The rapid evolution of network technology has dissolved the traditional security perimeter. In this new landscape of cloud, IoT, and remote work, the Zero Trust model has emerged as a critical solution. But what exactly is it, and what are its core principles? Let's delve into them.
What is Zero Trust?
Zero Trust is a cybersecurity concept centered on the principle of "never trust, always verify". Its core lies in breaking the "default trust" assumption of traditional security models. It asserts that all users, devices, or applications—whether inside or outside an enterprise’s network—should be treated as potential threats. Every access request must undergo strict authentication and authorization, with trust levels dynamically evaluated.
Cyber security protects your data from online threats. Learn its basics and how AnySecura DLP keeps your information safe. Learn more>>
Origin and Core Philosophy of Zero Trust
The concept of Zero Trust was born in 2010. Forrester analyst John Kindervag proposed it to tackle new security headaches. Why? Because cloud computing, IoT, and remote work were blurring the traditional boundaries of corporate networks. The old "castle-and-moat" defense was no longer enough.
The traditional perimeter security model assumes that internal networks are trustworthy while external networks are not. However, modern enterprise networks no longer have clear perimeters. Frequent internal threats and Advanced Persistent Threats (APTs) have forced the security system to shift from "perimeter defense" to "continuous verification".
Key concepts of Zero Trust can be summarized as follows:
- Never trust, always verify: By default, no person, device, or system is trusted—regardless of whether it is inside or outside the network.
- Principle of least privilege: Only the minimum permissions required to complete a task are granted, avoiding over-authorization.
- Dynamic trust assessment: Permissions are dynamically adjusted based on user behavior, device status, environmental risks, etc., rather than being authorized once and for all.
Zero Trust International Standards and Core Principles
Currently, there is no single global unified standard for Zero Trust. However, multiple international authoritative organizations have released framework-based guidelines, with the core goal of shifting from a "concept" to "executable industry norms" to help enterprises avoid chaos during implementation.
Standards from different organizations have distinct focuses: some center on technical architecture, while others emphasize compliance and implementation. Enterprises can choose references based on their specific industries and needs.
| Standard/Framework Name | Issuing Organization | Core Positioning and Features |
|---|---|---|
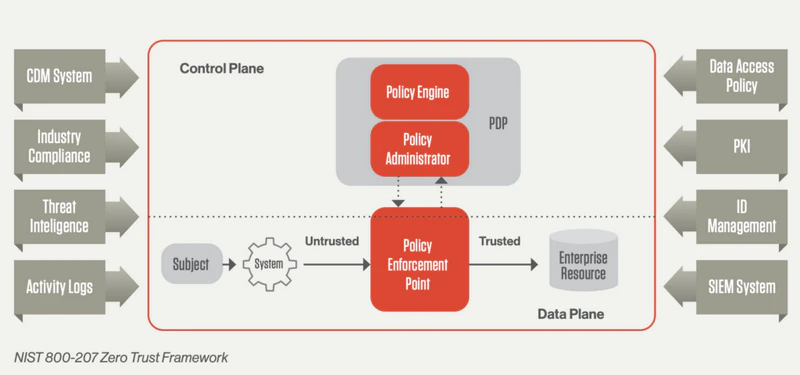
| NIST SP 800-207 | National Institute of Standards and Technology (NIST, U.S.) | The most influential "technical implementation-oriented" framework, suitable for reference by technical teams. It clarifies Zero Trust core components (e.g., policy engines, identity management), provides a phased implementation path, does not mandate technology selection, and emphasizes a "data-centric" approach. |
| Zero Trust Architecture (ZTA) Standard | International Organization for Standardization (ISO) / International Electrotechnical Commission (IEC) | Focuses on "global compliance," suitable for multinational enterprises. From the perspective of Information Security Management Systems (ISMS), it integrates Zero Trust into the existing ISO 27000 series standards and emphasizes compatibility with risk assessment and continuous improvement. |
| CIS Critical Security Controls (CIS CSC) | Center for Internet Security (CIS) | Focuses on "practical protection," suitable for small and medium-sized enterprises to get started quickly. It breaks down Zero Trust concepts into 20 executable security control measures (e.g., multi-factor authentication, least privilege), and provides specific configuration guidelines to lower implementation thresholds. |
| Cloud Security Alliance (CSA) Zero Trust Guidelines | Cloud Security Alliance (CSA) | Focuses on "Zero Trust for cloud environments," suitable for cloud-native or multi-cloud enterprises. For access scenarios involving cloud resources (e.g., SaaS, IaaS), it proposes a "Zero Trust cloud architecture" model to address security issues caused by blurred boundaries in cloud environments. |
Despite differences in their frameworks, all mainstream standards revolve around 5 core principles:
Identity is the Foundation of Access Control
Trust is no longer based on network location (e.g., IP address), but on the digital identities of entities such as users, devices, and applications. For example, when remote employees access internal systems via a corporate VPN, they must pass multi-factor authentication (MFA) and device health checks—instead of relying solely on the VPN connection.
