- [email protected]
- 15 Scotts Road, #03-12, Singapore
How Does AnySecura Work
Explore the core features of AnySecura data loss prevention, endpoint management, and user behavior monitoring solutions. Click on the tabs below to view detailed demos of each function.
Document Control: Full Visibility & Protection
-
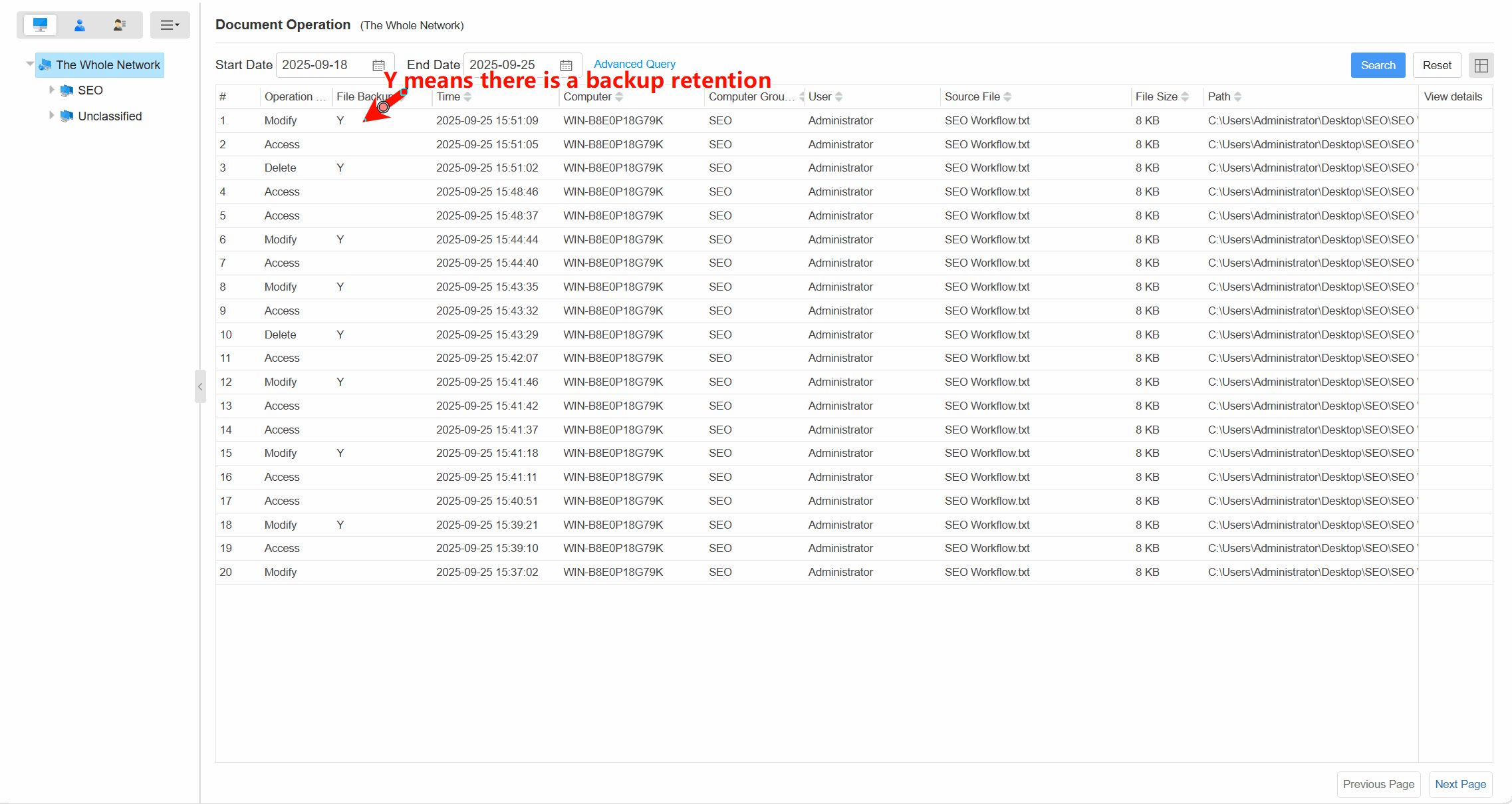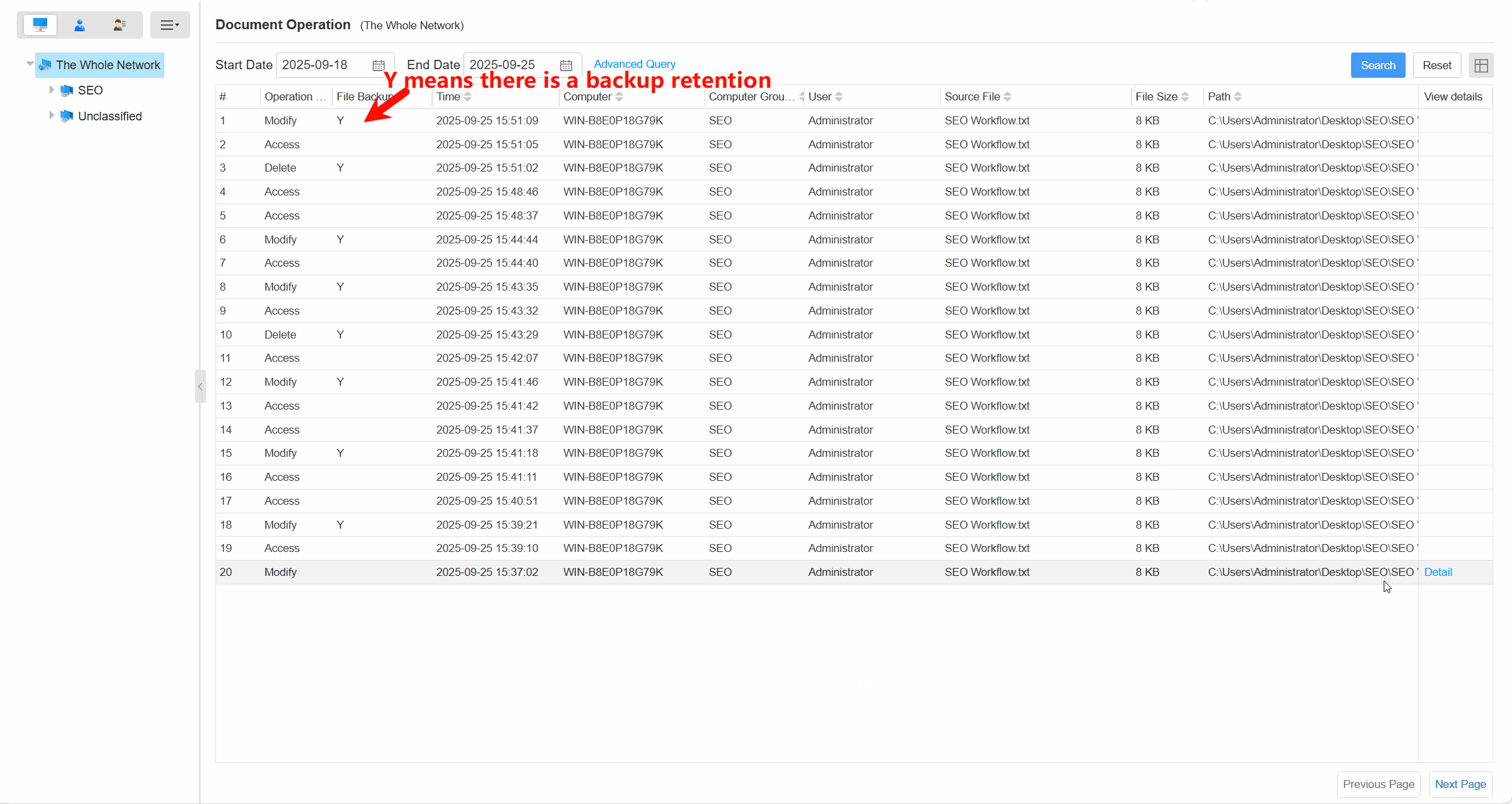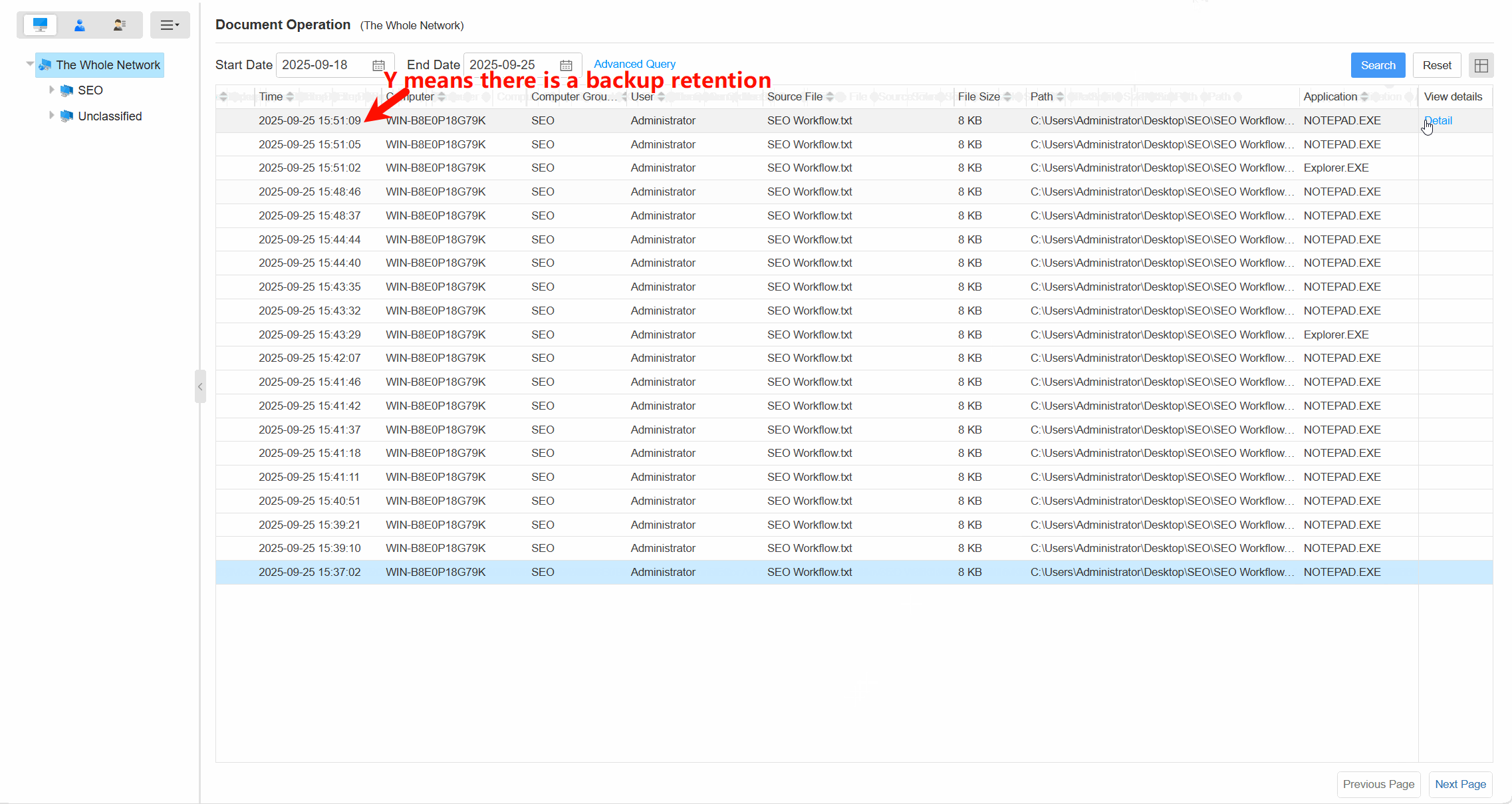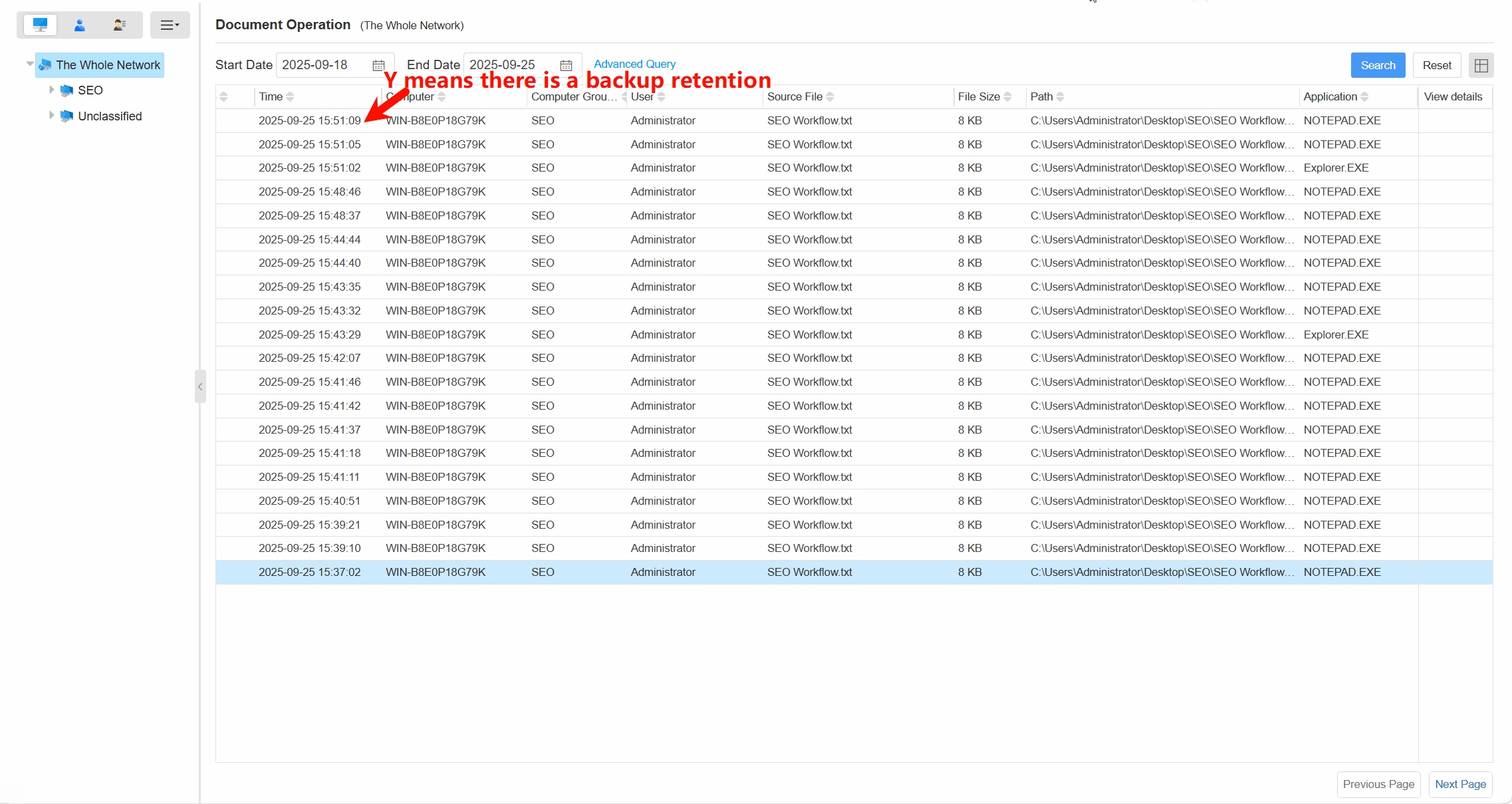
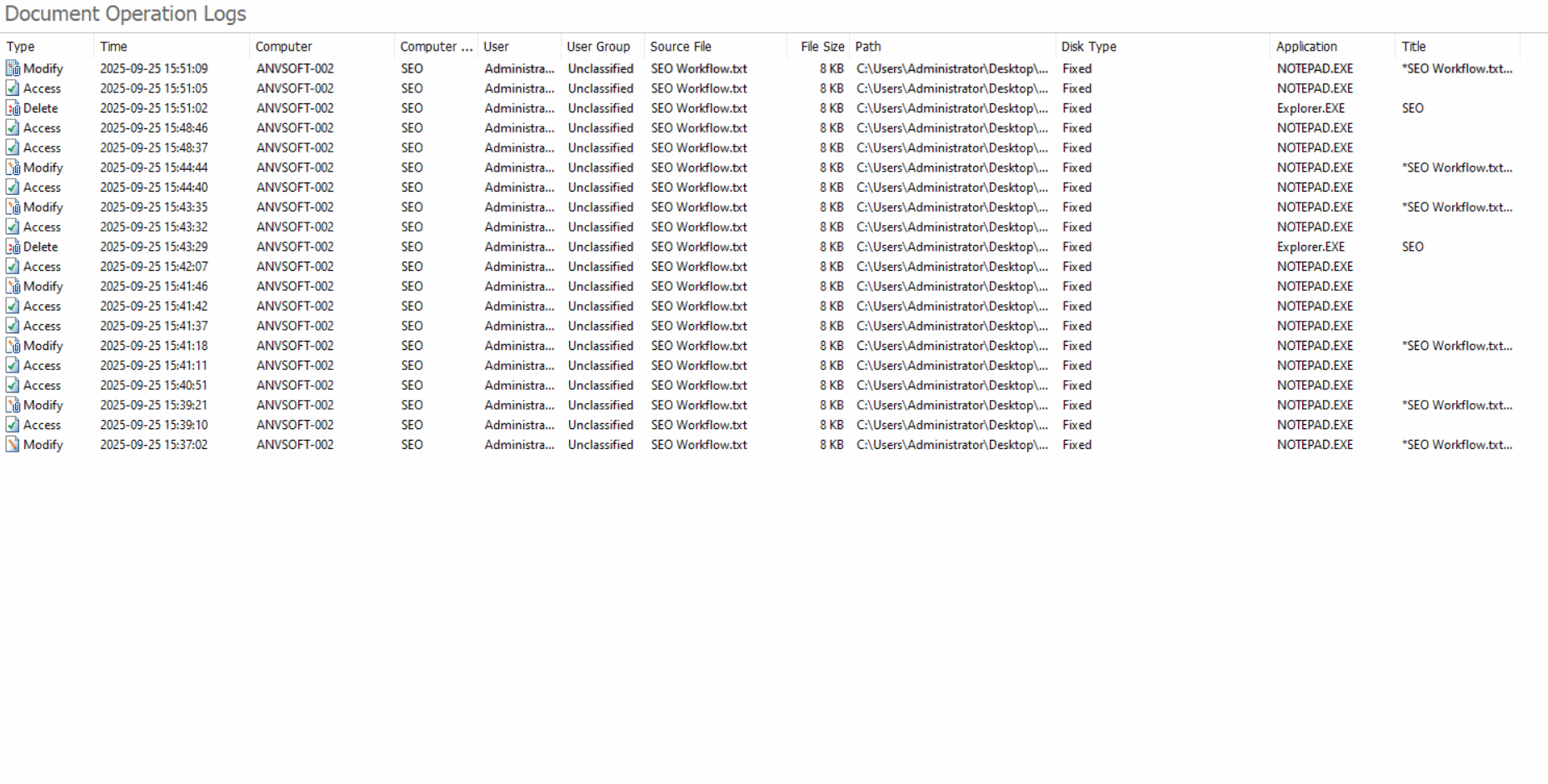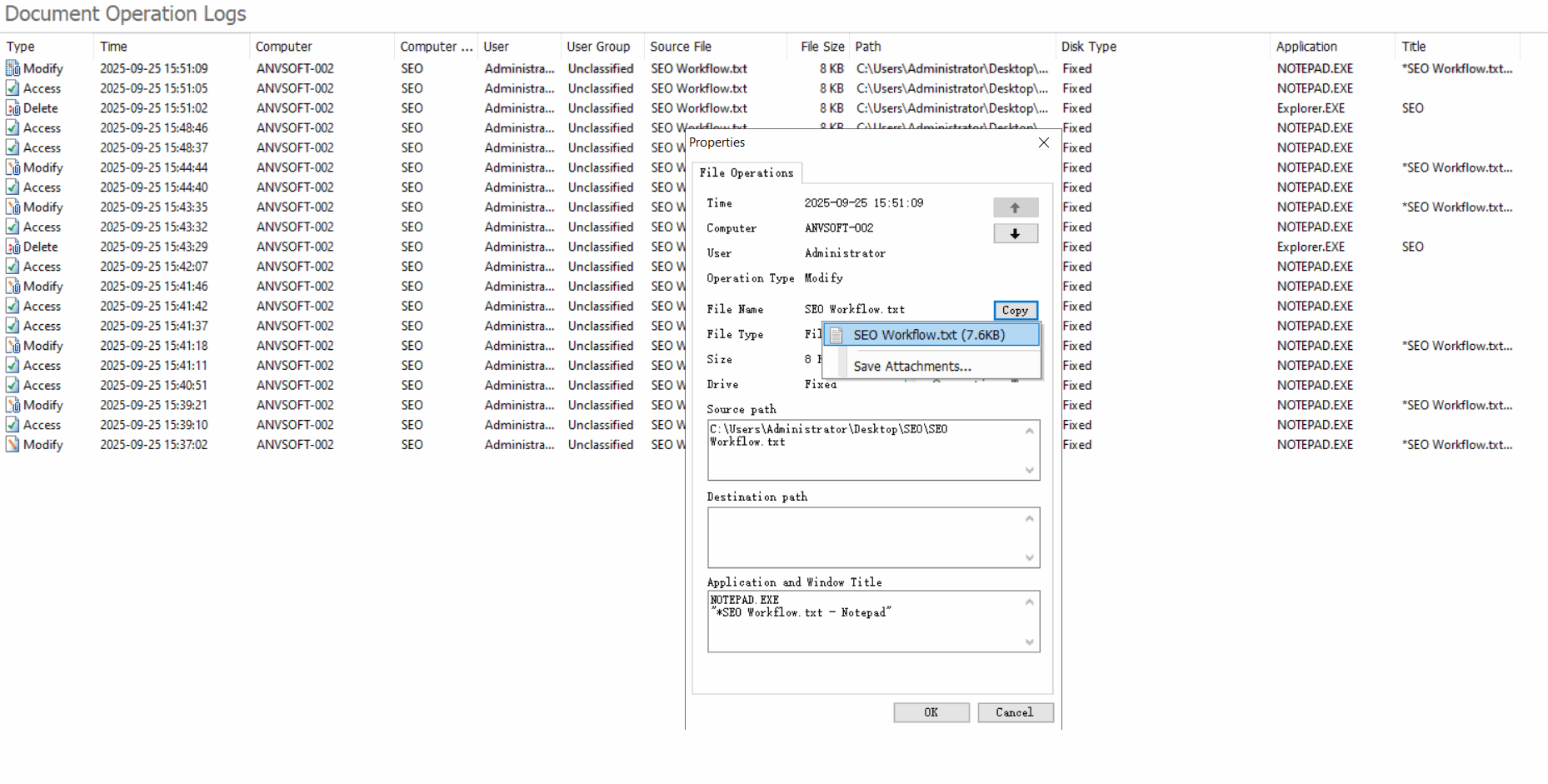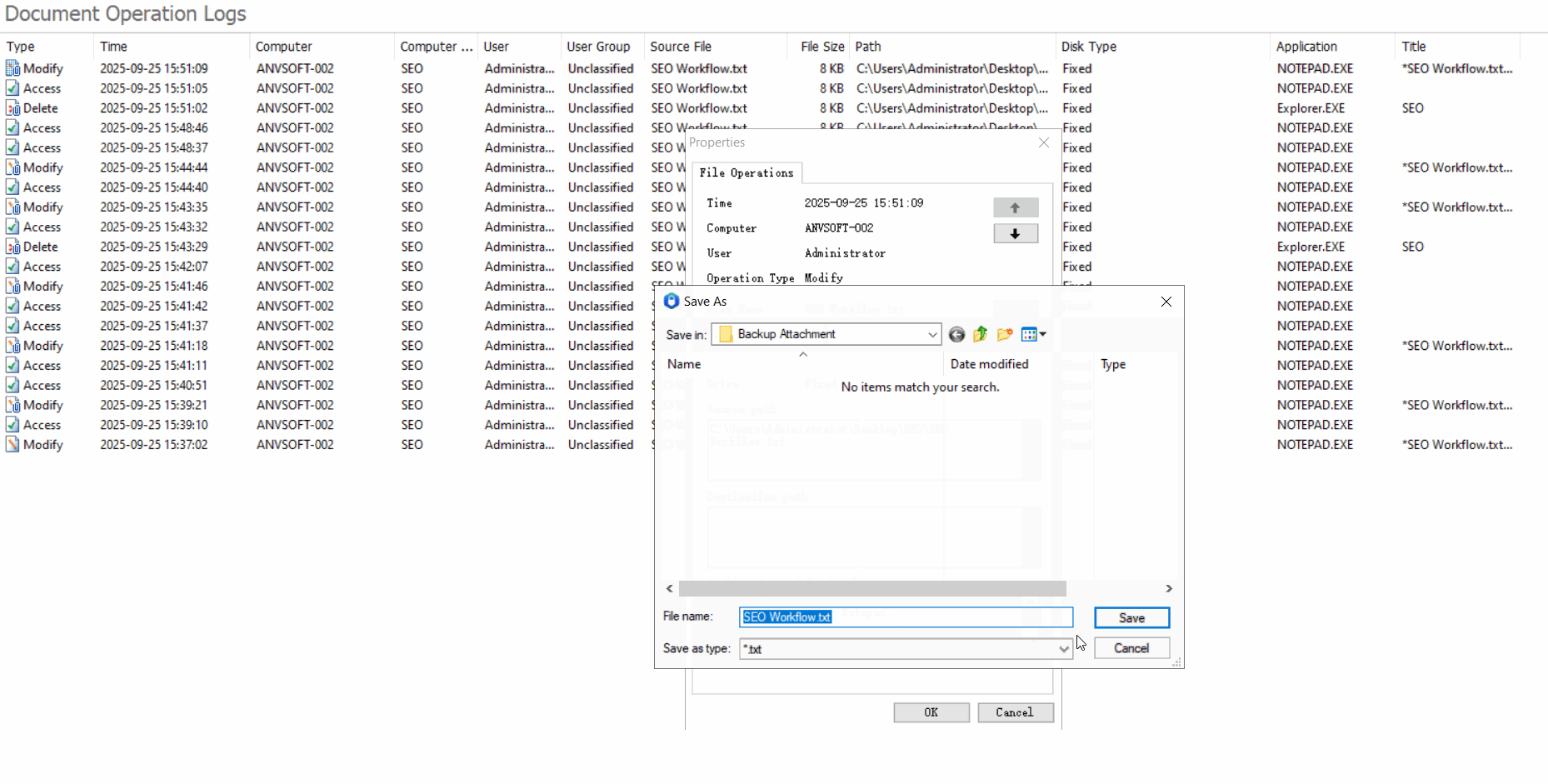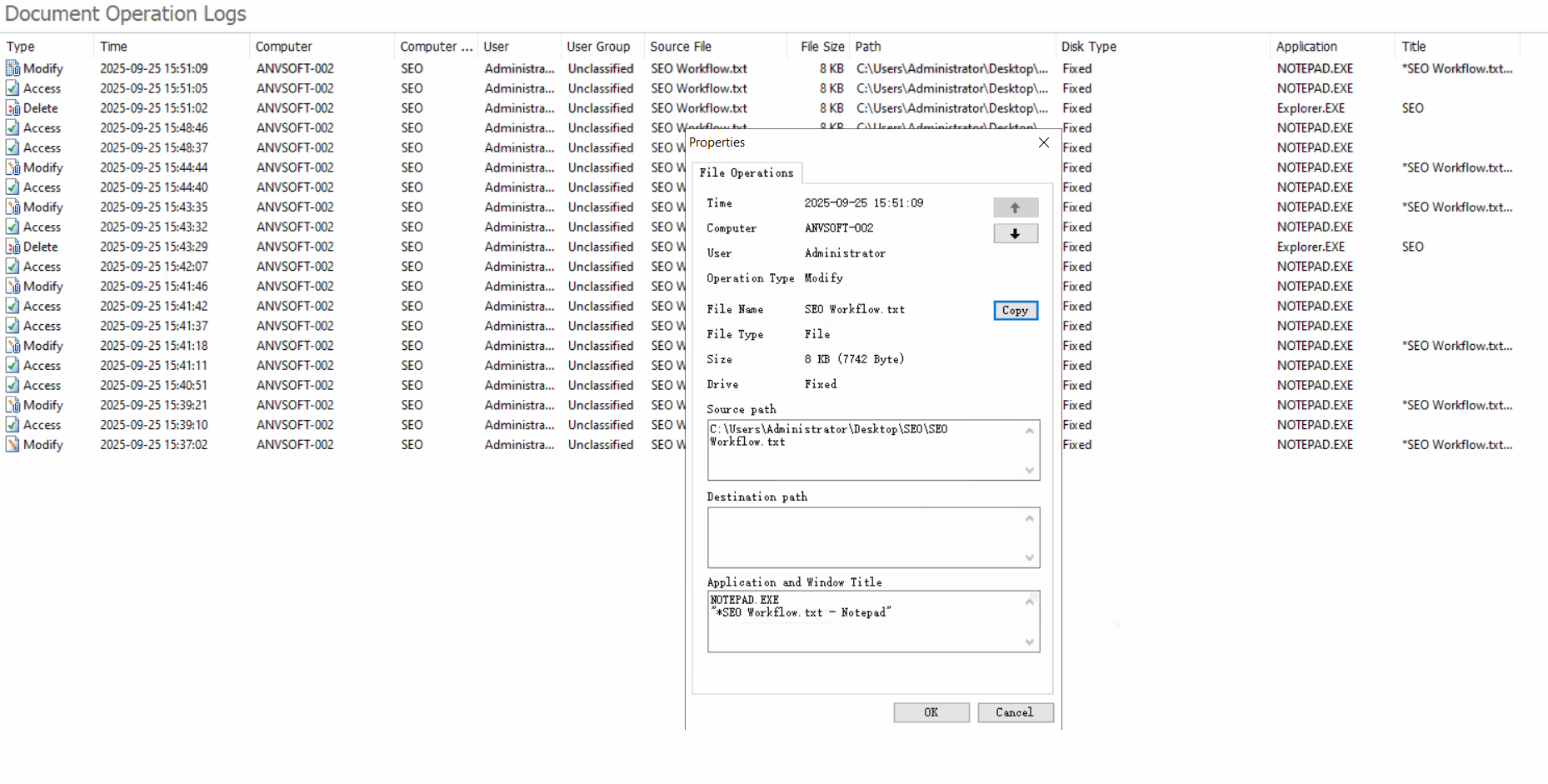
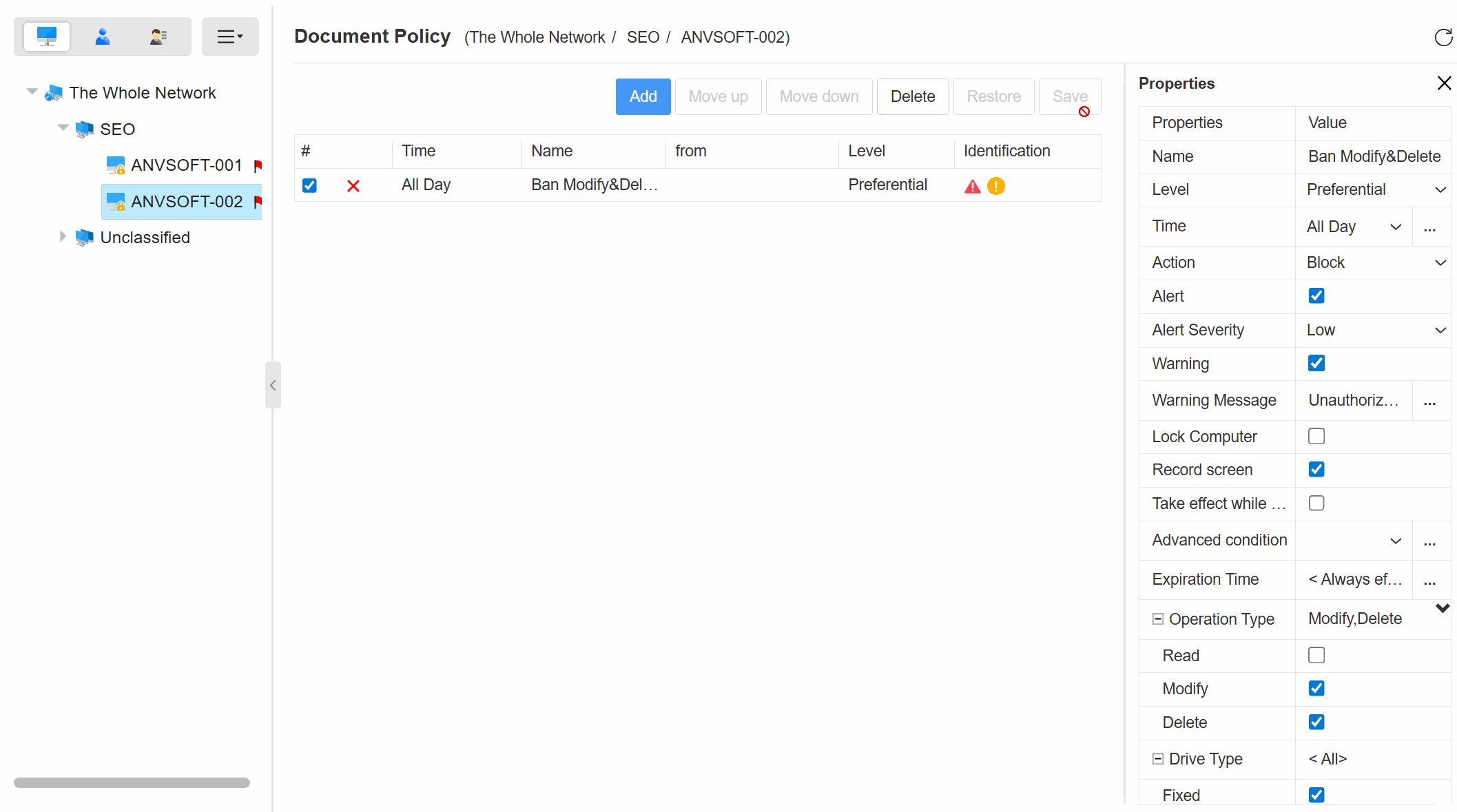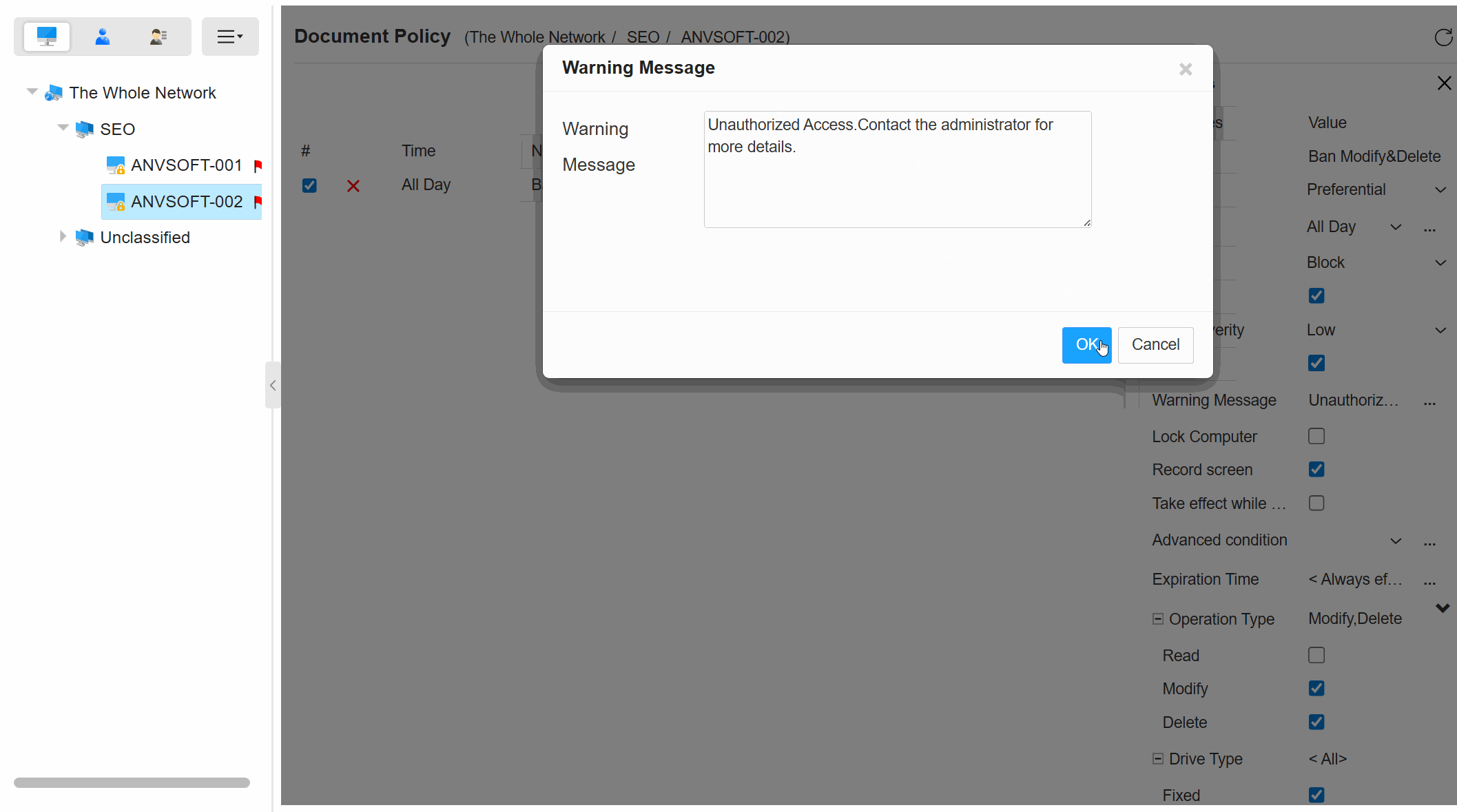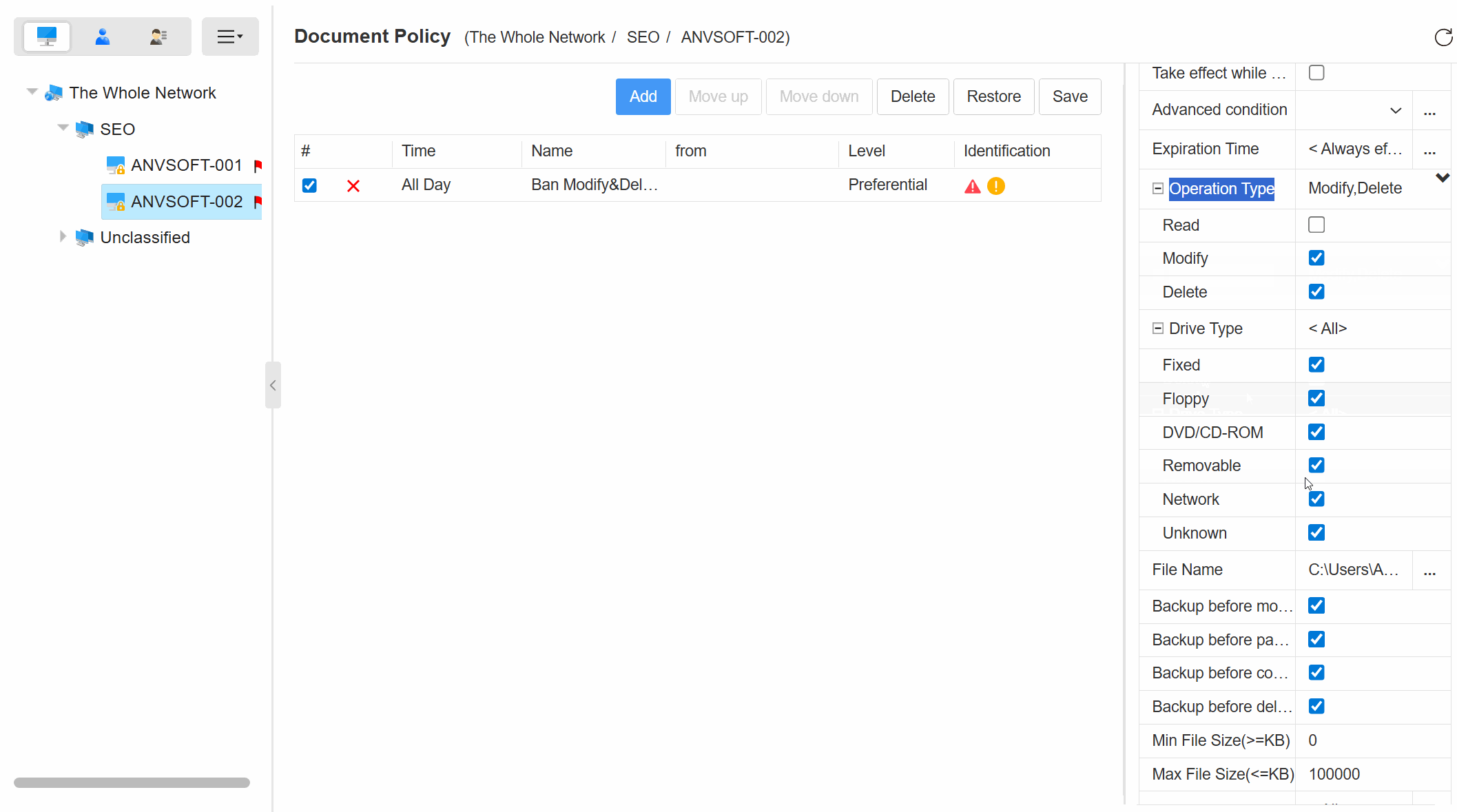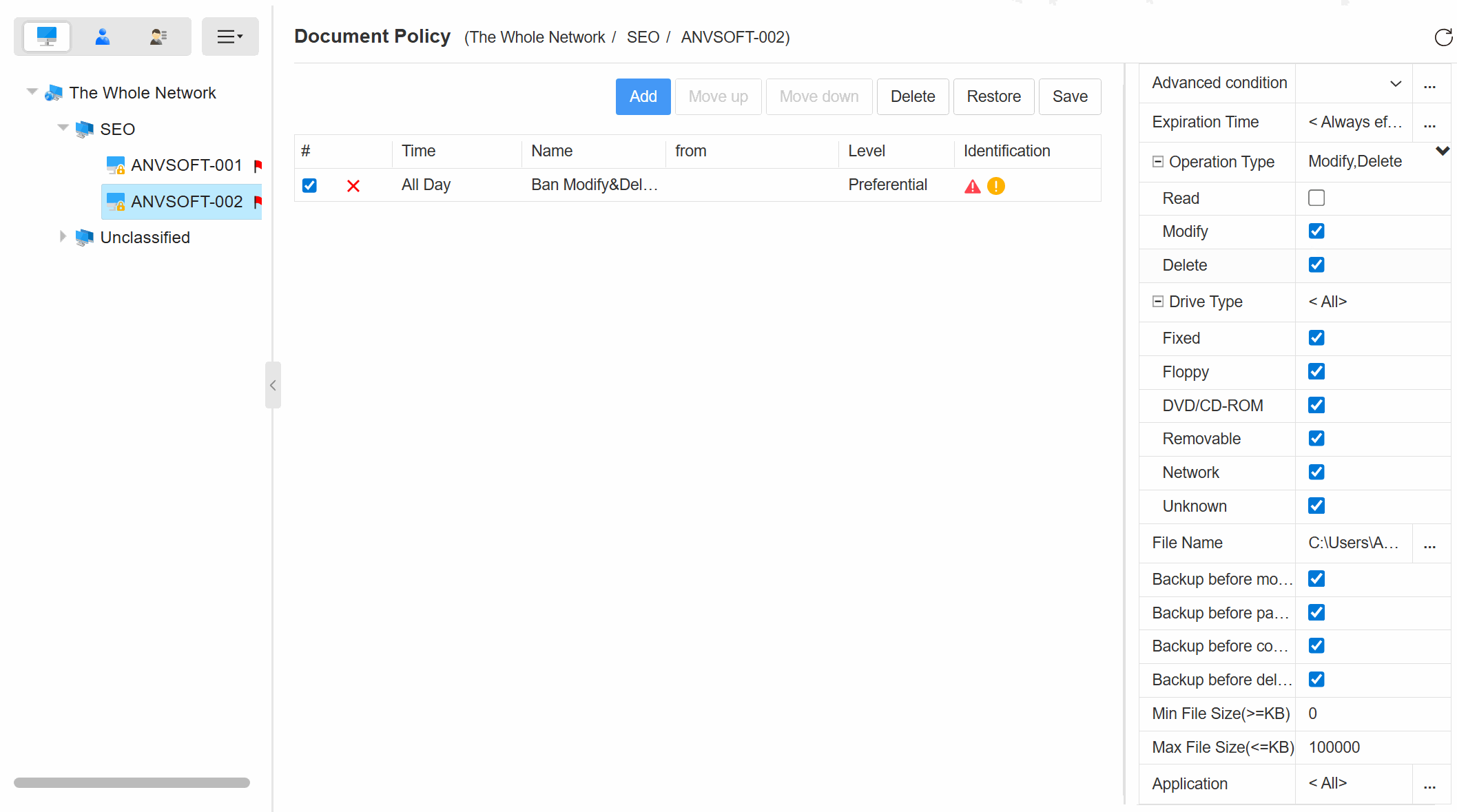
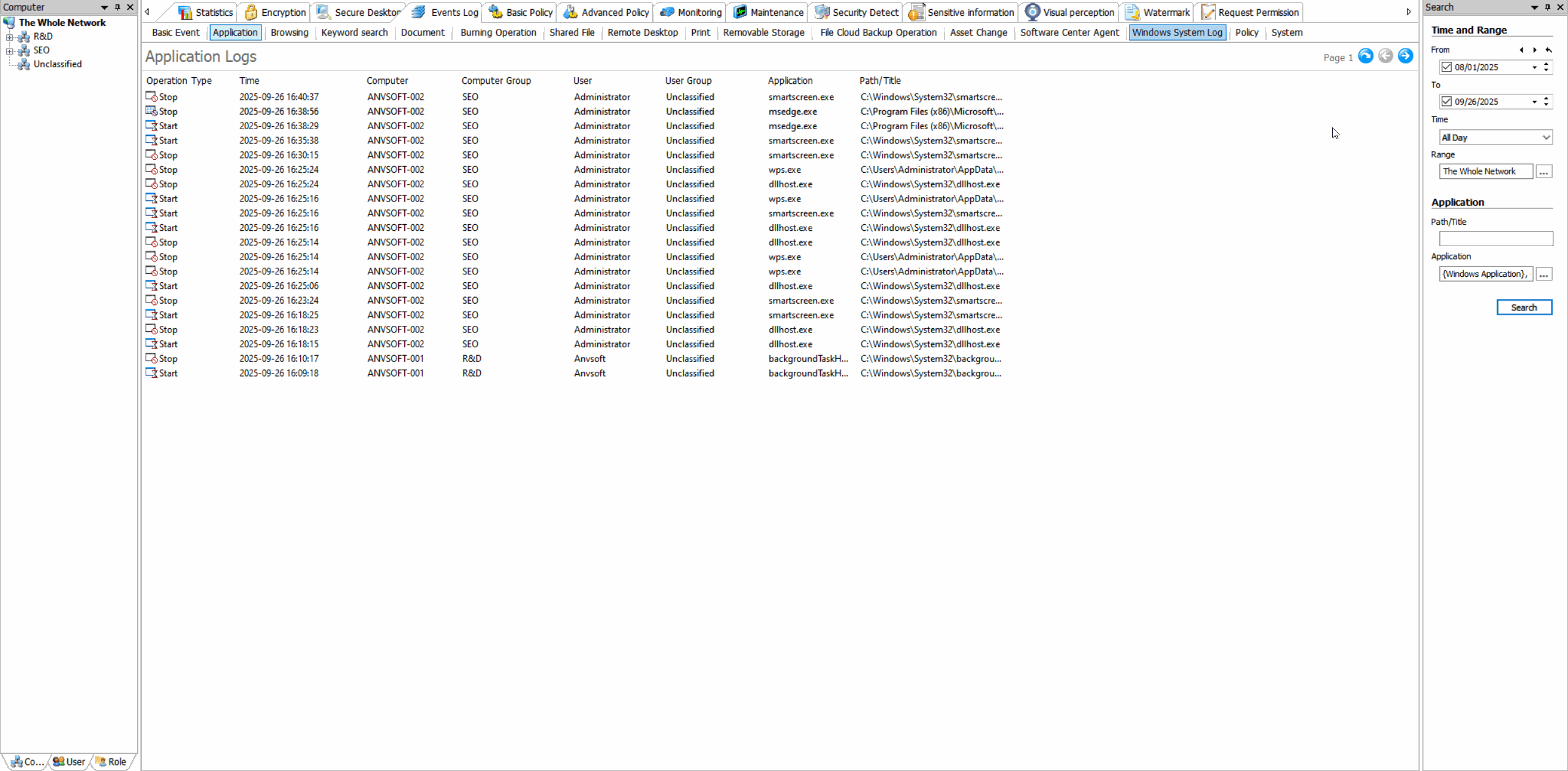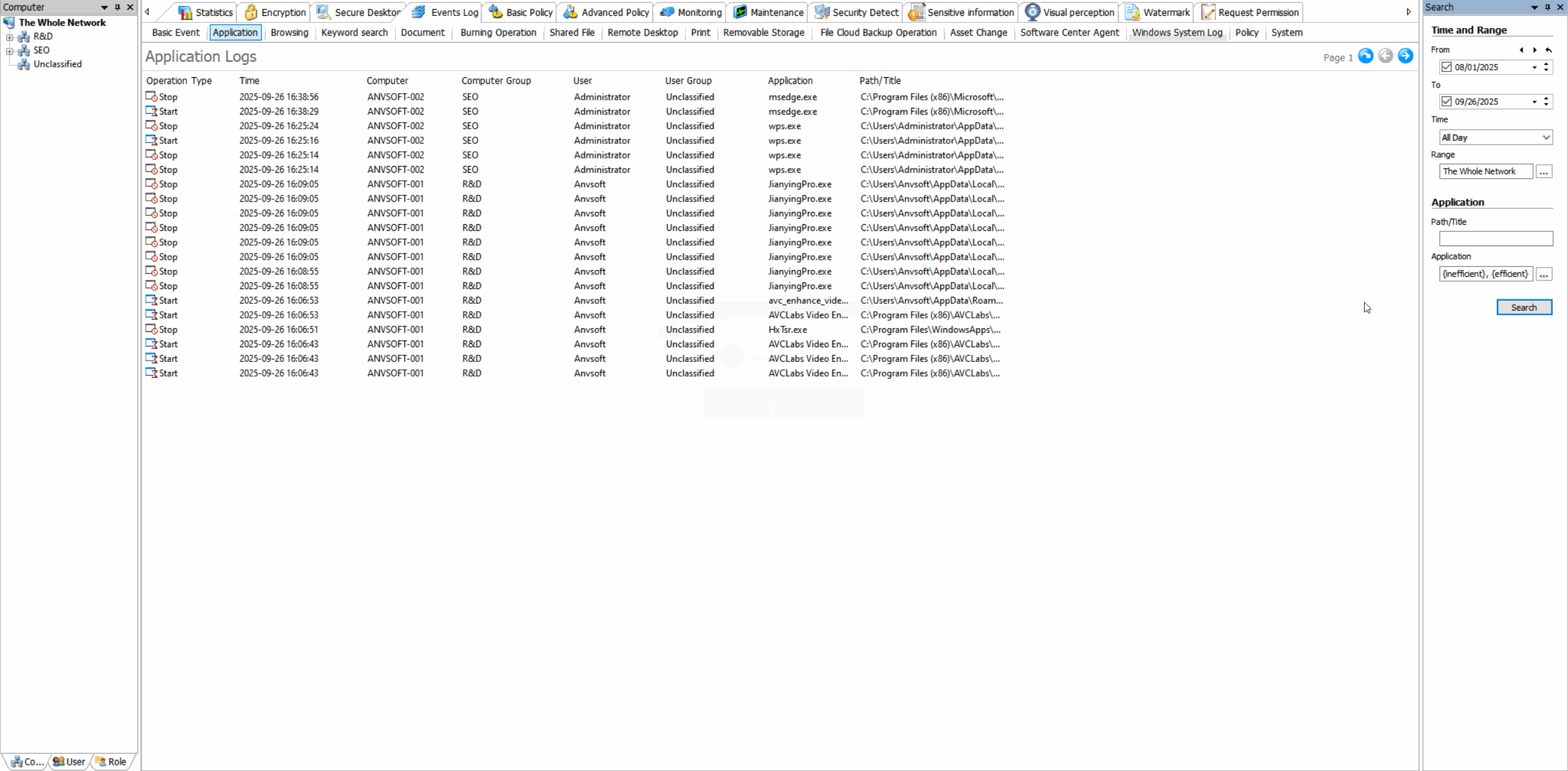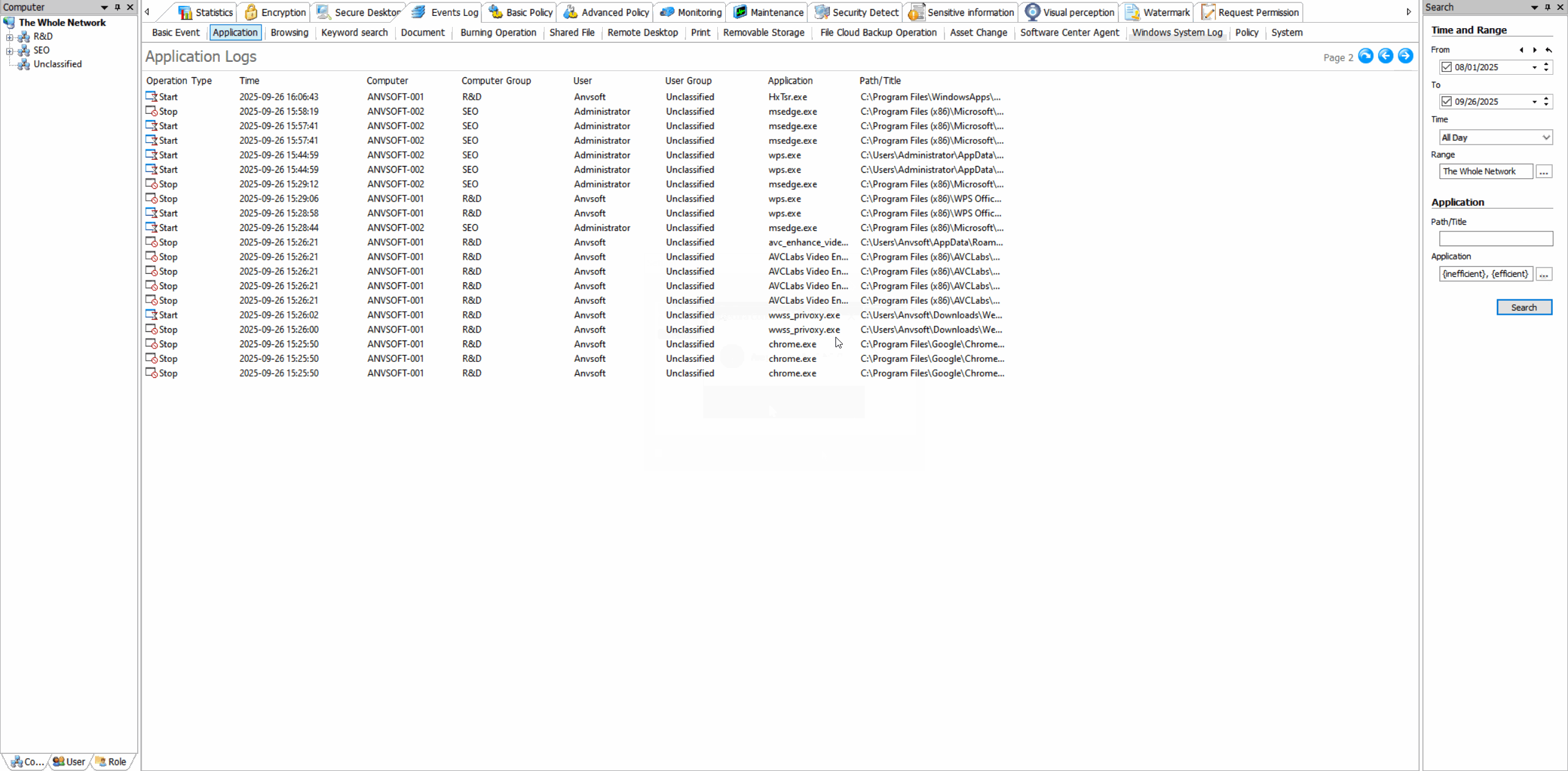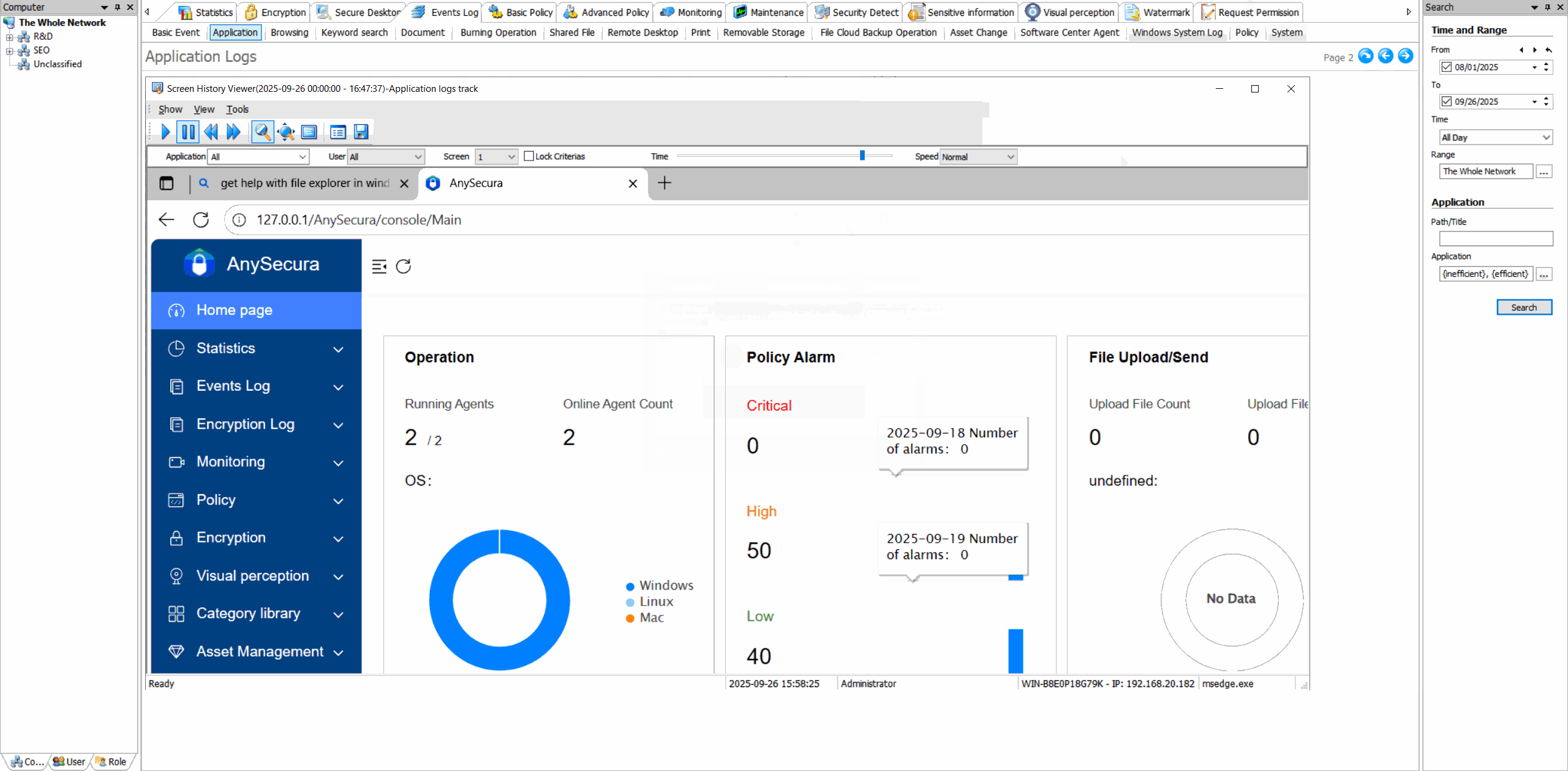
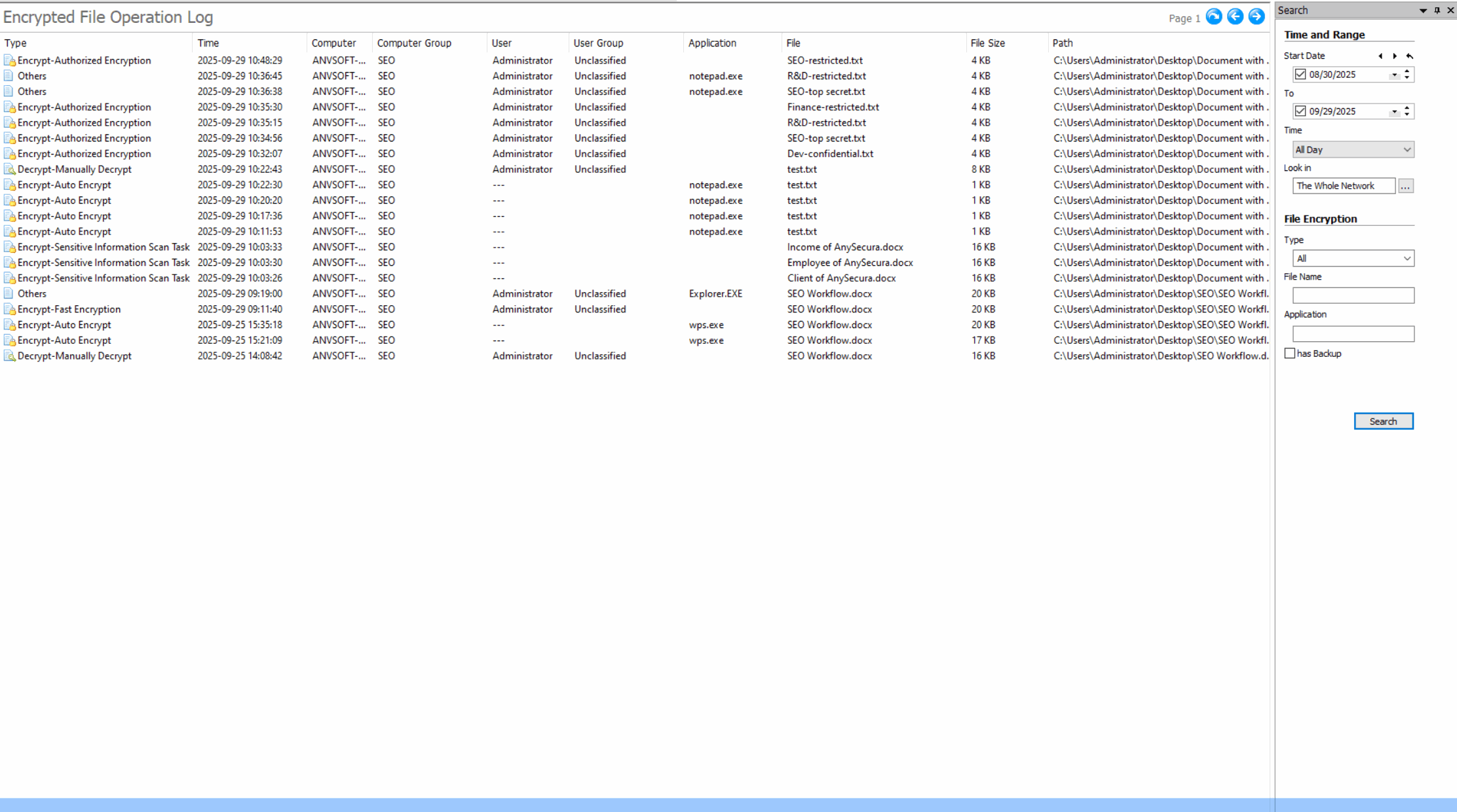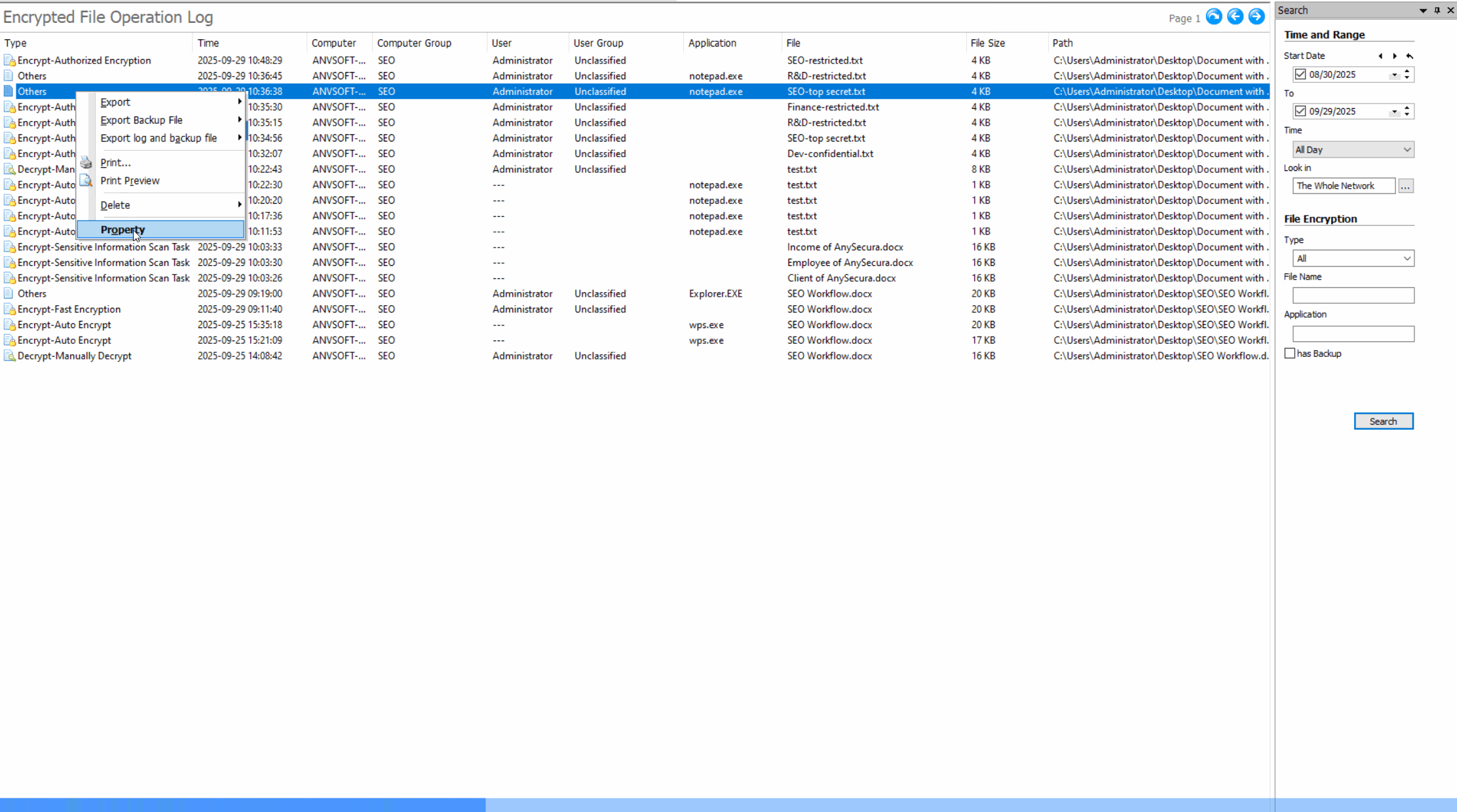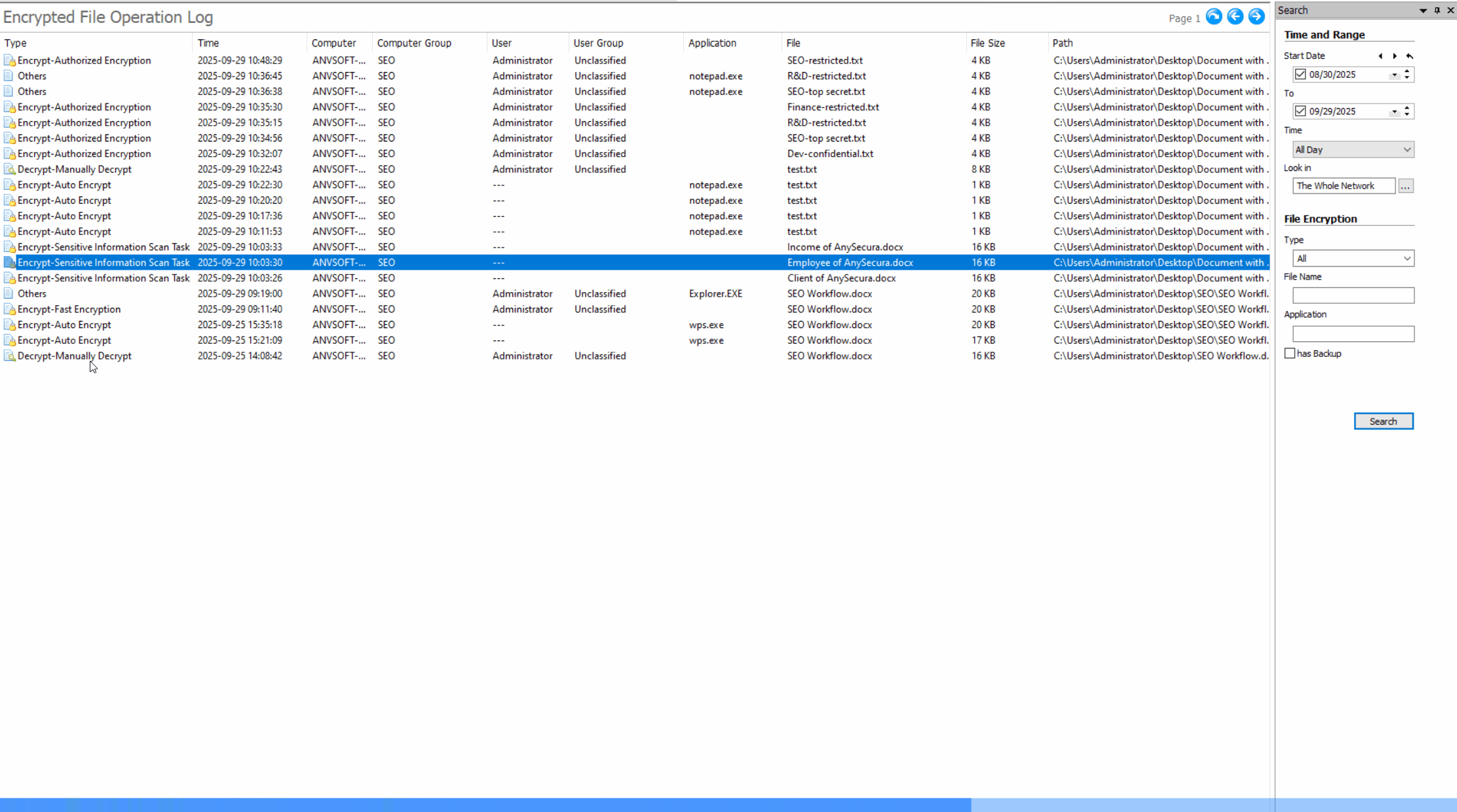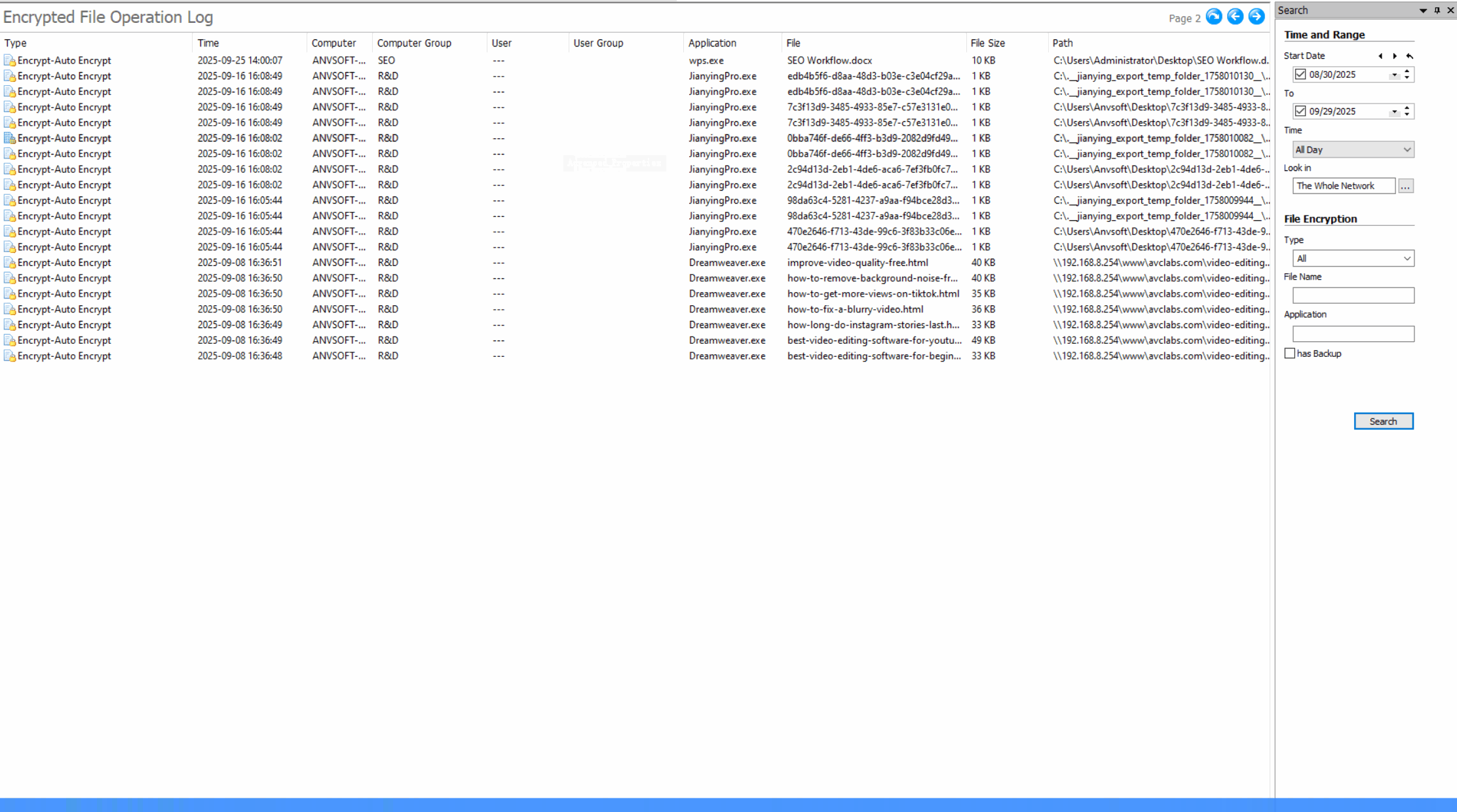
