As security threats continue to evolve and become increasingly sophisticated, organizations across industries face constant risks from both inside and outside their networks. Traditional defenses like firewalls and antivirus software are no longer enough to counter subtle and adaptive threats. What enterprises need is an ocular insight into potential and ongoing risks — a system that can secure anyting before any damage occurs or escalates.
This is where User and Entity Behavior Analytics (UEBA) comes in. It can offer an intelligent, data-driven way to detect anomalies and prevent incidents in advance.
What is UEBA?
To understand what UEBA is, it helps to first break down what the “U” and “E” represent.
The “U” refers to the users within the organization who have access to its networks and systems — including the accounts they use to interact with these systems.
The “E” stands for non-human entities related to business processes, which complement user analysis. This includes endpoint devices (e.g., PCs, mobile phones), servers, applications, databases, and other network-connected assets.
Therefore, UEBA refers to the real-time, detailed analysis of behavioral data generated by both users and entities through data analytics and machine learning. Its goal is to detect ongoing risk events and potential threats, then trigger alerts and responses accordingly.
It acts like a “God’s Eye” within an organization — making every hidden security threat visible and traceable.

Insider threats in 2026 are smarter and harder to detect. Explore real cases, key trends, and practical strategies to prevent internal risks before they cause serious damage. Learn more>>
Why UEBA Is Needed?
Traditional security tools can no longer keep pace with today’s complex and rapidly evolving threat landscape. Cyberattacks, insider risks, and IT asset misuse often bypass manual oversight and rule-based defenses because they appear legitimate on the surface. Driven by the urgent need for stronger security and powered by advances in machine learning and AI, UEBA has emerged as a new-generation solution.
Specifically, UEBA is designed to address the following threats and challenges:
- Insider Threat Detection: UEBA collects, aggregates, and analyzes user behavior data—such as application usage, document operation logs, web browsing history, instant messaging, and email activity. By combining historical data, contextual information, and trained models, it detects anomalous behaviors in real time and identifies potential insider threats early. For instance, by monitoring email activities, UEBA can detect potential data leakage attempts from employees as they occur. The collected data also supports long-term trend analysis and forensic investigations.
- Network Monitoring and Defense: UEBA continuously monitors bandwidth usage and traffic patterns of servers, routers, and other endpoint devices across the organization. It compares real-time network flow with historical data to identify anomalies, helping detect potential or ongoing data leaks and cyberattacks before they escalate.
- IT Asset Protection: As the number of users and entities within an enterprise grows, managing hardware and software assets becomes increasingly complex. UEBA enables cost-effective monitoring of software installation and removal, preventing users from installing pirated or unsafe applications that may introduce security or legal risks. It also tracks hardware usage in real time to ensure devices are functioning properly and remain untampered.
As security threats become more sophisticated, addressing the above challenges is essential to building a stronger security posture. UEBA is designed to meet these needs—so how exactly does it work?
How Does UEBA Work?
UEBA operates as a systematic project that follows a standard operating procedure (SOP) to ensure effective deployment. In essence, it works through five core stages to keep your organization secure. Here’s how it works:
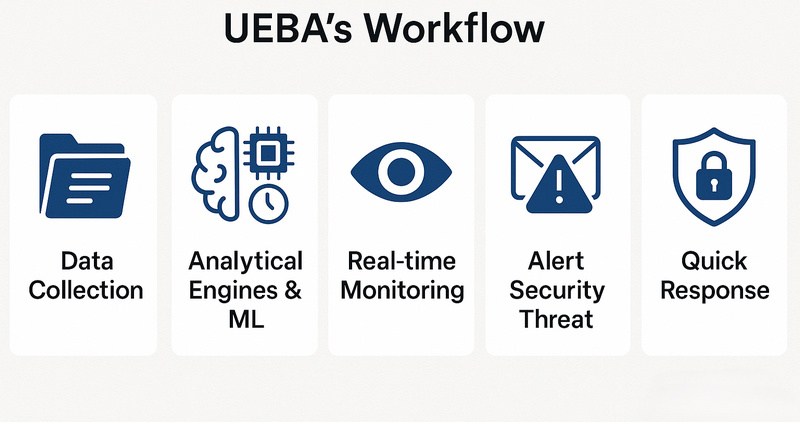
1. Data Collection
Accurate threat detection begins with comprehensive data collection. Since machine learning relies heavily on behavioral data, the more detailed and diverse the data, the smarter the system becomes. Below are the types of data typically collected:
- From Users:
- Application Usage Metrics
- File Operation Logs
- Browsing History
- Login/Logout Records
- ...