Principle of Least Privilege
Only the minimum permissions required to perform a task are granted to prevent permission abuse. For example, employees in the finance department can only access financial systems, not the entire corporate internal network.
Real-Time Calculation of Access Control Policies
Permissions are dynamically adjusted based on user behavior, device status, environmental risks, etc. For example, if malicious software is detected on an employee’s device, the system will automatically restrict its access to sensitive data.
Controlled and Secure Access to Resources
All resource access requires mandatory identity verification, authorization, and encryption. For example, the Software-Defined Perimeter (SDP) technology in Zero Trust architecture hides resource ports and only opens access channels to authenticated users.
Trust Assessment Based on Multi-Source Data
Data such as user behavior, device status, and network traffic is continuously collected. AI analysis is used to evaluate trust levels. For example, Tencent’s iOA system identifies abnormal behaviors and triggers alerts by analyzing users’ login time, location, and operation habits.
Why Zero Trust Matters
Zero Trust addresses critical flaws in traditional security models like ACL and RBAC, while countering today's complex cyber threats. As cloud-native tech, remote work, and IoT become widespread, the old "perimeter defense" model fails against modern attacks. By rethinking security logic, Zero Trust provides a core solution. This analysis covers three areas: traditional model limits, Zero Trust advantages, and real-world threat drivers.
Traditional Security Flaws: Broken Trust Assumptions
Traditional models assume clear network boundaries, treating internal networks as safe and external ones as dangerous. This static trust model fails today, with flaws in two key areas:
1. Weak "One-Time Auth + Static Permissions"
Traditional security places firewalls, VPNs, and IDS at network edges, with little internal verification. Once attackers breach the perimeter—through phishing or supply chain attacks—they can use stolen permissions to lurk inside and move laterally.
⚠️Example: The 2017 WannaCry ransomware attack.
Exploiting a vulnerability in the Windows SMBv1 protocol (EternalBlue), attackers infiltrated corporate networks and rapidly propagated across internal systems that were implicitly trusted. Within hours, the malware spread to finance and R&D servers worldwide. The UK’s National Health Service (NHS) was severely impacted, suffering operational disruptions and financial losses exceeding £90 million.
This incident highlighted the fatal flaw of perimeter-based security: once the boundary is breached, the entire internal network becomes exposed.
2. Rigid Permissions, No Context
RBAC and ACL use static rules that can't adjust to real situations, causing two problems:
- Misses abnormal behavior: If an accountant exports bulk customer data at 2 AM, or an engineer accesses a unrelated financial system, traditional tools can't spot these anomalies, raising leakage risk.
- Ignores device/environment risks: When employees use infected personal devices or public Wi-Fi, traditional models only check user identity, not device health or network safety. This opens a "back door" to attackers.
Zero Trust Advantages: A New Security Approach
Zero Trust uses "never trust, always verify" to shift security focus from network perimeters to managing identities, devices, and behaviors. Its three mechanisms—continuous verification, least privilege, and dynamic adaptation—fix traditional flaws.
