows—from endpoints to the network and cloud—allowing security teams to spot vulnerabilities, track usage patterns, and refine policies for maximum protection.
👉 In short, DLP acts as a shield: ensuring compliance with strict regulations, stopping insider threats, protecting intellectual property, securing cloud and Shadow IT environments, and providing visibility across the entire data landscape. It’s not just a security tool—it’s a strategic enabler for safer, smarter businesses.
Challenges and Pain Points in DLP Implementation
While the benefits of DLP are clear, implementing it comes with real-world challenges. Many enterprises face common hurdles that can undermine the effectiveness of their DLP program.
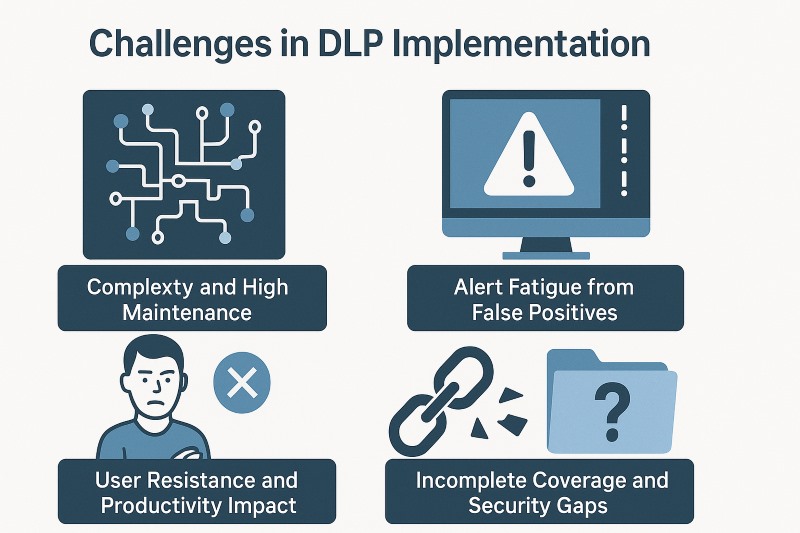
Complexity and High Maintenance
DLP systems can be intricate to deploy and manage. Configuring granular policies, adapting to changing business processes, and maintaining the infrastructure requires significant expertise and resources. Many organizations struggle with the ongoing administration needed to keep DLP solutions effective.
Alert Fatigue from False Positives
Poorly tuned DLP systems can generate a flood of alerts, many of which are false positives triggered by legitimate activities. This "alert fatigue" can overwhelm security teams, causing them to miss genuine threats. Studies show that over half of DLP alerts can be false positives.
User Resistance and Productivity Impact
If DLP policies are too restrictive, they can disrupt normal workflows and frustrate employees. For example, blocking a legitimate email to a client may hinder productivity. Employees may seek workarounds, which ultimately defeat the purpose of the DLP solution.
Incomplete Coverage and Security Gaps
Data exists everywhere—in laptops, emails, cloud apps, and mobile devices. Many traditional DLP solutions fail to provide consistent, comprehensive coverage, creating dangerous blind spots. Policies protecting the corporate network are useless if employees can copy data to a USB drive or personal cloud account.
Difficulty in Defining and Locating Sensitive Data
The first step in any DLP strategy is knowing what data is sensitive and where it resides. While PII is easier to spot, critical data like financial plans or unique IP may be scattered across unstructured files, making discovery and classification a major challenge.
👉 Building a robust DLP program is challenging. Enterprises must navigate complexity, alert fatigue, user resistance, coverage gaps, and the difficulty of accurately identifying sensitive data. Addressing these obstacles is key to effective deployment.
What is DLP: Actionable Solutions and Best Practices
Overcoming DLP challenges requires a strategic, business-aligned approach. By following best practices, organizations can build a DLP program that is both effective and sustainable.

Start with Data Discovery and Classification
Before protecting your data, you need to know what you have and where it resides. Conduct a thorough inventory to identify and classify sensitive data. Use automated tools to scan endpoints, servers, and cloud repositories for PII, PHI, financial data, and IP. Classification should form the foundation of your policies.
Develop a Phased, Risk-Based Policy Rollout
Don’t try to secure everything at once. Focus on the most critical data and highest-risk scenarios. Start with a monitor-only policy to gather baseline data and fine-tune rules before moving to active blocking, reducing user friction and false positives.
Align with Business Processes and Educate Users
Work with business units to understand workflows and ensure DLP policies support, not hinder objectives. Educate employees on data security importance and train them on policies. Understanding the "why" fosters user cooperation rather than resistance.
Implement Strong Access Controls
Enforce the principle of least privilege (PoLP), granting access only to data absolutely needed for the job. This minimizes the potential attack surface for both insider and external threats.
