Data breaches can cost companies millions in fines and lost trust—and most start with a single misstep, like an accidental file share or email. Data Loss Prevention (DLP) software helps stop this by securing data across endpoints, networks, and cloud platforms while keeping businesses compliant with rules like GDPR and CCPA.
In this article, we’ll introduce the 5 best Data Loss Prevention Software in 2026, compare their strengths, and help you decide which fits your business.

You may also want to know: Forcepoint DLP vs AnySecura: Right Data Security Choice
What is Data Loss Prevention Software?
Simply put, DLP software is a mechanism that helps enterprises manage sensitive data. But don't let the name fool you; it's more than just data loss prevention; it's more importantly about managing data flows. Data in modern enterprises flows like water, from employee computers to cloud servers, from email to collaboration tools. Traditional firewalls can't stop this flow. Good DLP software should be like an intelligent sluice gate, knowing which water can flow, where it flows, and what the normal flow rate is. The core functions are divided into three parts:
- Endpoint Data Protection: To put it simply, it means keeping an eye on employees' laptops and mobile phones to prevent data from being copied to USB drives or sent through unauthorized applications.
- Cloud DLP: With Cloud DLP, you can automatically identify sensitive data in uploaded files on platforms like Google Workspace or AWS and block unauthorized access when they are shared or transferred.
- Network Monitoring: This system tracks every data flow. It accurately identifies unusual activity, such as large file transfers to unknown locations, and immediately prompts action to prevent sensitive information from leaking at the source.
These features go beyond plugging loopholes to help companies accumulate compliance evidence. Every data interception and every operation recorded serves as crucial evidence for subsequent audits.
Compliance is, after all, something you can’t ignore. GDPR requires data traceability, and CCPA mandates reporting breaches within 72 hours. These tasks cannot be accomplished manually. Mature DLP software automatically logs data flows and generates compliance reports. Essentially, it transforms legal requirements into enforceable technical rules, allowing companies to manage their data while also ensuring compliance.
Which Data Loss Prevention Software Is Right for You?
If you don't want to spend time understanding the features of all products, you only need to answer the following 9 simple questions to immediately find the data security solution that best suits your business.
Best DLP Solution for you: AnySecura
Depending on your needs, this product can best meet your data security requirements.
Product Features
The product description will be displayed here.
- Feature 1
- Feature 2
- Feature 3
- Feature 4
Quick Comparison of Top 5 Data Loss Prevention Software
If you don't want to waste time on a detailed analysis of the features, pros and cons of each Data Loss Prevention software and want to quickly pick the right one, here's a quick comparison of five major data leakage prevention software options. This will help you understand the core differences between the products and easily identify the one that's right for you.
| Comparison Dimension | AnySecura | Forcepoint | Digital Guardian | Symantec DLP | Teramind |
|---|---|---|---|---|---|
| Core Advantages | Unified management of multiple system terminals (Windows/Mac/Linux). Mature document encryption, USB control, email monitoring, and cloud data protection modules eliminate multi-tool dependency. | Unifies endpoint/network/cloud policies with 80+ country compliance templates. Expandable SASE/DSPM capabilities for complex architectures. | Real-time network/endpoint monitoring with pre-built compliance templates. Faster emergency deployment than competitors. | Strong content recognition (image text/ML sensitive data detection). Multi-channel protection (email/cloud/endpoints) with extensive compliance templates. | UEBA-based behavior analysis, real-time alerts, screen recording. AI monitoring reduces manual workload. |
| Best For | Medium teams (50-500), no dedicated security team required | Large enterprises (>1000 employees), dedicated IT/security team mandatory | Medium-large (200-1000), rapid implementation needs | Large enterprises (>1000), multinationals | Financial/legal firms (any size), internal risk-sensitive |
| Deployment | On-premises and cloud. Module-based installation, half-day IT training. Clear management interface. | SaaS/On-premises/Hybrid. Requires extensive environment adaptation & network architecture knowledge. Professional services needed. | SaaS. Fast initial deployment but needs network optimization. Compatibility risks without tuning. | On-premises and cloud. Complex policy configuration requiring technical expertise. Rule changes demand skilled personnel. | Endpoint agent/Private cloud (AWS). Basic functions easy to use, but behavior analysis rules require complex configuration. |
| Cloud Support | Compatible with local servers & major clouds. No separate debugging. | Deep hybrid cloud/SaaS/multi-region multinational support. | SaaS/local server support with stable cloud data response. | Comprehensive cloud/endpoint coverage with excellent compatibility. | Integrates with mainstream clouds but lacks depth in complex data flows. |
| Cost | Flexible module-based pricing. Get the best protection you need at the lowest cost. | High-budget enterprise solution with ongoing service costs. | High overall investment due to maintenance/policy optimization costs. | High cost threshold. The basic version is expensive, and advanced features are charged extra. | Tiered deployment. Basic version good value, advanced features cost extra. |
| Overall Rating | 9.2/10 | 8.0/10 | 8.3/10 | 8.5/10 | 7.8/10 |
In practice, the pain point for most companies isn't a lack of functionality, but rather fragmented tools and conflicting rules. AnySecura's strength lies in simplifying complex tasks, which explains its rapid adoption among mid-sized enterprises this year.