1. End "Static Trust" for Dynamic Threats
Traditional "authenticate once, trust forever" systems can't stop attackers who steal access. Zero Trust ensures precise control through continuous checks and dynamic permissions:
- Continuous verification: Every access request, internal or external, checks three factors simultaneously:
- Identity: Confirm via MFA (password + code or fingerprint).
- Device health: Check for latest patches, active antivirus, and malicious processes.
- Behavior: Analyze operation frequency, time, and location. Alerts trigger if actions seem abnormal.
- Dynamic permissions: Access rights change based on real-time risk. If the system finds anomalies—like strange device processes or unfamiliar login locations—it instantly downgrades permissions (e.g., to "read-only") or freezes the account.
This approach is common. For example, Windows Defender restricting a risky file's access mirrors Zero Trust's "dynamic control" applied to all enterprise resources, cutting abuse risk.
2. Enforce Least Privilege
Traditional models often grant excessive permissions through "role inheritance." For example, regular employees might access entire department shares, not just needed files. This "permission overflow" lets attackers expand their reach. Zero Trust uses Just-In-Time (JIT) authorization and limited sessions to minimize access.
JIT Authorization: Temporary Access
For rare, high-risk tasks, permissions are granted temporarily and revoked after use.
⚠️Example: Large bank transfers. A bank's Zero Trust system might set a default transfer limit. For a larger transfer, the customer must apply. The system then checks:
- Account status: Recent logins and transaction patterns.
- Identity verification: Additional confirmation via facial recognition or codes.
- Device security: Scan for risks on the device used.
Only after passing these checks is temporary large-transfer permission granted, then immediately revoked.
Even with a stolen password, attackers can't make big transfers without real-time checks, greatly reducing theft risk.
Least Privilege Sessions: Limited-Time Access
For short-term collaboration, users get time- and scope-limited permissions that expire automatically.
⚠️Example: Project document review. If a developer named Tom needs to view a tester's document. The Zero Trust system can create a temporary session:
- Scope: Read-only access to that specific document.
- Time: Access expires after 10 minutes.
- Re-verification: If Tom needs more time, he must re-apply for the system to re-check his tasks and behavior.
Even if Tom's account is hacked, the attacker can only briefly read one document, minimizing damage.
3. Solve Perimeter Failure in New Networks
With cloud-native, remote work, and IoT, traditional network boundaries have blurred, making perimeter defense obsolete. Zero Trust's "borderless security" fits these new scenes.
Cloud & Remote Work: Identity-Centric Security
Traditional models struggle with hybrid cloud and remote access:
- Blurred boundaries: Enterprise data spreads across public clouds, private clouds, and on-prem servers. Traditional firewalls can't protect public cloud resources. For example, an e-commerce firm keeping promo data in the public cloud and user data privately risks cross-cloud attacks during data sync.
- Uncontrolled mobile access: When employees use personal devices on home or café Wi-Fi, traditional models can't assess device or environmental risks, raising leakage chances.
Zero Trust builds borderless security around identity:
- Identity-based control:
- Strong authentication: All access needs MFA.
- Dynamic authorization: Permissions are finely split by role and task.
- Lifecycle management: Access updates automatically when employees join, move, or leave.
- Device security checks:
- Compliance checks: MDM tools ensure devices meet security standards (patches, antivirus, encryption). Non-compliant devices are blocked.
- Device identity: Each device has a unique ID. The system verifies this identity and checks for risks at each login.
- Behavior-based risk analysis:
- Baseline monitoring: AI establishes normal behavior patterns (like edit frequency). Operations outside the baseline trigger alerts and access suspension.
- Anomaly response: AI detects unusual logins or data access, auto-downgrading permissions and alerting security teams.
IoT and OT Systems: Securing Industrial Devices
IoT Operational Technology (OT) systems, like PLC controllers, are often outdated and lack security, making them easy targets.
- Device vulnerabilities: Many PLCs use static IPs and default passwords ("admin/123456"), letting attackers easily take control to disrupt production or steal data.
- No device authentication: Traditional models don't verify industrial device identities, allowing fake devices to join the network.