Comprehensive Operation LogsTrack all document actions (open, edit, save, delete, copy,etc) with timestamps, user info, and file paths.
-
Automatic BackupAutomatically back up files before modification, deletion, copying, or moving to prevent accidental data loss.
-
Granular Policy ControlDefine rules for document access, modification, and deletion based on user roles, departments, or sensitivity levels.
-
Unauthorized Action AlertsInstant notifications for suspicious document activities like mass copying or access attempts by unauthorized users.
Why Document Control Matters
Prevent unauthorized access, track document lifecycle, and maintain compliance with data protection regulations while ensuring business continuity through secure backups.
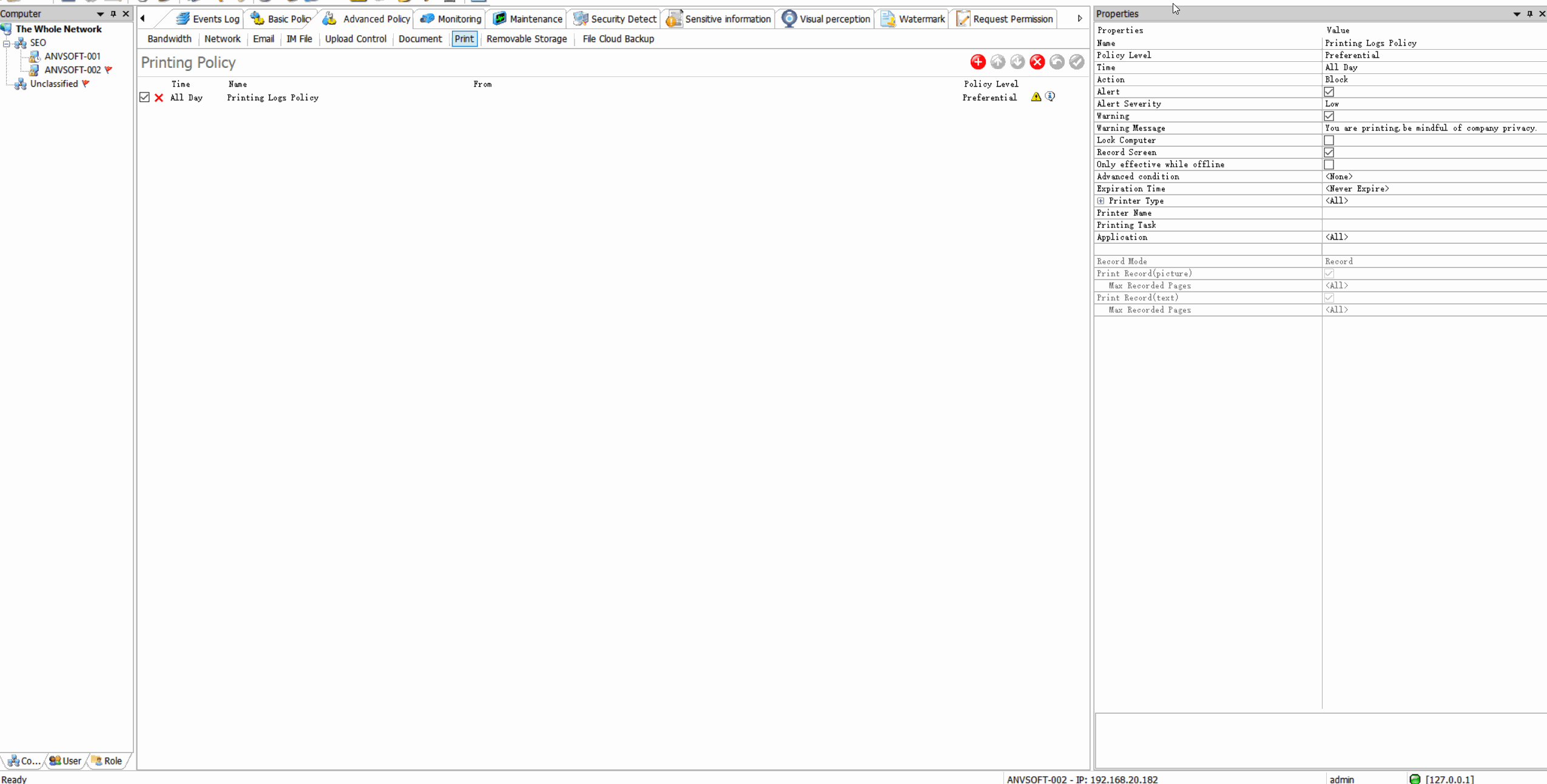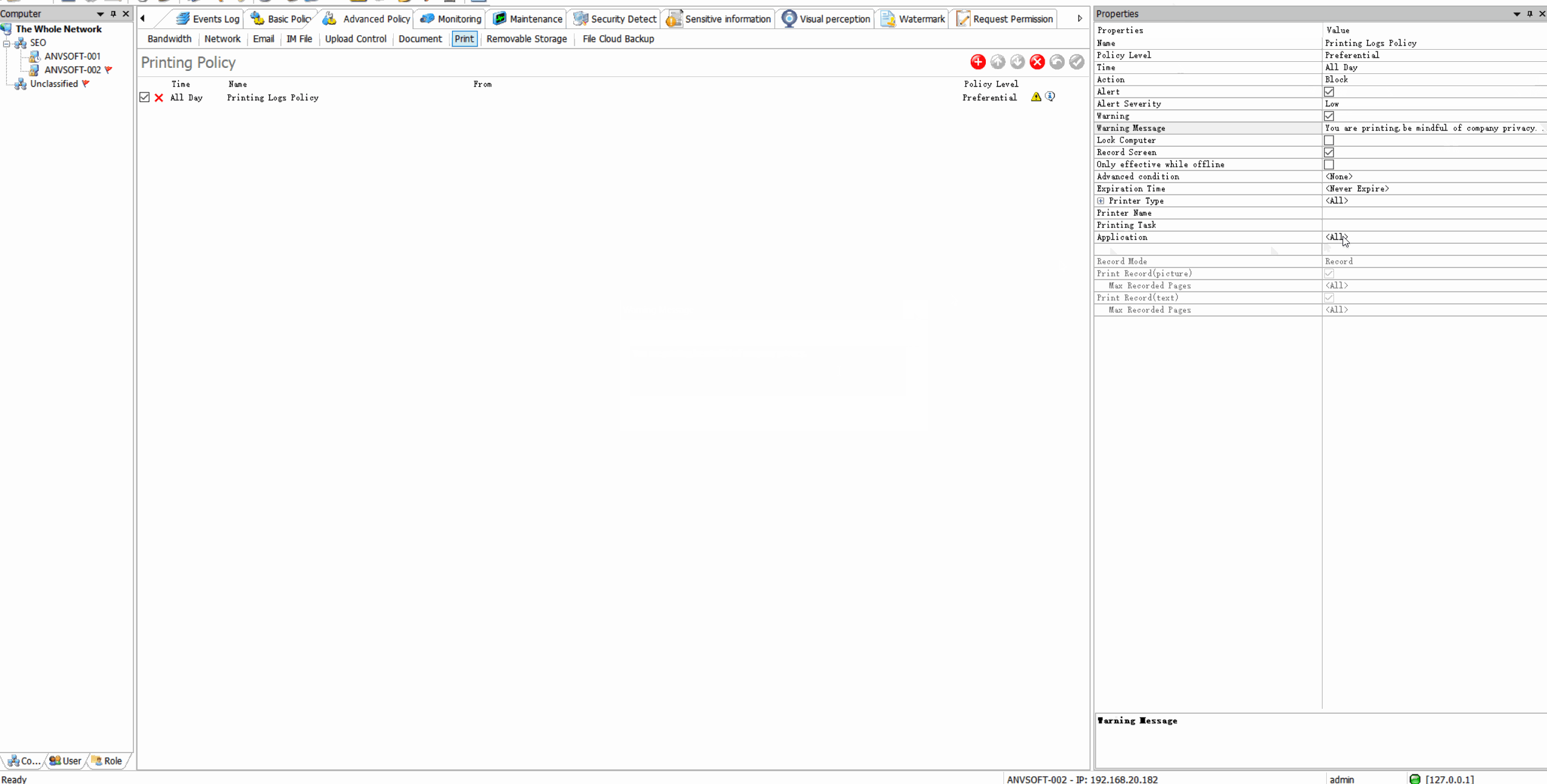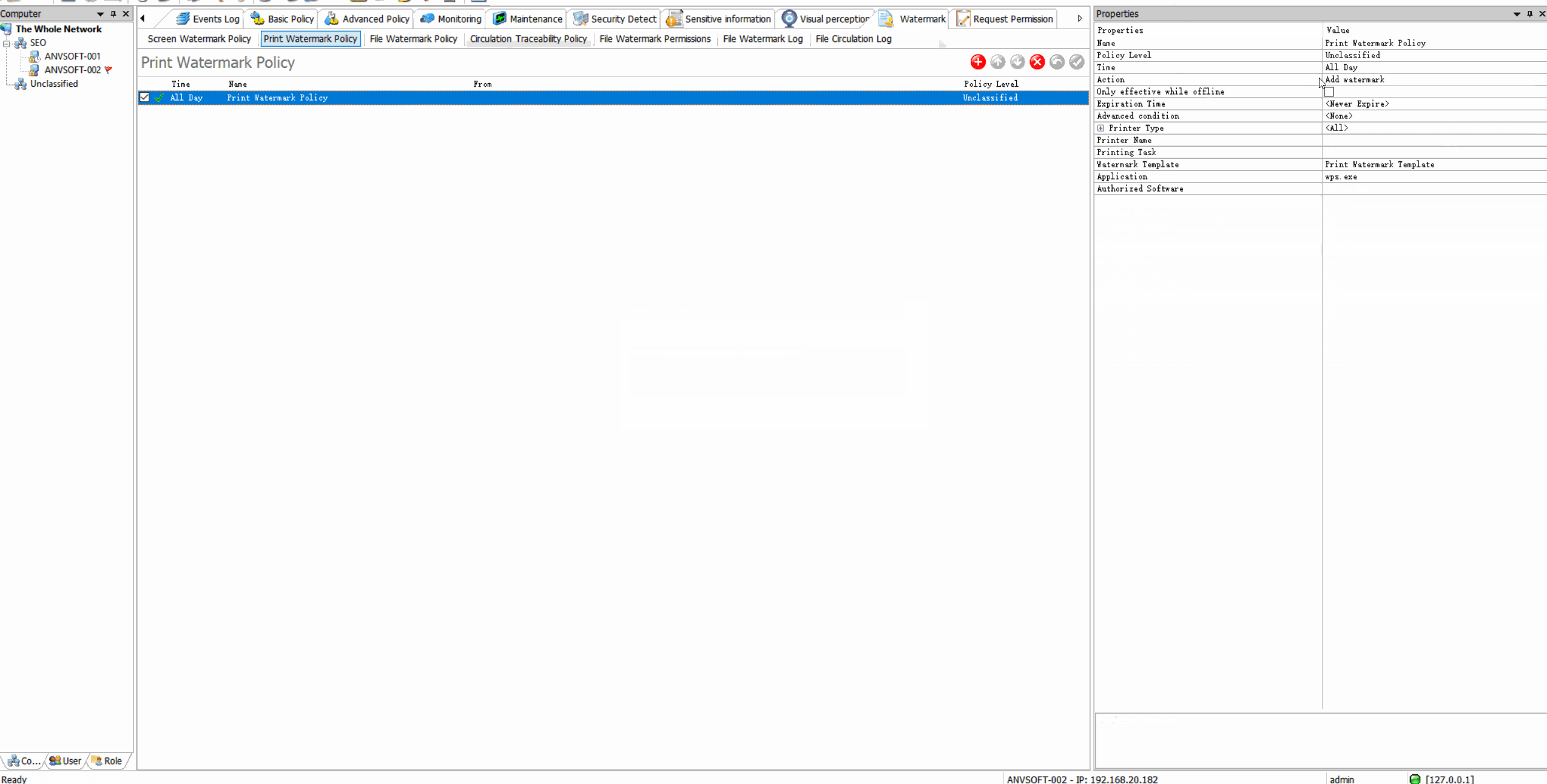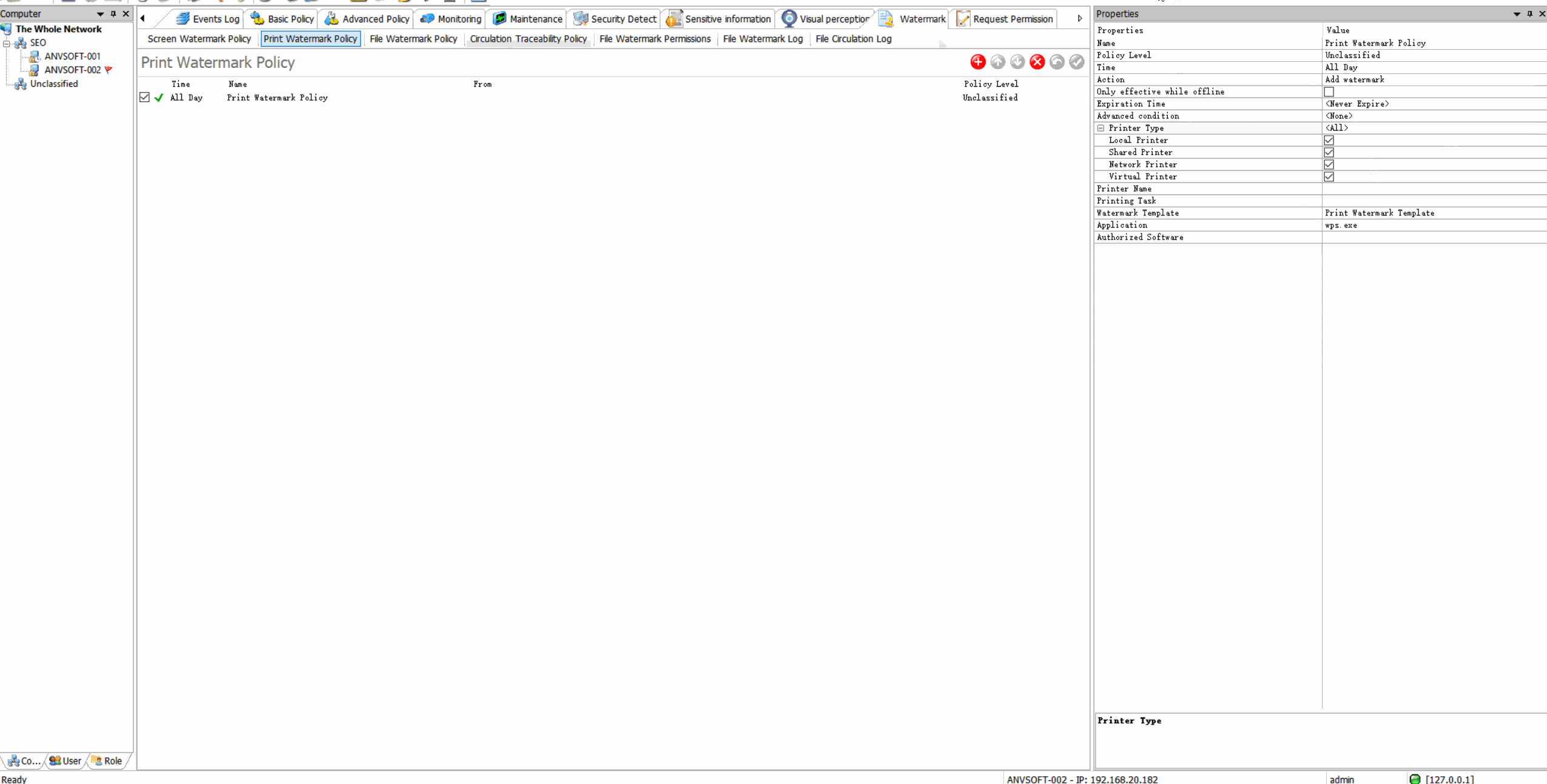
Print Control: Secure Document Output Management
-
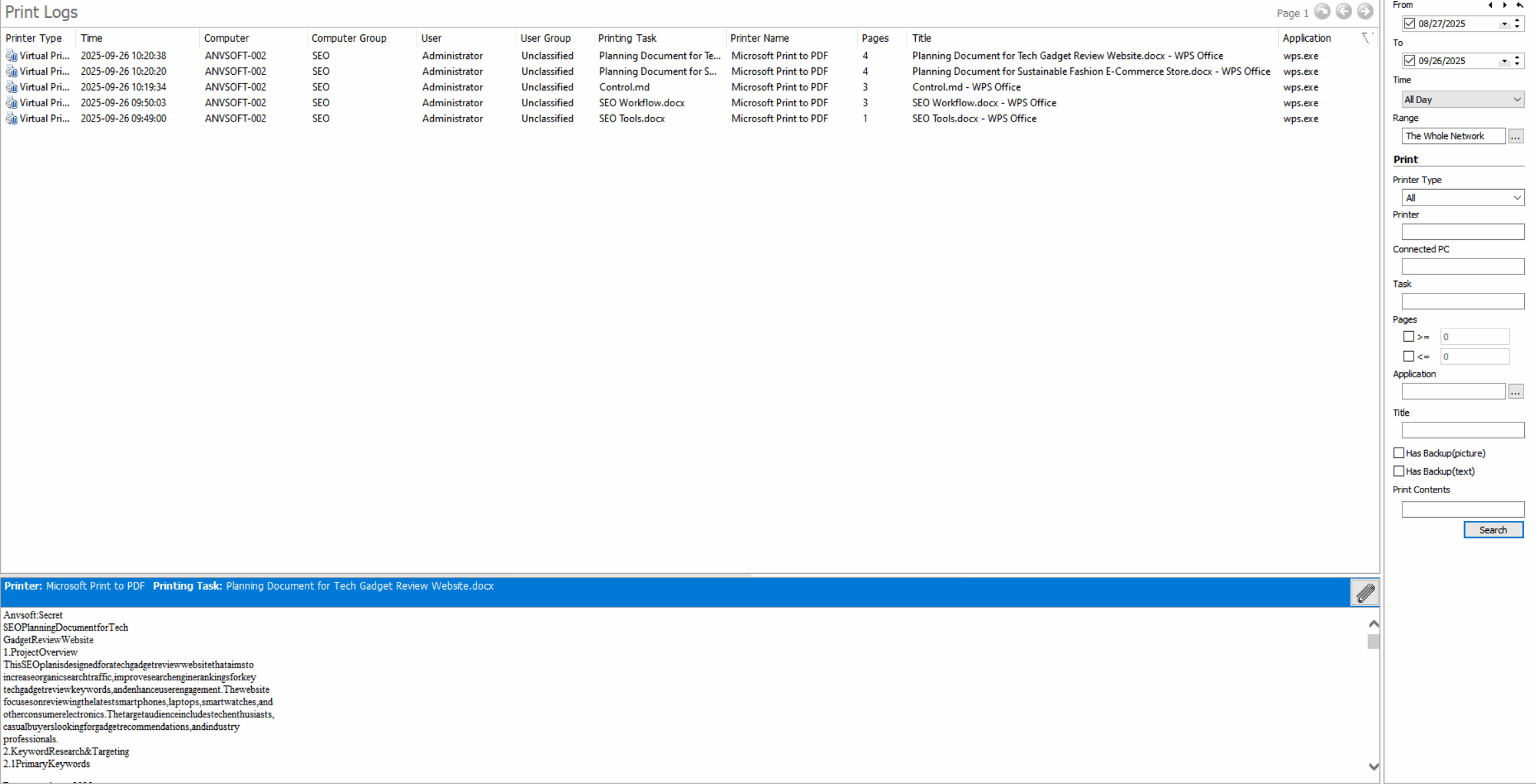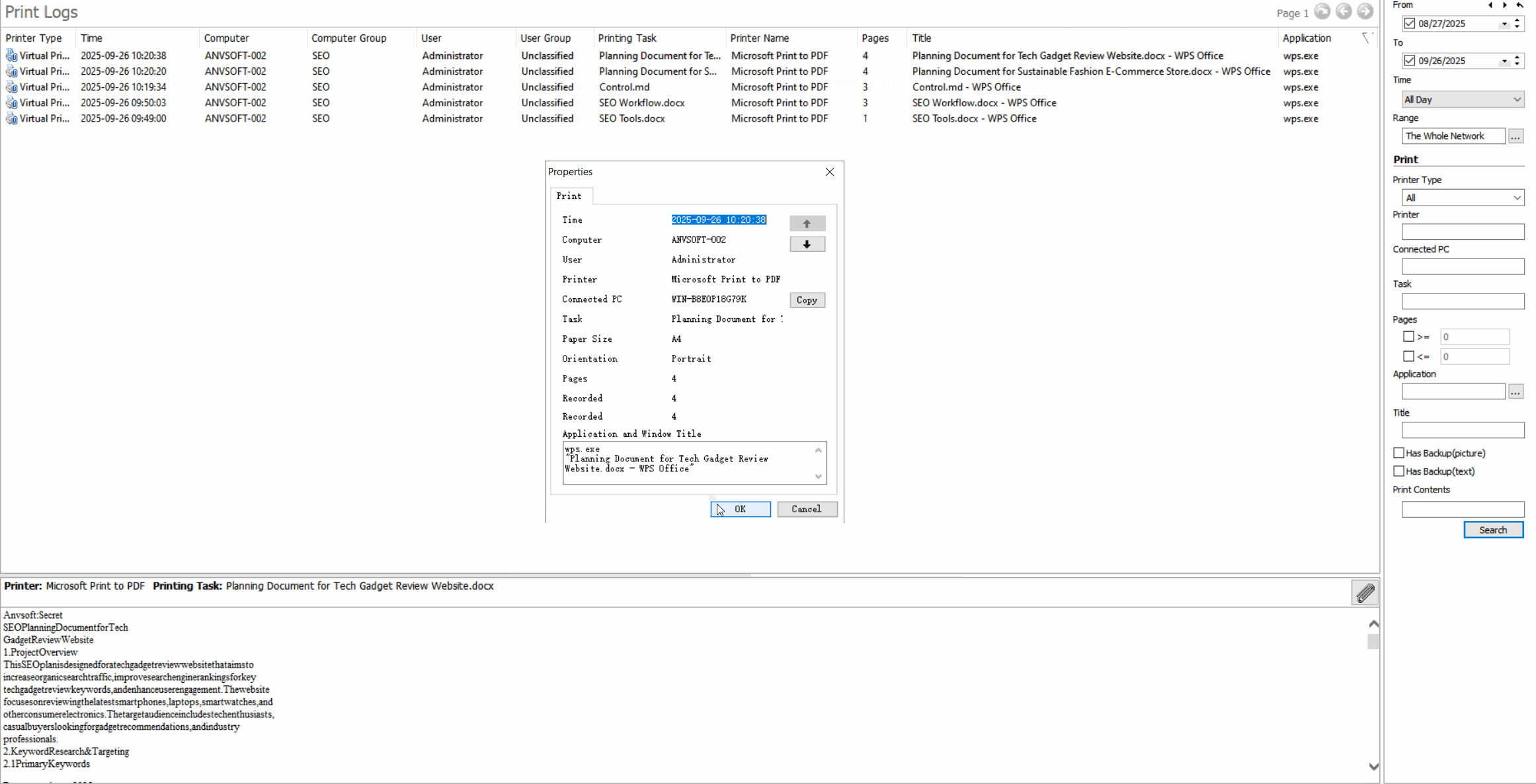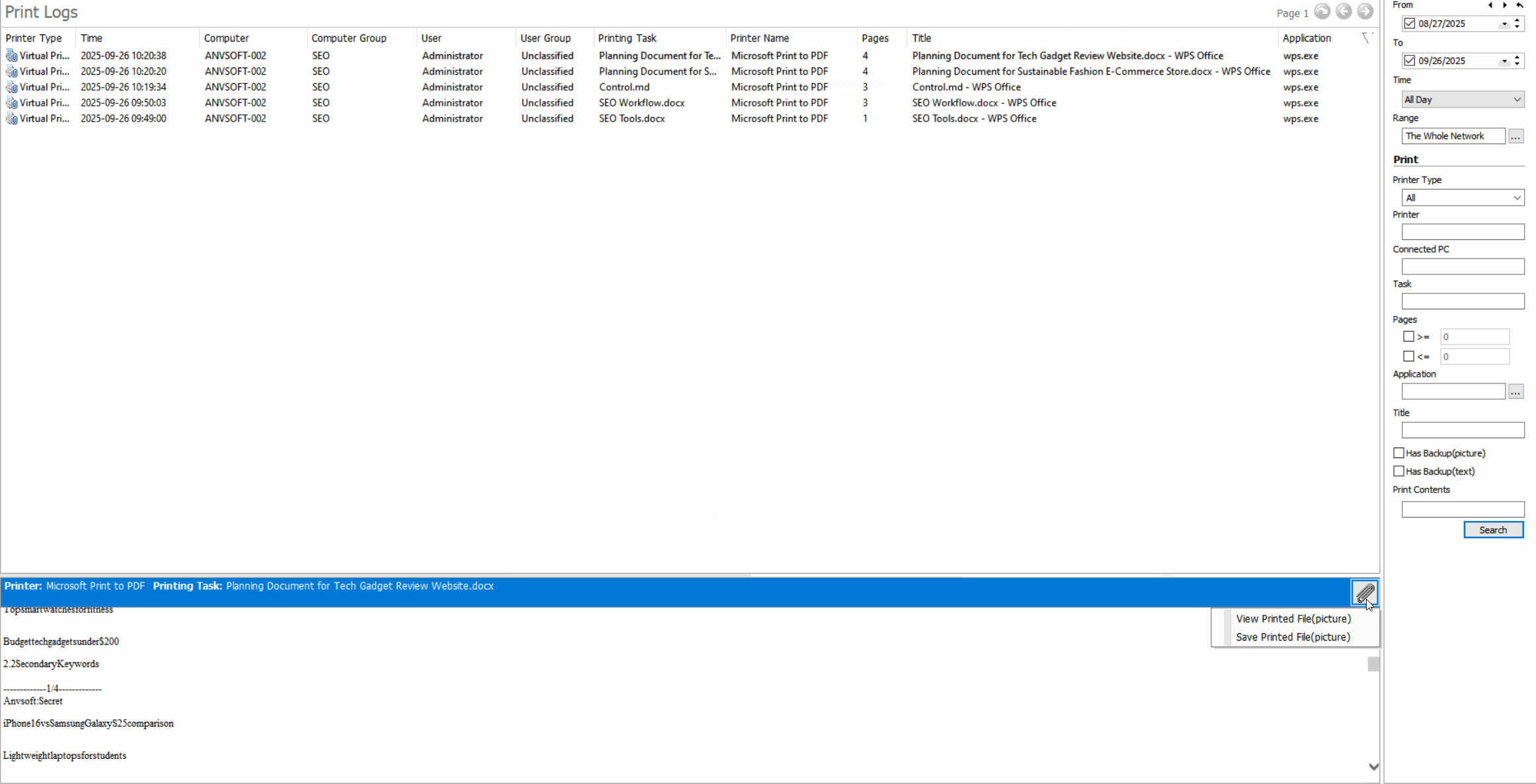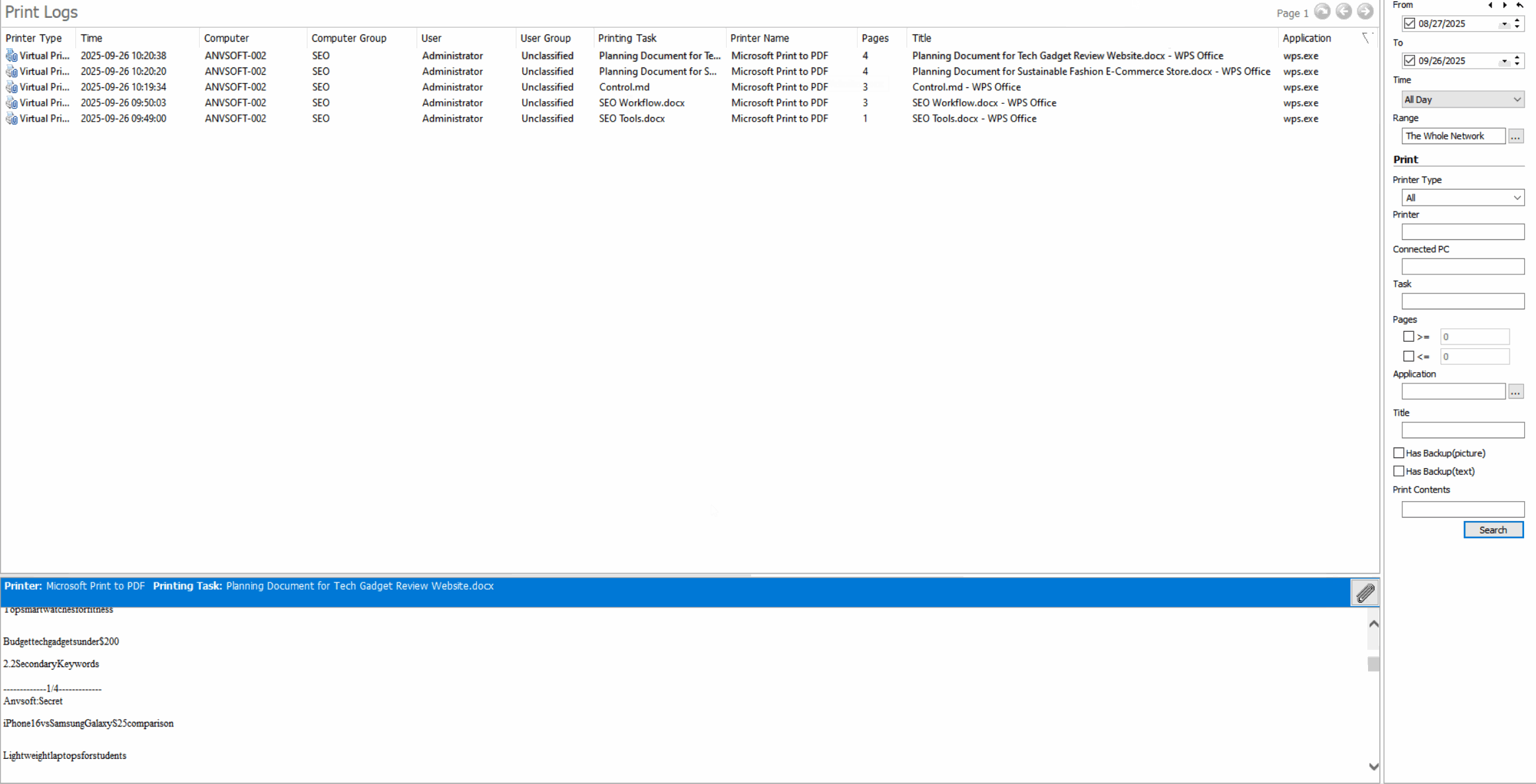
Detailed Print LogsRecord all print jobs with user ID, document name, timestamp, number of pages, and printer information.