Detailed Review of Top 5 DLP Solutions in 2026
When choosing a DLP tool, you shouldn't just focus on brand popularity. The key is whether it fits your company's actual needs. Currently, the following mainstream solutions (AnySecura, Forcepoint, Digital Guardian, Symantec DLP, Teramind) on the market each have a clear positioning in their applicable scenarios. There is no absolute "best," only "more suitable".
AnySecura
AnySecura is a data leakage prevention software covering all scenarios including computers, mobile phones, emails, cloud drives, and USB flash drives. The core can locate sensitive data according to rules or manually, and supports 24-hour real-time monitoring, anti-leakage through photo taking (the camera locks the computer when it detects a photo action), file encryption (files cannot be opened once they leave the company environment), and can also control printing and USB flash drives. If data is lost/damaged, it can be restored from cloud backup, adapting to the needs of multiple industries such as finance, medical care, and manufacturing.
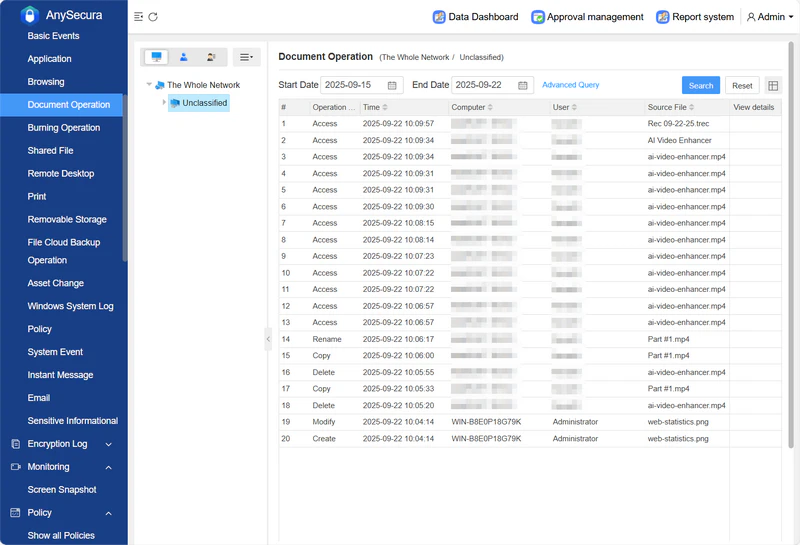
How AnySecura Protects Your Enterprise Data
- Set permissions for files/APPs/emails and set rules for sensitive data
- Real-time monitoring and interception.
- Encryption and backup.
- All actions are logged.
The Core Value of AnySecura DLP Software
 Protect your data: Files are automatically encrypted wherever they go, ensuring security is always there.
Protect your data: Files are automatically encrypted wherever they go, ensuring security is always there. Trace leaks to the root: Watermarks and logs pinpoint leaks to individuals and devices.
Trace leaks to the root: Watermarks and logs pinpoint leaks to individuals and devices. Prevent invisible leaks: Identify sensitive content and control hidden channels like chats and screenshots.
Prevent invisible leaks: Identify sensitive content and control hidden channels like chats and screenshots. Control external data: Files sent externally can also be assigned permissions and expiration dates to prevent secondary spread.
Control external data: Files sent externally can also be assigned permissions and expiration dates to prevent secondary spread. Balance protection and efficiency: With strict protection, employees' daily operations remain largely unaffected.