Zero Trust secures OT systems via device identity and dynamic credentials:
- Device identity authentication: Each industrial device gets a unique, unforgeable digital ID (like a hardware fingerprint). Devices must pass identity checks to connect, blocking fakes.
- Dynamic credential management: Static passwords are replaced with short-lived tokens or quantum keys that update frequently. Even if intercepted, they quickly expire. Transmission is encrypted (e.g., TLS 1.3) for safety.
This approach defends against industrial device attacks, keeping production stable.
Real-World Threats: Making Zero Trust Essential
Modern cyberattacks are targeted, hidden, and widespread, overwhelming traditional defenses:
- Targeted phishing: Attackers use personal info (e.g., from LinkedIn) to send fake "HR notices," tricking employees into giving passwords.
- Supply chain attacks: Hackers compromise supplier software (like the 2021 SolarWinds incident) to bypass firewalls and enter networks directly.
- Constant data leaks: 74% of breaches involve human factors (Verizon 2023), which traditional models can't stop due to poor permission and behavior control.
Zero Trust specifically counters these threats:
- Against phishing: MFA and device checks block attackers even with stolen passwords.
- Against supply chain attacks: Continuous verification finds abnormal processes and reduces access.
- Against permission abuse: Least privilege limits data exposure.
Clearly, Zero Trust is not just an upgrade but a necessary choice. Only by replacing "static trust" with a dynamic, comprehensive security system can businesses protect their data and operations continuously.
How to Implement Zero Trust?
The implementation of Zero Trust is a progressive process that can be divided into the following key steps:
Step 1: Asset Inventory and Risk Assessment
Conduct a comprehensive inventory of the enterprise’s digital assets (data, applications, devices, and services), and evaluate their security risks and importance.
Step 2: Develop Security Policies
Based on the inventory results, establish security policies covering identity, devices, applications, and data, and define clear access rules.
Step 3: Establish a Unified Identity and Access Management (IAM) System
Deploy an IAM system to centralize the management of the user lifecycle, and enforce multi-factor authentication (MFA) and fine-grained access control.
Step 4: Strengthen Device Security Management and Control
Register and manage all connected devices, use tools such as MDM and EDR to ensure device compliance, and monitor their status in real time.
Step 5: Advance Network Micro-Segmentation
Divide the network into fine-grained security zones (micro-segments) and implement strict access control policies between zones to prevent lateral movement by attackers.
Step 6: Enhance Application and Data Protection
Strengthen application security through measures such as hardening, encrypt sensitive data both in transit and at rest, and establish access policies based on data sensitivity.
Step 7: Build a Continuous Monitoring and Analysis System
Utilize systems such as SIEM, IDS/IPS to collect logs and traffic, and employ AI and machine learning for behavioral analysis to detect threats in real time.
Step 8: Dynamically Adjust Security Policies
Regularly evaluate and dynamically adjust security policies based on monitoring results and business changes, enabling continuous evolution of the security framework.

Discover how DLP software delivers compliance, prevents insider threats, and secures sensitive information across endpoints, cloud services, and networks. Learn more>>
AnySecura: A Solid Step toward a Zero-Trust Security Posture
Implementing Zero Trust is a journey, not a one-time project. It demands a layered strategy combining multiple technologies and policies—and securing endpoints, which are both the most vulnerable and most critical access points, lies at the heart of this framework. After all, every data access attempt ultimately happens through an endpoint: a laptop, server, or mobile device. AnySecura offers a comprehensive endpoint security management platform that aligns strongly with Zero Trust principles, helping organizations take that essential first step toward a resilient Zero Trust defense.