- From Entities:
- System Event Logs
- Network Traffic Data
- Software Installation/Uninstallation Records
- Hardware Usage Data
- ...
Once the data is collected, analytical engines and machine learning models begin to “listen and learn” from it, forming the foundation of the system’s intelligence.
2. Analytical Engines and Machine Learning
The analytical engines assess whether the gathered data indicates any potential threat, while machine learning algorithms use these results for continuous training. Over time, the UEBA system learns to recognize what behaviors suggest risks and how severe those risks might be. This is when the UEBA system develops its ability to think.
3. Real-time Monitoring
UEBA continuously monitors user and entity behavior in real time. When anomalies appear, the system evaluates them to determine if a security incident may be unfolding. This is where UEBA begins to see threats as they happen.
4. Threat Alerts
When a potential threat is detected, the UEBA system immediately notifies IT managers or security teams through predefined alert channels — such as email or desktop notifications — describing the type and severity of the threat. This is how UEBA tells your team what’s happening.
5. Automated Response
Before human intervention takes place, UEBA can take proactive actions to contain threats and minimize damage. For example, if a privileged user copies or deletes a large volume of corporate documents within a short period, UEBA may flag it as an insider threat and automatically suspend the user’s access to prevent data loss. In this way, the system acts as a 24/7 security guardian.
Building on this principle, the AnySecura Data Loss Prevention solution extends this control across the entire document lifecycle — from creation and modification to transfer and deletion. When abnormal file operations occur, control policies are immediately enforced to block the action and back up affected files in real time. The system simultaneously warns the user and alerts the administrator to ensure rapid response and minimal loss.
After understanding the UEBA workflow, it’s clear that this system plays a crucial role in proactively identifying, preventing, and mitigating security threats before they escalate.

Discover how DLP software delivers compliance, prevents insider threats, and secures sensitive information across endpoints, cloud services, and networks. Learn more>>
FAQs about UEBA
How is UEBA different from traditional security tools?
Traditional tools such as firewalls and antivirus software primarily focus on defending against known threats or rule-based patterns. UEBA, on the other hand, leverages machine learning and advanced analytics to detect unusual behaviors — enabling it to identify not only known attacks but also previously unseen threats such as zero-day exploits and insider risks.
Is UEBA difficult to deploy?
Not at all. Modern UEBA solutions are designed for seamless integration with existing IT infrastructures, including Security Information and Event Management (SIEM) systems and various data sources. Once deployed, the machine learning models continuously learn and adapt, improving detection accuracy over time to identify both potential and active security threats.
How does UEBA help with compliance and audits?
UEBA strengthens compliance and audit efforts by providing detailed, traceable activity logs for all users and entities within an organization. It records who accessed what resources, when, and how — creating a transparent audit trail for every security event. These logs support compliance with standards such as GDPR, ISO 27001, HIPAA, and SOX, and facilitate faster forensic investigations and accountability in the event of an incident.
Conclusion
In short, UEBA provides deep visibility into both potential and ongoing threats. By continuously learning from behavioral data, it evolves to become more intelligent and accurate—strengthening your organization’s overall security posture.
In today’s complex threat landscape, effective protection is incomplete without UEBA. If you’re looking for a reliable solution, AnySecura offers a comprehensive UEBA system designed to detect, analyze, and respond to security risks in real time.