-
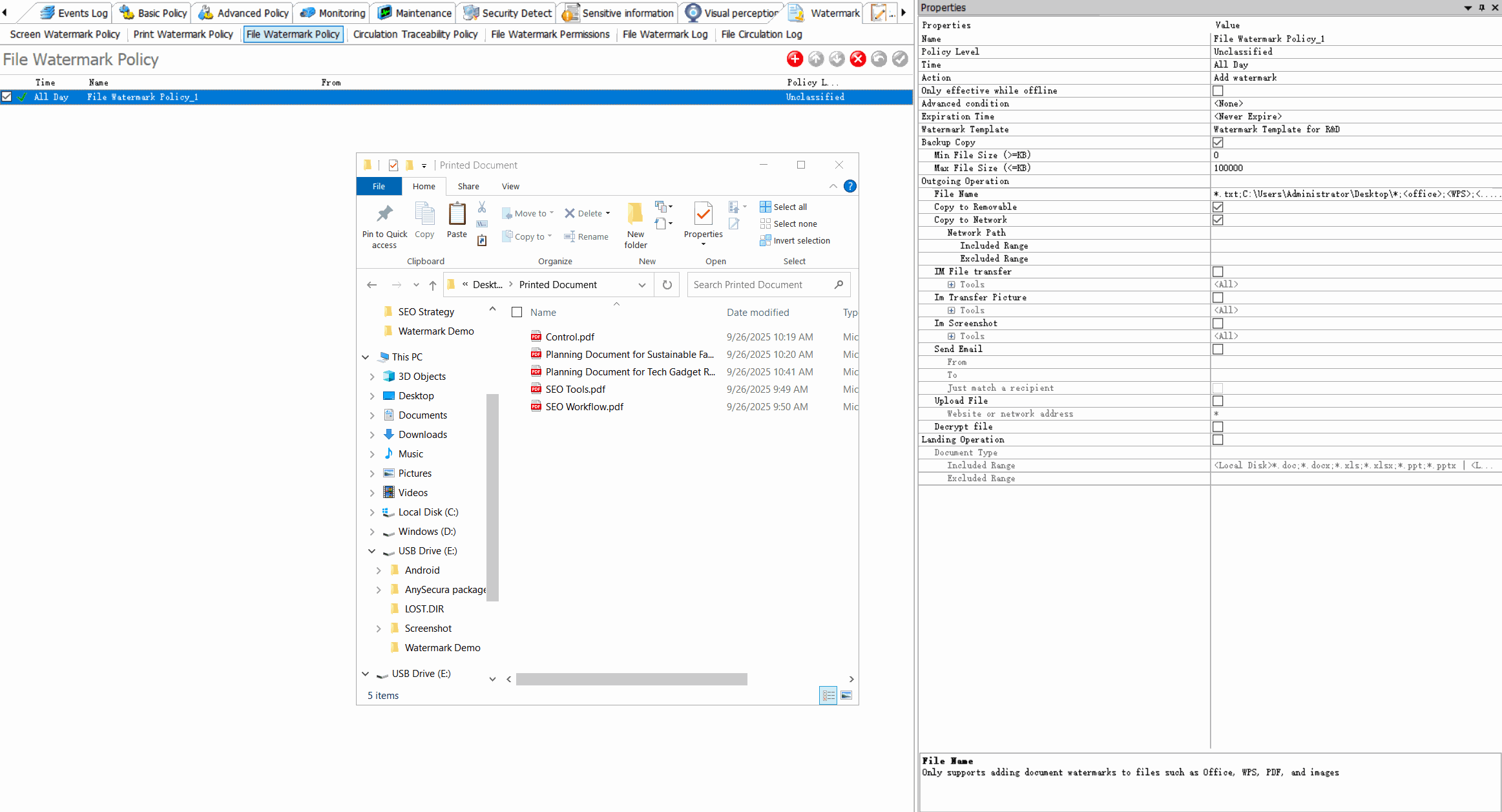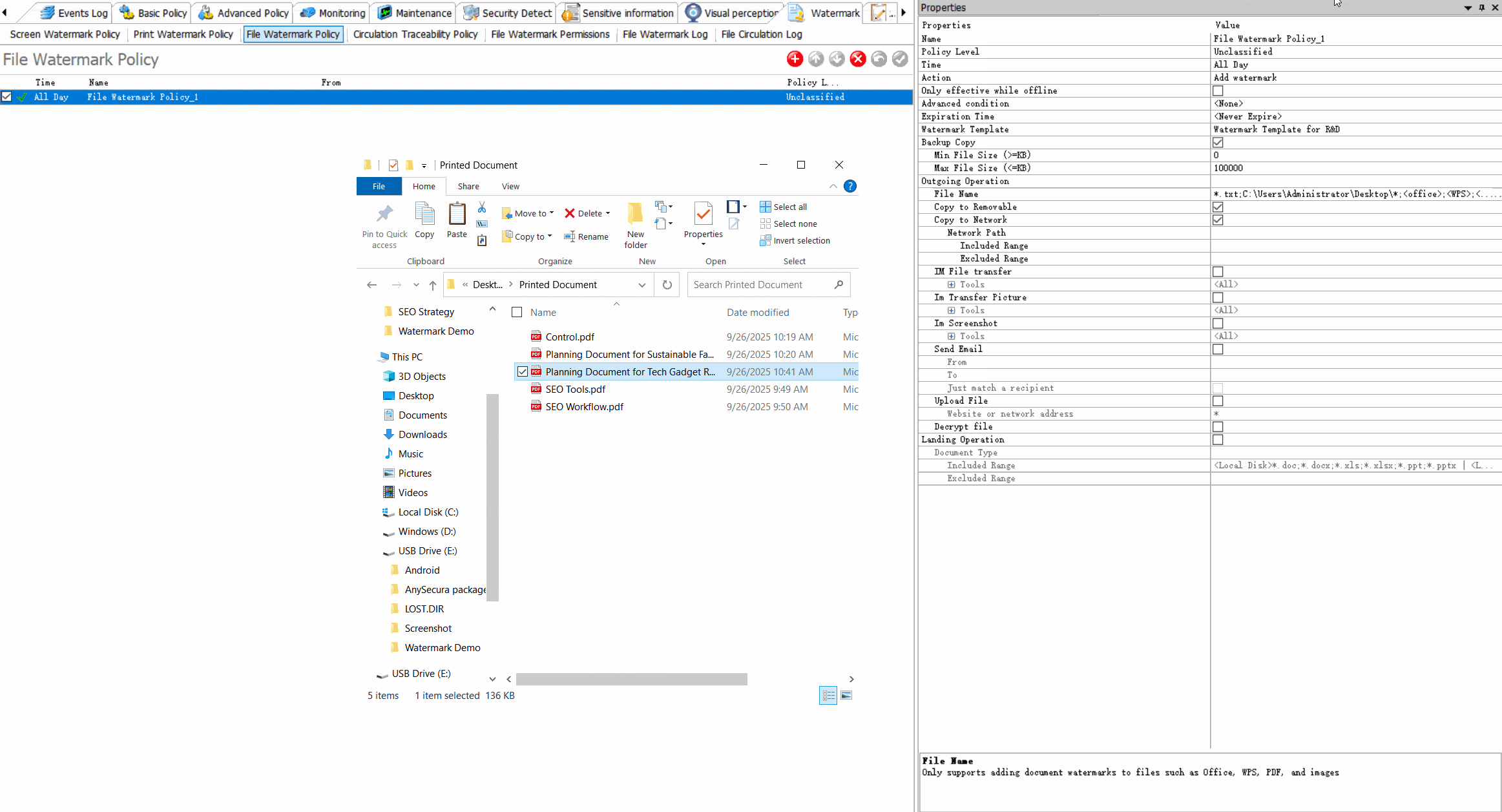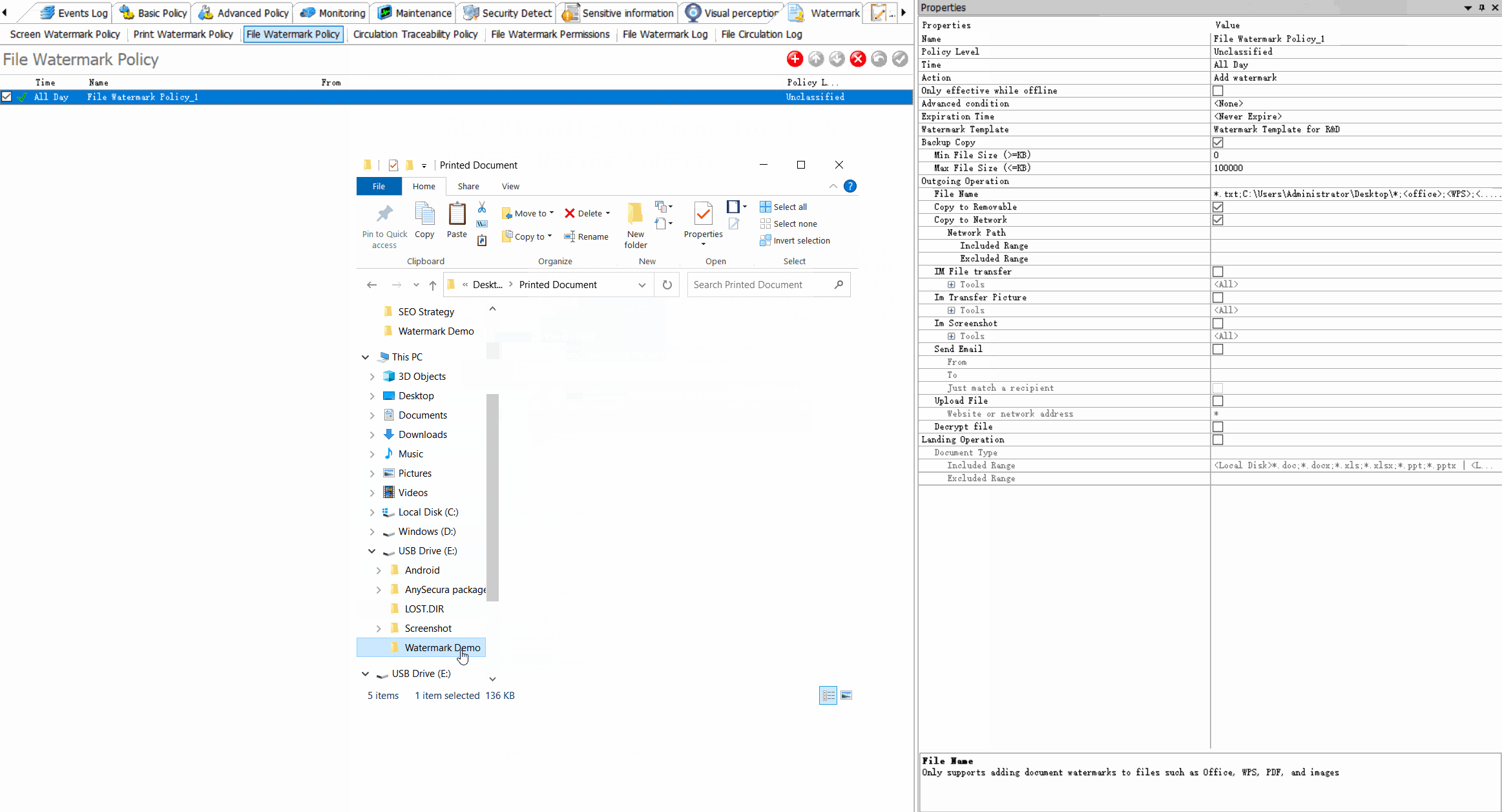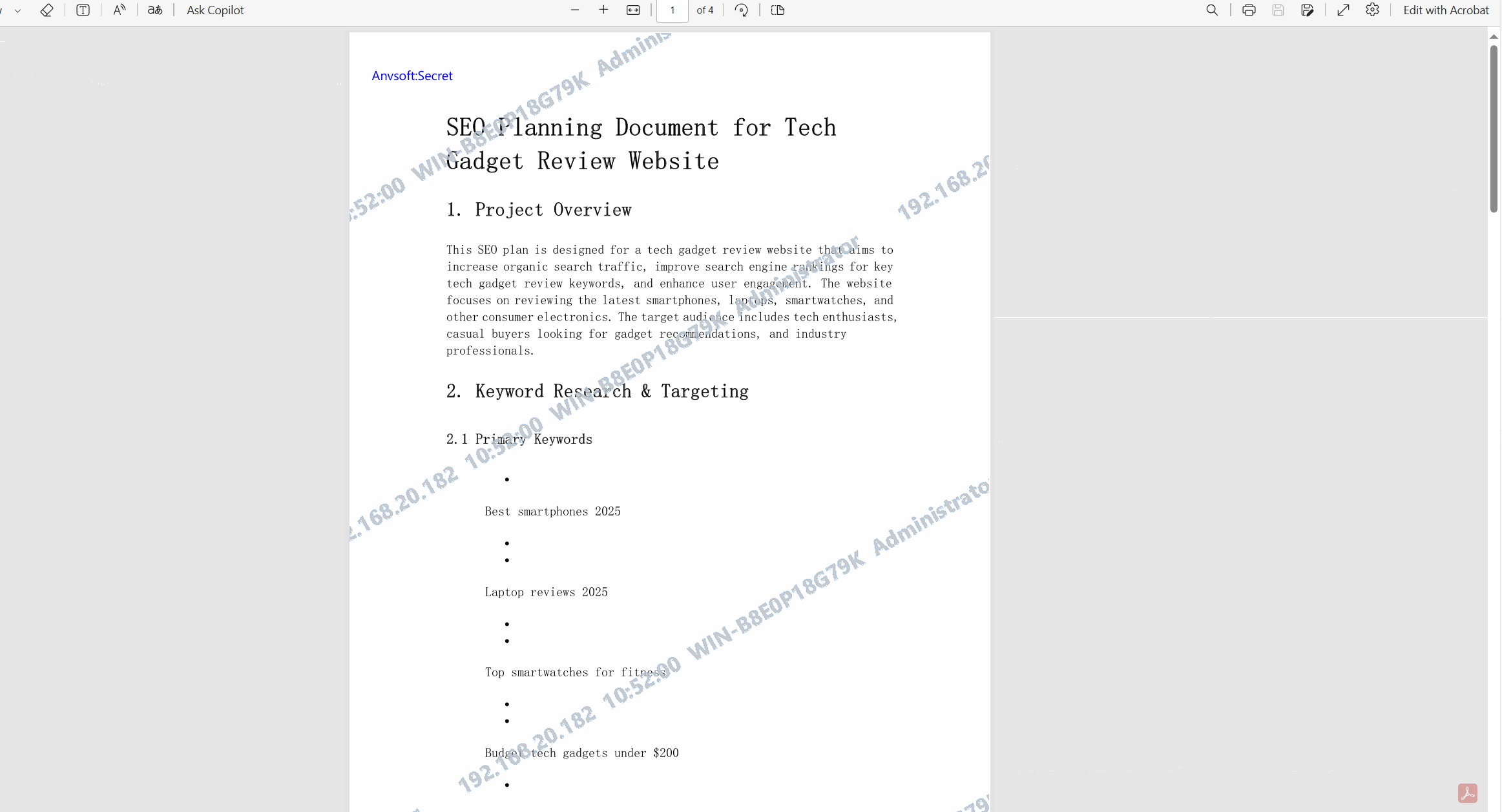
Dynamic WatermarkingApply visible/invisible watermarks containing user information, timestamps, or custom text to printed documents.
-
Print Policy EnforcementRestrict printing of sensitive documents, limit color printing, or require manager approval for large print jobs.
-
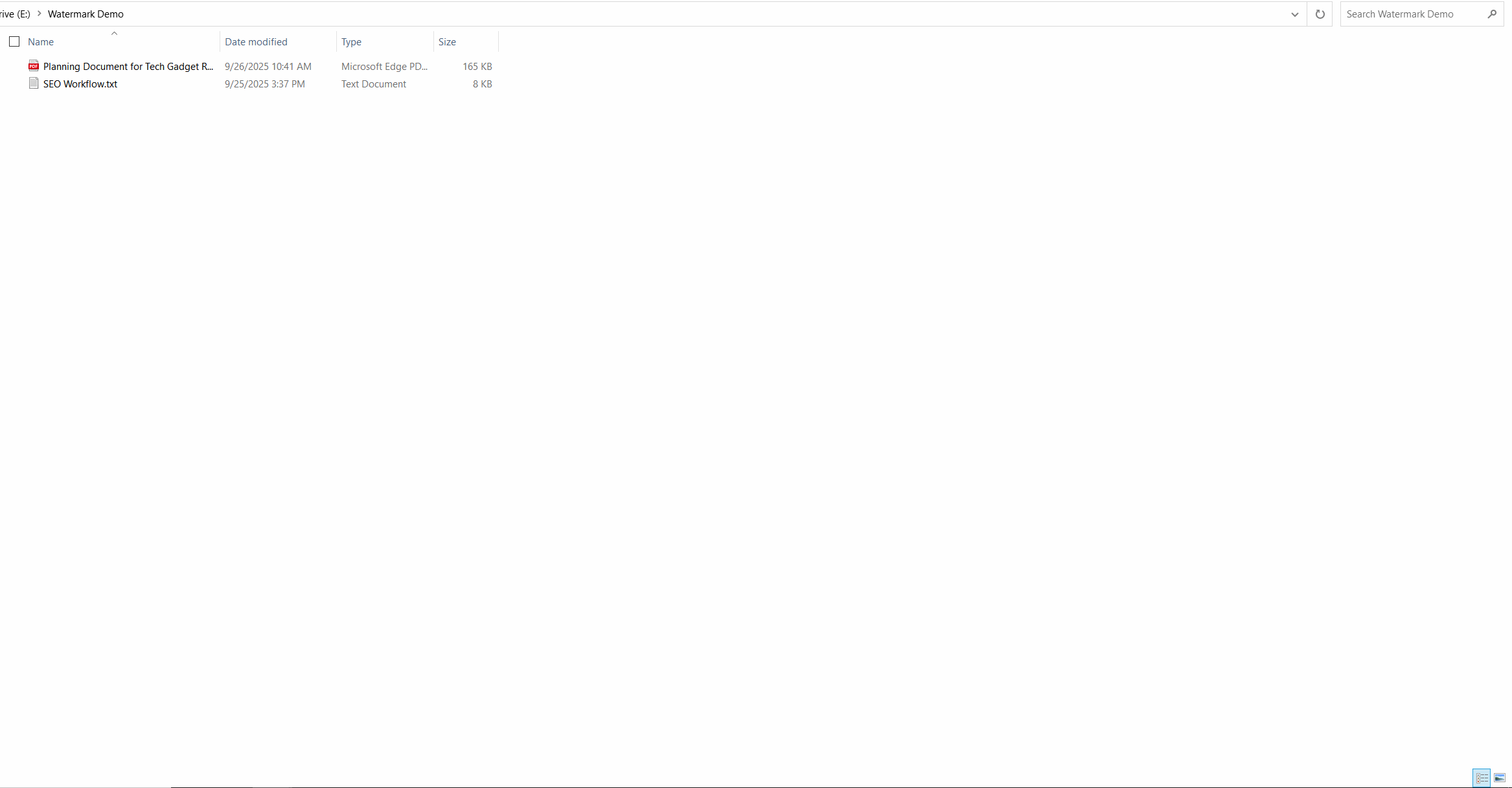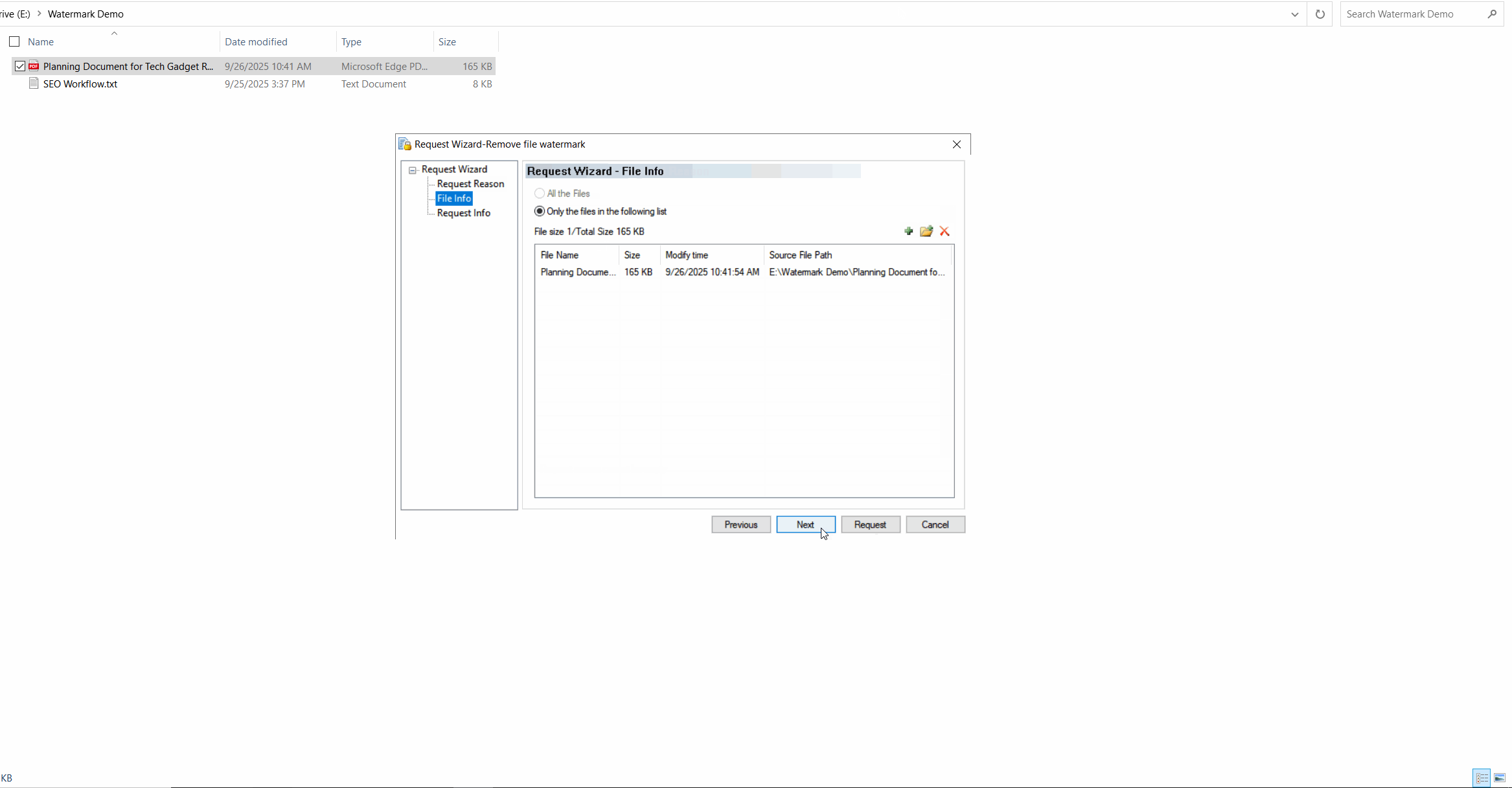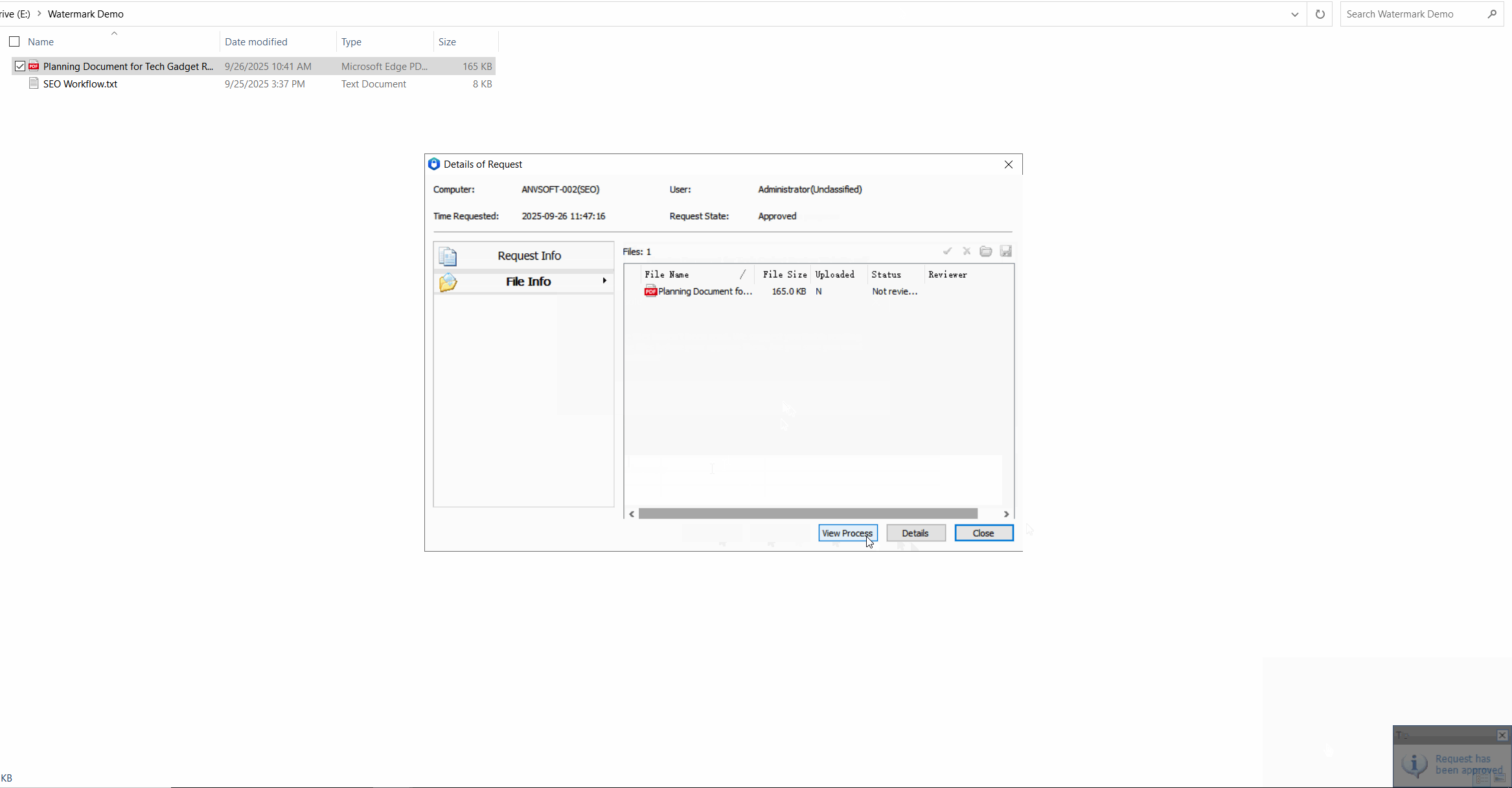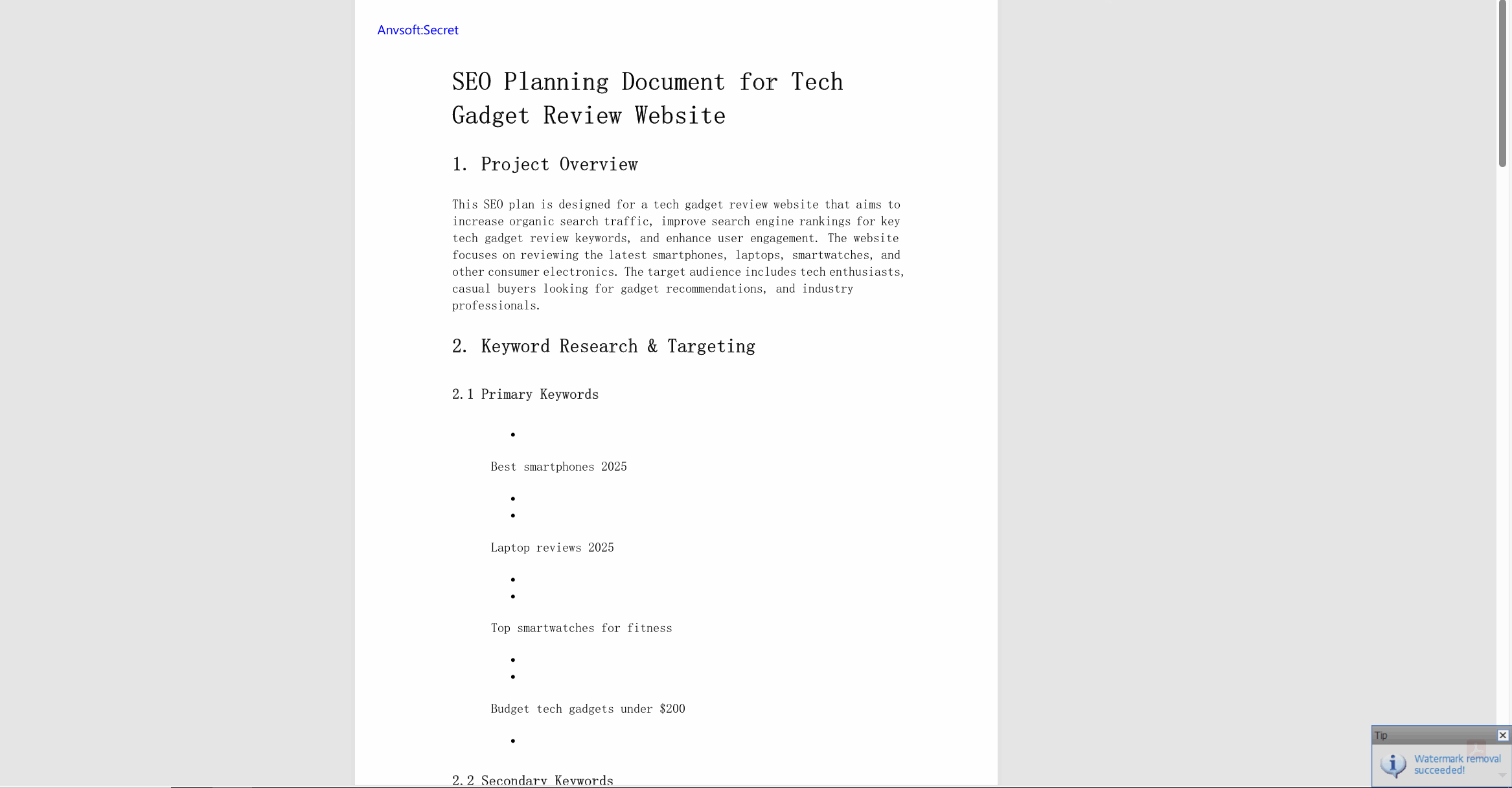
Request for Watermark RemovalEnable users to request watermark removal from administrators in specific scenarios.
Benefits of Print Control
Reduce information leakage through printed documents, lower operational costs by optimizing print usage, and maintain compliance with document distribution policies.