How AnySecura Supports Your Zero Trust Strategy
AnySecura’s integrated modules directly reinforce several core components of a Zero Trust architecture:
1. Strengthened Authentication & Granular Access Control
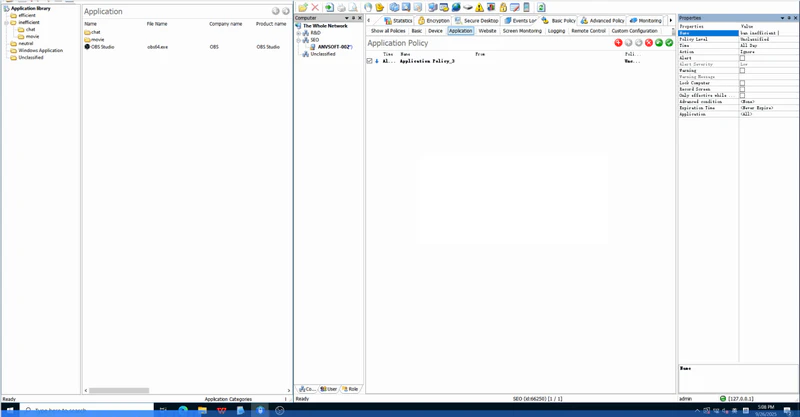
Zero Trust requires verifying every access request. AnySecura enforces strict device and application controls to ensure users only access what they’re authorized to, from authorized devices.
- Peripheral Control: Regulates use of USBs, smartphones, and printers to prevent data exfiltration via unauthorized channels.
- Application Control: Restricts software execution to approved programs, blocking potential malware.
- Network Control: Limits access to specific websites or services, supporting early-stage micro-segmentation.
2. Continuous Monitoring & Auditing
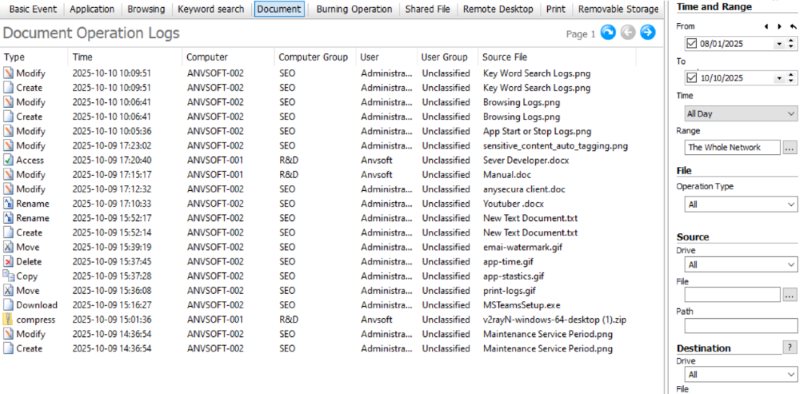
With Zero Trust, verification never stops. AnySecura delivers extensive auditing to track nearly all endpoint activities—creating a reliable evidence base for ongoing trust evaluation.
- Screen Recording: Captures user sessions for clear incident investigation and forensic proof.
- Activity Logging: Tracks file actions, app usage, web visits, print jobs, and chat messages for full visibility.
- Risk Analytics: Applies intelligent analysis to audit data, helping teams quickly detect policy violations and emerging threats.
3. Data-Centric Protection
The ultimate goal of Zero Trust is to safeguard critical assets: your data. AnySecura’s triple-shielded data loss prevention system, especially its encryption engine, delivers robust last-line defense.
- Transparent Encryption: AnySecura automatically encrypts sensitive files. They remain accessible inside the trusted environment but become unusable if leaked or transferred out.
- Content-Aware Protection: Identifies sensitive data—IDs, bank details, source code—and auto-triggers encryption or blocks external sharing.
- Secure External Sharing: Offers controlled document sharing with customizable limits: passwords, view counts, expiration dates, and restrictions on printing/screenshots.
Conclusion
Transitioning to a Zero Trust architecture is now essential for safeguarding core enterprise assets. While implementing this framework requires systematic effort, proven solutions make it achievable. With AnySecura's specialized endpoint security platform, organizations can immediately enforce core Zero Trust principles at the most vulnerable layer—the endpoint.
Through granular access control, continuous monitoring, and robust data encryption, AnySecura not only mitigates data leakage and regulates user behavior, but also establishes the foundation for a complete Zero Trust security posture. This enables secure business operations in an era where "never trust" is the new standard.