Balance protection and efficiency: With strict protection, employees' daily operations remain largely unaffected. Meet core compliance requirements: Provide a complete chain of evidence, making audits easier.
Meet core compliance requirements: Provide a complete chain of evidence, making audits easier. Proactive risk warning: Automatically detect and alert abnormal operations, shifting from reactive response to proactive prevention.
Proactive risk warning: Automatically detect and alert abnormal operations, shifting from reactive response to proactive prevention.
🚨 Considerations for AnySecura Data Loss Prevention Software:
- You need to go through an initial learning process to understand the detailed policy configuration and daily operations.
- You need to adjust policies as needed during initial deployment to prevent employees from feeling overly monitored.
Forcepoint DLP
Forcepoint DLP primarily protects against two types of risks: preventing private data from being copied to AI tools (such as ChatGPT), and controlling emails, web pages, and cloud applications (such as Office 365). It can block spam with viruses, prevent data from being transmitted to unknown websites, and monitor files in the cloud to prevent them from being shared with outsiders. It can also block data copying when the computer is offline.
How it Protects Your Enterprise Data
- Blocking AI data input.
- Monitoring email/cloud.
- Offline terminal management.
The Core Value of Forcepoint DLP:
 Focus on preventing AI leaks: Some people want to stick sensitive data into AI tools such as ChatGPT and intercept it directly.
Focus on preventing AI leaks: Some people want to stick sensitive data into AI tools such as ChatGPT and intercept it directly. Omnichannel data control: Block virus-carrying spam, prevent data from being transmitted to dangerous websites, and keep a close eye on cloud storage (such as Office 365) to prevent indiscriminate sharing.
Omnichannel data control: Block virus-carrying spam, prevent data from being transmitted to dangerous websites, and keep a close eye on cloud storage (such as Office 365) to prevent indiscriminate sharing. Offline terminal protection: When employees' computers are offline, they can also be prohibited from copying data to USB drives and printing sensitive content.
Offline terminal protection: When employees' computers are offline, they can also be prohibited from copying data to USB drives and printing sensitive content. Behavioral risk warning: By analyzing user operations to calculate a "risk score", high-risk behaviors (such as suddenly downloading a large number of files) will automatically trigger an alarm.
Behavioral risk warning: By analyzing user operations to calculate a "risk score", high-risk behaviors (such as suddenly downloading a large number of files) will automatically trigger an alarm.
🚨 Considerations for Forcepoint DLP:
- Data copying to USB drives is prohibited, but there's no way to prevent external USB drives from being used or company USB drives from being opened, leaving gaps in device protection.
- Forcepoint DLP doesn't have a screen-snap feature. If your employees use their phones to take photos of sensitive data on their computers, you have no control over it.
- Its configuration is complex and costly. You need a professional security team to adjust policies, and hardware procurement is expensive, making it difficult for small and medium-sized businesses to afford it. The return on investment (ROI) period exceeds three years.
Digital Guardian
Digital Guardian relies on online deployment, eliminating the need to install complex software on every computer. It quickly locates sensitive company data (both on computers and in the cloud). It supports Windows, Mac, and Linux, even Linux computers commonly used by developers. If your company lacks a dedicated IT team, you can enlist the vendor's support for operations and monitoring. Cloud tools can also provide virus protection and shared file encryption.
How it Protects Your Enterprise Data
- SaaS-based data targeting.
- Cloud encryption.
- Managed team monitoring.
The Core Value of Digital Guardian DLP:
 Rapid online deployment: There is no need to install complex software on each computer, you can use it online and implement it quickly.
Rapid online deployment: There is no need to install complex software on each computer, you can use it online and implement it quickly. Multi-system full coverage: Supports Windows, Mac, and Linux, and can even manage Linux computers commonly used for research and development.
Multi-system full coverage: Supports Windows, Mac, and Linux, and can even manage Linux computers commonly used for research and development. Cloud file encryption protection: Regardless of whether the file is stored locally or in a cloud drive (such as Box or OneDrive), it can be automatically protected with high-strength encryption.
Cloud file encryption protection: Regardless of whether the file is stored locally or in a cloud drive (such as Box or OneDrive), it can be automatically protected with high-strength encryption. Hosted operation and maintenance: If your company does not have an IT team, it can ask the manufacturer to handle monitoring and policy configuration.