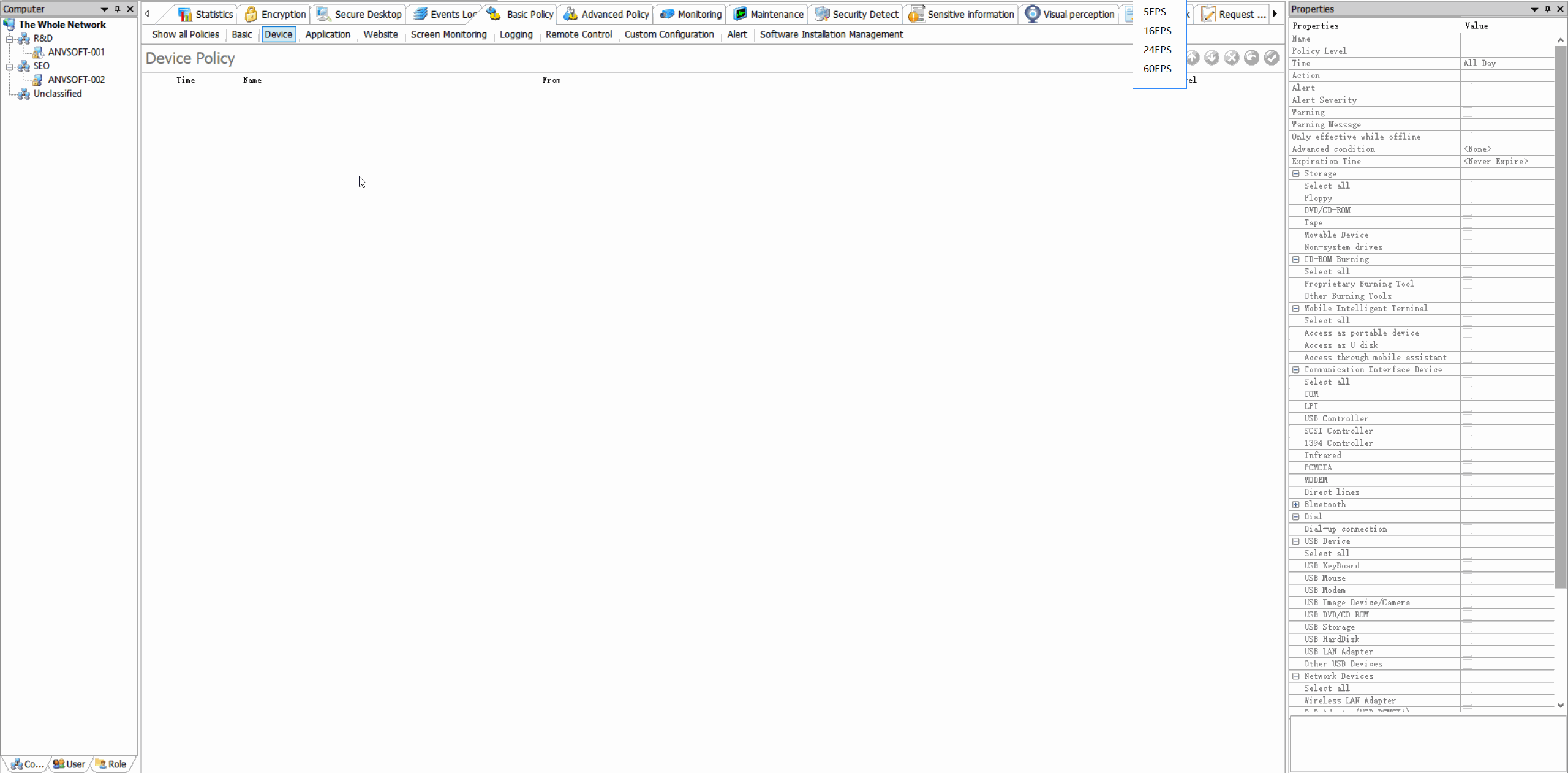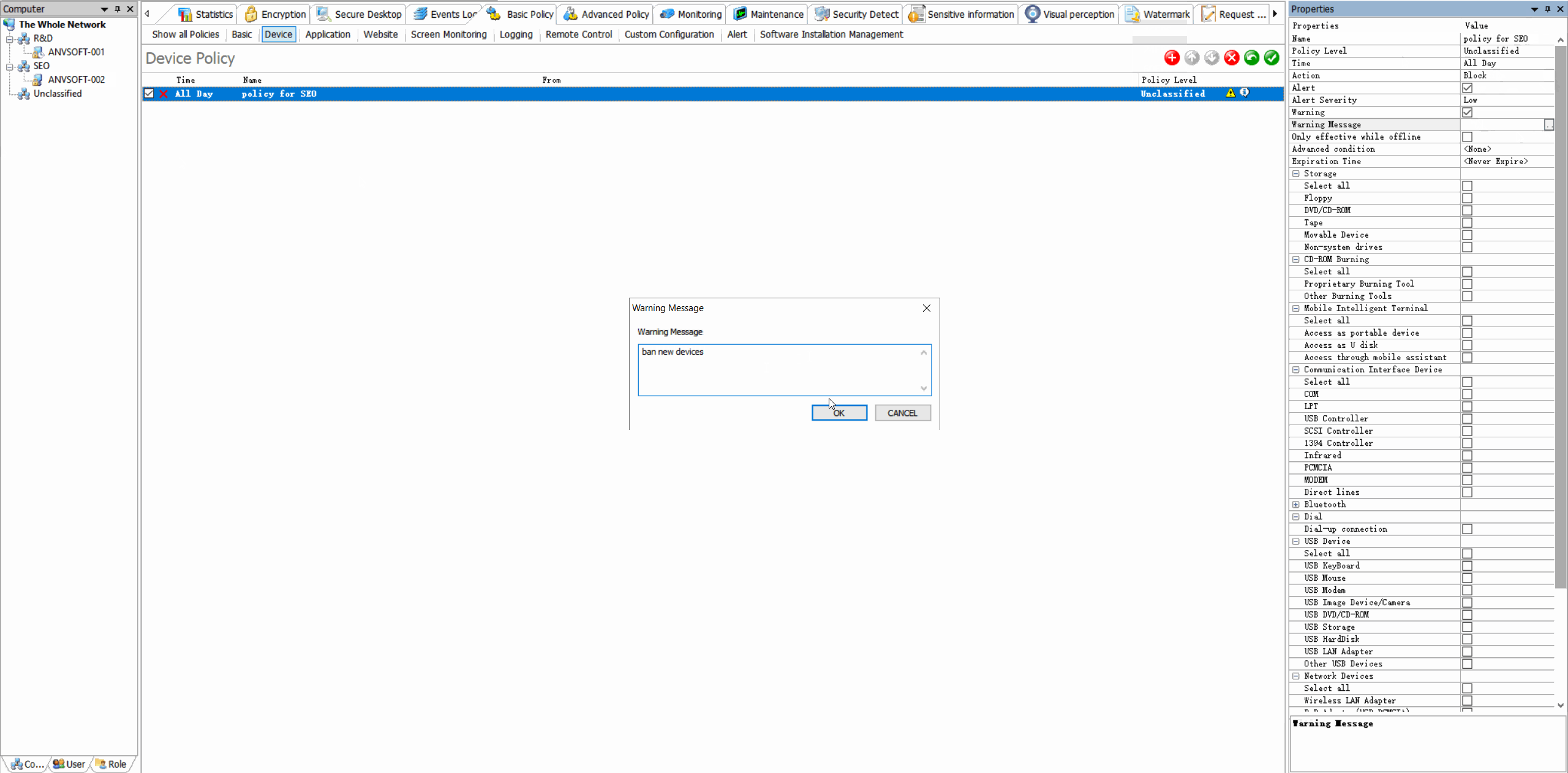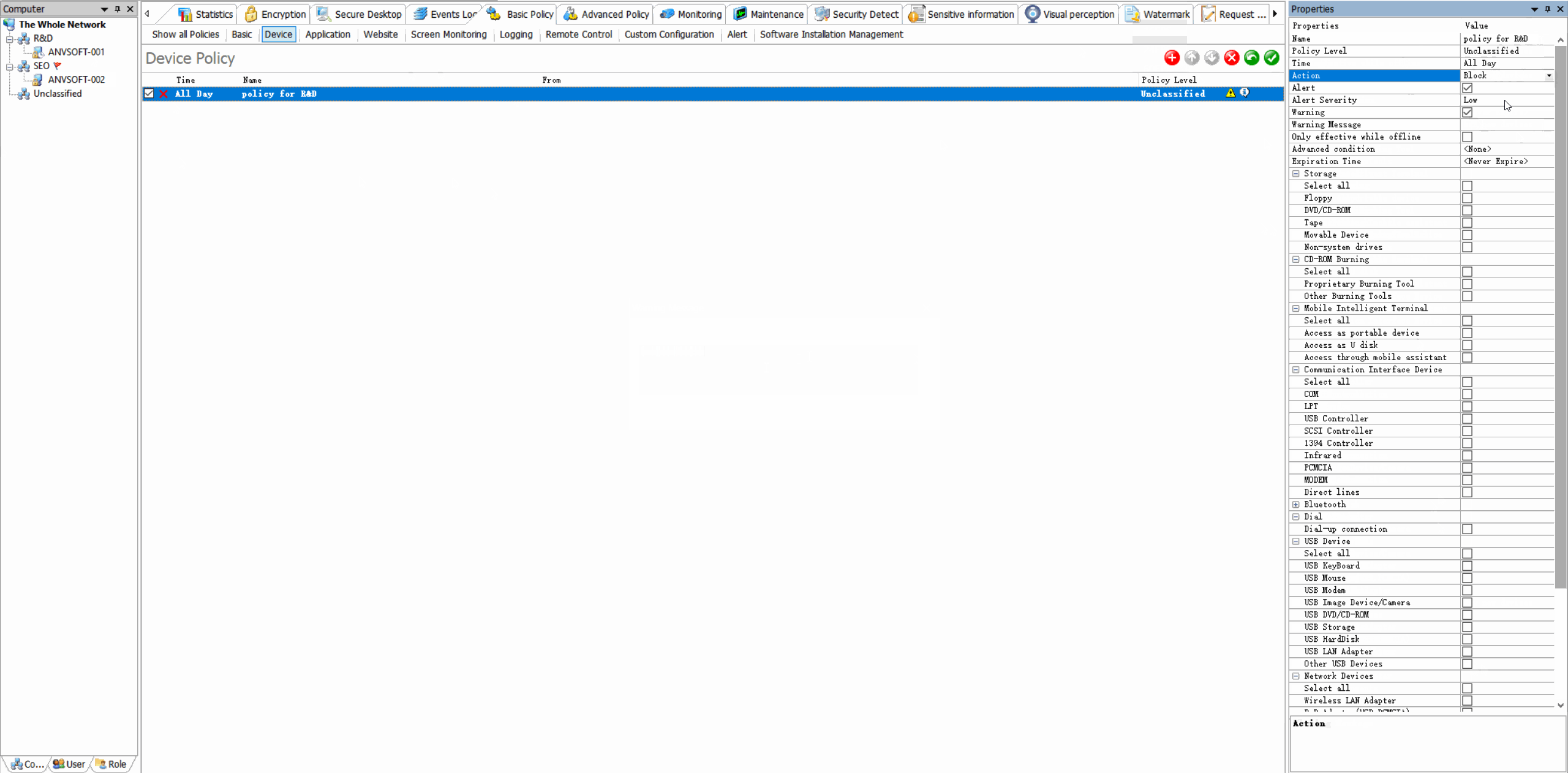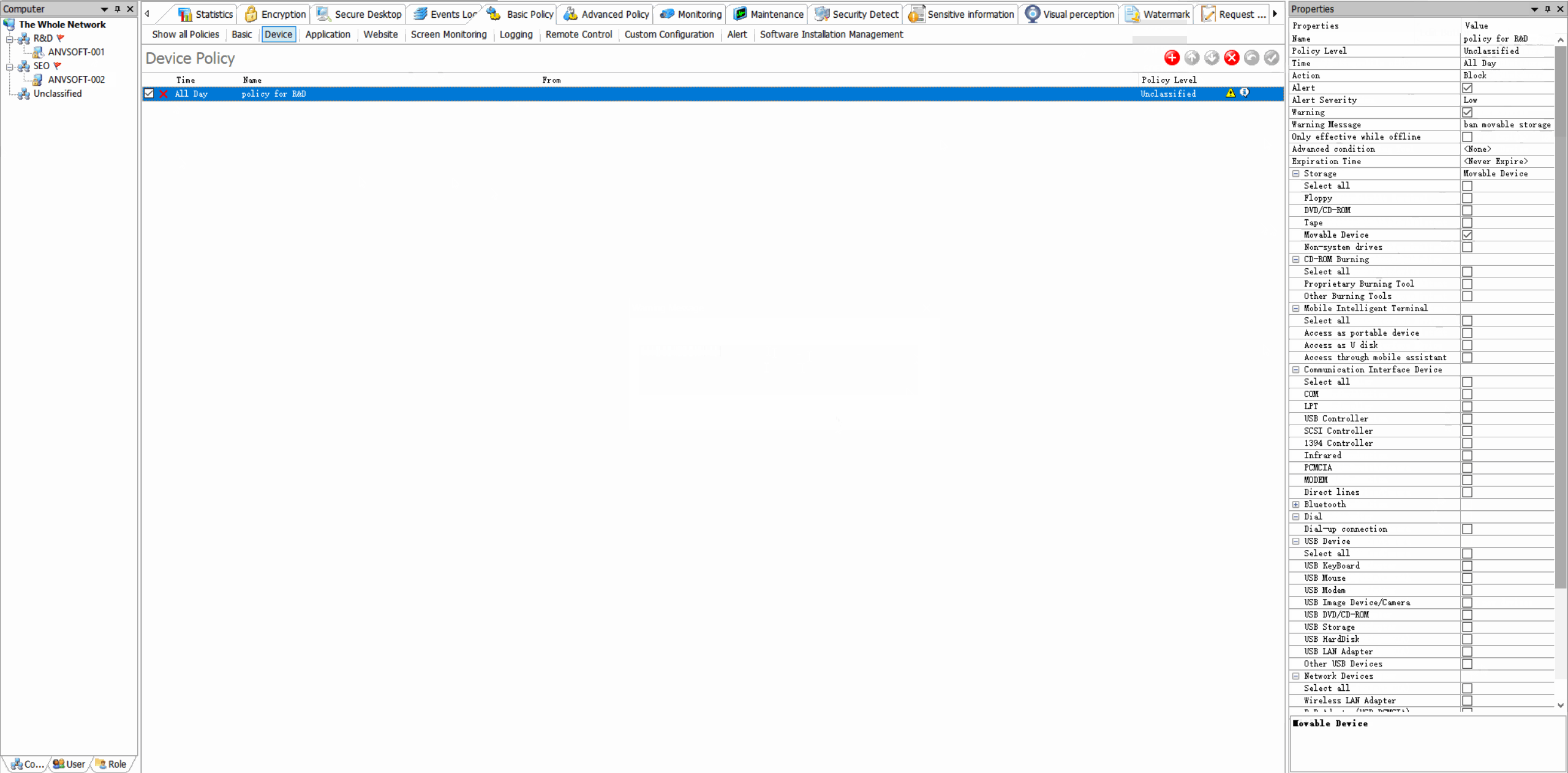
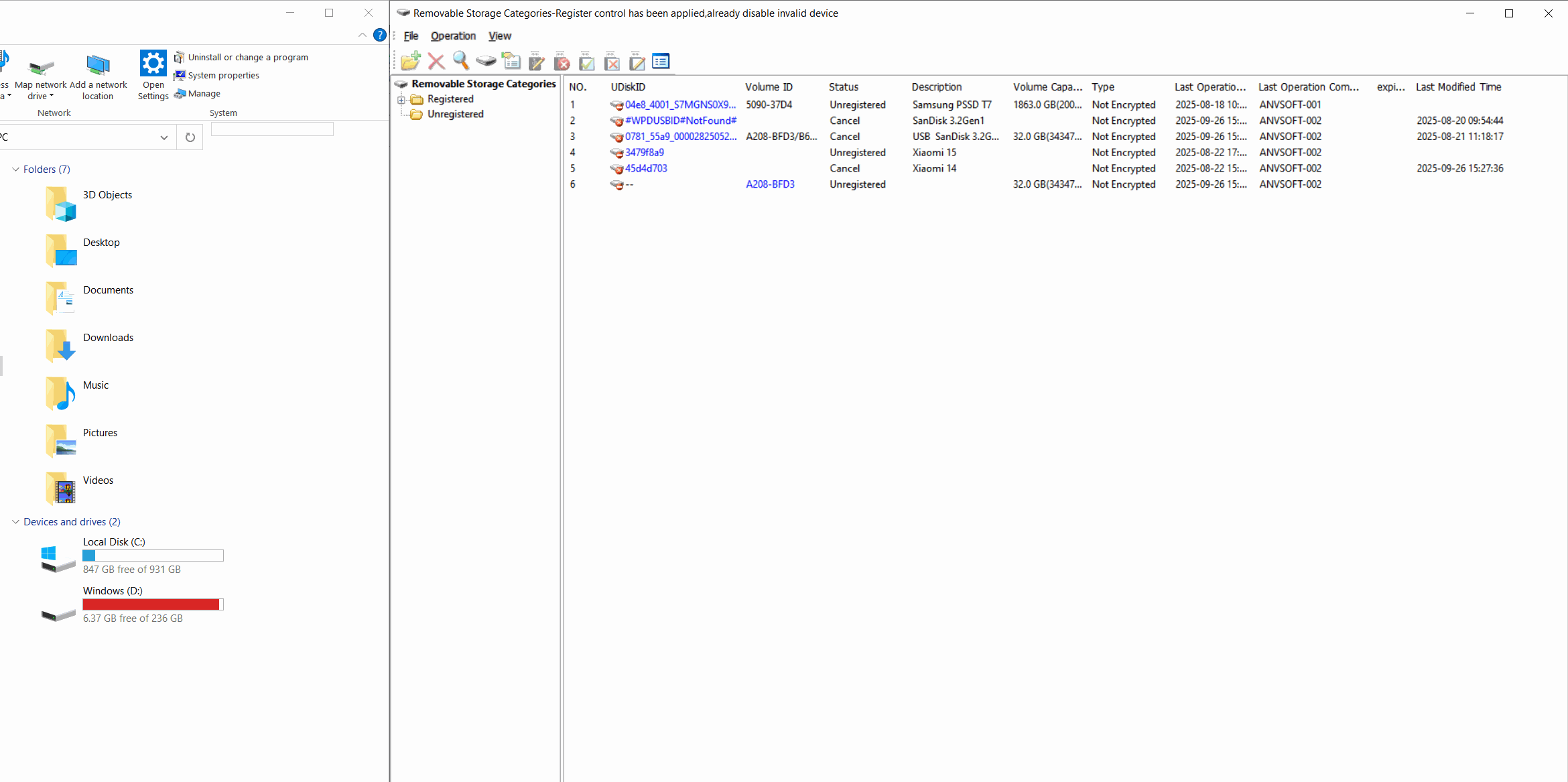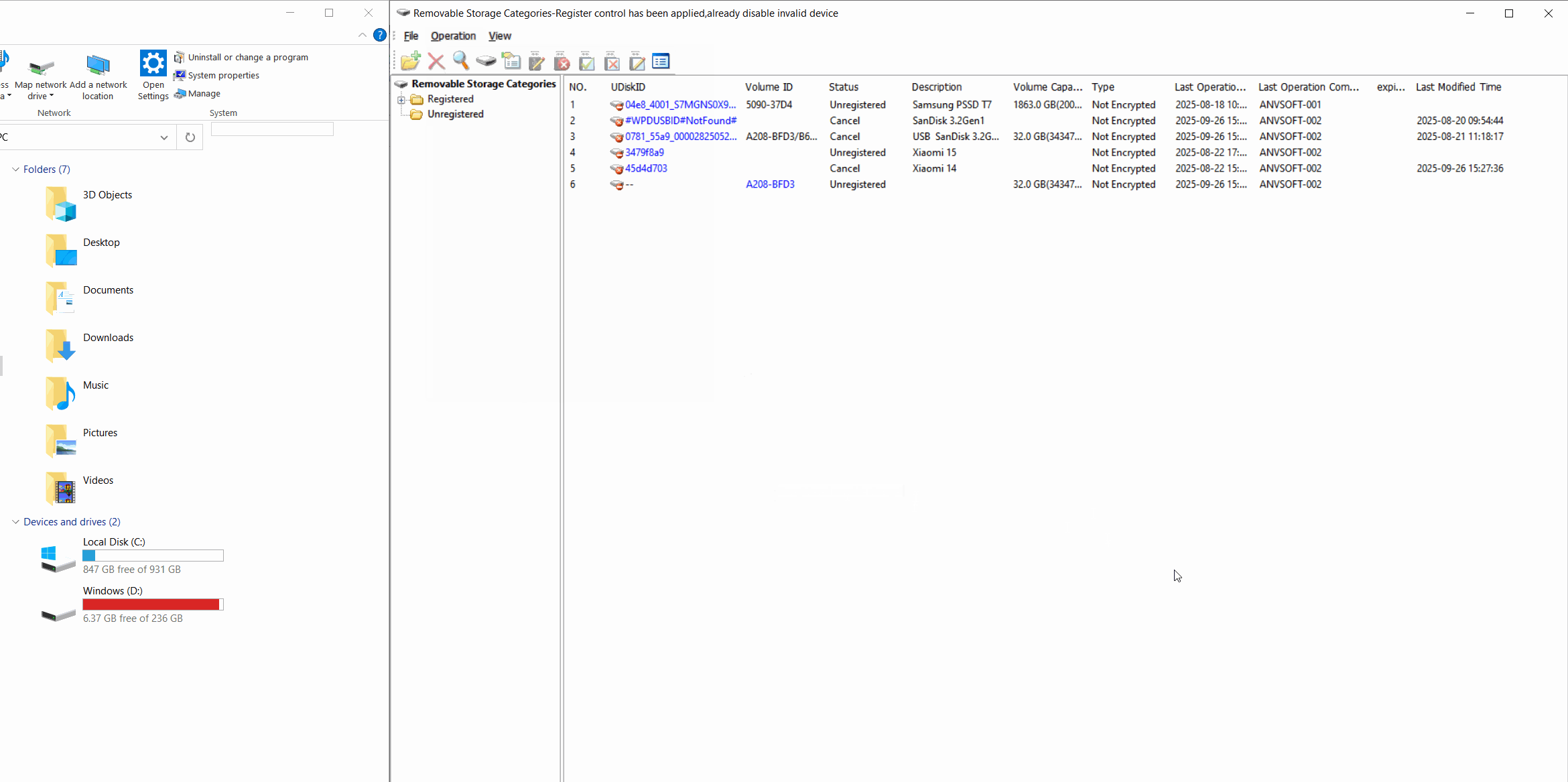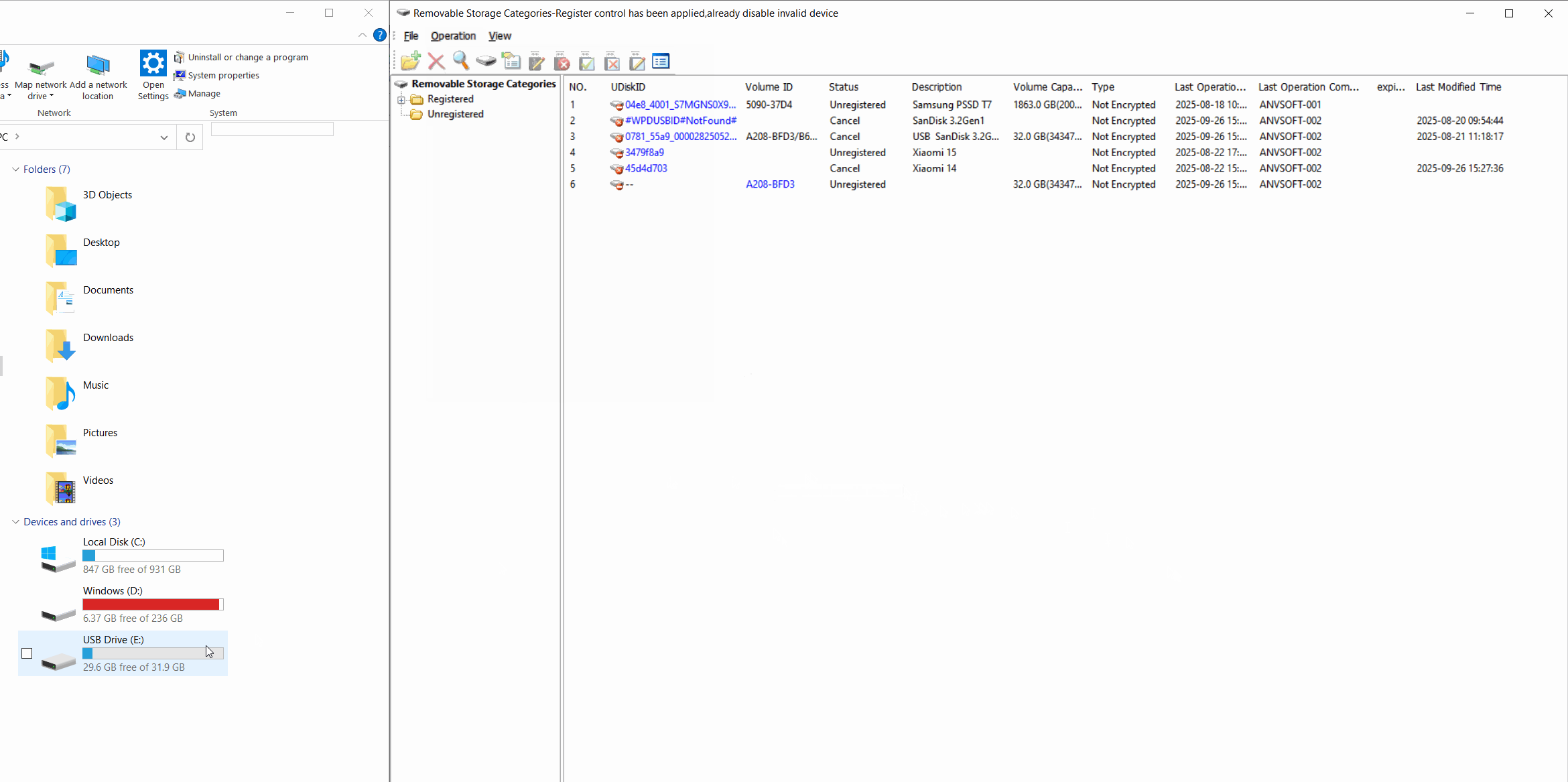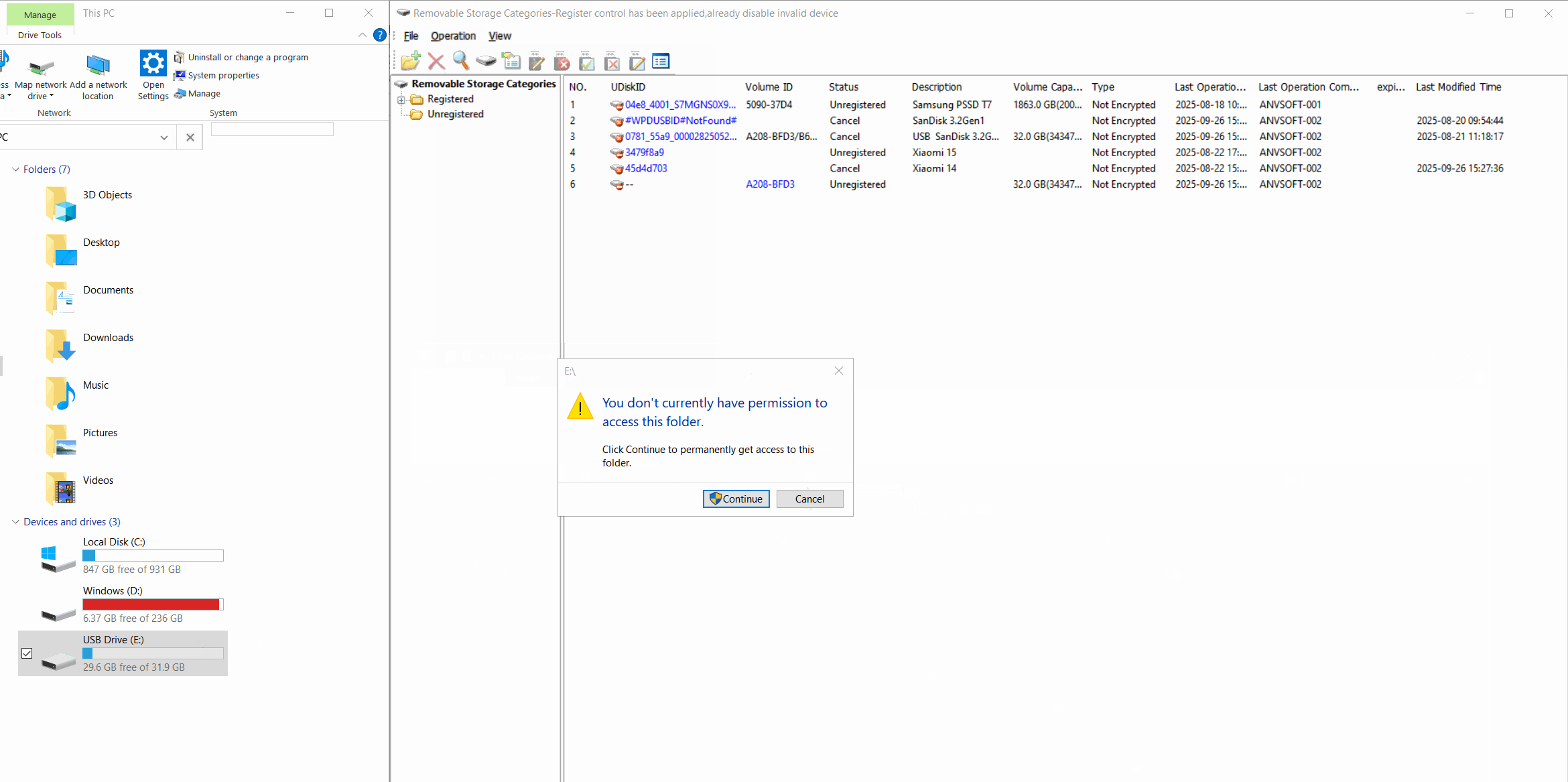
Device Control: Manage Peripheral Access
-
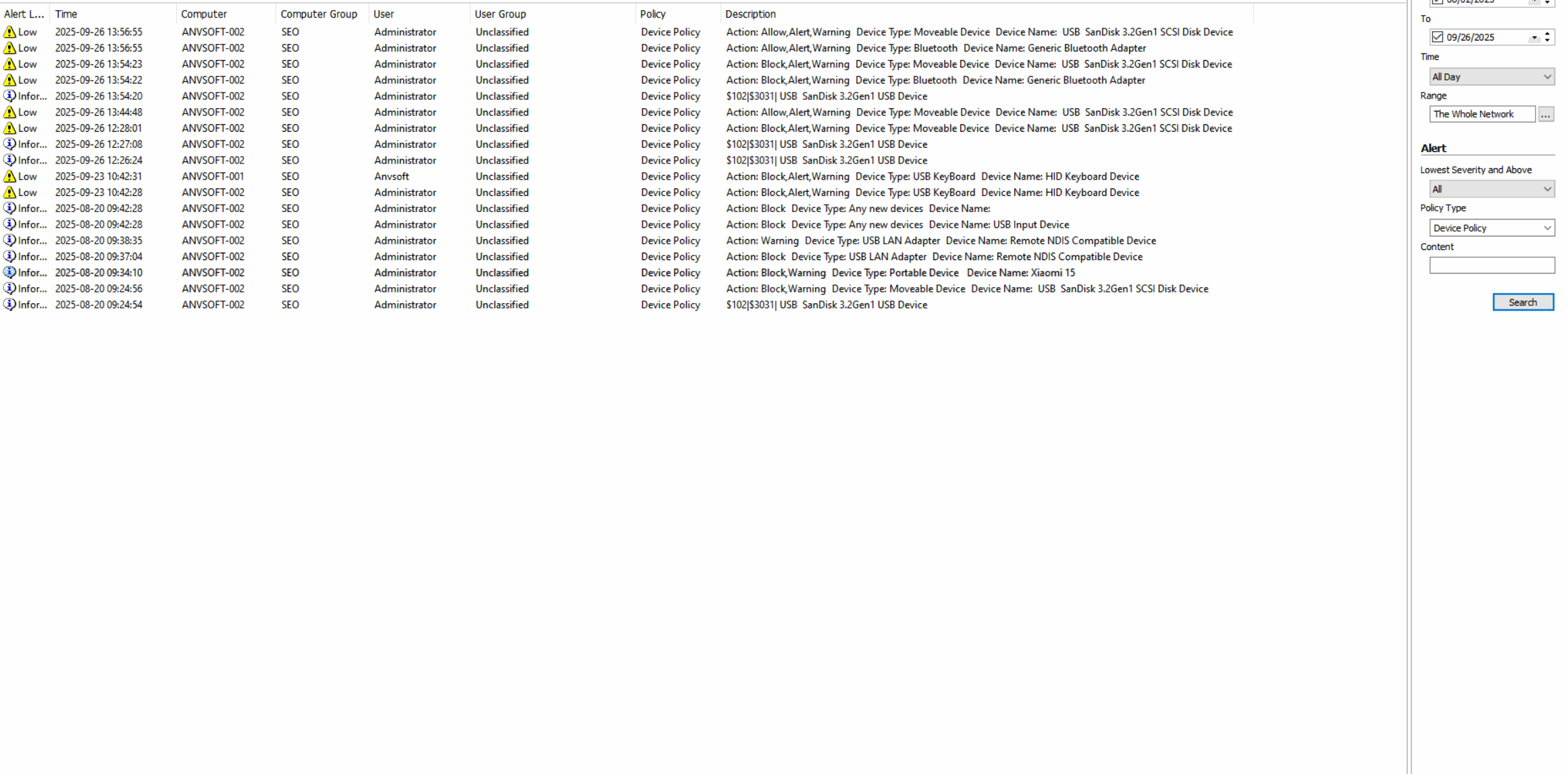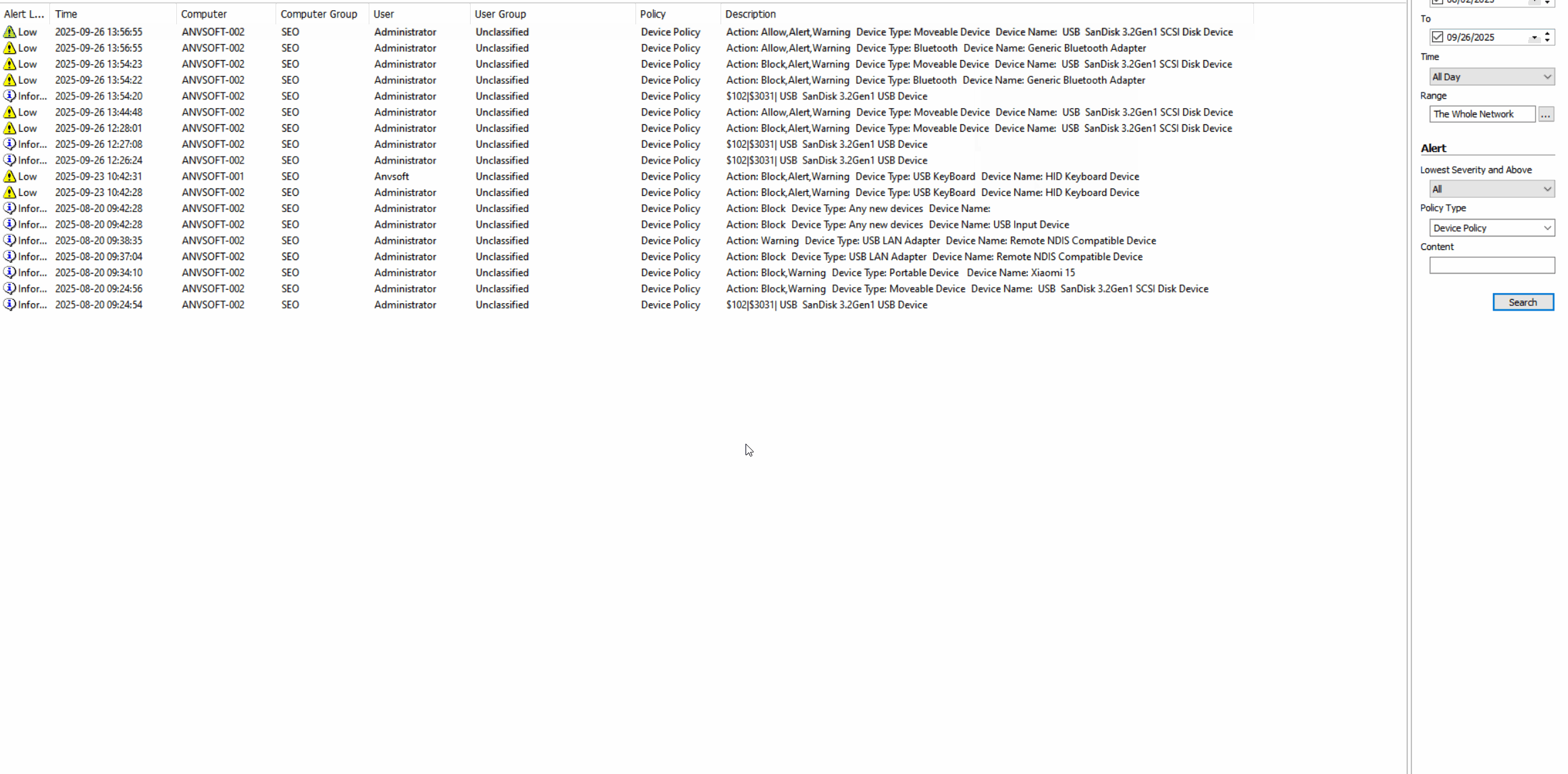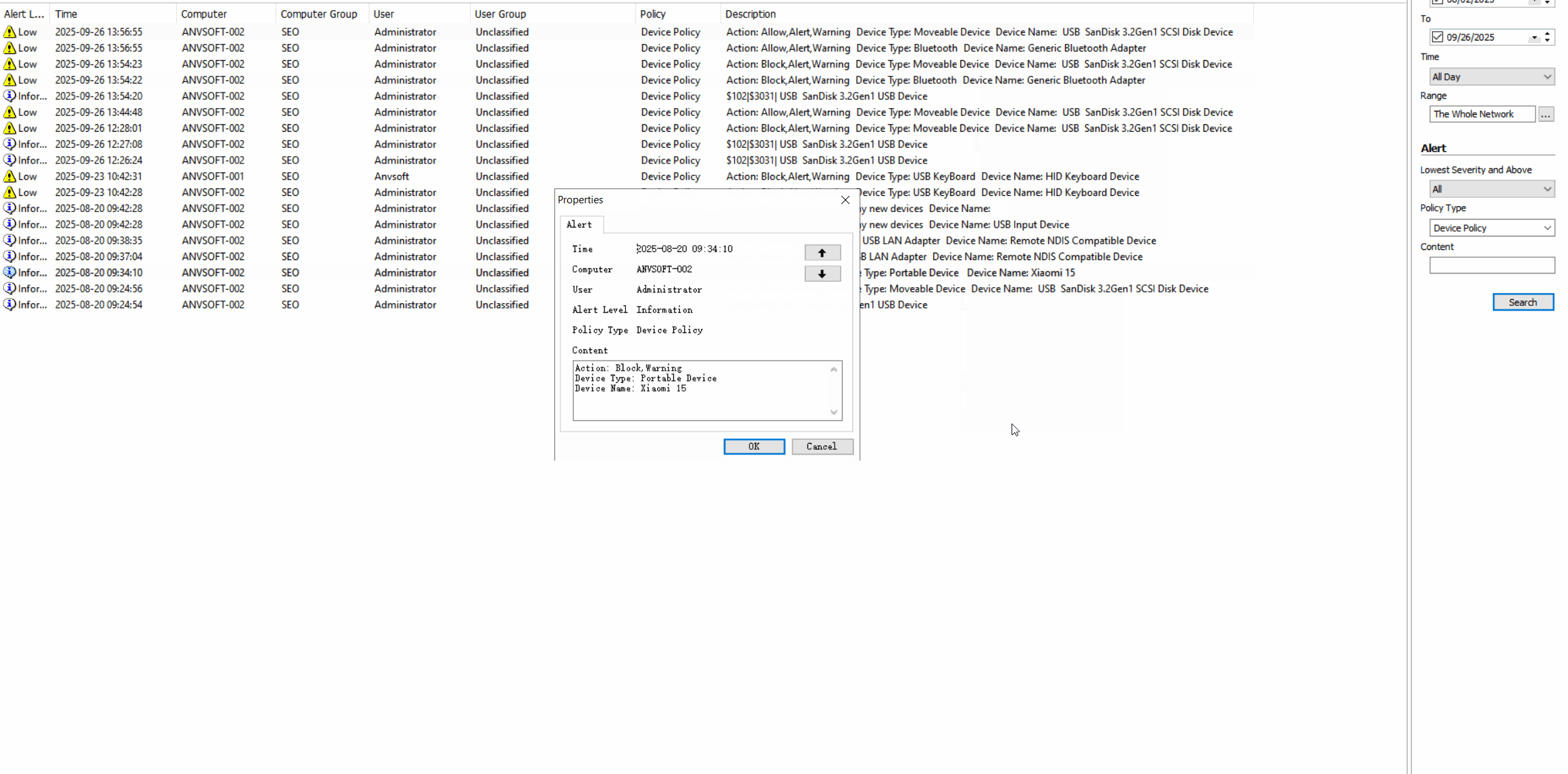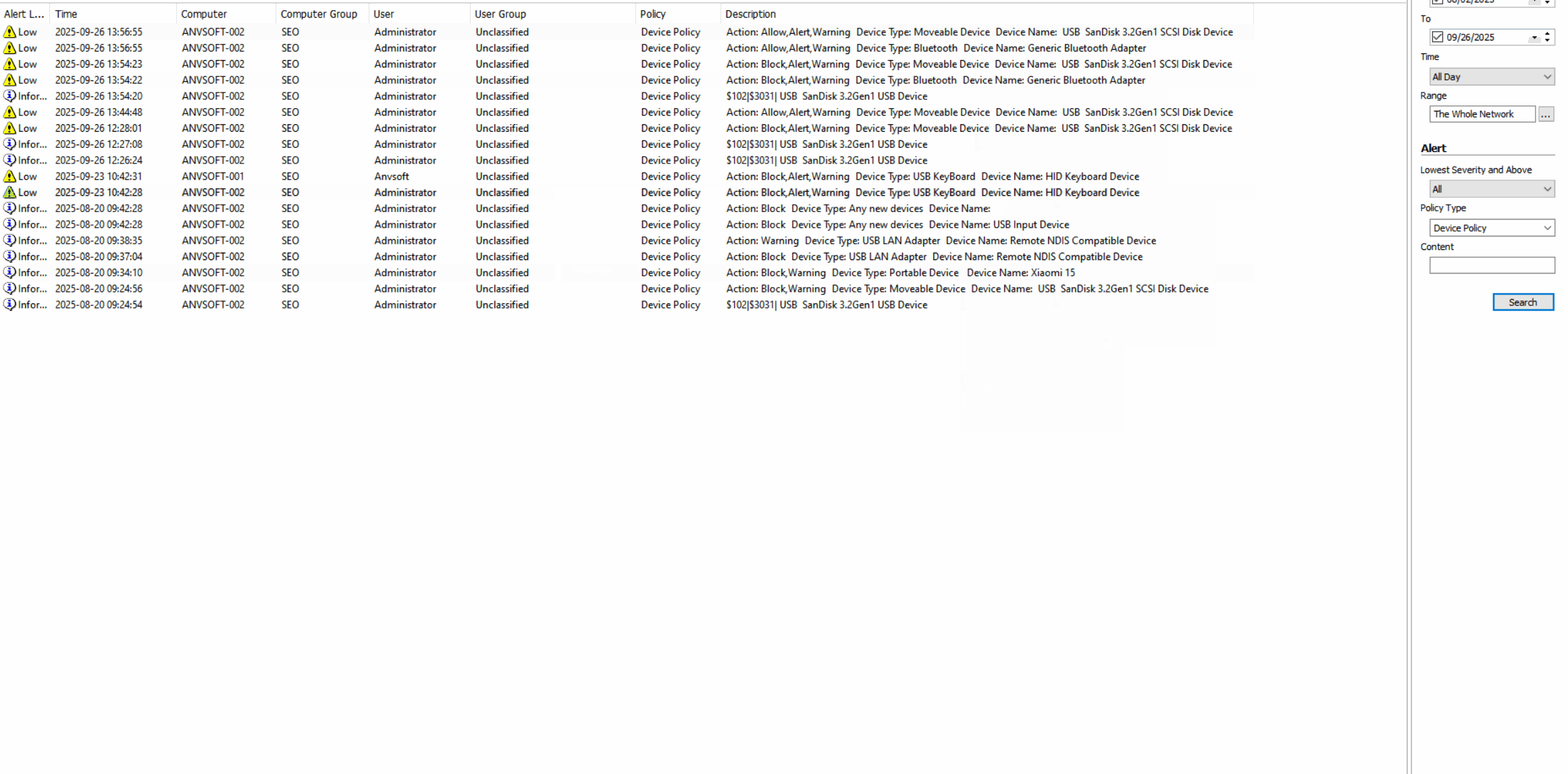
Device Activity LogsMonitor all connected devices (USB drives, keyboards,mouses,Bluetooth devices,etc) with connection/disconnection timestamps.
-
Granular Device PoliciesAllow/block specific device types based on device ID, user role, or department.
-
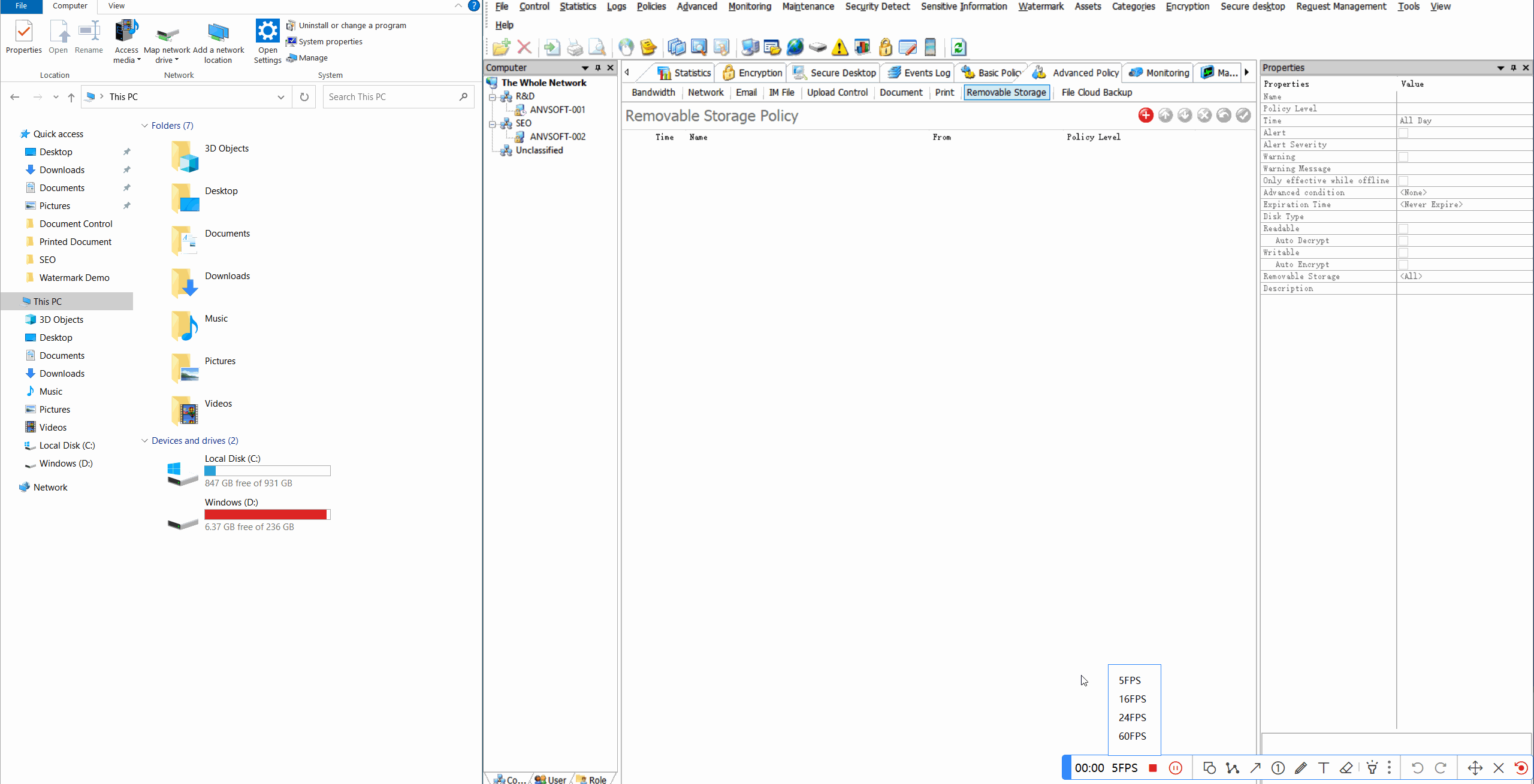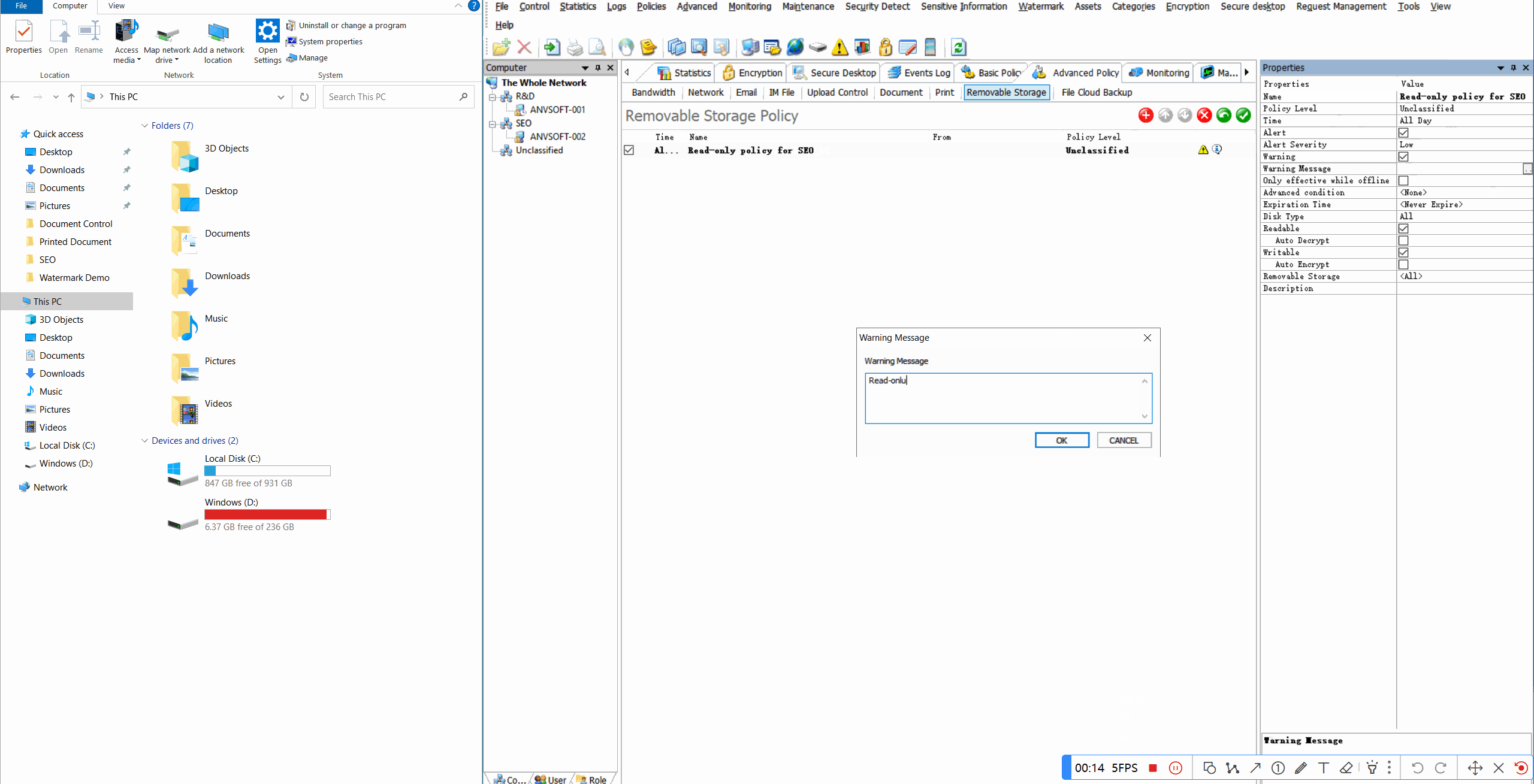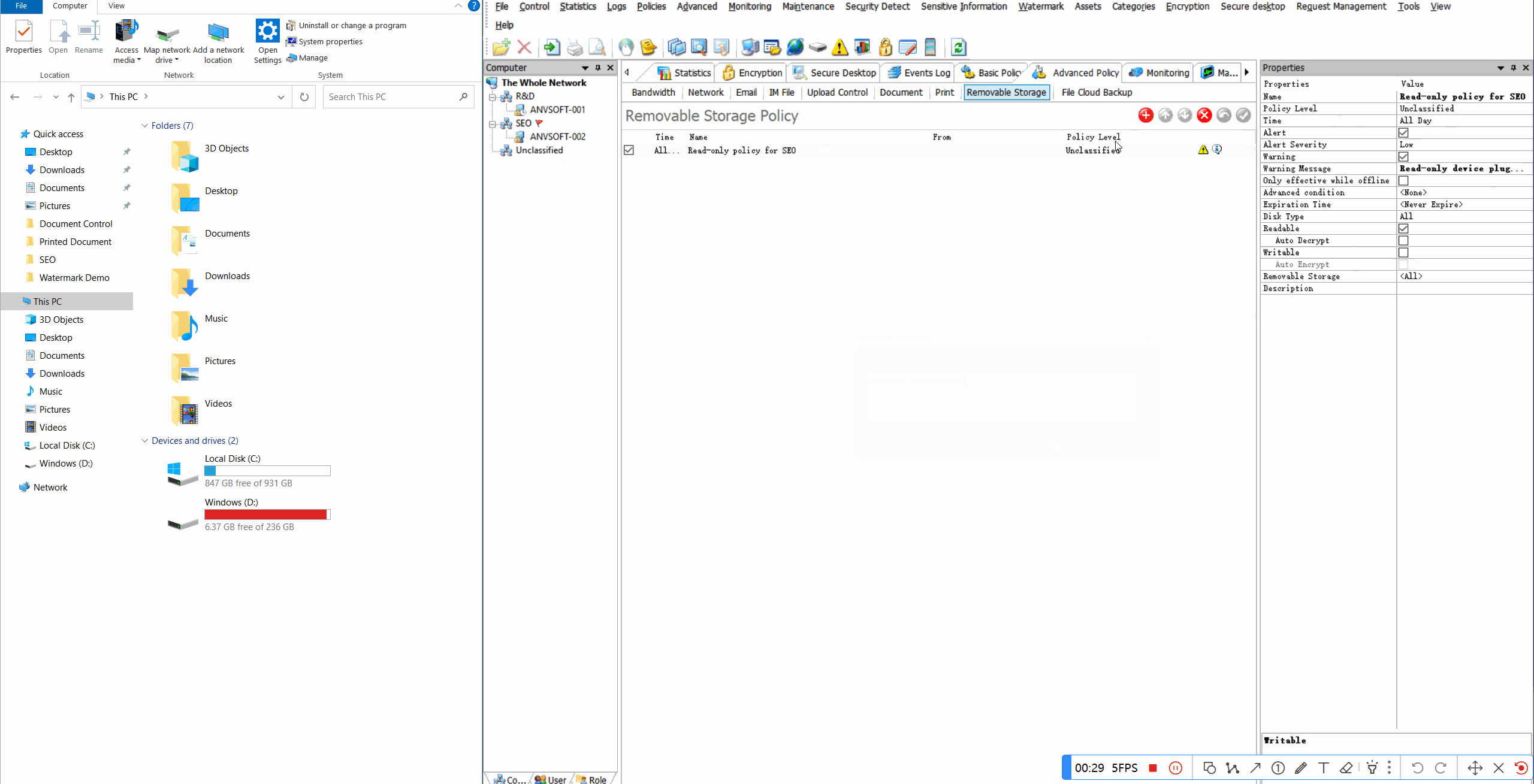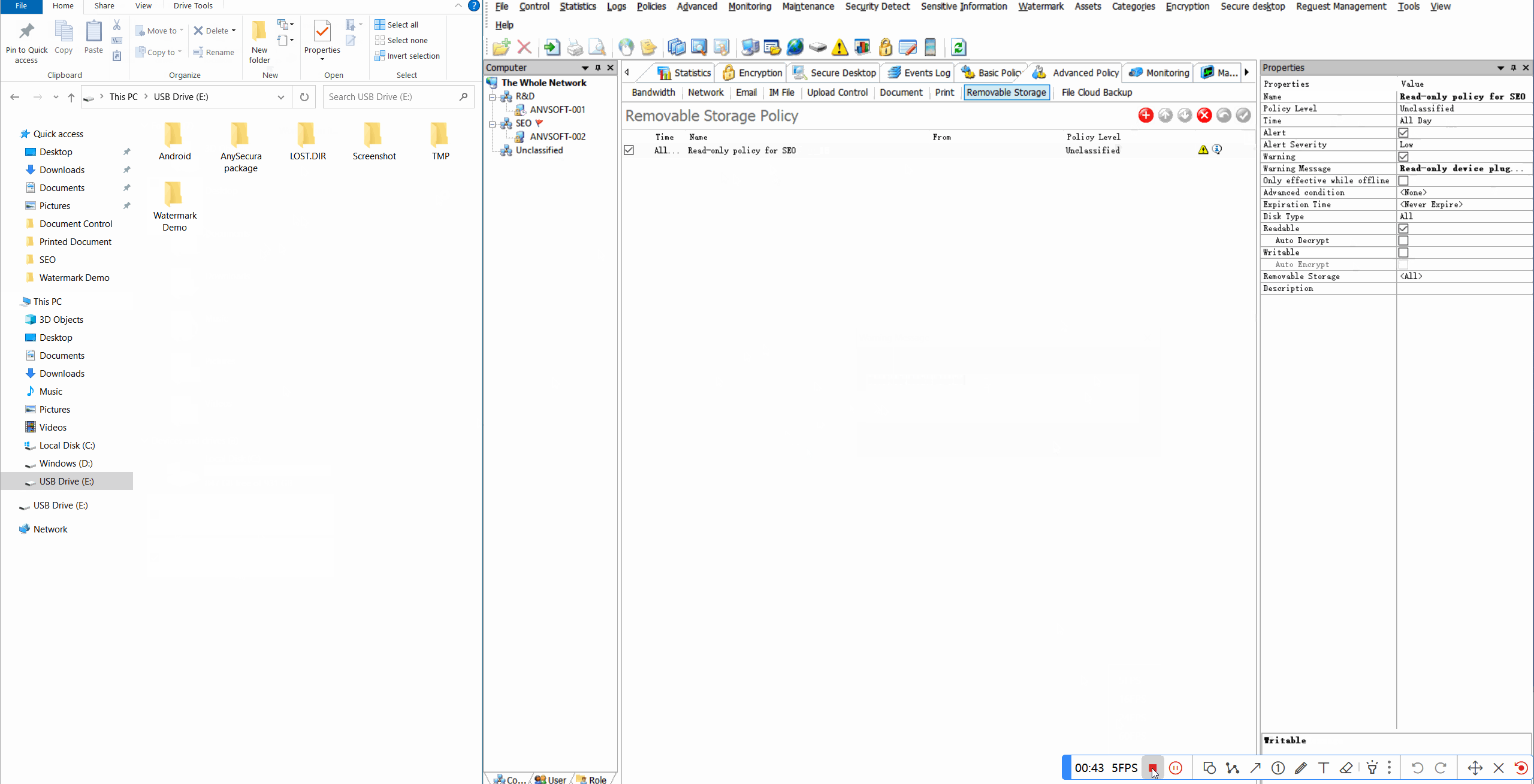
Read-Only RestrictionsConfigure USB storage devices to operate in read-only mode to prevent data copying.