Encrypt Data Everywhere
Encryption is a critical defense layer. Ensure sensitive data is encrypted at rest and in transit, making it useless to unauthorized parties even if stolen.
Measure, Monitor, and Continuously Improve
DLP is not a “set it and forget it” solution. Regularly review incident logs, policy effectiveness, and user feedback. Track key metrics to refine policies and address emerging threats continuously.
👉 Navigating DLP complexities requires a strategic, phased approach. Begin with data discovery and classification, roll out policies incrementally, foster user adoption, enforce access controls, use encryption, and embrace continuous monitoring. This transforms DLP into a resilient, evolving defense.
Top-rated Enterprise-Grade DLP Solution - AnySecura
Addressing the common pain points of DLP implementation requires a modern, intelligent solution. AnySecura is an enterprise-grade DLP platform designed to provide comprehensive data protection while simplifying management and minimizing user friction. It directly tackles the challenges enterprises face with its integrated, feature-rich architecture.
AnySecura addresses the core DLP challenges in the following ways:
Solve Complexity with Intelligent Automation
A primary challenge is accurately identifying sensitive data without creating a massive manual workload. AnySecura's Sensitive Content Inspection module automates this process. It uses keywords, regular expressions, and pre-built templates to discover sensitive data across the organization. Its Document Tagging module can then automatically apply classification labels (e.g., "Confidential," "Internal") to documents as they are created or modified. This automation drastically reduces manual effort and ensures policies are applied consistently.
Reduce False Positives and Alert Fatigue
Instead of relying on rigid, binary block/allow rules, AnySecura provides a range of flexible policy controls. For instance, rather than blocking a file transfer outright, an administrator can configure a policy that triggers a user warning, requiring them to provide a business justification before proceeding. For higher-risk actions, Critical Behavior Audit can trigger screen recording, capturing context for review without generating a low-value alert. This nuanced approach, combined with precise content-aware policies, significantly reduces false positives and allows security teams to focus on genuine risks.
Balance Security and Usability
AnySecura is built to secure data without halting business. Its Application and Filing feature allows users to request temporary exceptions (e.g., permission to use a USB drive or send an email that would normally be blocked) through a streamlined approval workflow. For less critical actions, users can "self-file" a justification, which is logged for audit. Furthermore, its Screen Watermark and Print Watermark features serve as a constant but non-disruptive reminder to users about data sensitivity, deterring casual leaks without blocking work.
Ensure Comprehensive Coverage
AnySecura provides a unified agent that covers data across its entire lifecycle and all potential egress points. Its modules offer granular control over:
- Endpoints: Document Control, Print Control, Removable Media Control and Device Control manage operations on local files and peripherals like USB drives.
- Network: Network Access Control, Network Traffic Control, and Web Access Control monitor and block unauthorized uploads to websites and cloud storage.
- Communications: Email Control and Instant Message Monitoring inspect outgoing messages and file transfers for sensitive content.
- Data at Rest: The Transparent Encryption module ensures sensitive files are always stored in an encrypted state, readable only by authorized users and applications, even if stolen.
👉 AnySecura rises as a sophisticated answer to DLP's inherent challenges—an enterprise-grade solution engineered for comprehensive protection with streamlined management. It intelligently automates sensitive data inspection and classification, drastically reducing manual effort. Its flexible policy controls, including user warnings and critical behavior audits, dramatically cut false positives, allowing security teams to focus on genuine threats.
Conclusion
Throughout this article, we’ve answered the critical question: “What is DLP (Data Loss Prevention)?” and explored why it is indispensable for modern enterprises. We examined how DLP operates in practice, highlighted common use cases where safeguarding data is crucial, reviewed the challenges and pain points organizations often face, and outlined actionable solutions and best practices for successful adoption. These insights demonstrate that understanding what DLP truly means is not just academic—it’s a business-critical step toward long-term resilience against data breaches.
Implementing a robust DLP strategy is essential in today’s threat landscape. Moving beyond a checklist approach to compliance, organizations can unlock real benefits: greater data visibility, protection against both accidental and malicious leaks, and assured adherence to regulatory mandates. A strong DLP program strengthens security while enabling business growth.
Solutions like AnySecura empower enterprises to tackle traditional DLP challenges with confidence. By leveraging intelligent automation for data classification, offering flexible policy controls that minimize user friction, and providing comprehensive coverage across all data channels, AnySecura allows organizations to safeguard their most valuable asset—their data. This transforms IT and security teams from a reactive, incident-driven posture to a proactive, strategic defense that secures information, boosts productivity, and builds a truly resilient enterprise.
Start Free Trial