Hosted operation and maintenance: If your company does not have an IT team, it can ask the manufacturer to handle monitoring and policy configuration.
🚨Considerations for Digital Guardian:
- Data misuse can be detected, but it can't be intercepted in real time, so by the time an alert is triggered, the information may have already been leaked.
- If your employees transmit data through document printing and chat tools, etc., it cannot control it.
- Like Forcepoint, it cannot prevent mobile phone screen captures, posing a high risk of sensitive data exposure.
Symantec DLP
Symantec DLP is a famous Data Loss Prevention software designed specifically for large companies. It manages local data on company servers and online data in the cloud separately. It uses specialized techniques (such as matching database information) to precisely locate sensitive data, minimizing the risk of missed data. It also integrates with Microsoft Office software (such as Word and Excel) to label files as confidential, allowing you to set rules that are enforced across all company devices.
How it Protects Your Enterprise Data
- Scanning local/cloud data.
- Unified rule-based interception.
- Collaborative processing.
The Core Value of Symantec DLP:
 Exclusive adaptation for large enterprises: It can manage local data on the company's servers and data in the cloud separately, and supports hierarchical management and control for enterprises with tens of thousands of people.
Exclusive adaptation for large enterprises: It can manage local data on the company's servers and data in the cloud separately, and supports hierarchical management and control for enterprises with tens of thousands of people. Sensitive data positioning accuracy: Using specialized techniques (such as matching database information) to find sensitive data is less likely to be missed.
Sensitive data positioning accuracy: Using specialized techniques (such as matching database information) to find sensitive data is less likely to be missed. Cross-tool integration: Can integrate with Microsoft Office (Word/Excel, etc.) to automatically assign confidentiality tags to files.
Cross-tool integration: Can integrate with Microsoft Office (Word/Excel, etc.) to automatically assign confidentiality tags to files. Complete compliance evidence chain: Complete operation logs meet compliance audit requirements in industries such as finance and healthcare.
Complete compliance evidence chain: Complete operation logs meet compliance audit requirements in industries such as finance and healthcare.
🚨Considerations for Symantec DLP:
- Its deployment is extremely complicated. You need to install two systems, one local and one cloud, and you need a professional IT team to handle it. Small companies simply cannot handle it.
- Its basic functions are expensive, and many advanced functions (such as image sensitive information recognition) require additional payment.
- It has poor semantic recognition capabilities for professional content such as source code, so it often mistakenly blocks normal files, affecting work efficiency.
- It is completely useless for mobile phones to shoot sensitive content on computers.
Teramind
Teramind differs from other DLP software in its focus. It specifically monitors employee computer activity. It can monitor real-time screen activity, record keystrokes (e.g., typed characters), and track slacking (e.g., watching videos). It also helps prevent data leaks by alerting employees if they copy sensitive files or send external emails. You can also choose to notify employees that you're monitoring or monitor secretly to avoid employee complaints.
How it Protects Your Enterprise Data
- Monitoring computer operations.
- Warning of abnormal behavior.
- Intercepting violations.
The Core Value of Teramind DLP:
 Full employee operation monitoring: View real-time screens, record keyboard input, take screenshots, and even log the software used and files accessed.
Full employee operation monitoring: View real-time screens, record keyboard input, take screenshots, and even log the software used and files accessed. Internal leak warning: Automatically trigger alerts when employees suddenly copy large files or send sensitive emails.
Internal leak warning: Automatically trigger alerts when employees suddenly copy large files or send sensitive emails. Offline monitoring: Records operations even when the computer is offline and automatically uploads data when connected.
Offline monitoring: Records operations even when the computer is offline and automatically uploads data when connected. Efficiency management: Counts employee work hours, software usage frequency, and detects slacking.
Efficiency management: Counts employee work hours, software usage frequency, and detects slacking.
🚨 Considerations for Teramind:
- It completely ignores scenarios such as transferring files via cloud disk, transferring pictures via mobile chat tools, and taking things out with USB flash drives, as these are all blind spots in its protection.
- It cannot automatically encrypt files (it can be opened as soon as it is taken out), and it has no backup function, so data cannot be recovered if lost.
- It can record keyboard input and view the screen in real time, but be aware that employees may have strong resistance
- Multiple users (over 30) simultaneously use the system, which hogs CPU and memory, causing computer sluggishness. Screen recording also consumes a large amount of storage.