-
Real-time AlertsReceive notifications for unauthorized device connections or suspicious peripheral activities.
Device Control Advantages
Prevent data exfiltration through removable devices, maintain control over peripheral usage, and reduce the risk of malware introduction via external storage.
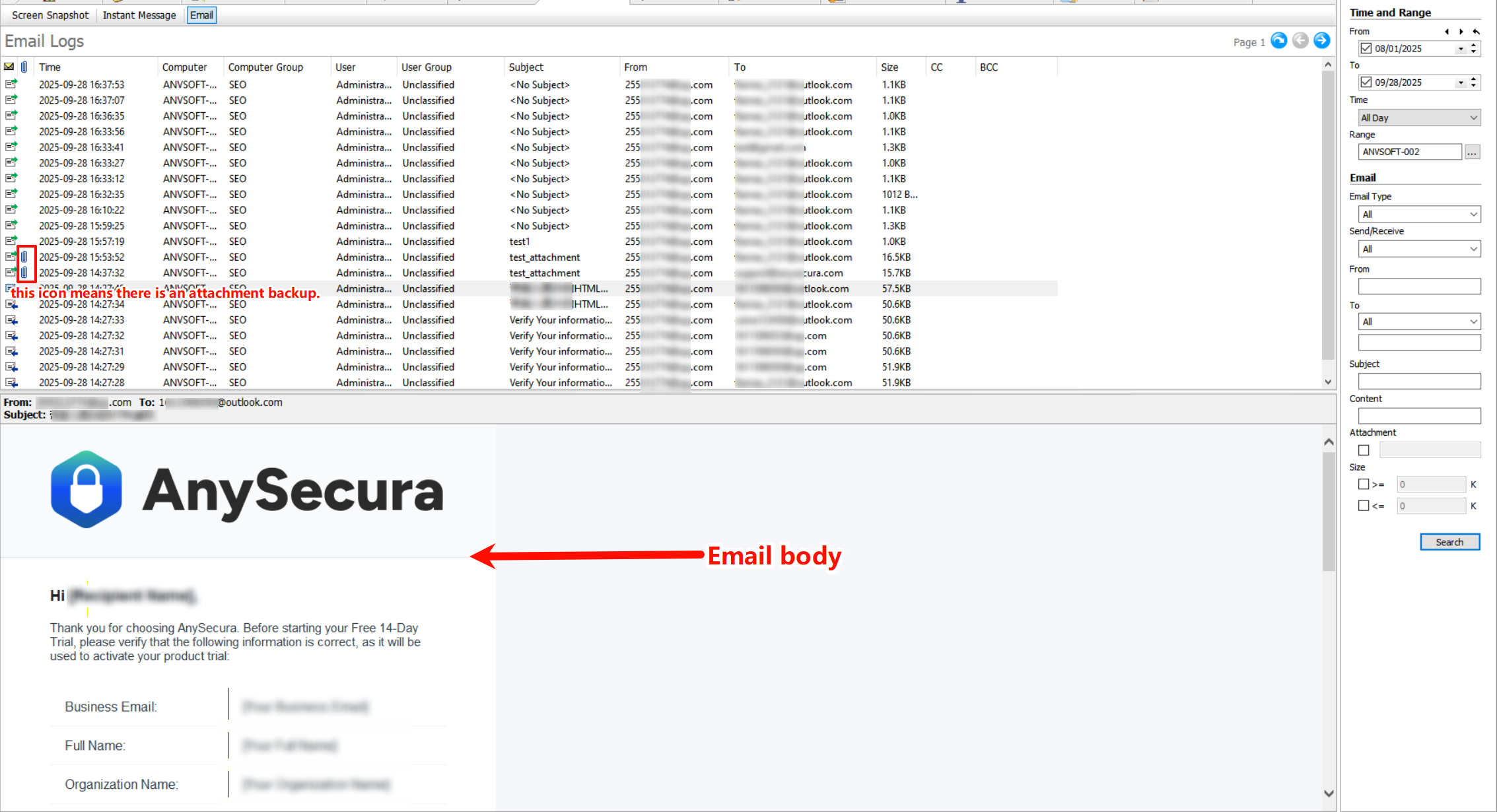
Email Control: Secure External Communication
-
Email Transaction LogsTrack all incoming/outgoing emails with sender/recipient details, timestamps, and attachment information.
-
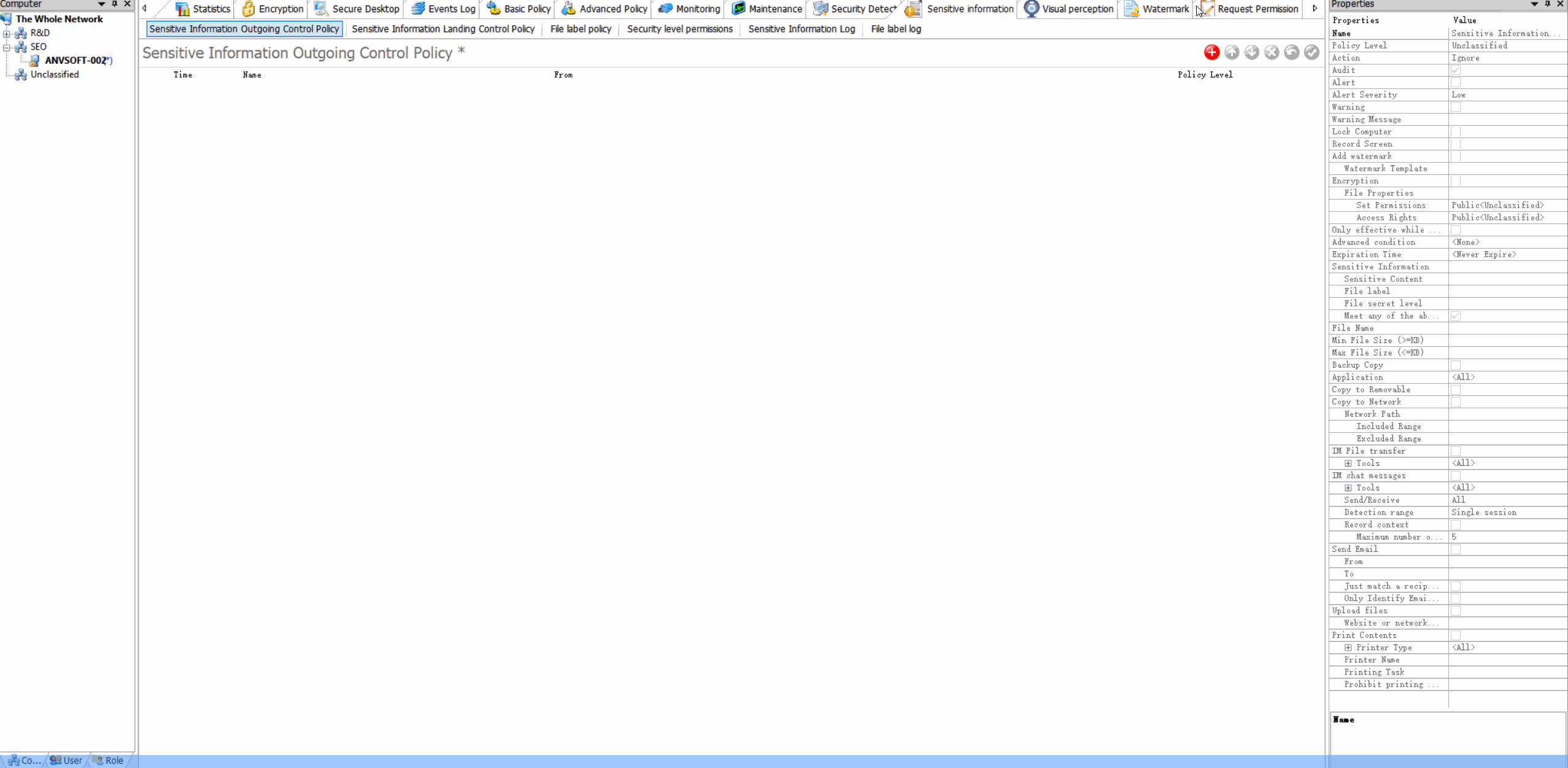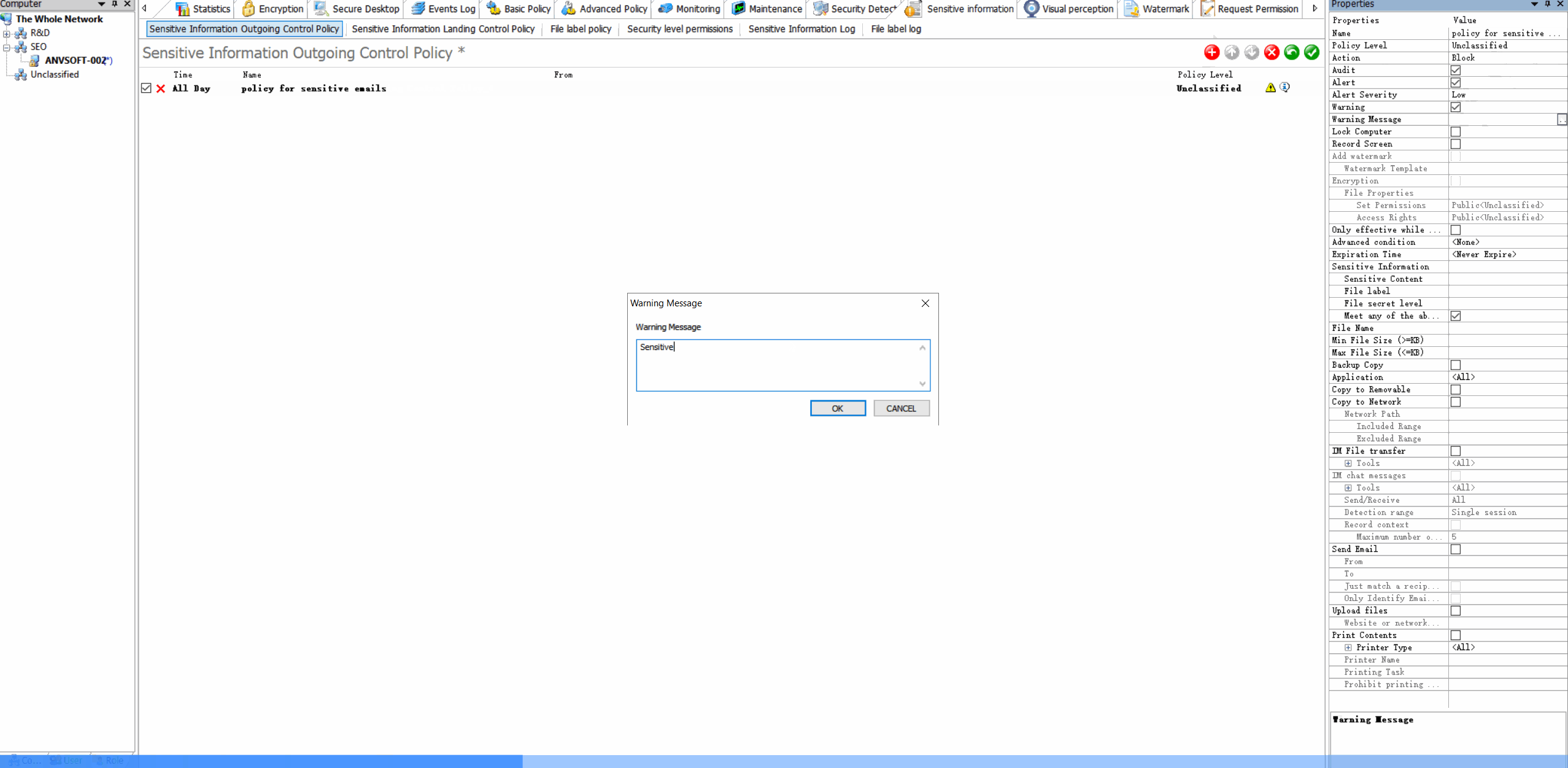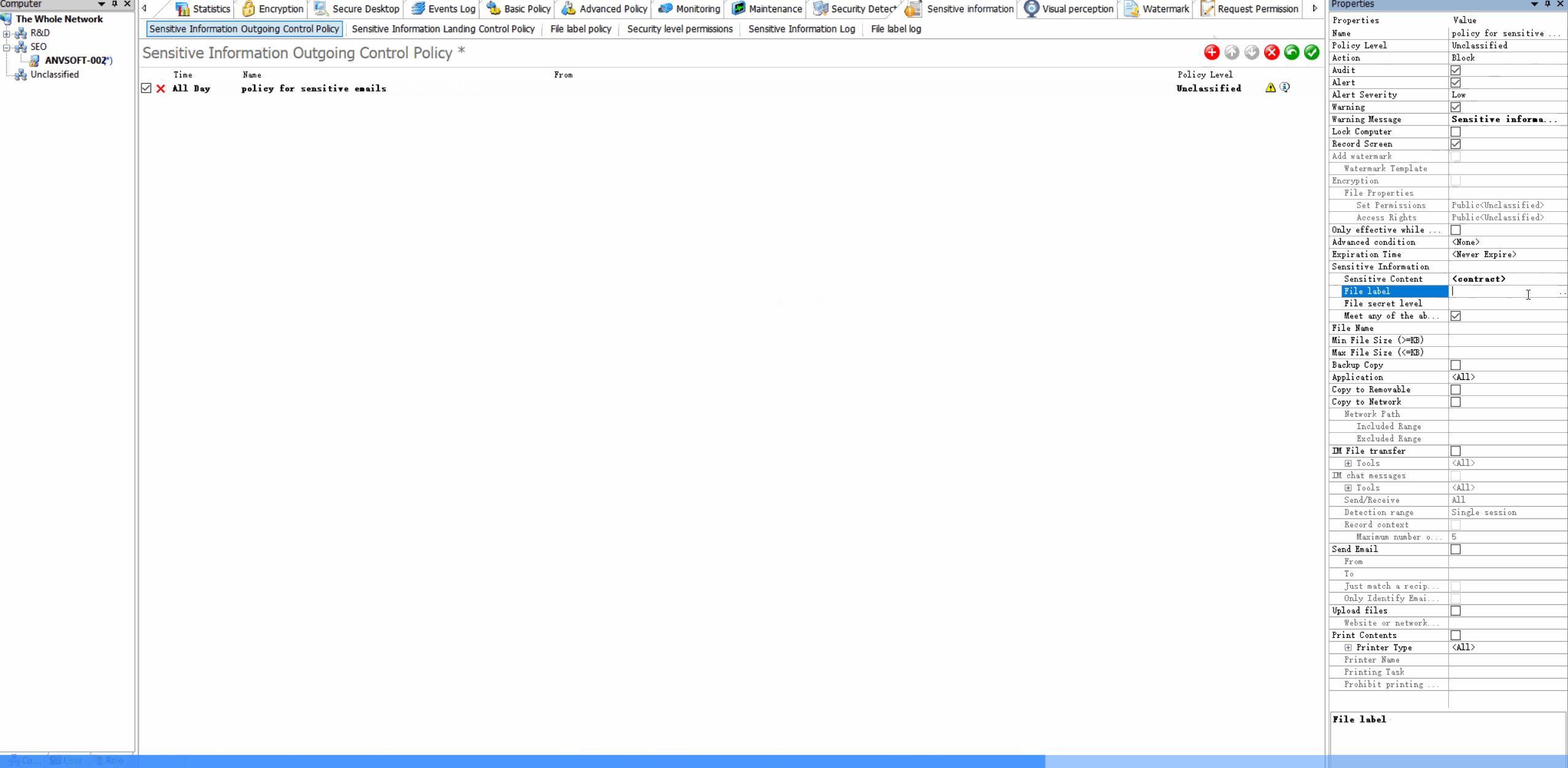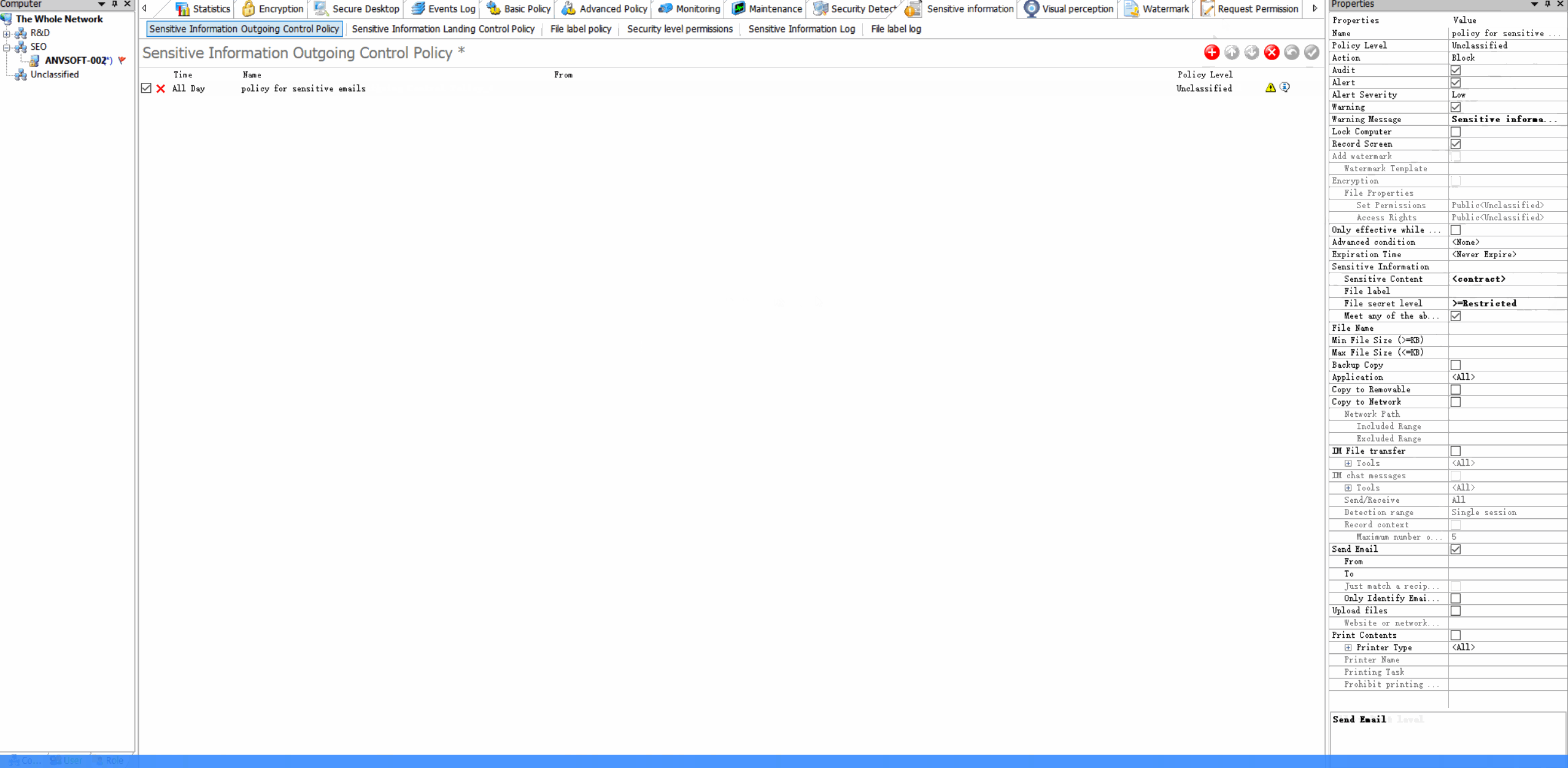
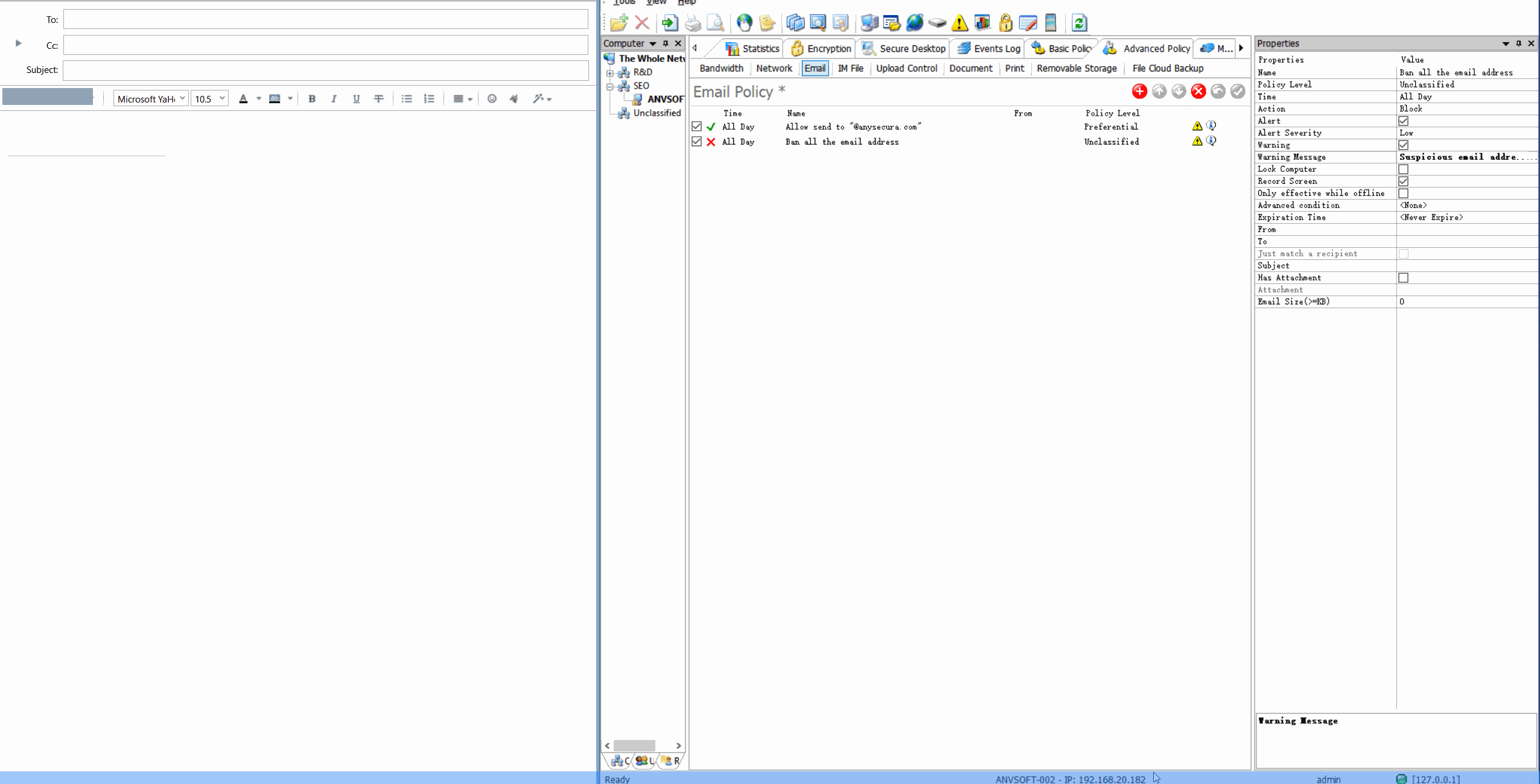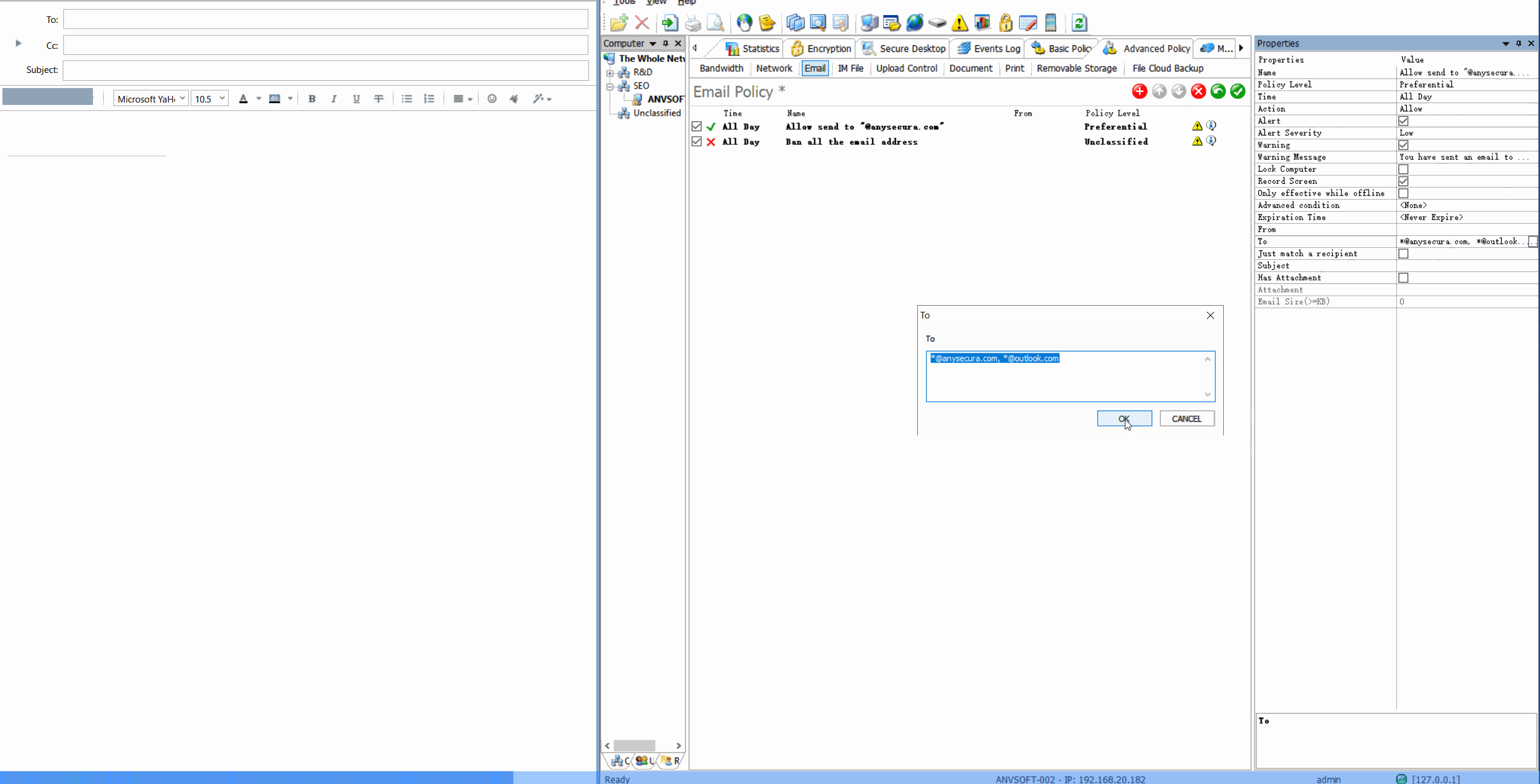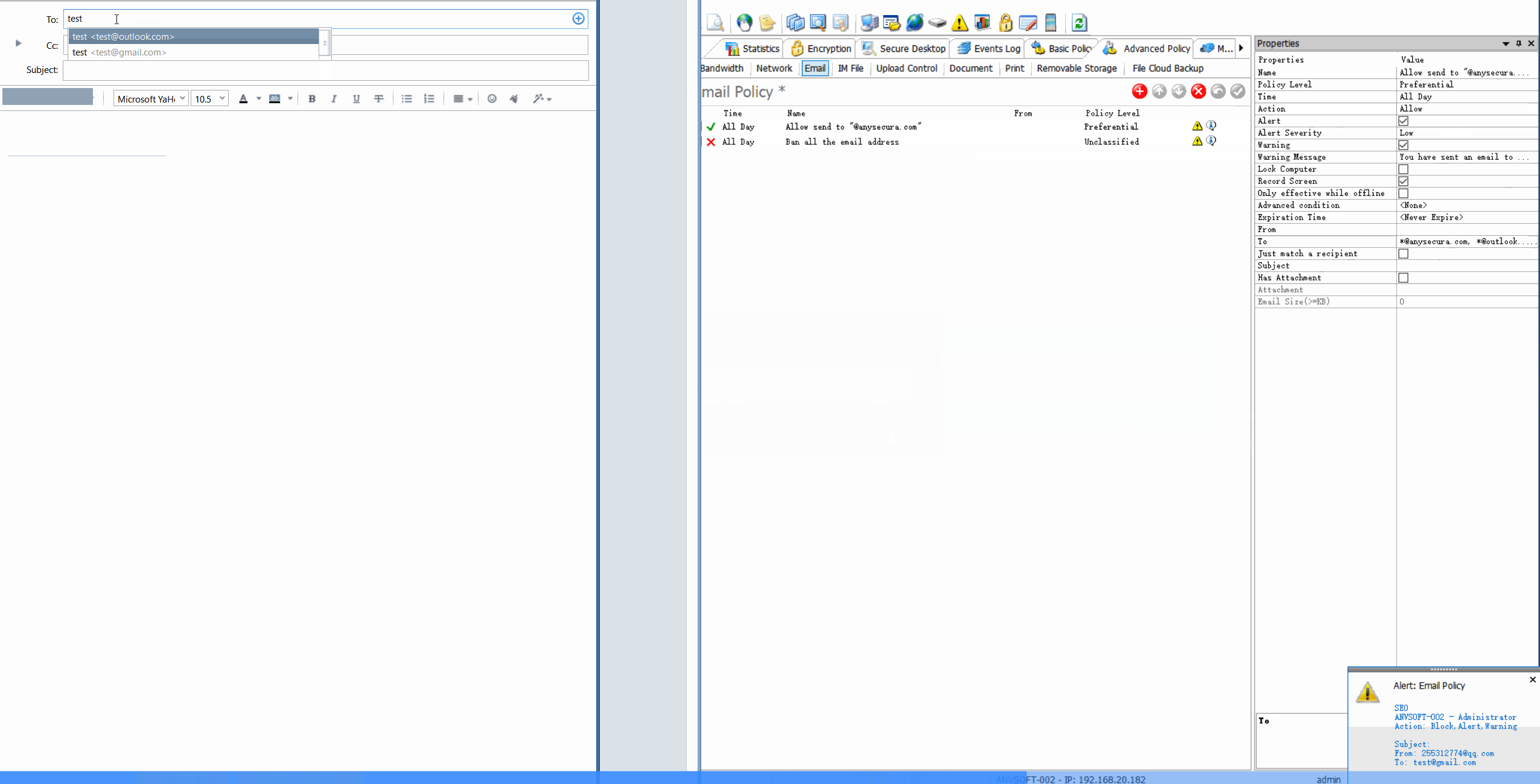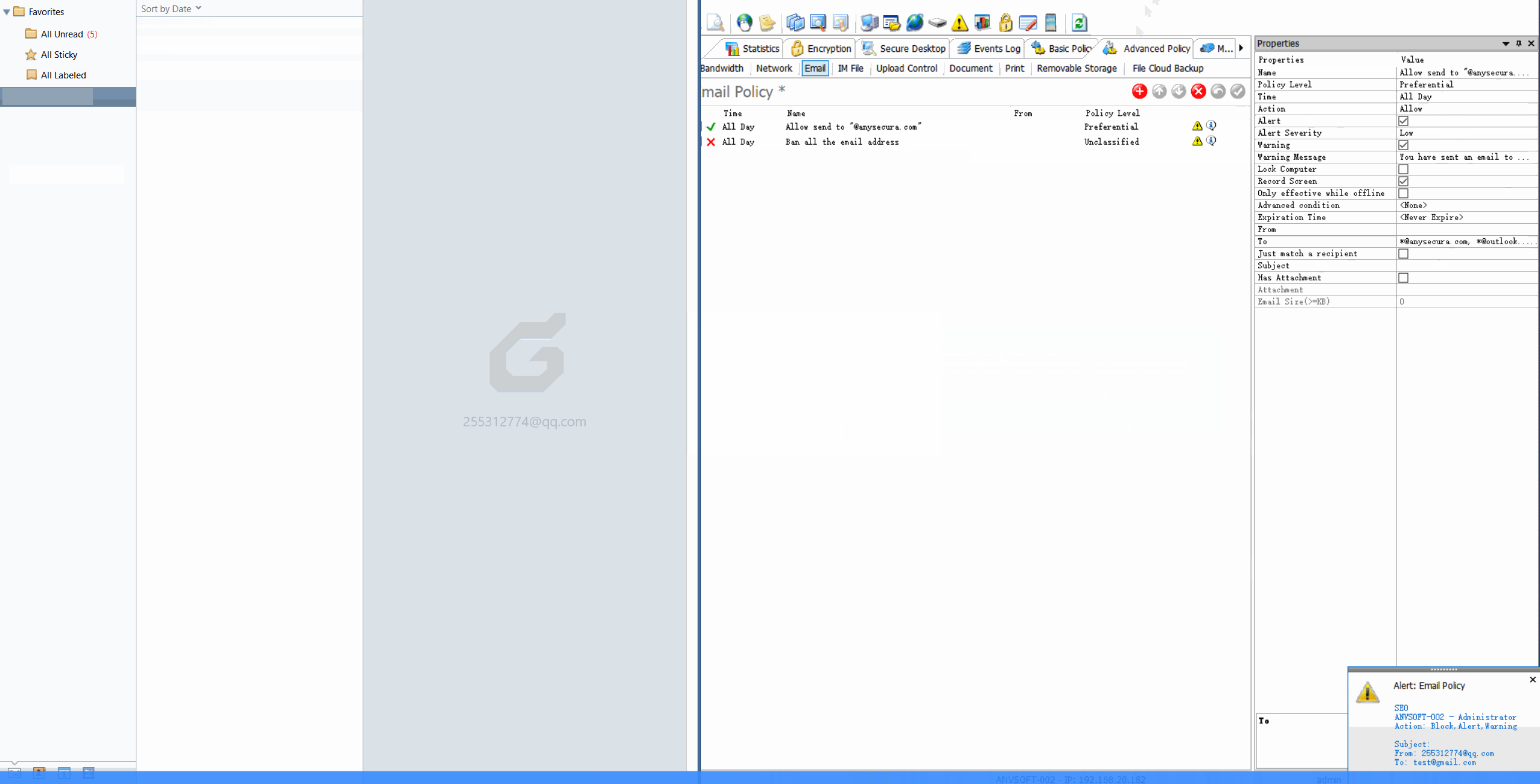
Content-Based PoliciesBlock or encrypt emails containing sensitive information (credit cards, personal data, confidential reports).
-
Automatic WatermarkingApply watermarks to email attachments based on sensitivity level and recipient.
-
Domain RestrictionsAllow email communication only with approved domains and block suspicious email addresses.
Email Control Benefits
Prevent data leakage through email communications, ensure regulatory compliance for sensitive information, and maintain visibility over external data transfers.
Application Control: Manage Software Usage
-
Application Usage LogsTrack which applications are used, by whom, and for how long with detailed activity timelines.
-
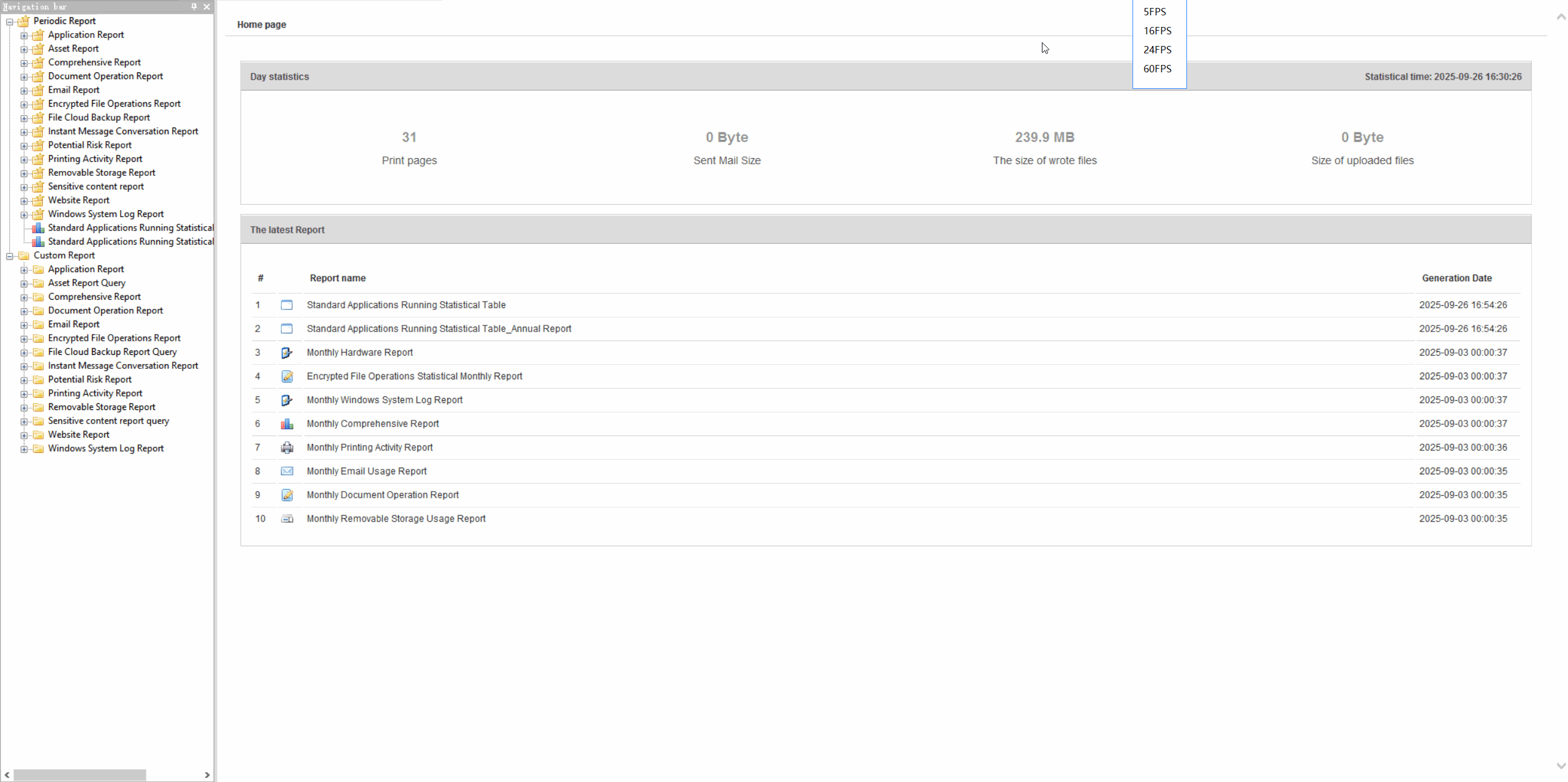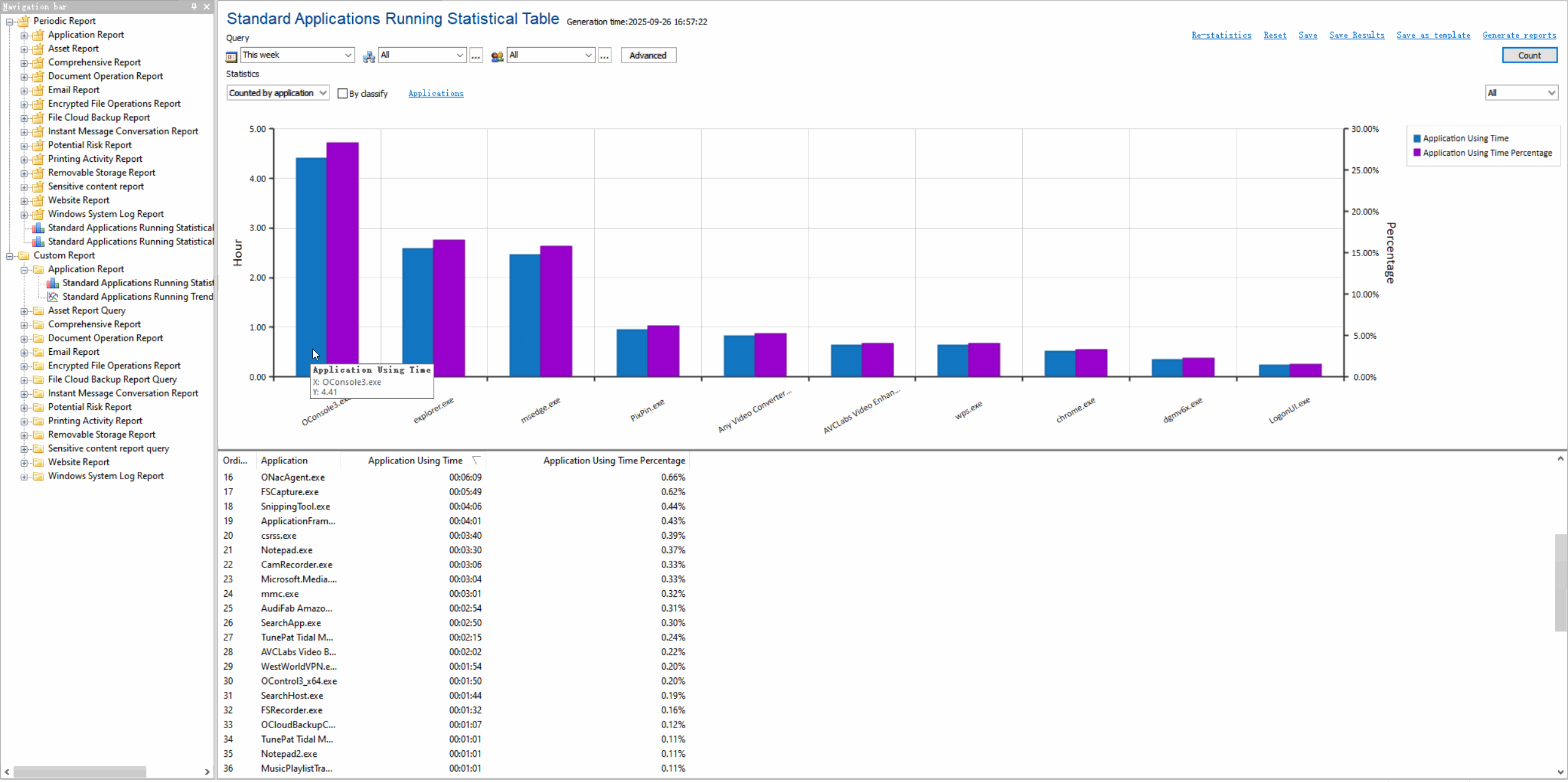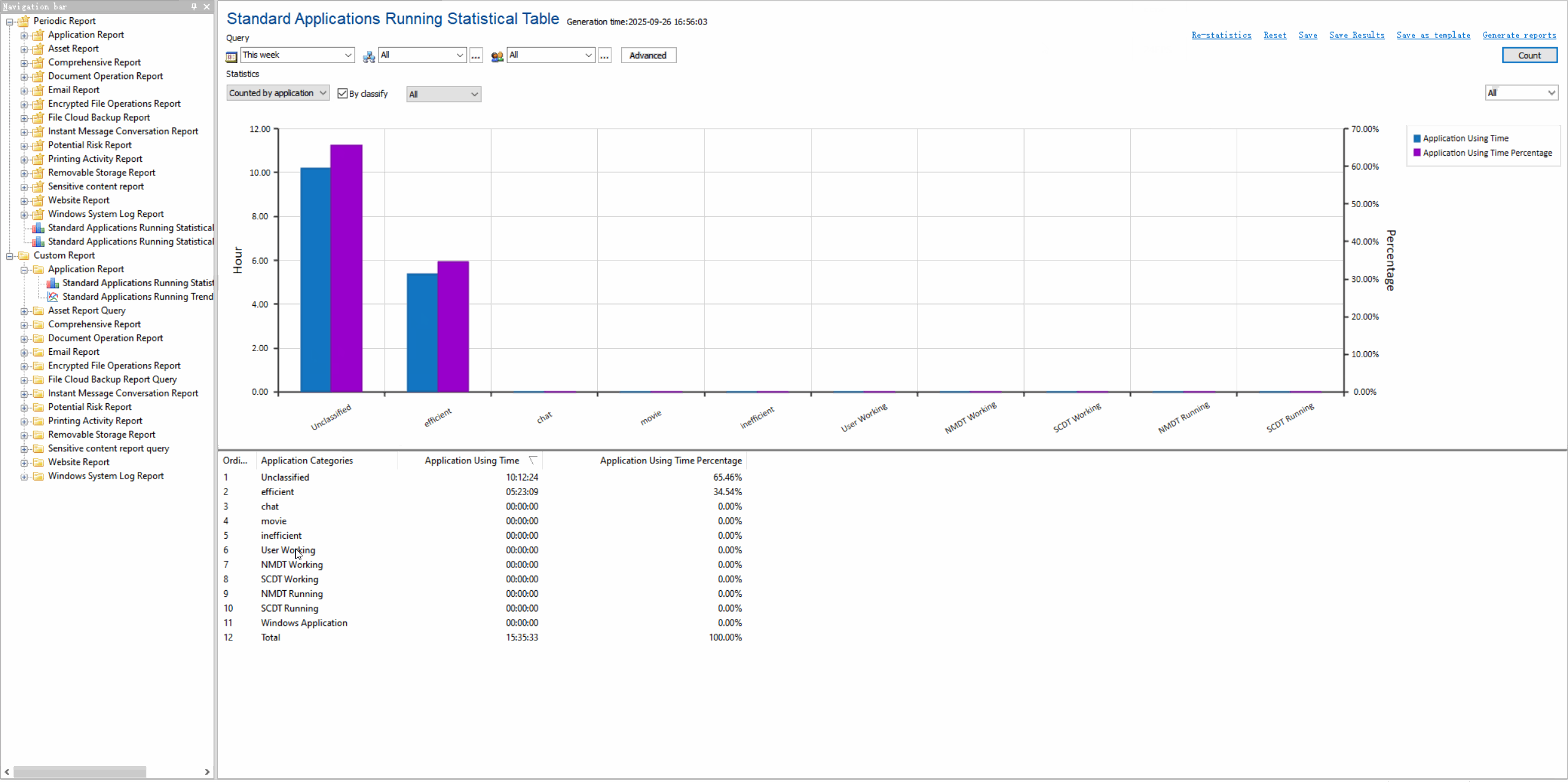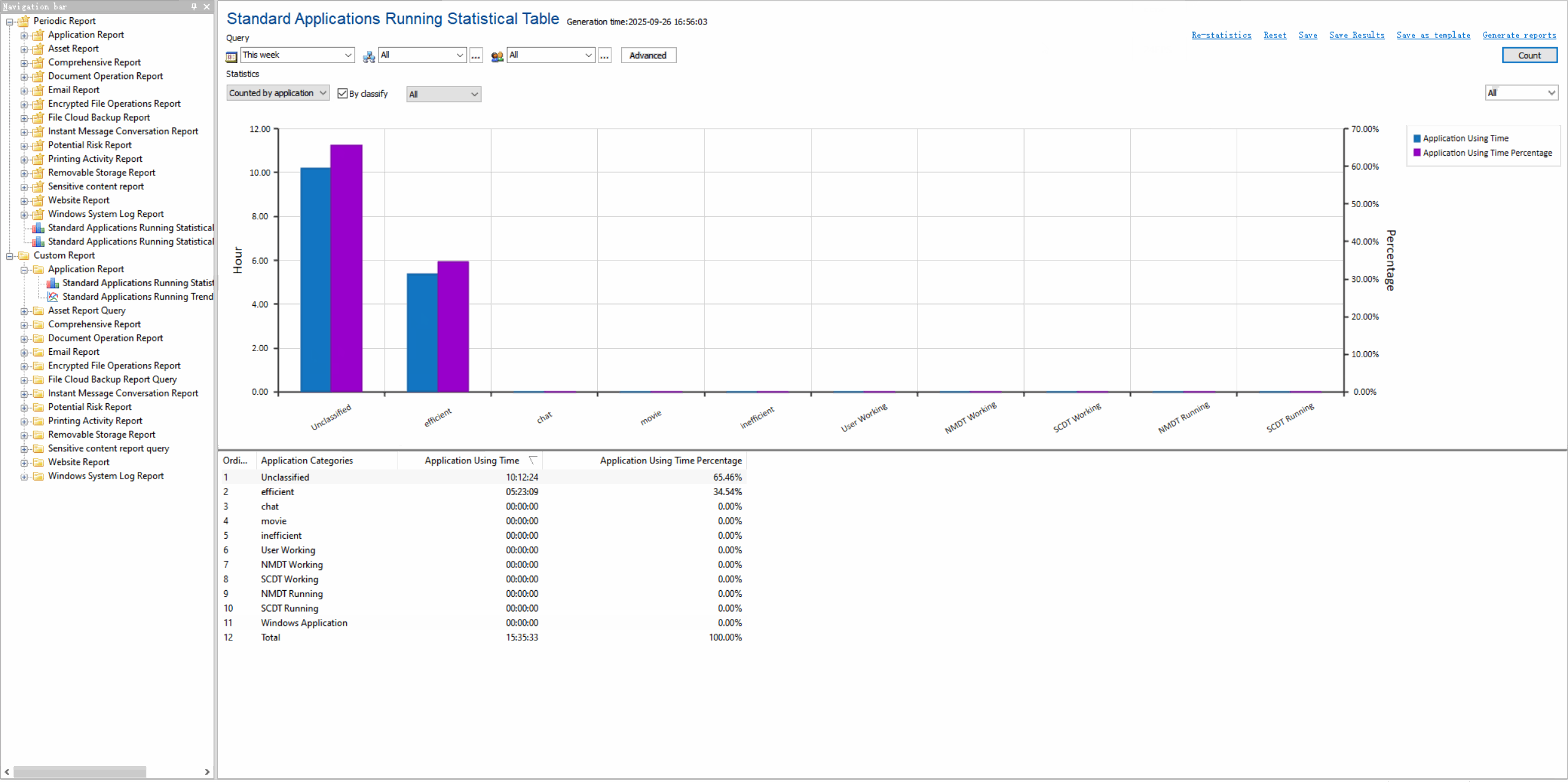
Usage Statistics & ReportsGenerate visual reports on application usage patterns, productivity metrics, and resource consumption.