- Many monitoring features are inoperable on Mac computers, and cross-operating system compatibility is poor.
Why Choose AnySecura as Your DLP Solution?
After working with over 200 companies on DLP deployments, a common thread has emerged: tools that succeed over the long term share a critical trait — they don’t disrupt existing workflows. This is what truly impressed us about AnySecura.
1. Core Need for Data Loss Prevention and Traceability.
It records all document operations (read, write, burn, and ADB transfer), granularly defines read, write, and delete permissions, and supports automatic backup (including cloud and batch backups). Accidentally deleted or tampered files can be quickly restored, and data operations are fully traceable, eliminating the problem of losing track of who moved the data.
2. No Disruption to Daily Work.
Protection measures seamlessly integrate into existing processes: Printing automatically logs and adds watermarks (no additional approval required), and triggers alerts when sensitive information is transmitted via IM or email. This eliminates the need for frequent system switching for employees, resulting in high employee acceptance and unaffected work efficiency.
3. Automatic Sensitive Data Management.
Proactively scans sensitive files locally and in the cloud (such as customer information and code), automatically assigns confidentiality levels, and accurately intercepts external transmissions. Transparent encryption ensures normal internal use and prevents access to external devices (such as home computers), preventing copying and leaks.
4. Eases compliance audits.
Automatically generates multi-dimensional audit reports (covering printing, email, and mobile storage operations), highlights risky behaviors, and provides early warning of unusual operations (such as bulk downloading of customer information). Eliminating the need for manual record organization significantly improves audit efficiency.
5. Adapting to Business Scale
Flexible functional module splitting: Small businesses can initially deploy document control and device management, while larger enterprises can expand to sensitive inspection and auditing capabilities. Adding new users or modules eliminates the need for re-deployment, supporting smooth expansion from teams of dozens to hundreds of employees, eliminating resource waste.
FAQs about Data Loss Prevention (DLP)
Is DLP a legal requirement?
The law does not require everyone to install it, but if a company wants to protect sensitive data such as customer information and medical records, DLP is often used to meet relevant compliance regulations.
Is DLP compliance required?
It's not required, but if an enterprise needs to comply with regulations that protect sensitive data, DLP is often a key tool for achieving compliance, helping the enterprise cope with audits and avoid penalties.
What is the best DLP solution?
There is no absolute best option and it depends on your needs: If you need full-scenario protection that is simple and easy to operate, choose AnySecura. For large enterprises with complex architectures, use Forcepoint or Symantec DLP. If you lack an IT team, choose Digital Guardian. If you want to monitor employee operations, choose Teramind.
What is an example of DLP?
For example, company technical documents are automatically encrypted and have permissions set, making them impossible to copy or transfer. Even if you take them away, they will only be garbled when opened on a computer outside.
What is the main purpose of Data Loss Prevention?
Simply put, it is to first find the important data in the company, and then keep an eye on this data to prevent it from being transmitted, copied, or sent randomly. If something goes wrong, the cause can be found, and the data security will be kept without affecting work.
Find Your Fit: Making the Final DLP Decision
When choosing a DLP tool, enterprises rely on one core criterion: whether it can protect data without adding to the complexity.
Comparing mainstream products on the market, Forcepoint DLP is suitable for large enterprises with complex architectures, Digital Guardian is ideal for businesses without dedicated IT teams and requiring rapid SaaS deployment, Symantec DLP focuses on tiered management of local and cloud data for enterprises with 10,000+ employees, and Teramind excels in internal employee operation monitoring and risk alerts. AnySecura's value lies in its core balance: it provides comprehensive protection across endpoints, cloud, and networks. By simplifying operations, reducing false positives, and aligning with business processes, it addresses practical challenges faced by most enterprises in DLP deployments, such as restricted access and difficult maintenance.
For most growing businesses, however, AnySecura is a more practical choice. It eliminates the need to hire security experts for operations and maintenance, eliminates the need for employees to constantly respond to pop-up alerts, and eliminates the need to overpay for features you don't use. It manages data flows across endpoints, cloud, and email in a single place, and can keep pace with business expansion.
To put it bluntly, a good DLP solution shouldn't impose constraints on an enterprise. Neither excessive control nor laxity can hinder business operations. AnySecura is the best solution for most businesses. It is not complicated and practical enough, and that's all.