-
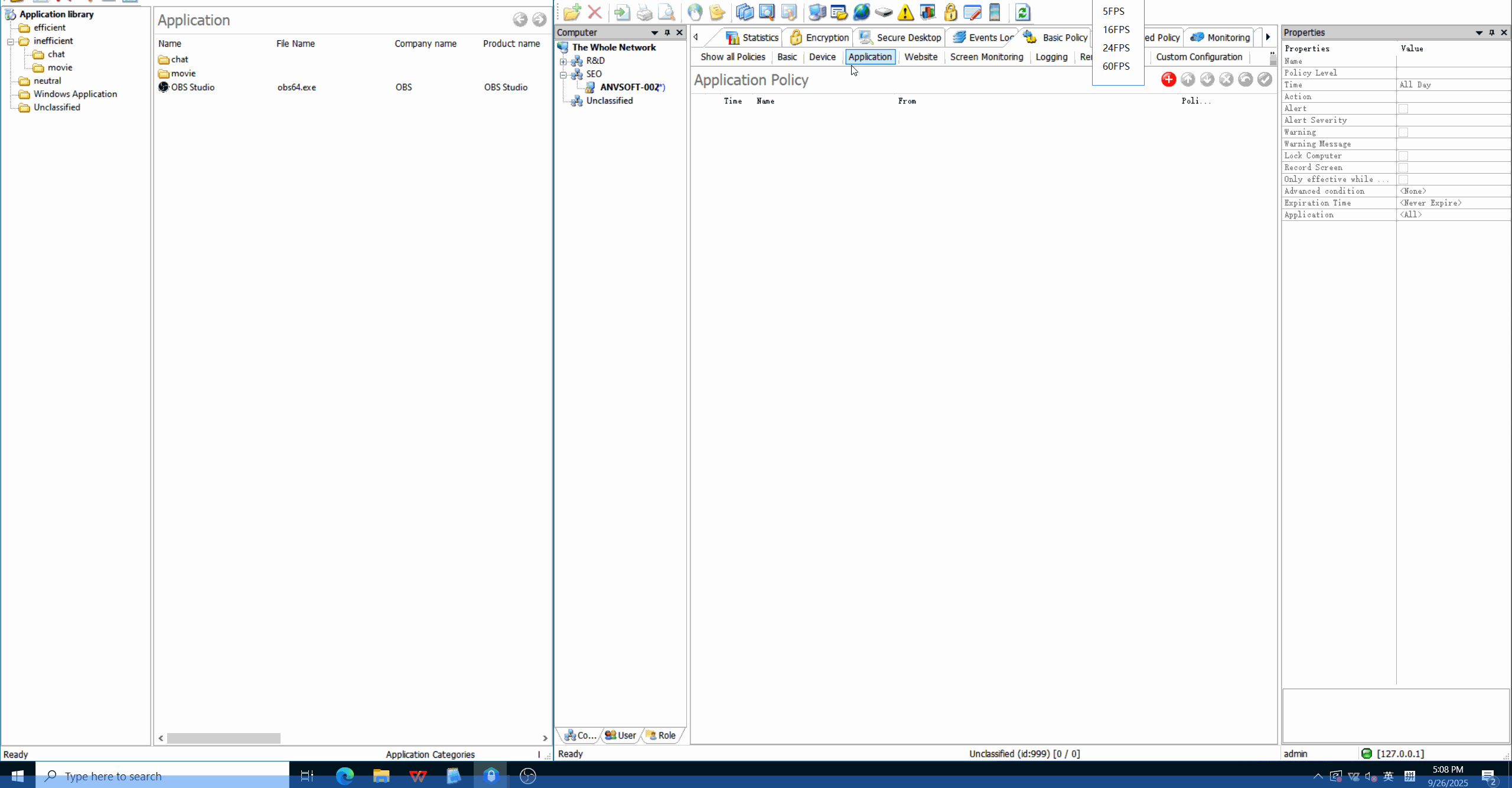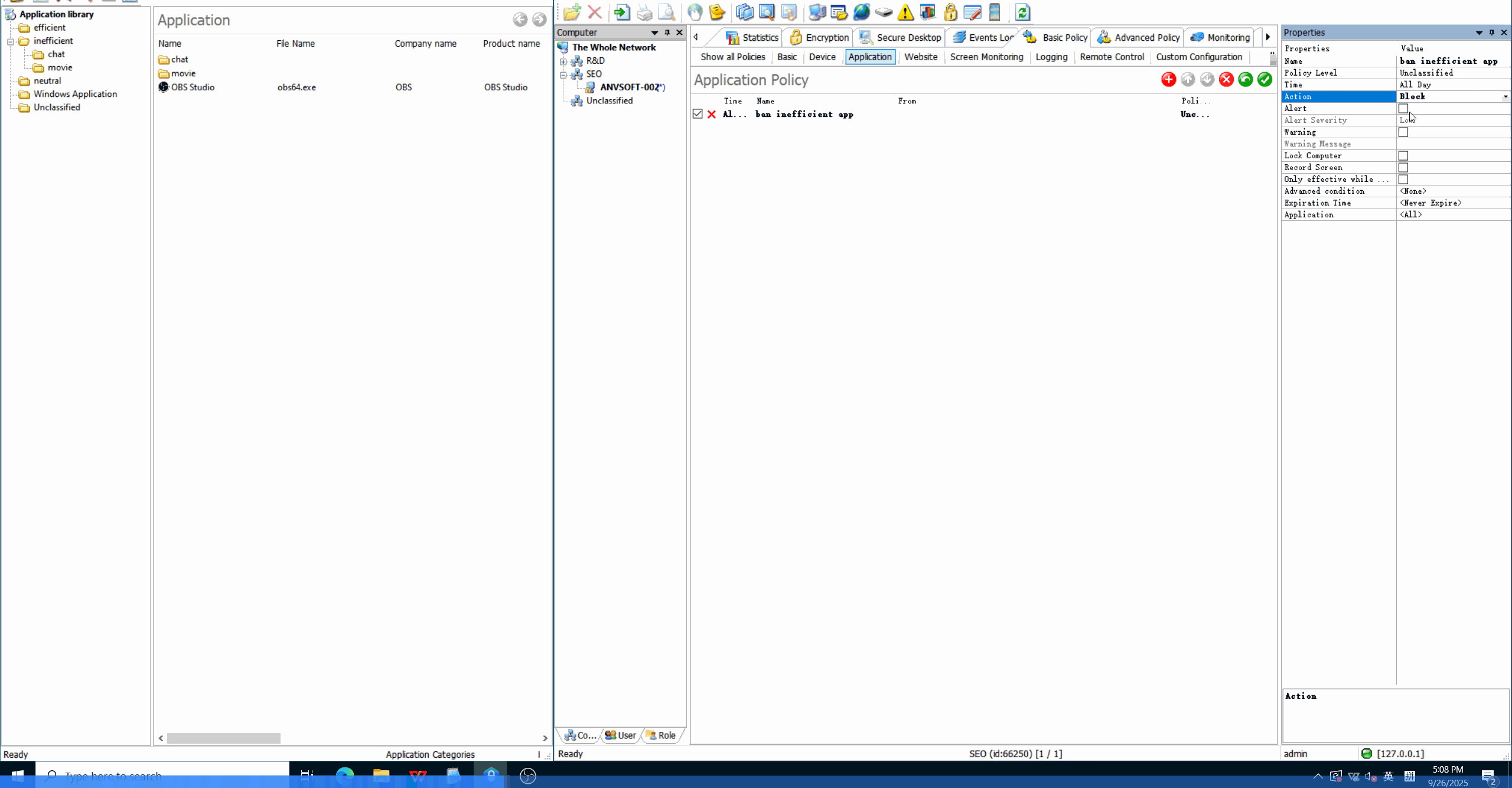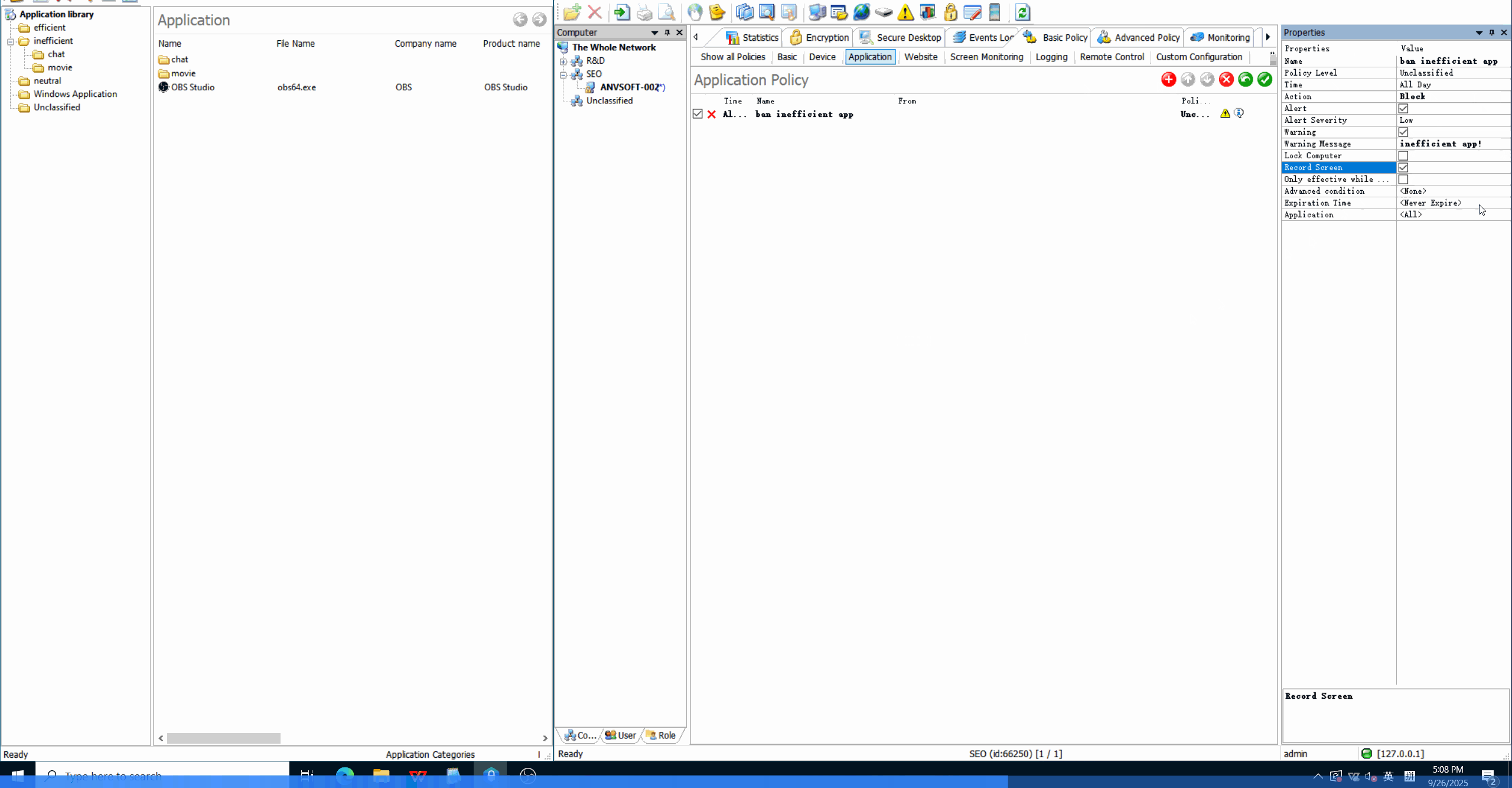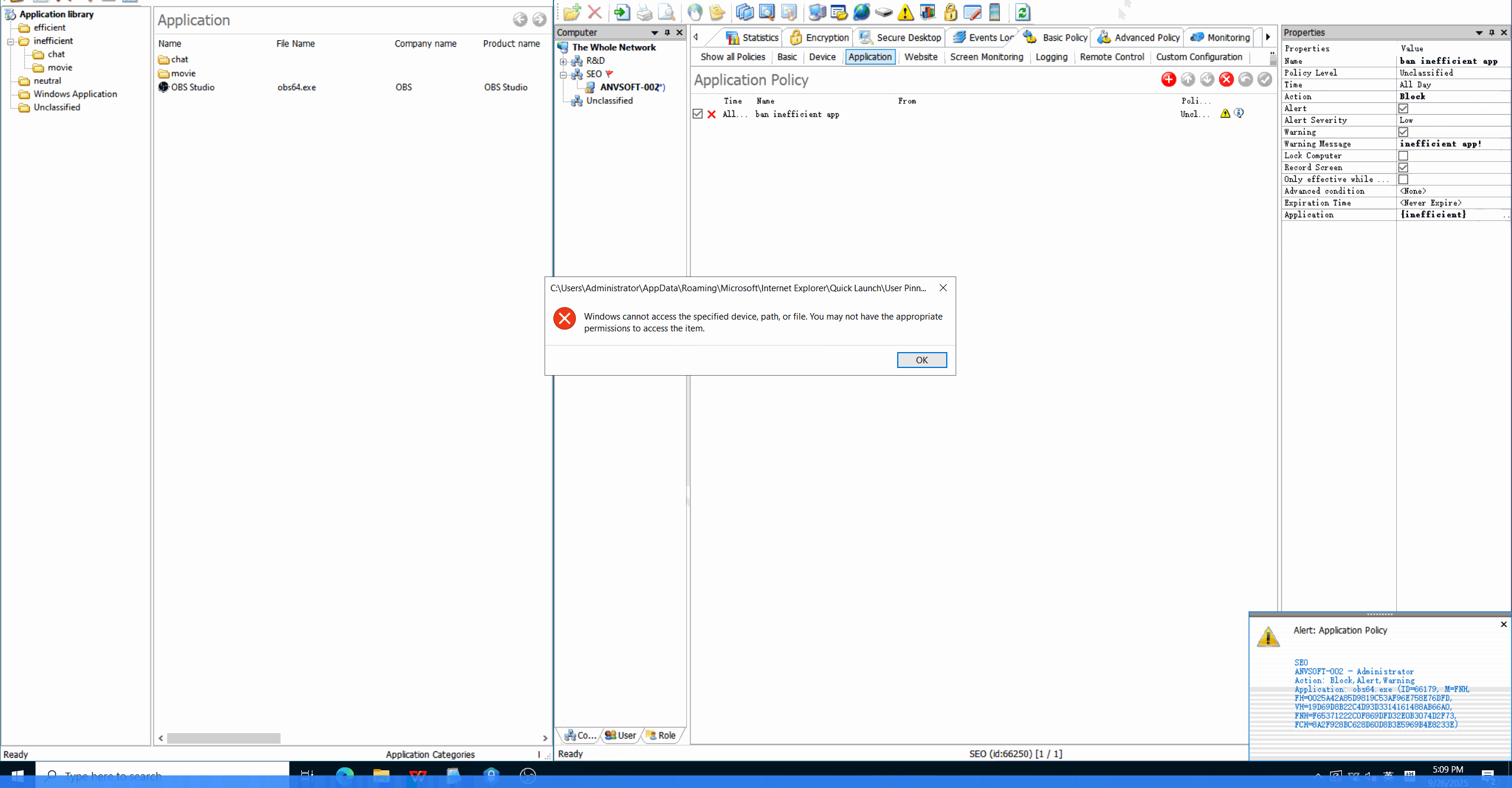
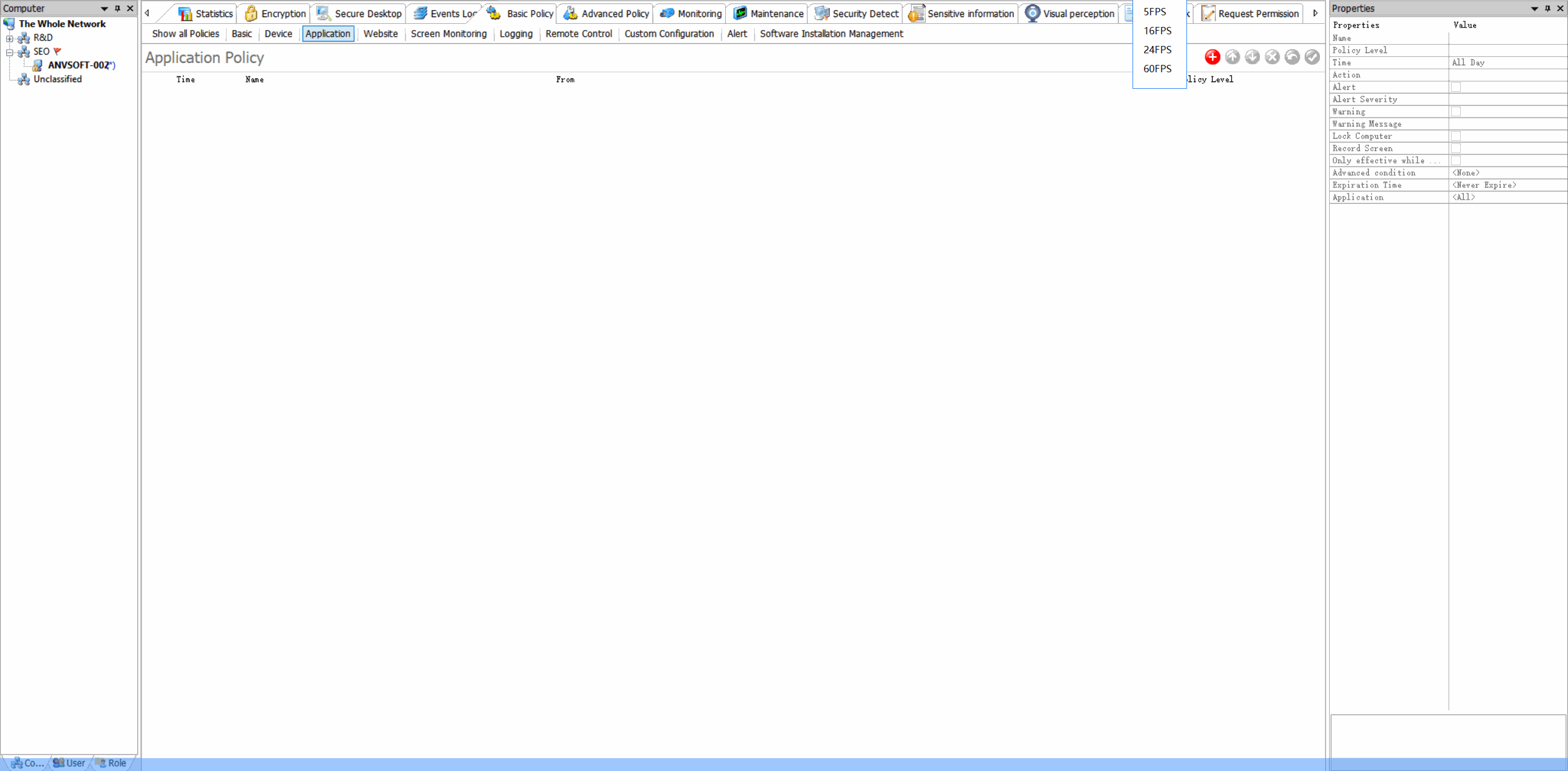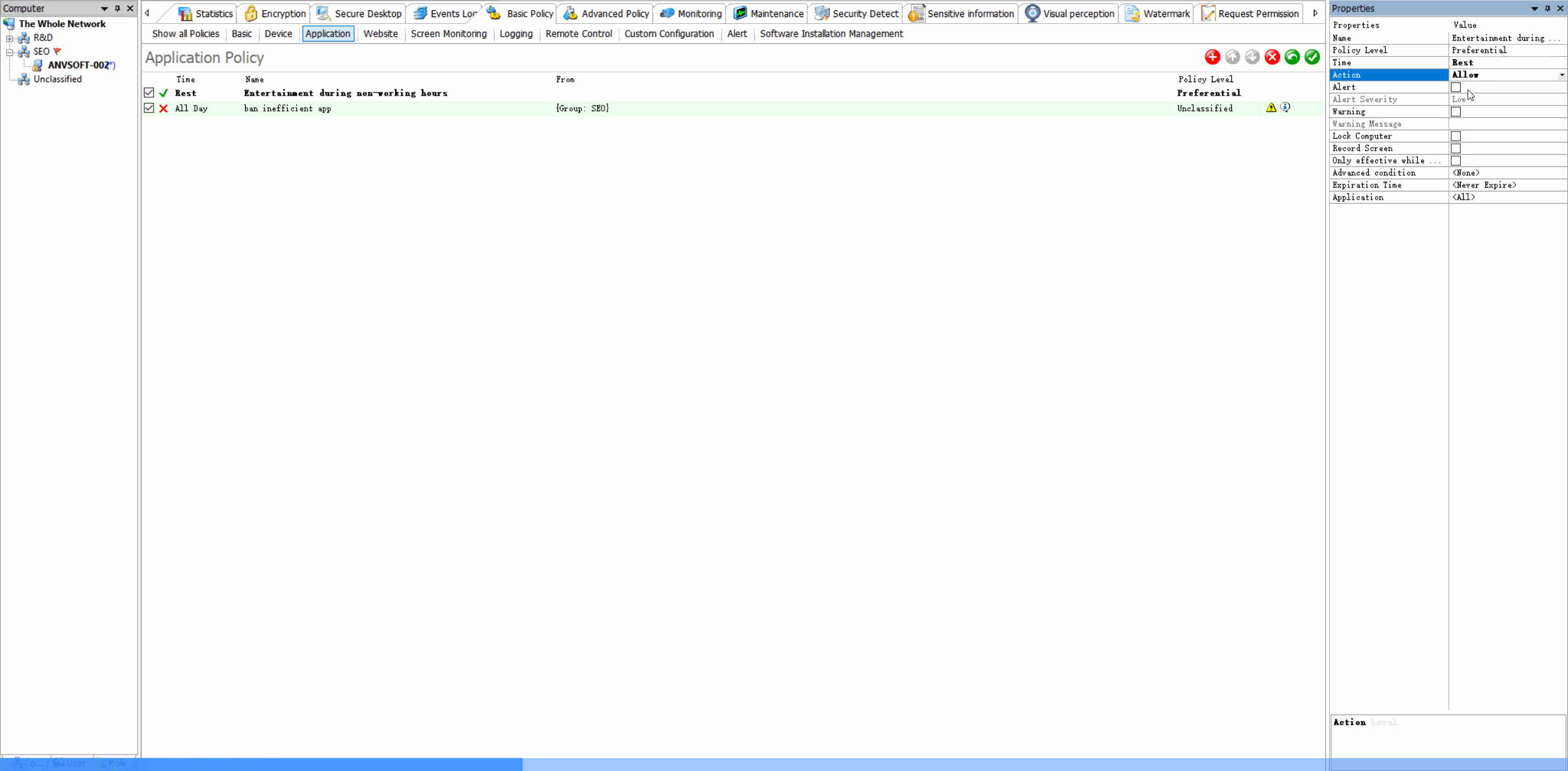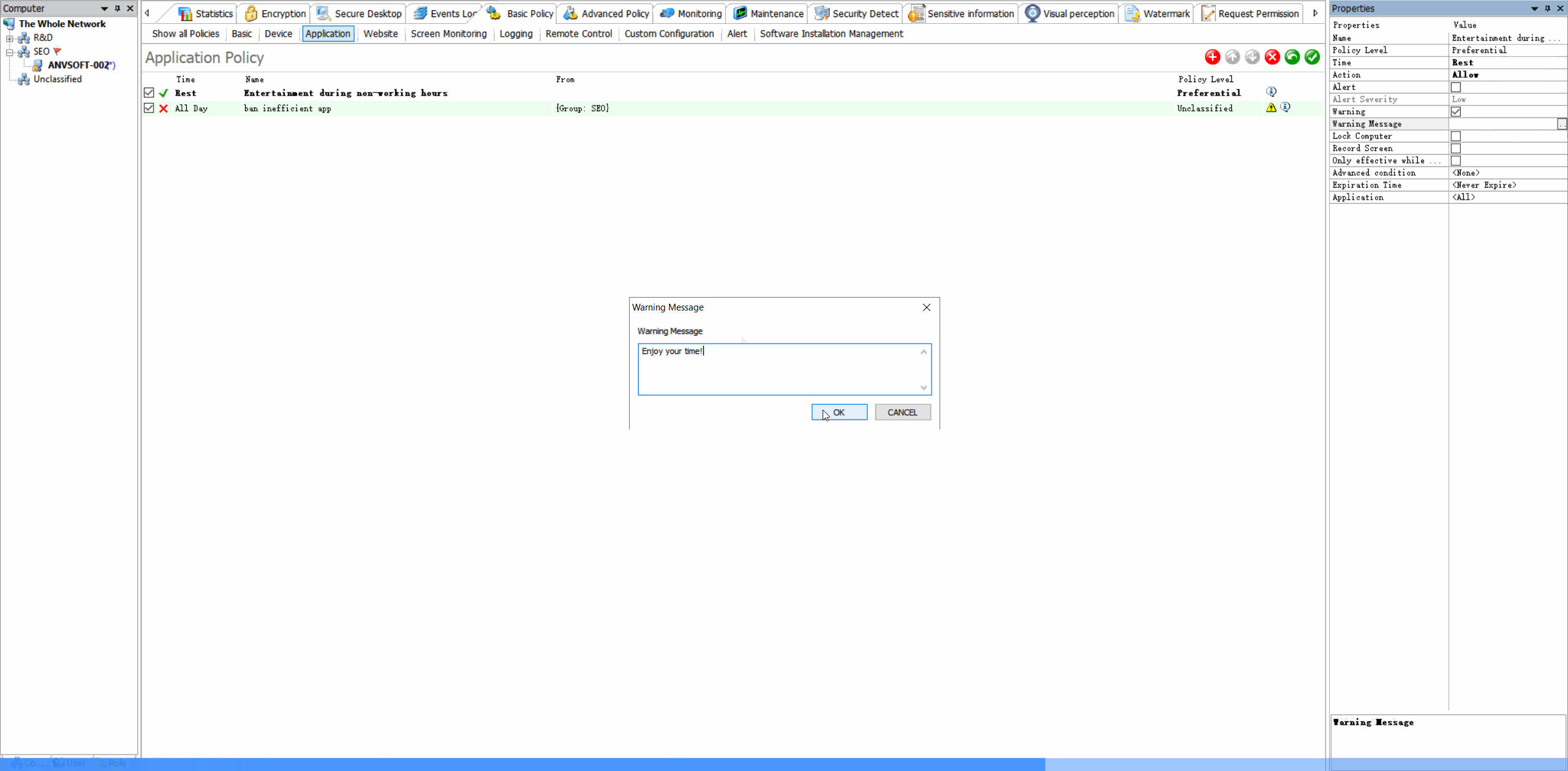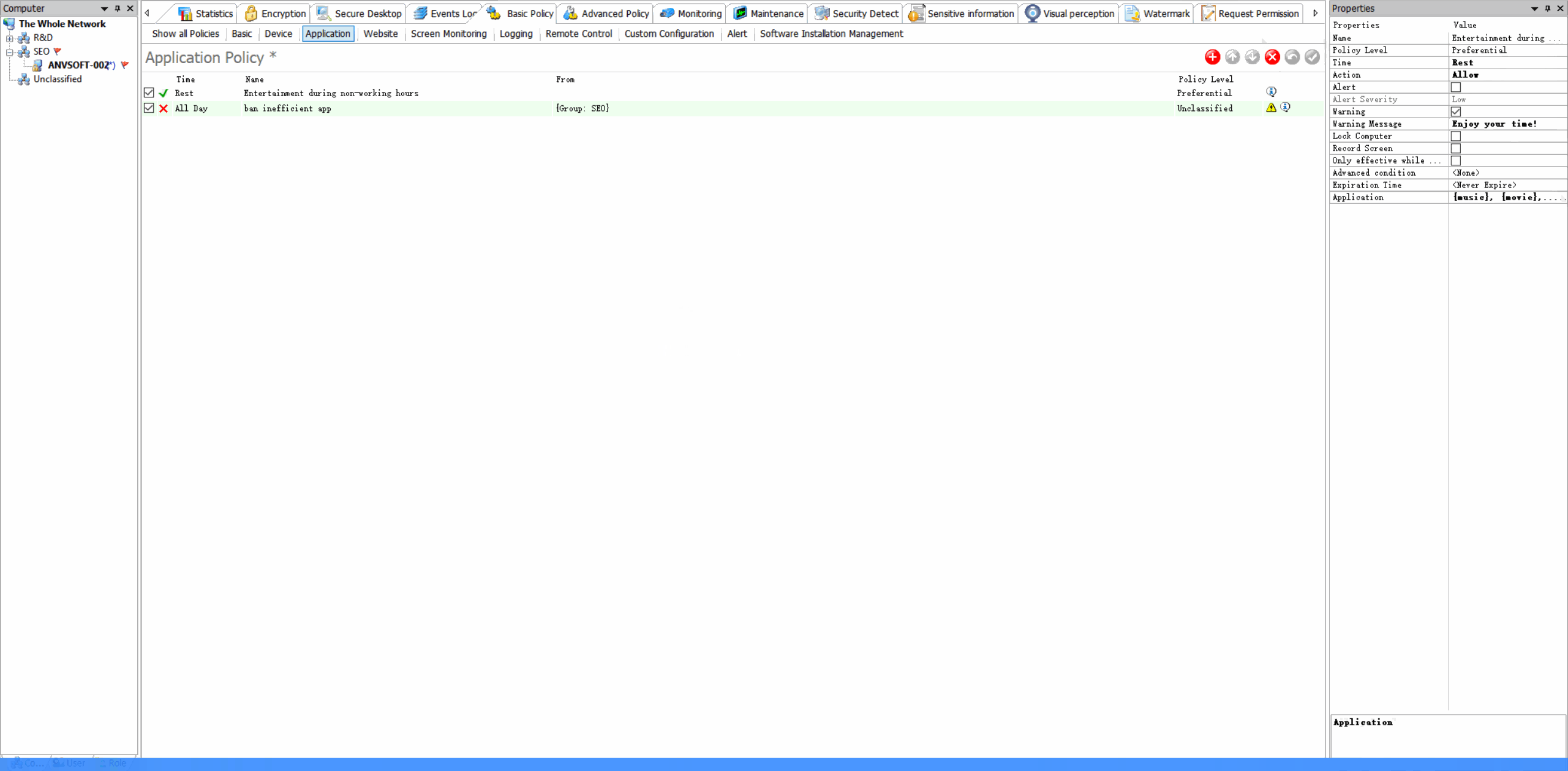
Application Whitelisting/BlacklistingAllow only approved applications to run and block unauthorized or potentially risky software.
-
Time-Based RestrictionsDefine when specific applications can be used to maintain productivity and security.
Value of Application Control
Enhance security by preventing unauthorized software execution, improve productivity by managing application usage, and reduce IT support costs.
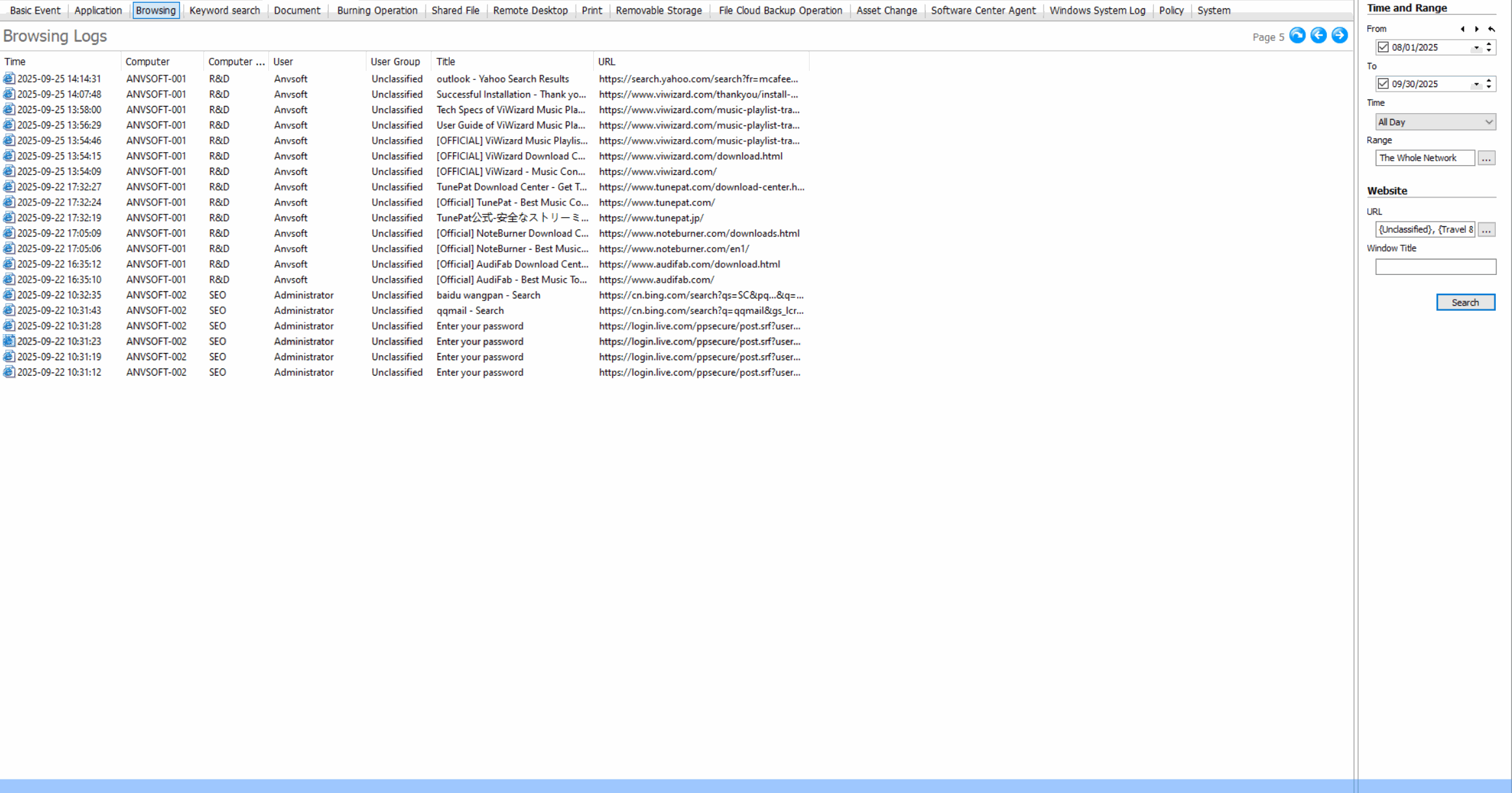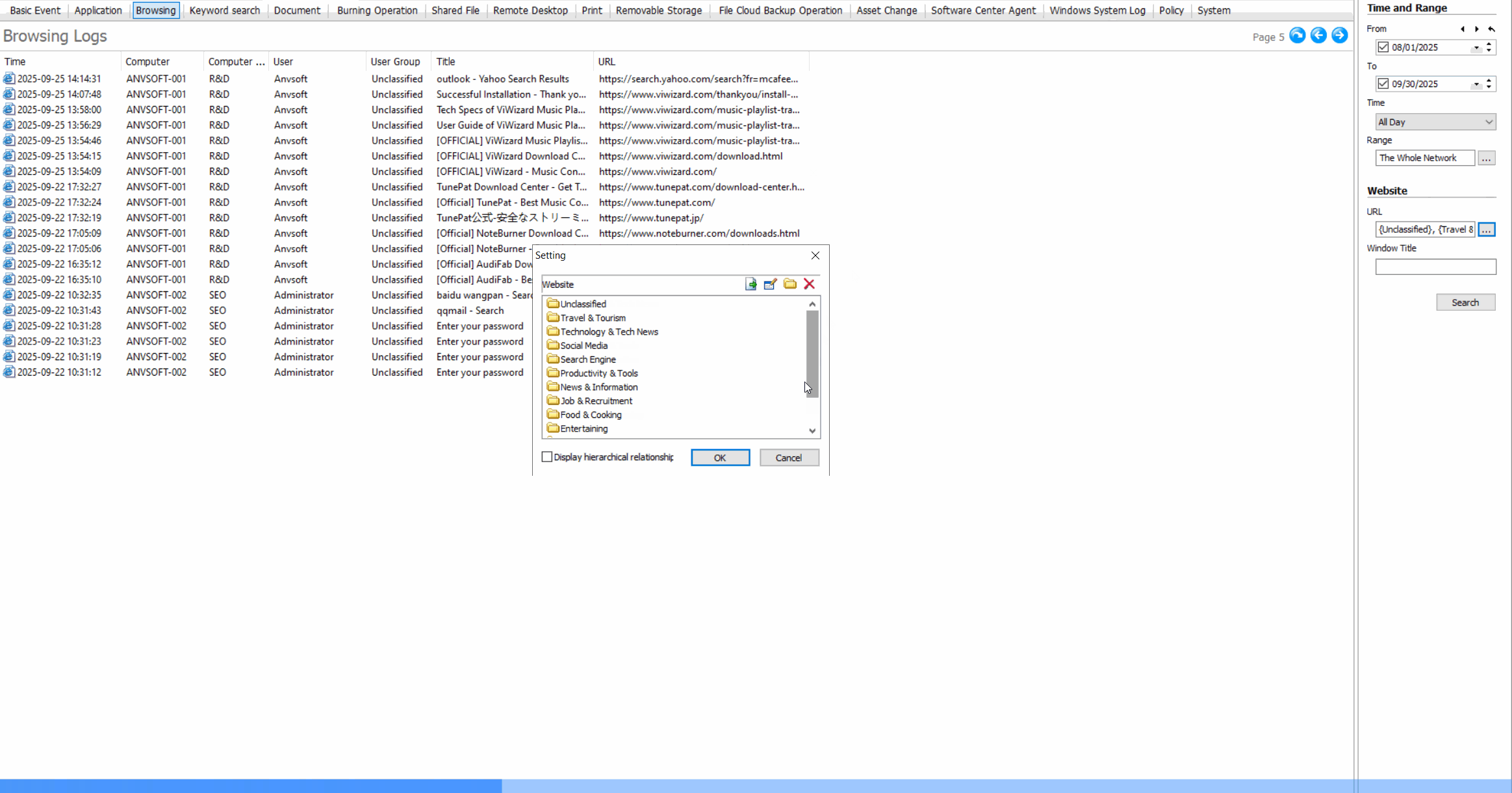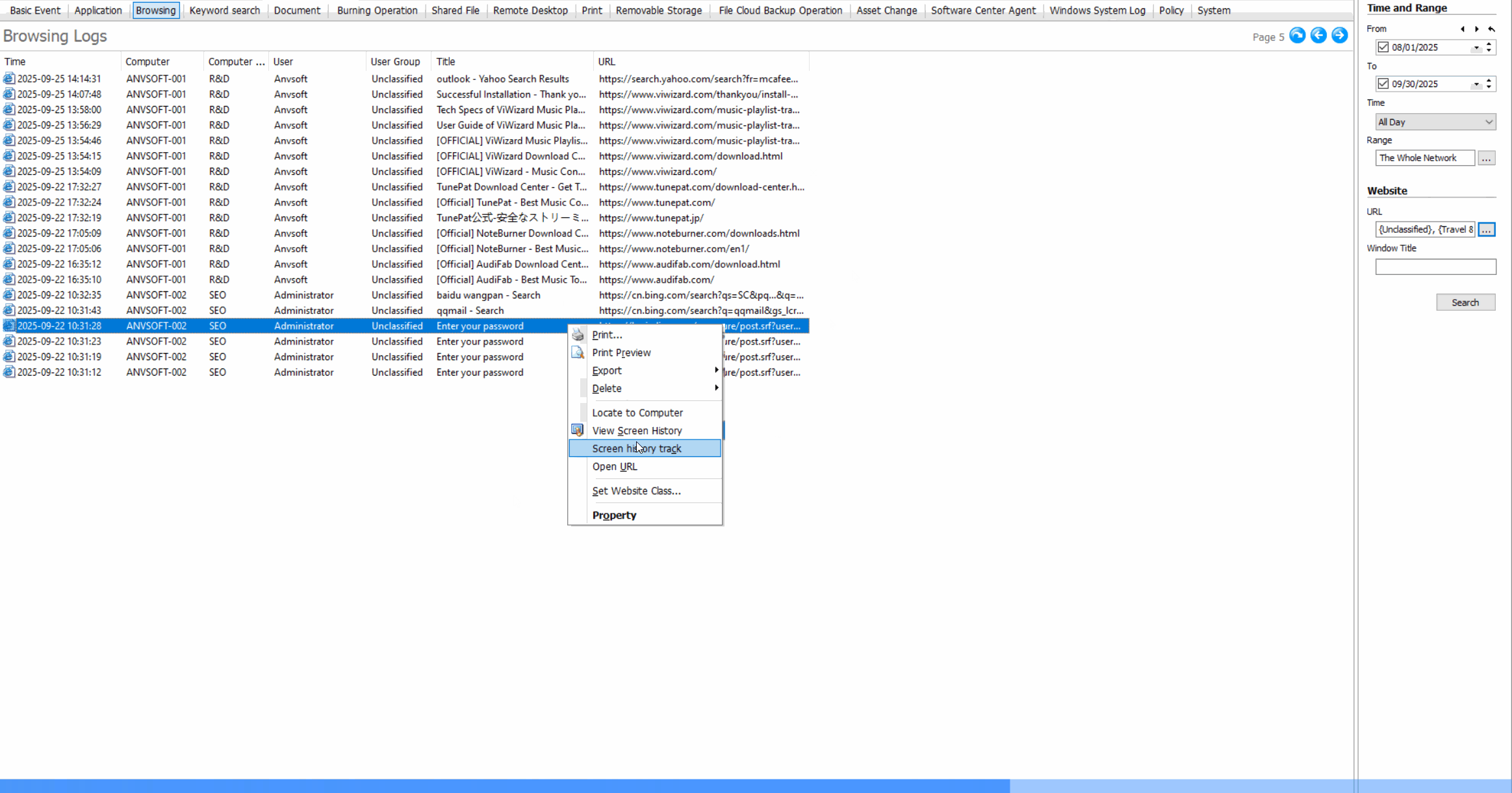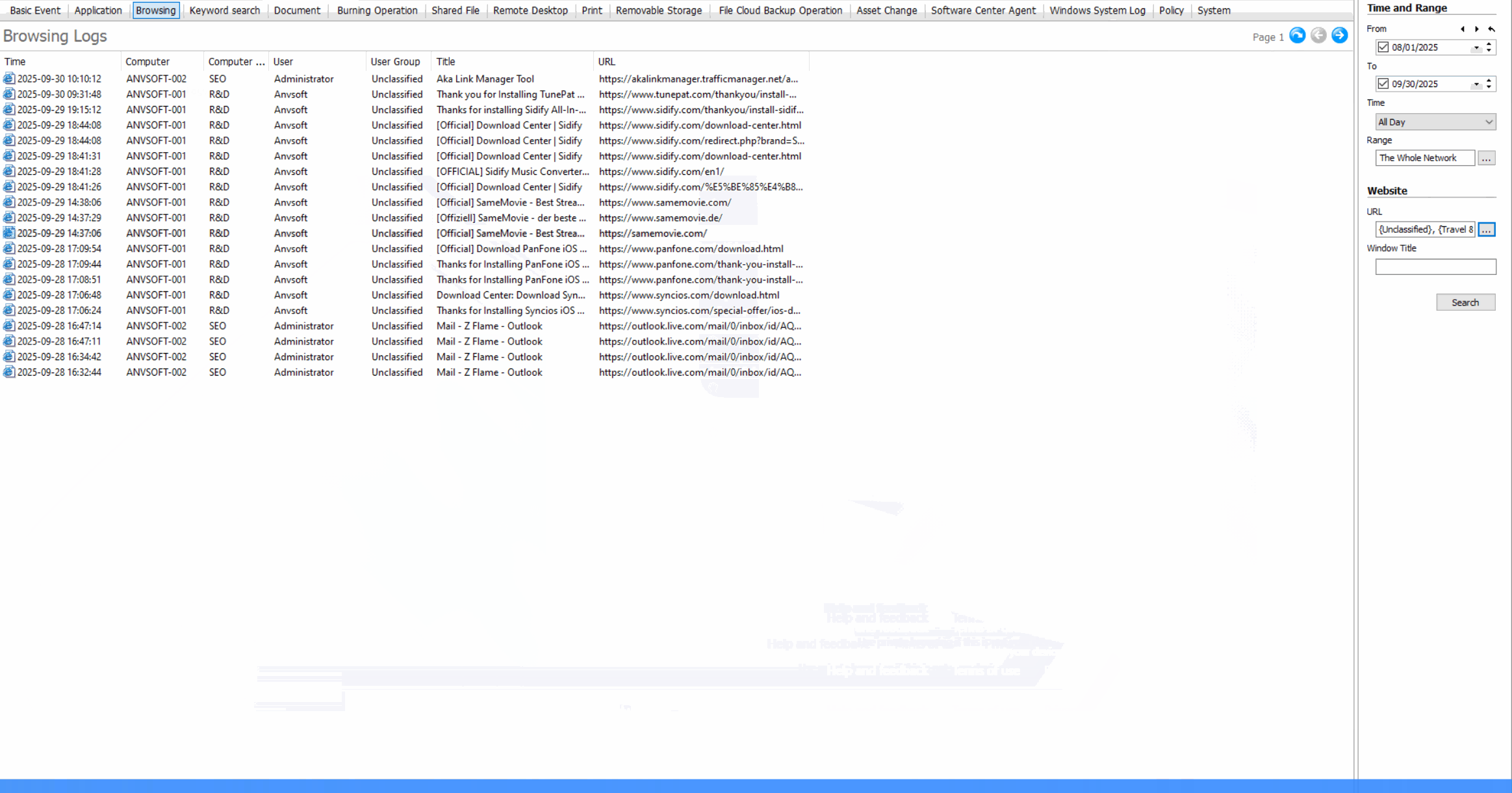
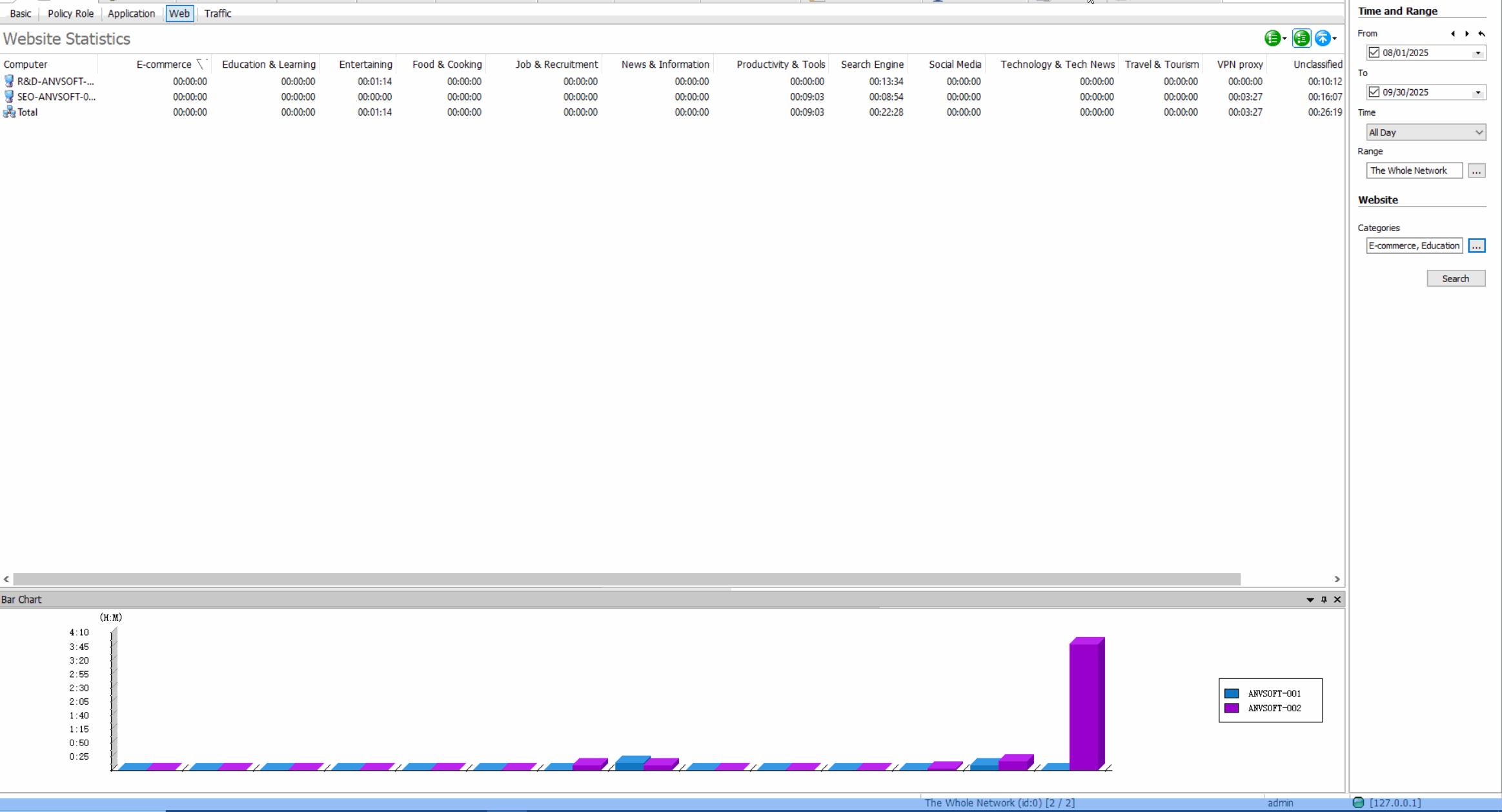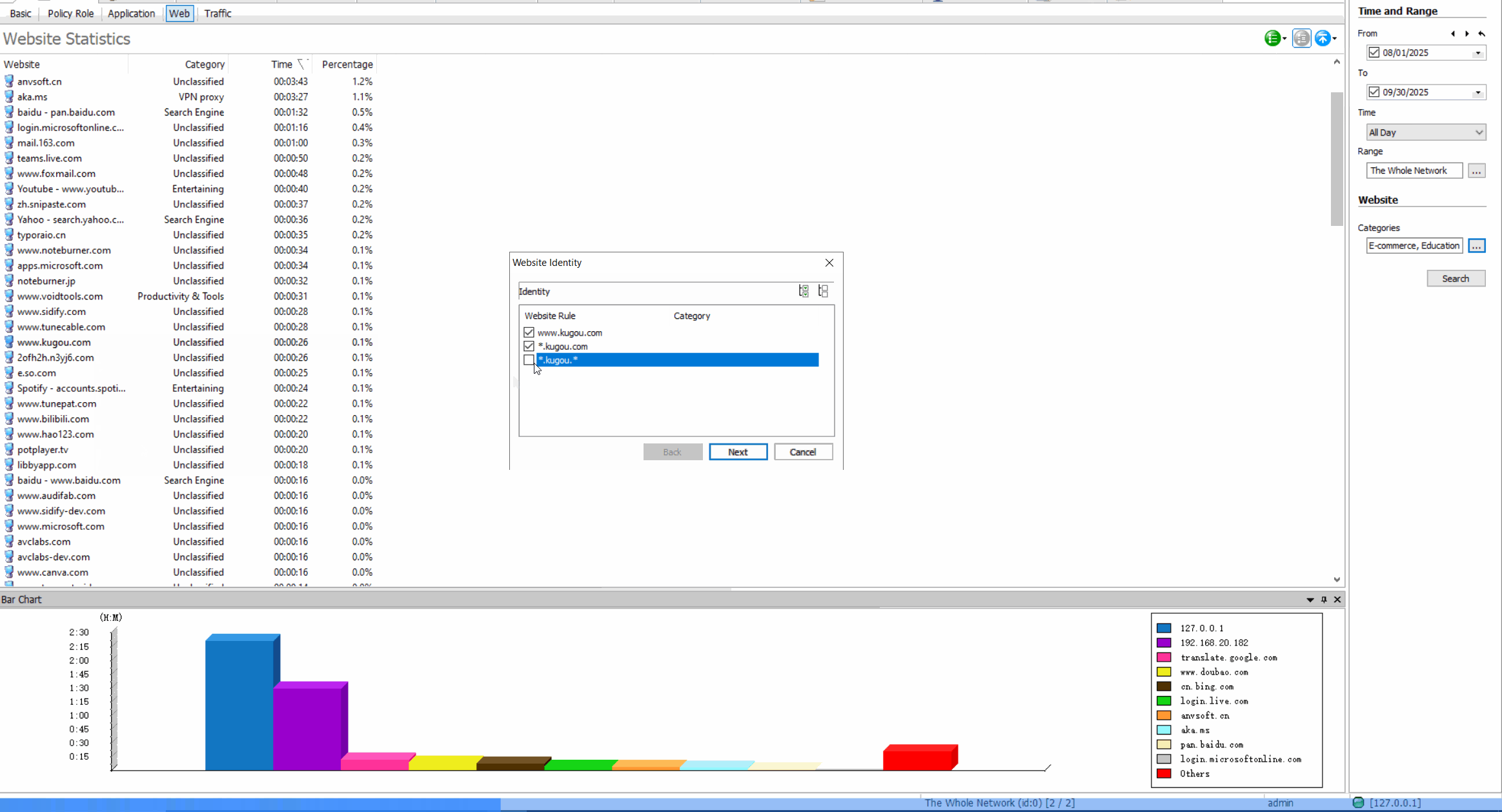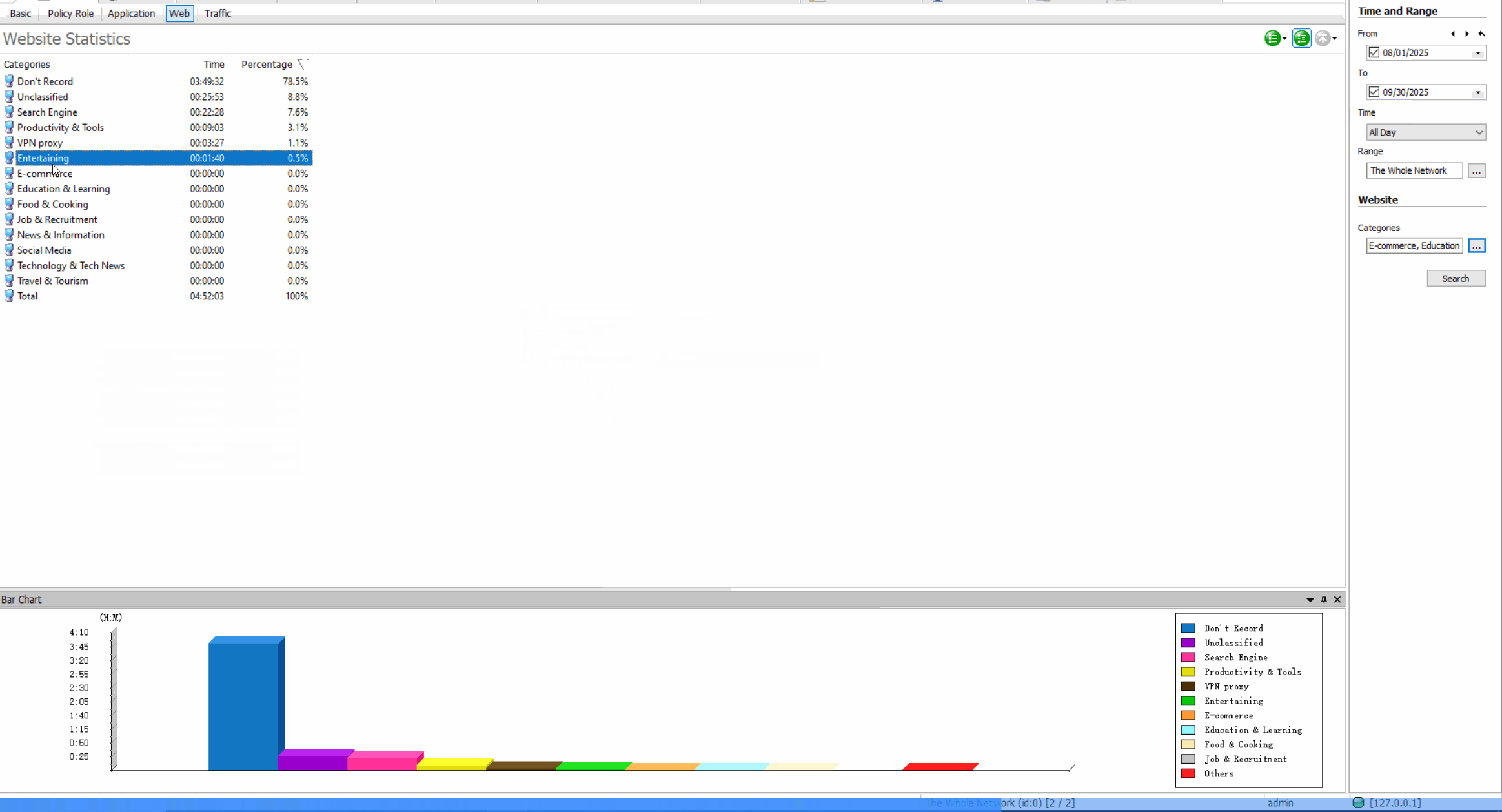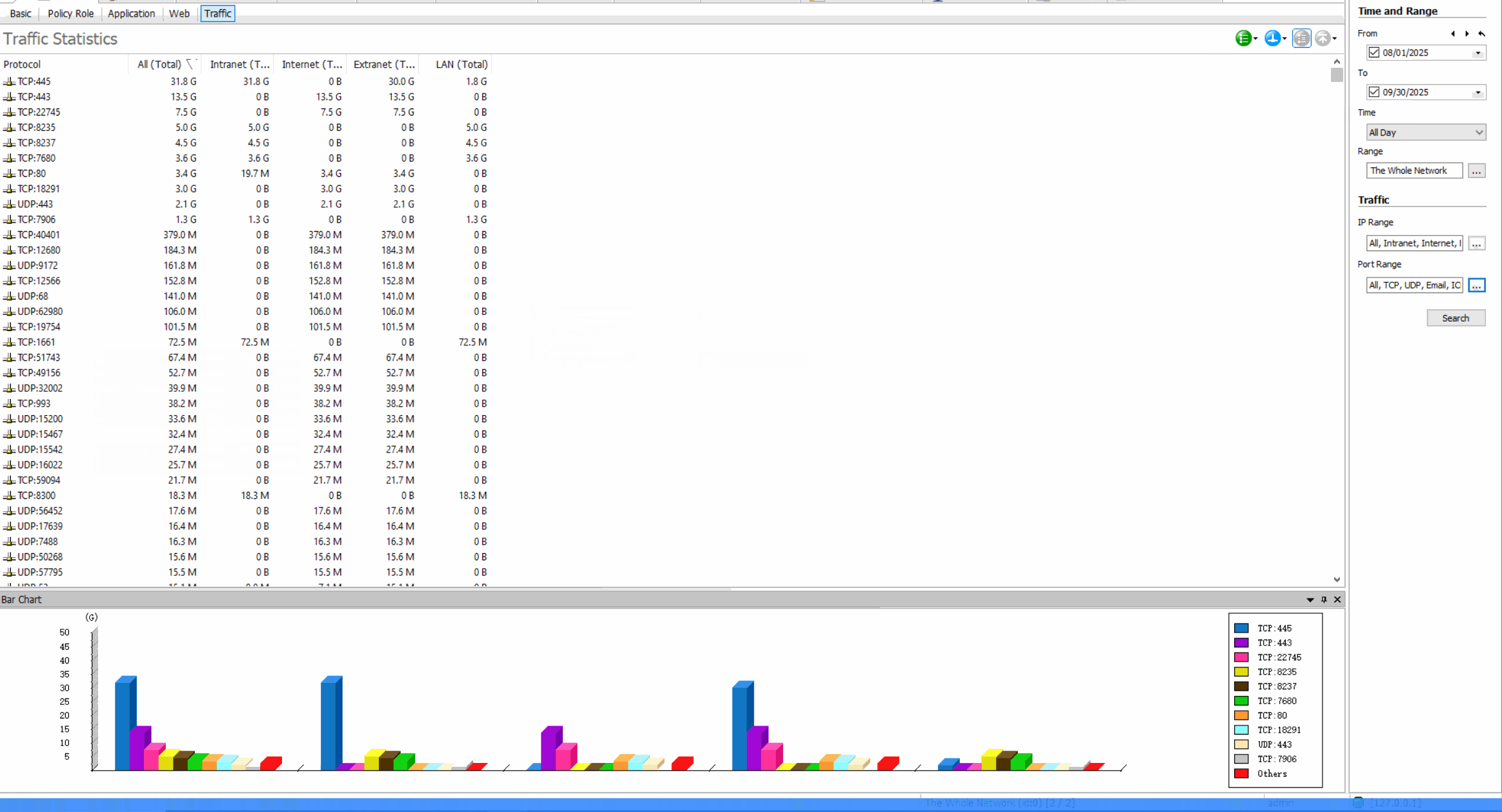
Web Access Control: Regulate Internet Usage
-
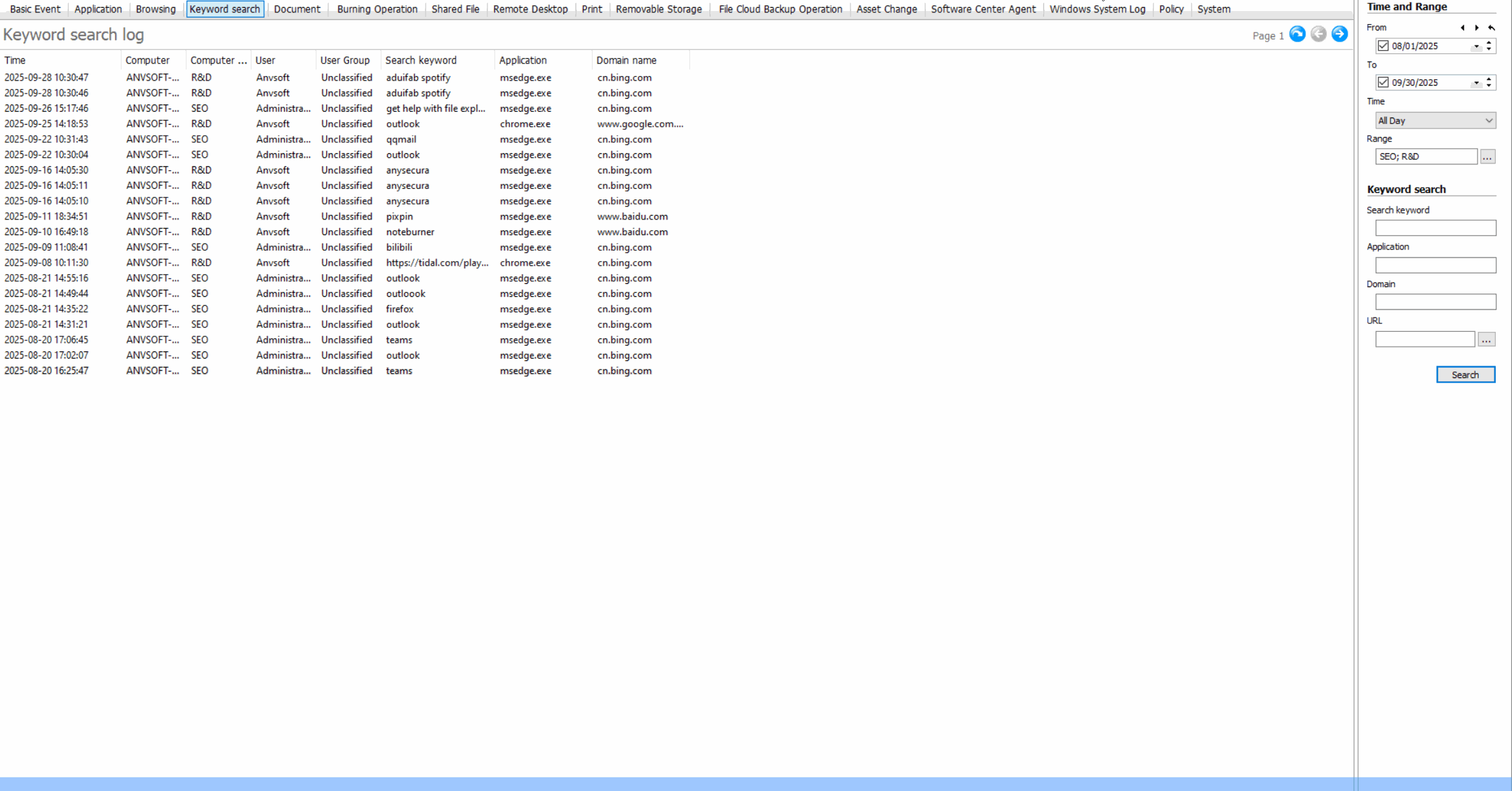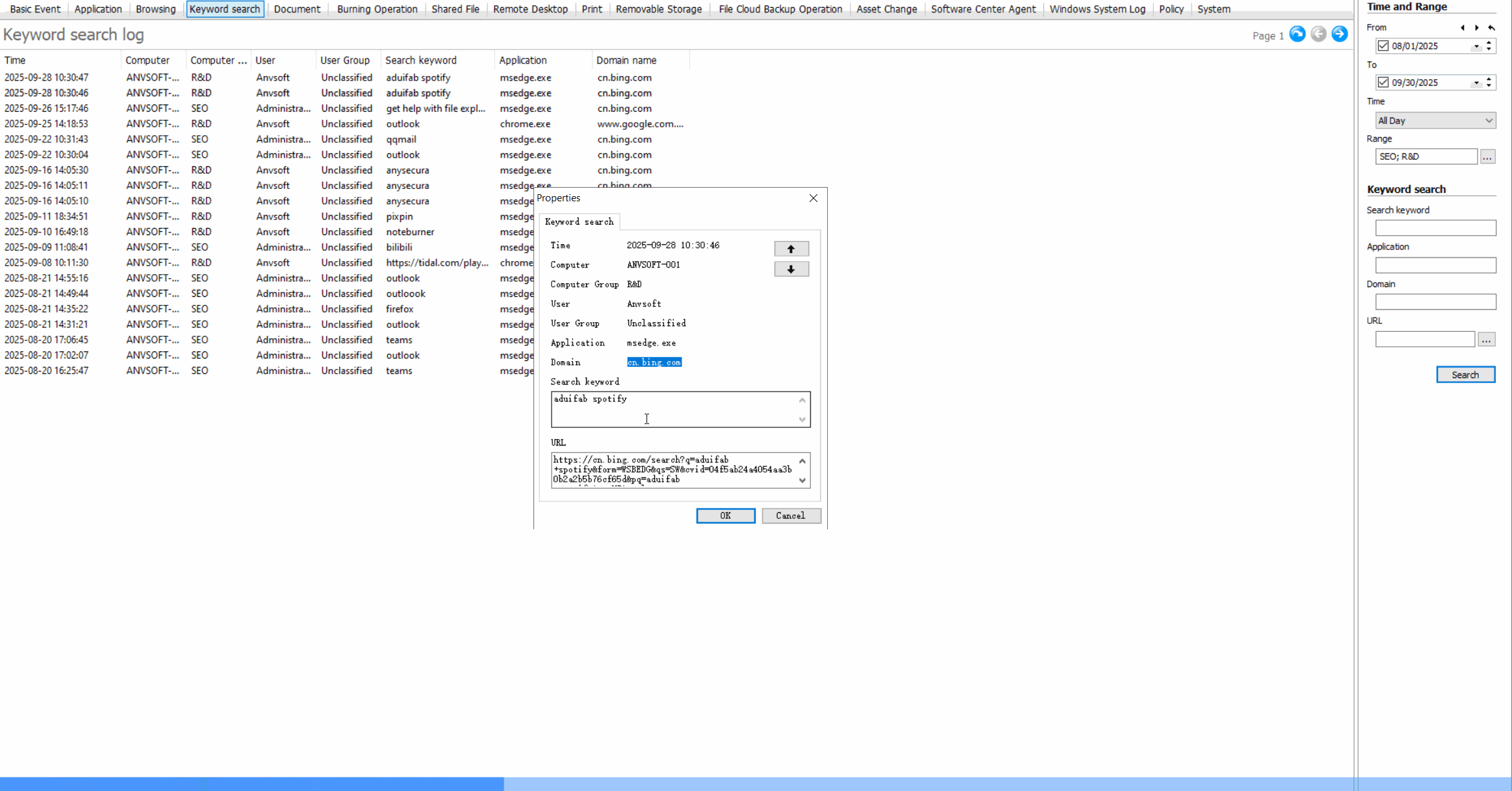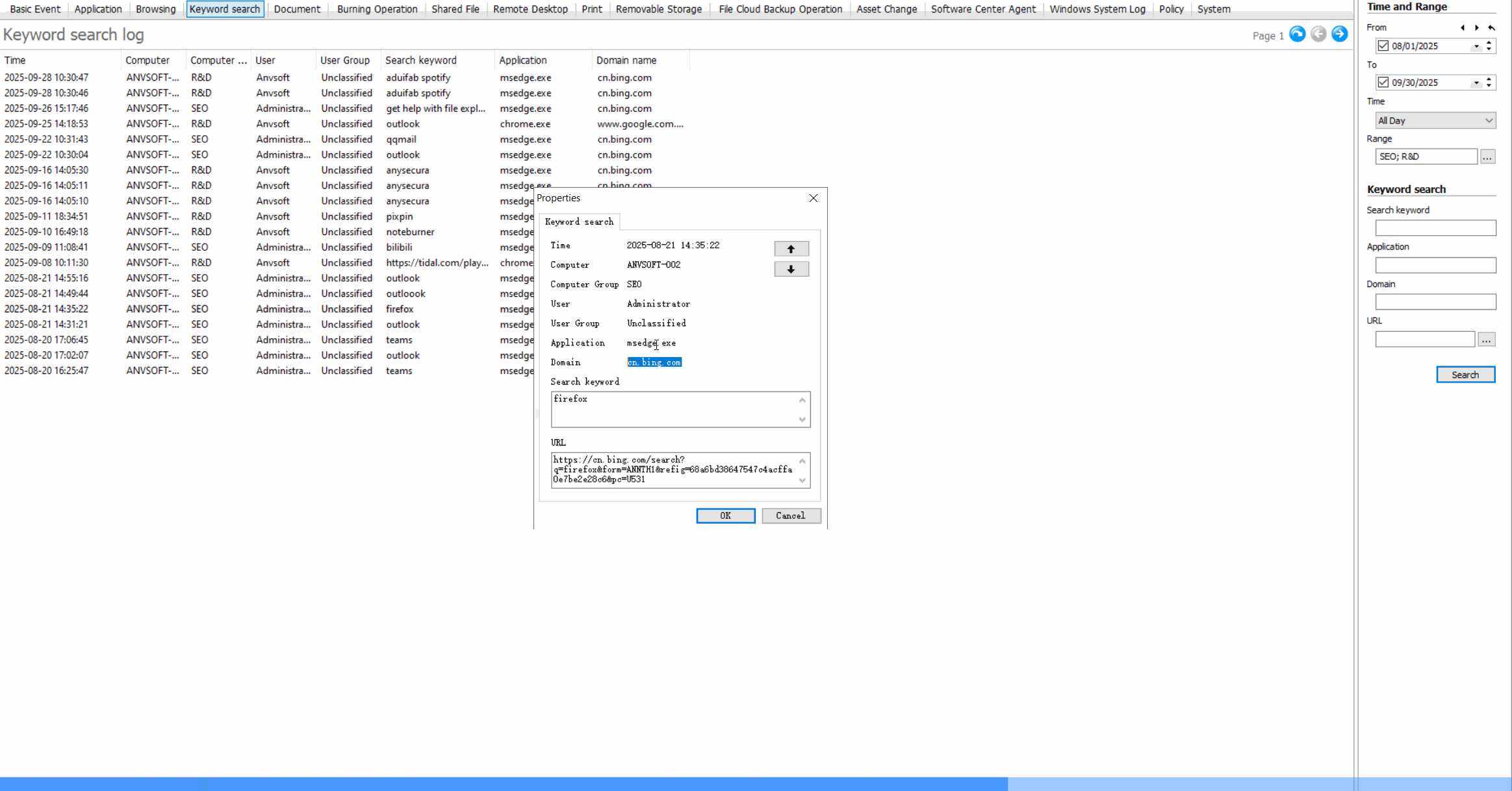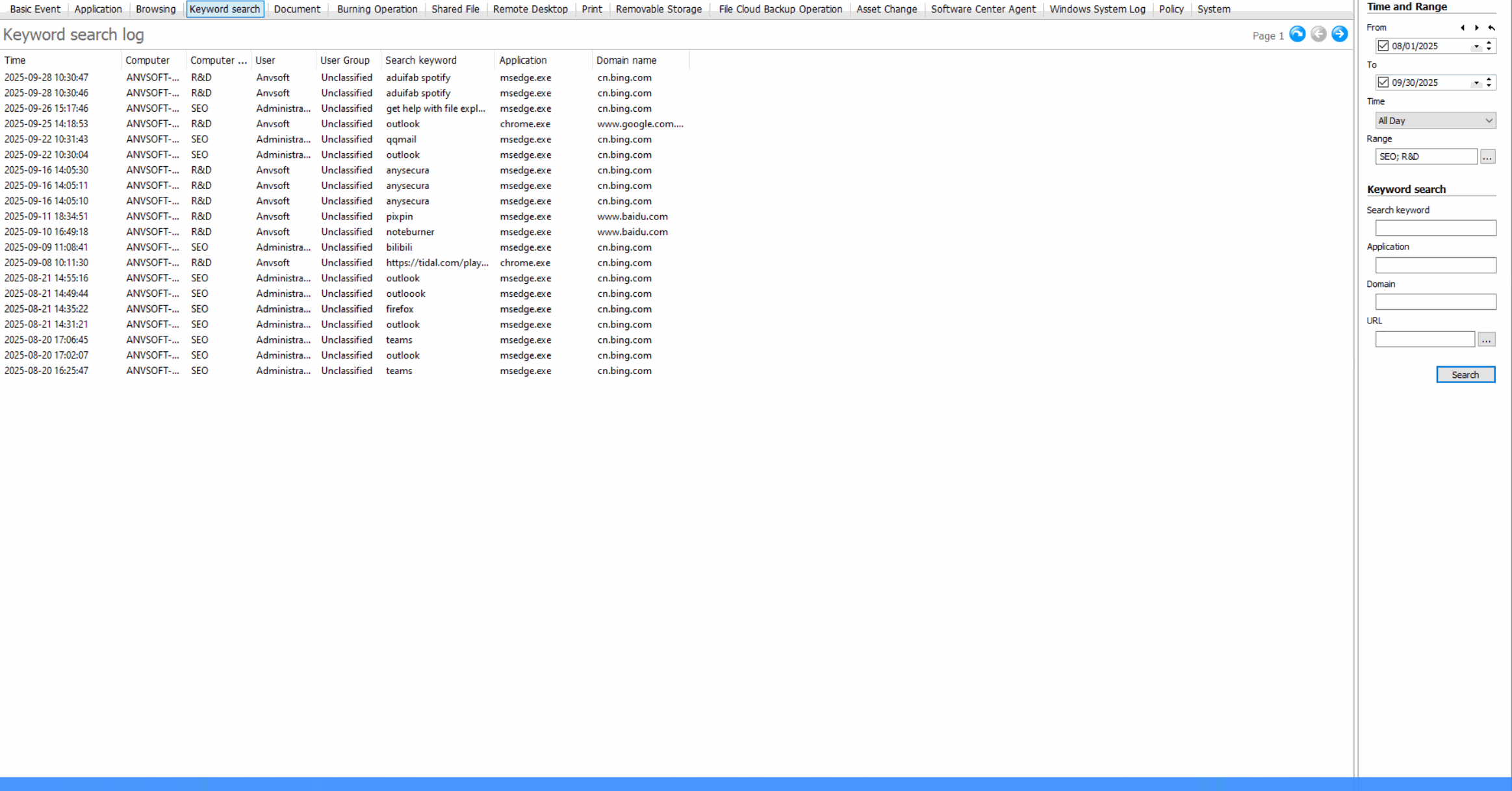
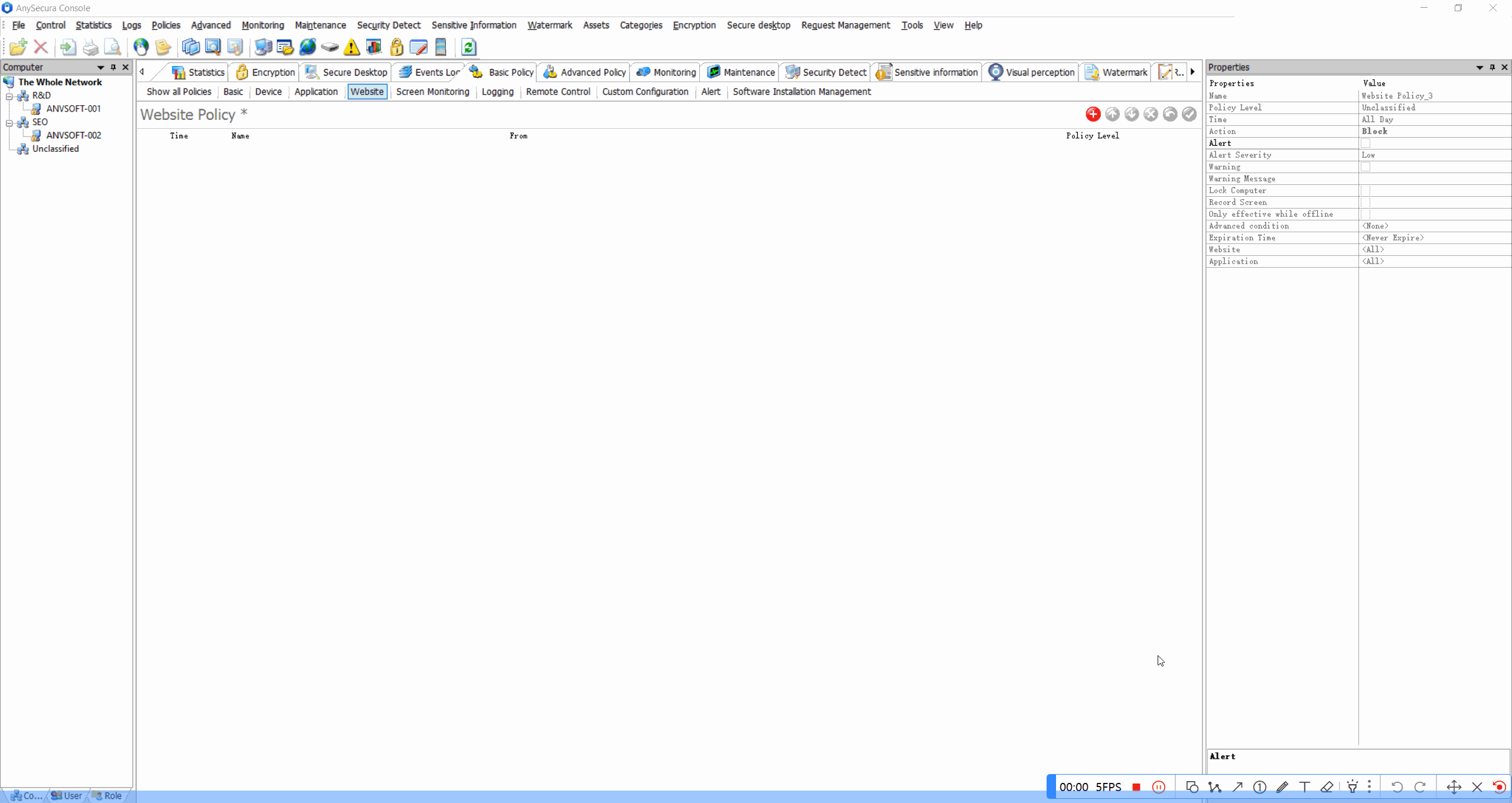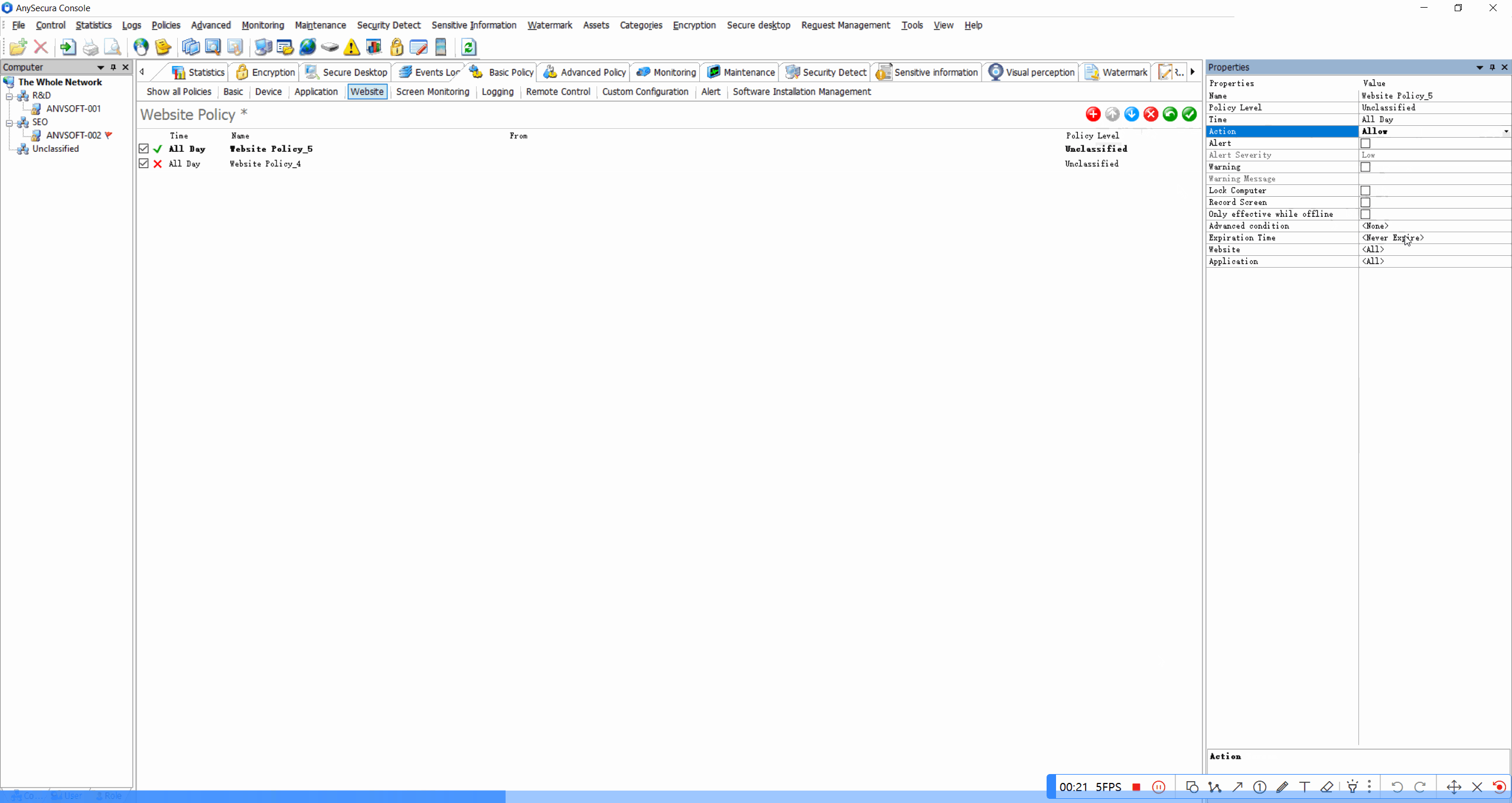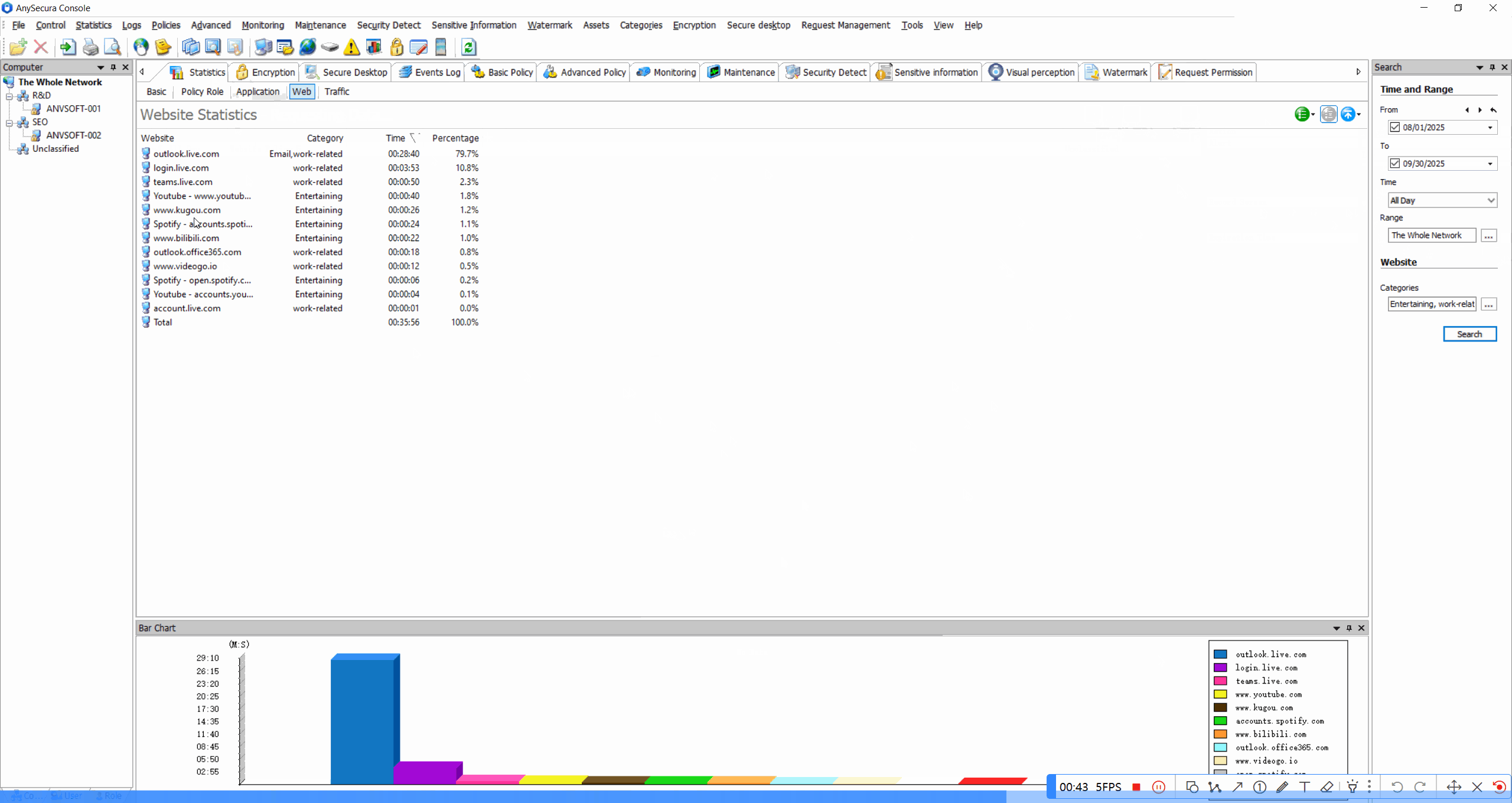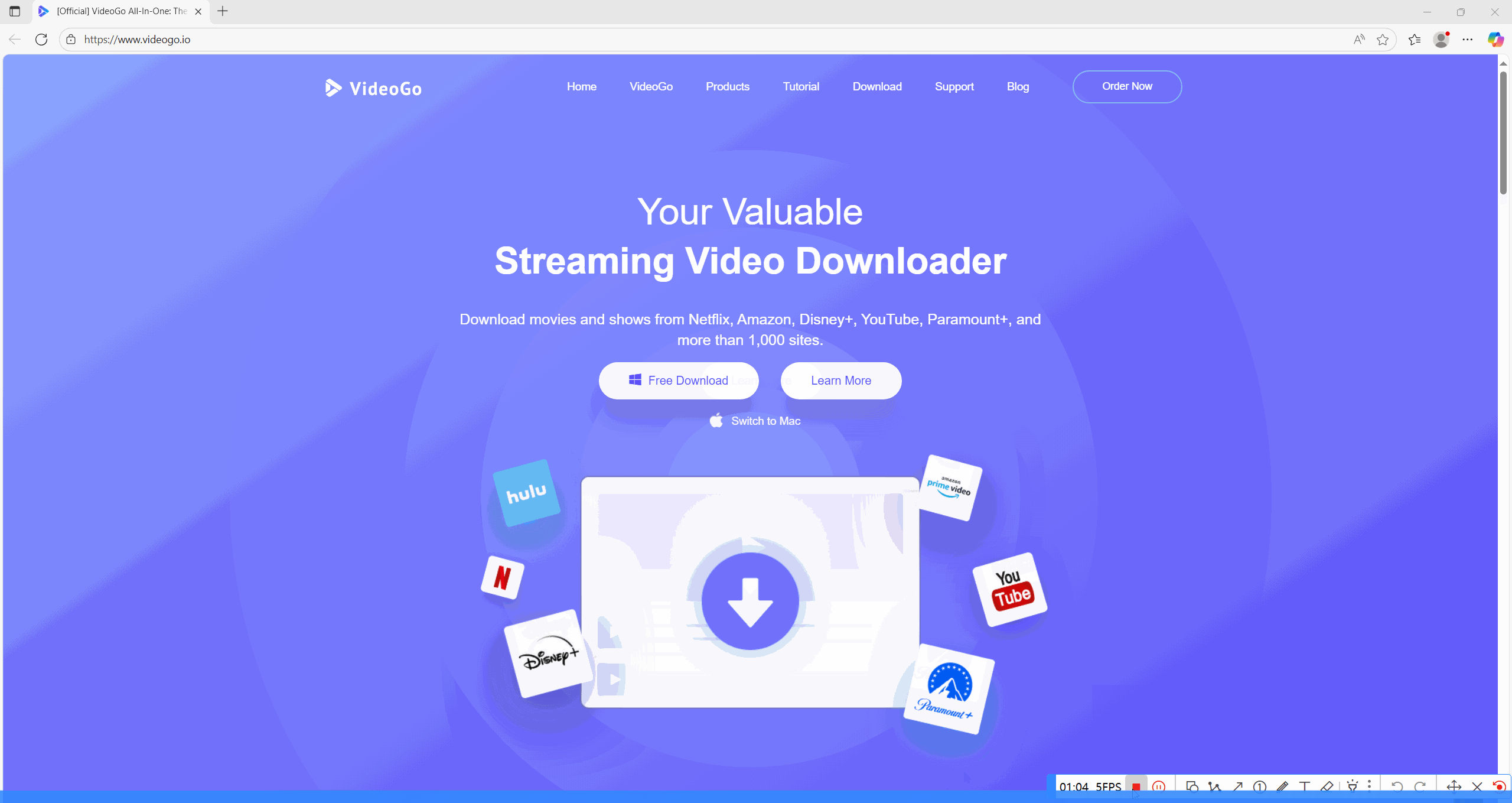
Web Browsing LogsRecord all websites visited, including timestamps, duration, and data transfer amounts.
-
Usage StatisticsGenerate reports on web usage patterns, most visited sites, and bandwidth consumption.
-
Keyword Search MonitoringTrack search queries containing sensitive or inappropriate keywords across search engines.
-
Site Classification & BlockingRestrict access to inappropriate or non-work-related websites based on content categories.
Web Control Benefits
Improve employee productivity, reduce bandwidth waste, prevent access to malicious websites, and maintain compliance with internet usage policies.
Transparent Encryption: Seamless Data Protection
-
Encryption Activity LogsTrack all encryption and decryption activities with detailed logs including user, time, file path, and operation status.
-
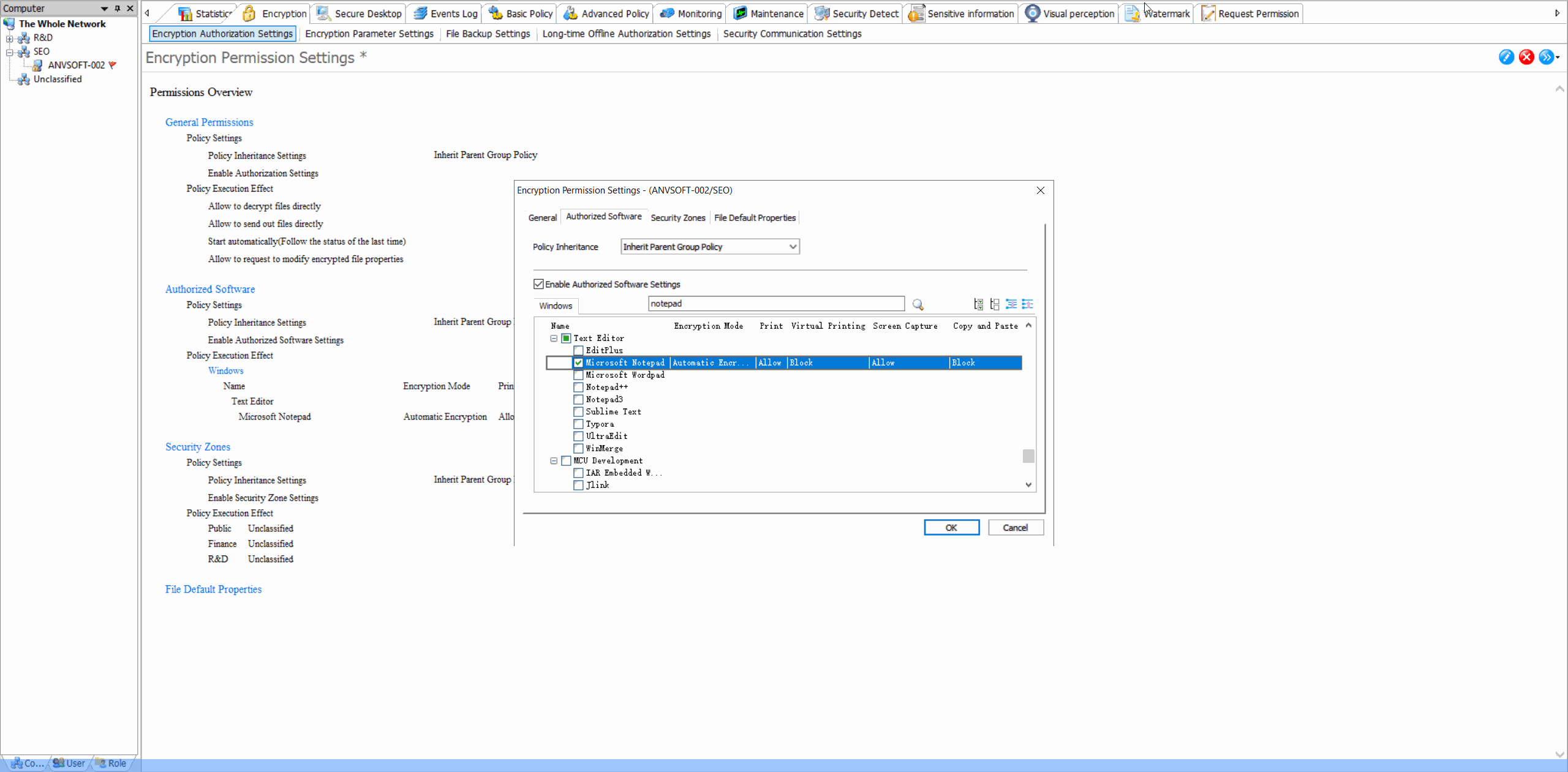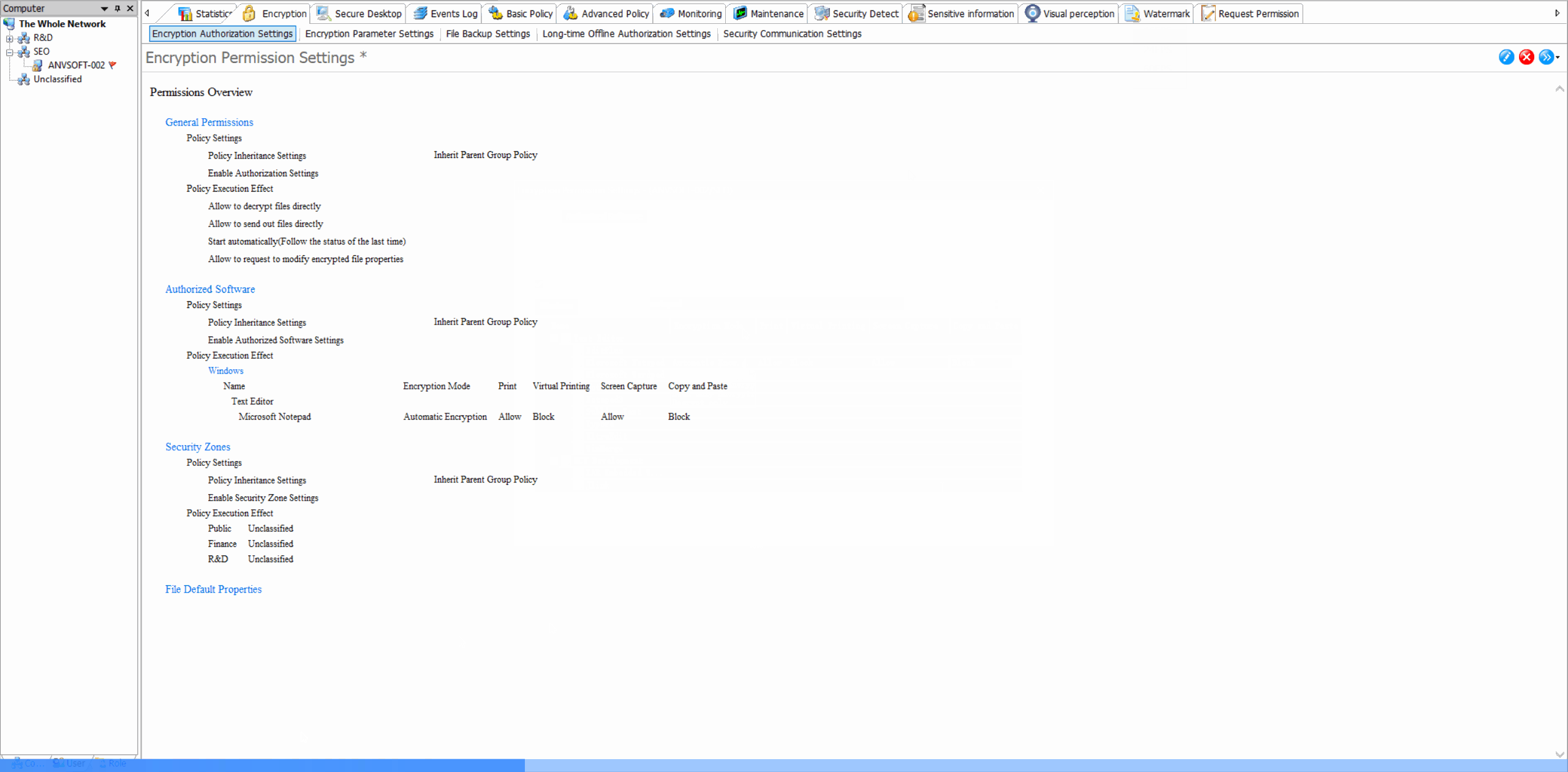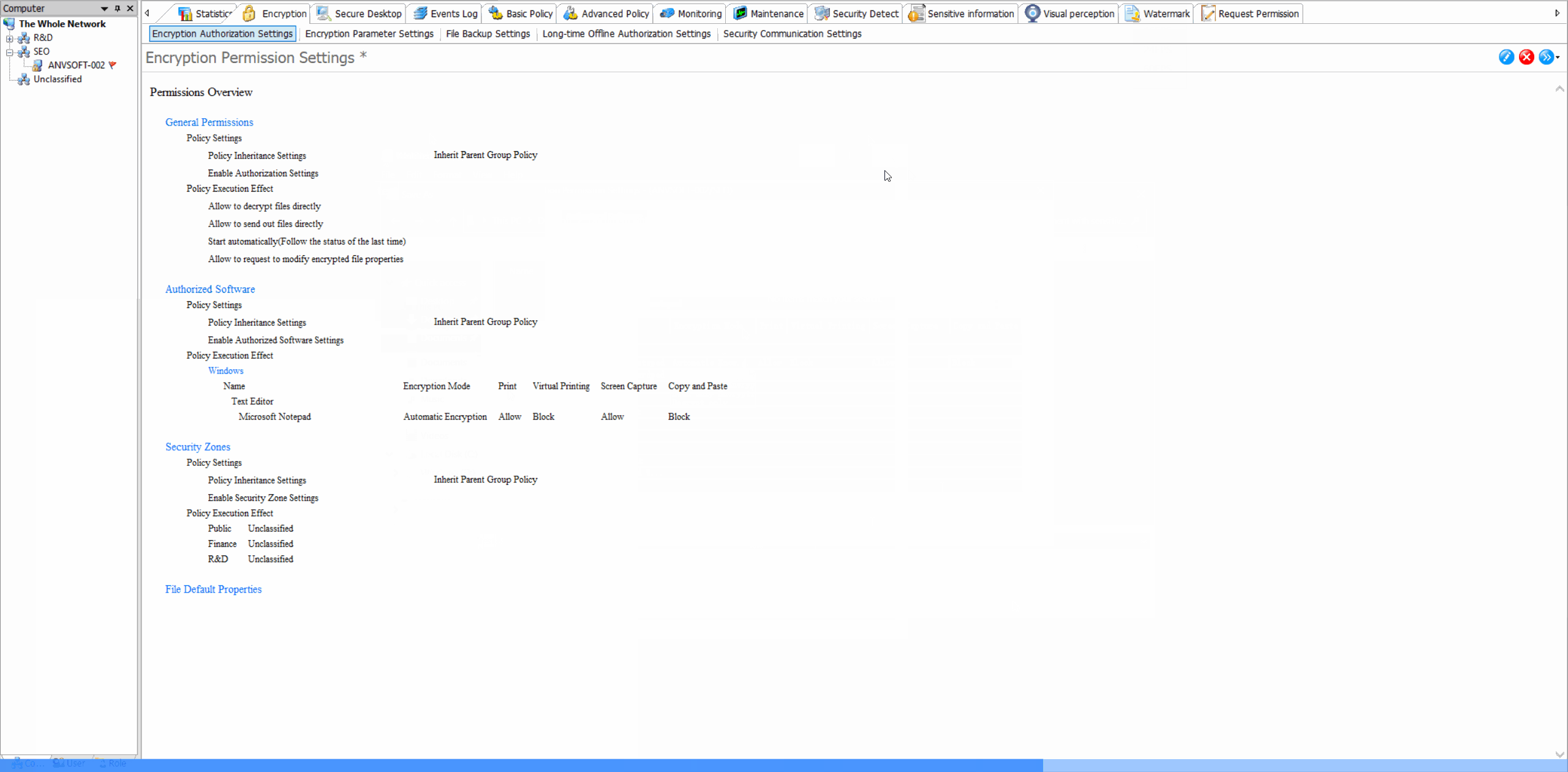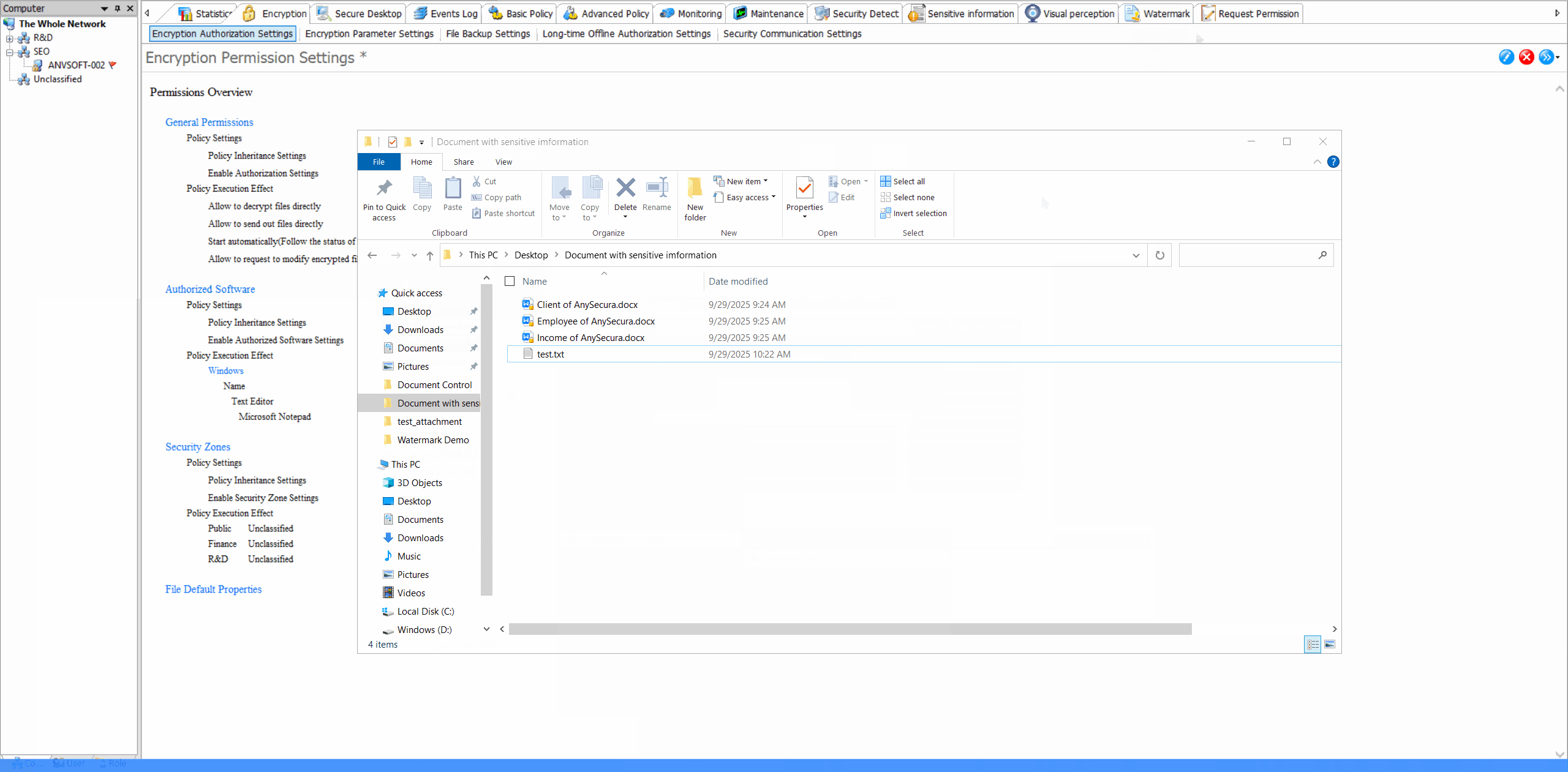
Authorized Software ManagementControl which applications are allowed to automatically encrypt/decrypt documents, preventing unauthorized software from accessing protected files.
-
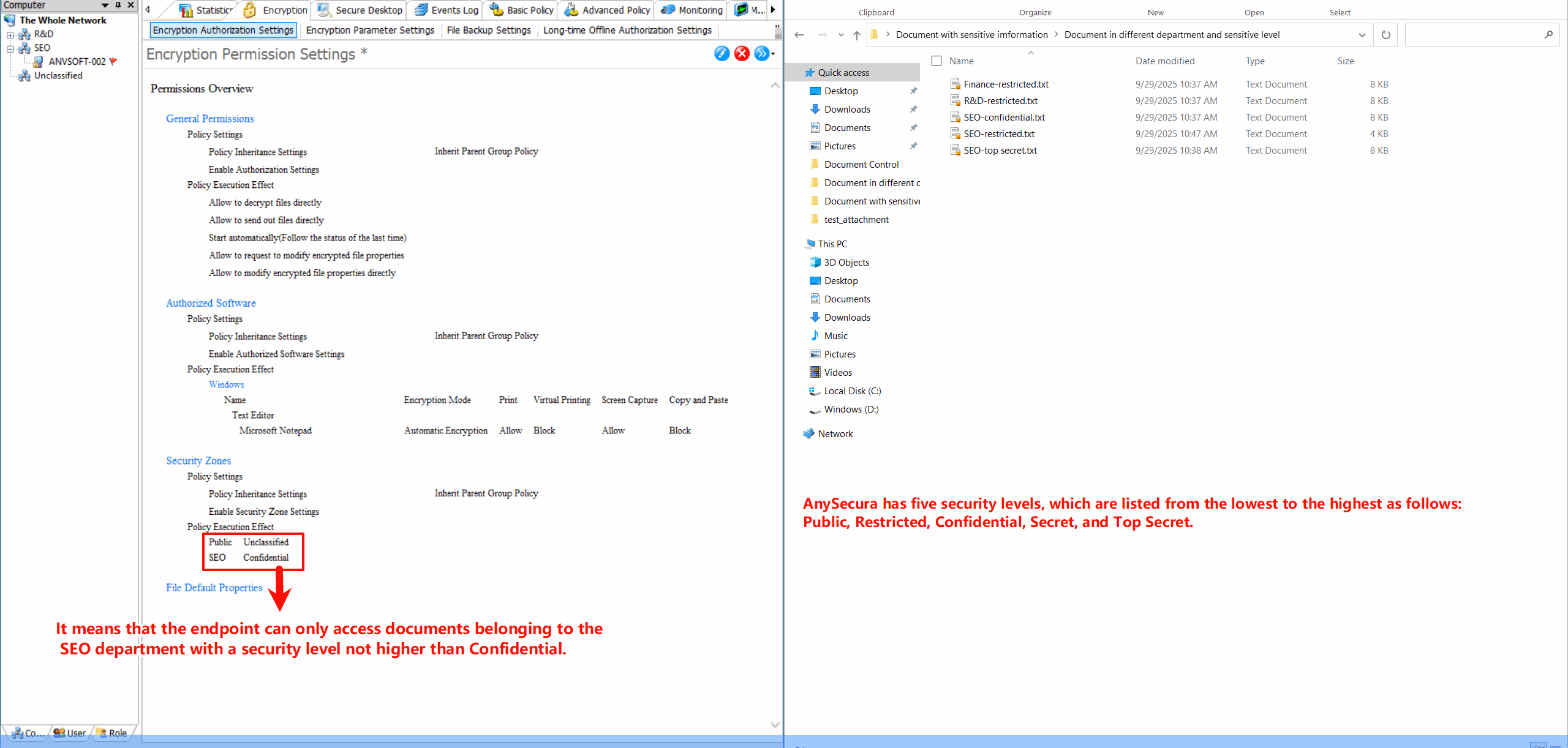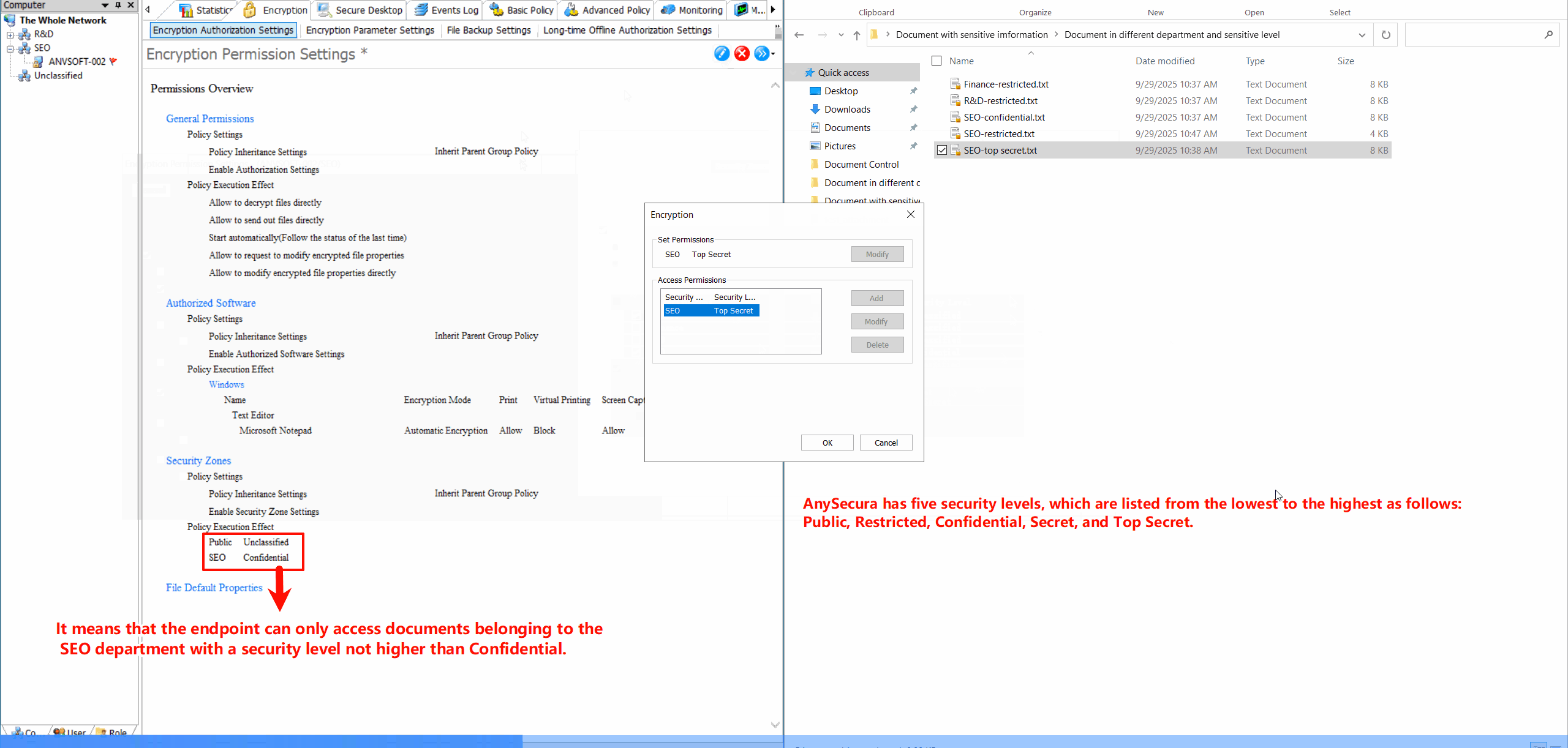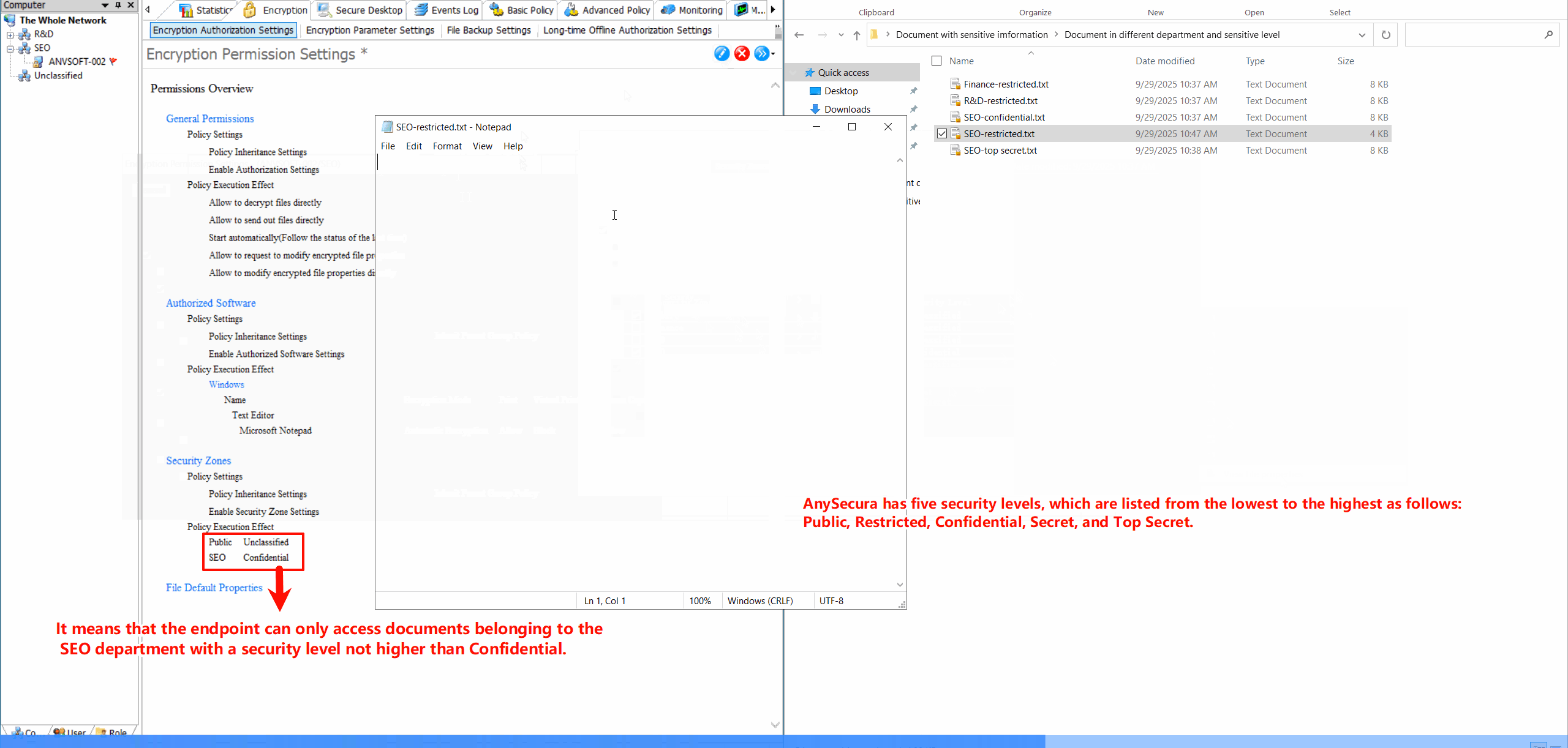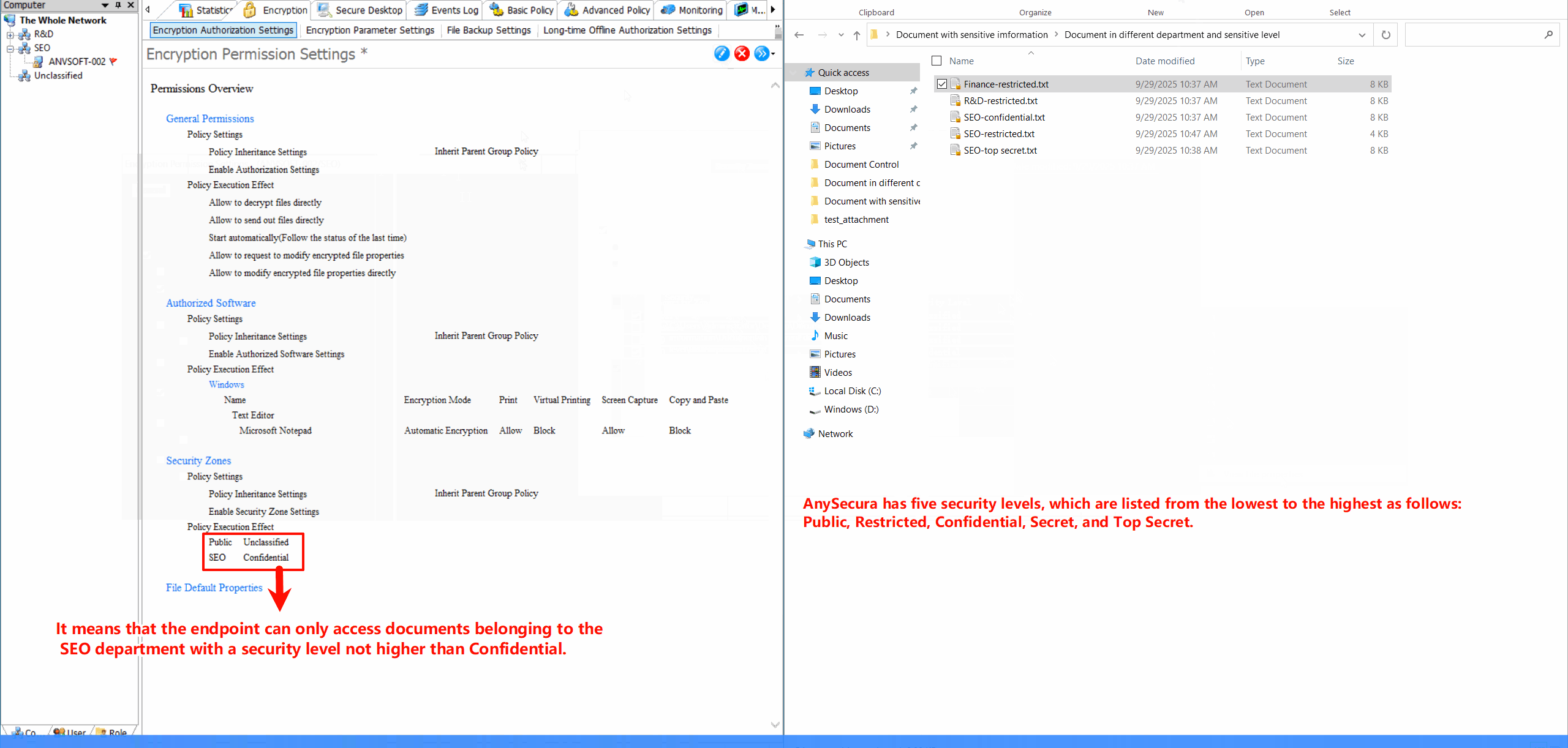
Security Zone ConfigurationDefine security zones with different encryption policies, allowing granular control over data protection based on location and sensitivity.
-
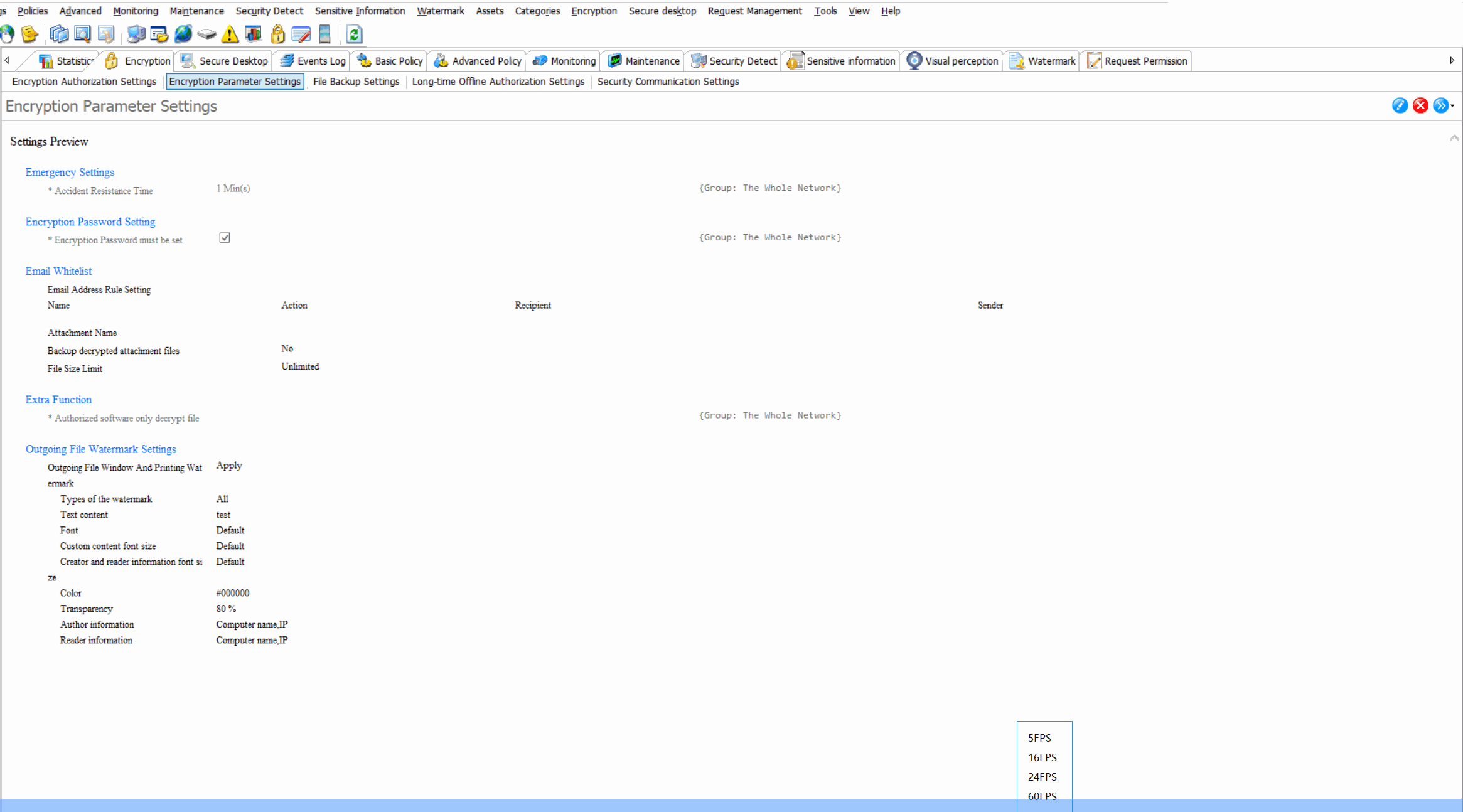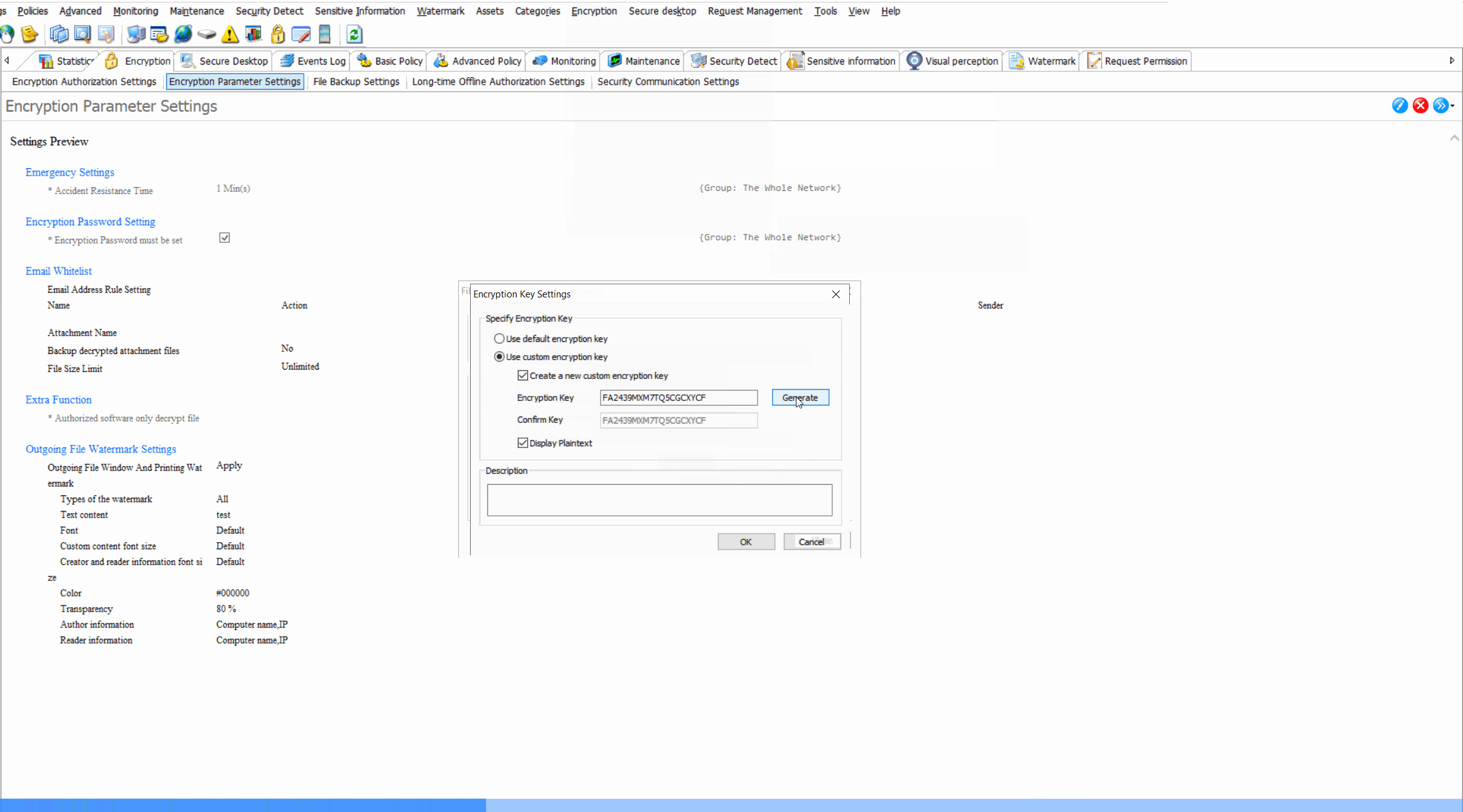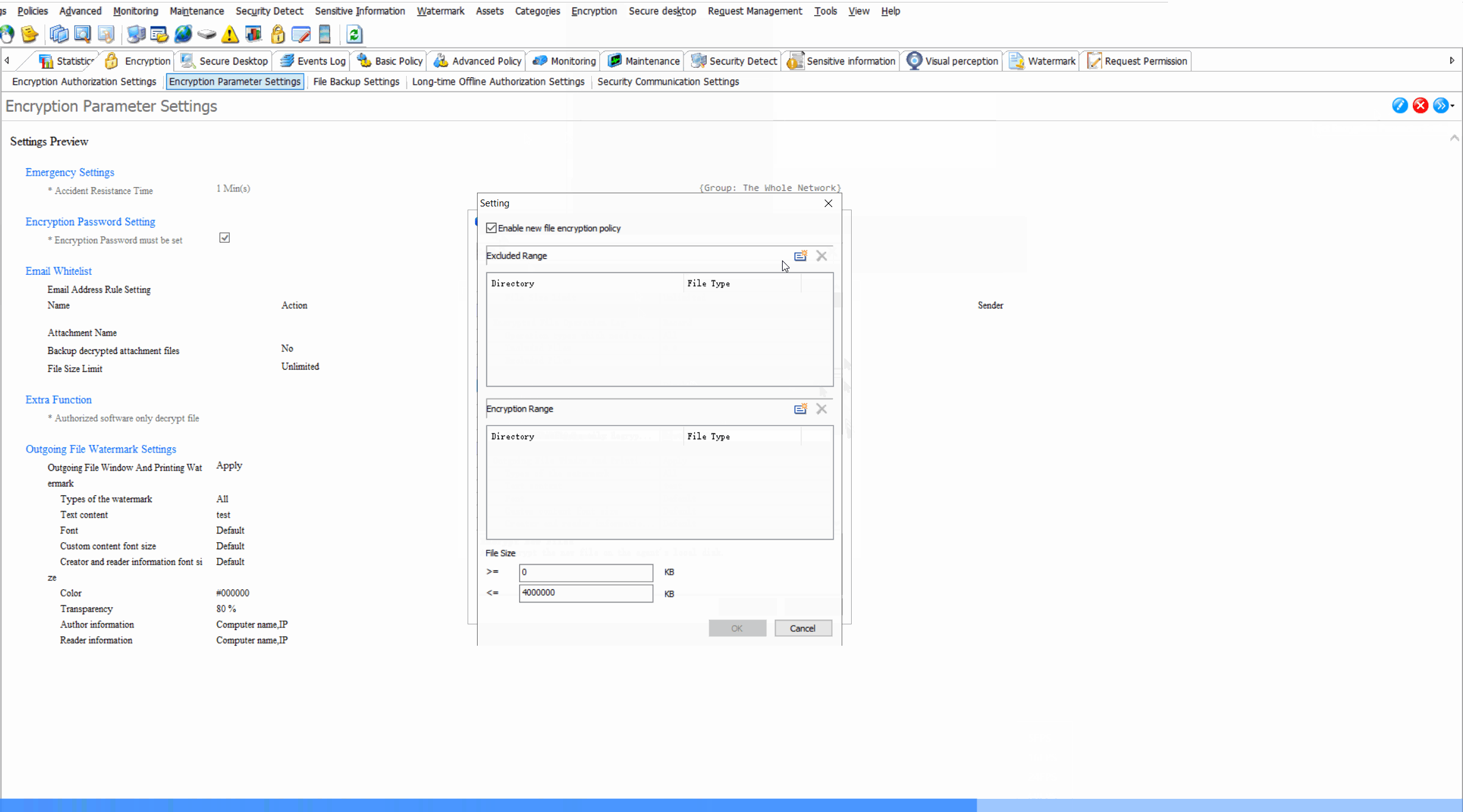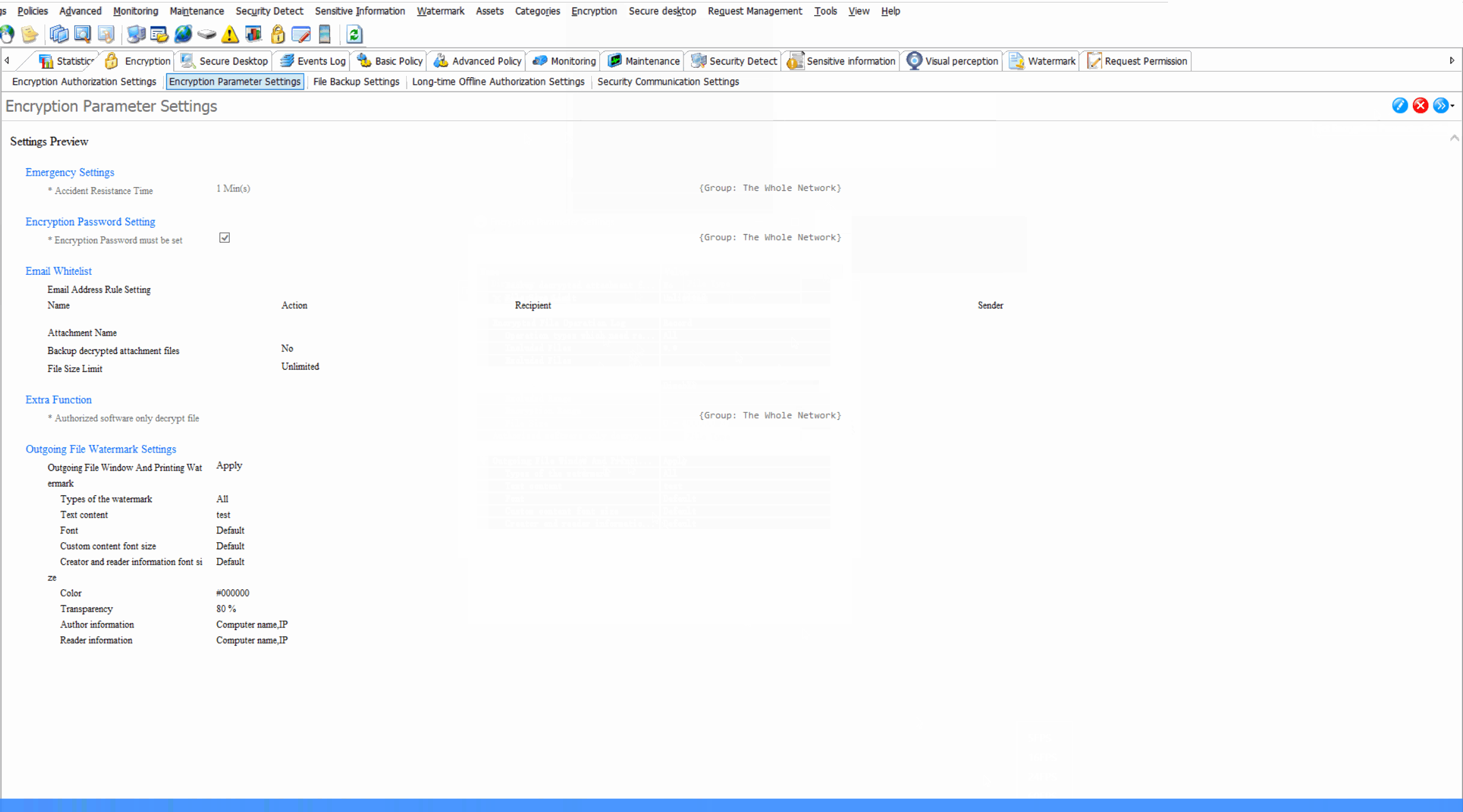
Encryption Parameter SettingsCustomize encryption algorithms (DES,AES-256, etc), key management policies, and automatic encryption triggers for different file types.
Advantages of Transparent Encryption
Protect sensitive data without disrupting user workflows, ensure only authorized personnel can access confidential information, and maintain compliance with data protection regulations.