Even with the best firewalls and anti-ransomware tools, your biggest cybersecurity threat may come from inside—your own employees or contractors. Keep reading to find out what a malicious insider is, the behaviors to watch for, and how to spot them before they can cause serious harm.

What Is a Malicious Insider?
Malicious insiders are like “turncoats” within a company. They can be current or former employees, contractors, or trusted business partners. Using their legitimate access, they carry out harmful actions such as stealing data or sabotaging company assets, causing serious problems.
These “turncoats” are much harder to catch than external hackers because they normally have authorized access to sensitive information, and their daily activities often blend with routine work. Detecting their malicious actions usually takes a long time.
According to the 2020 Cost of Insider Threats Global Report by the Ponemon Institute, it takes an average of 77 days for organizations to identify and contain insider threat incidents. Only 13% of incidents are contained within 30 days, and incidents taking more than 90 days can cost companies an average of $13.71 million annually. This highlights how challenging it is for organizations to detect and respond to insider threats quickly.

Insider threats in 2026 are smarter and harder to detect. Explore real cases, key trends, and practical strategies to prevent internal risks before they cause serious damage. Learn more>>
5 Types of Malicious Insiders
When we talk about “malicious insiders,” they generally fall into five groups: disgruntled employees, opportunists, coerced or compromised staff, thrill-seeking or power-abusing tech personnel, and those driven by ideology. Some frameworks only use three categories, but here we break it down into five so it’s easier to see the different motives and behaviors.
Disgruntled Employees
We’ve all seen it—a coworker who feels overlooked, frustrated with management, or fed up with changes at work. When anger and resentment build up, some employees lash out. They might delete files, leak confidential data, or try to disrupt systems just to get back at the company. Because these actions come from strong emotions, they’re often unpredictable and especially dangerous.

Opportunistic Insiders
Others aren’t angry at all—they just see a chance to make money. Opportunistic insiders might copy client lists, steal intellectual property, or grab sensitive business data to sell or use for themselves. Unlike the disgruntled type, they’re usually calm, patient, and deliberate. Their goal is profit, so they work quietly to avoid being noticed.
Coerced or Compromised Staff
Not every insider acts willingly. Some are pushed or pressured from the outside. They may be threatened, blackmailed, or manipulated into doing something against the company. In some cases, their families may even be at risk. These situations are tricky because the insider isn’t acting out of greed or anger—they’re acting out of fear, which makes them very hard to spot.
Thrill-Seekers or Power-Abusing Tech Staff
This type usually comes from the IT or technical side of the company. With special access to systems, some people just can’t resist pushing boundaries. Maybe they want to prove how smart they are, maybe they’re bored, or maybe they just enjoy the power. They might leave backdoors, mess with system settings, or snoop on colleagues. Even if it’s not about money, the chaos they can cause is no small thing.
Ideology-Driven Insiders
Finally, there are insiders who act because of their beliefs or values. They might leak information to expose something they think is wrong—like unethical practices, safety concerns, or environmental issues. Sometimes, they’re even working on behalf of a government or competing organization. A famous example is Edward Snowden, who shared classified documents because he believed the public had a right to know.
In situations like these, tools like AnySecura DLP can help you prevent data leaks and insider risks. AnySecura helps you automatically monitor sensitive activities and block risky actions in real time, which is something regular employee monitoring software cannot do. AnySecura also supports strict access control, ensuring employees only have the privileges they truly need, and it provides secure data backup to keep key information safe. With these measures working together, the risk of damage from malicious insiders can be greatly reduced.
What Are Insider Threat Signs?
Of course, not every employee is going to turn into a malicious insider—so there’s no need to look at everyone with suspicion. Still, certain behaviors and warning signs can hint at potential risks. These signals can show up as early as the hiring process and continue to surface once someone has already joined the team.
During Recruitment / Before They Join
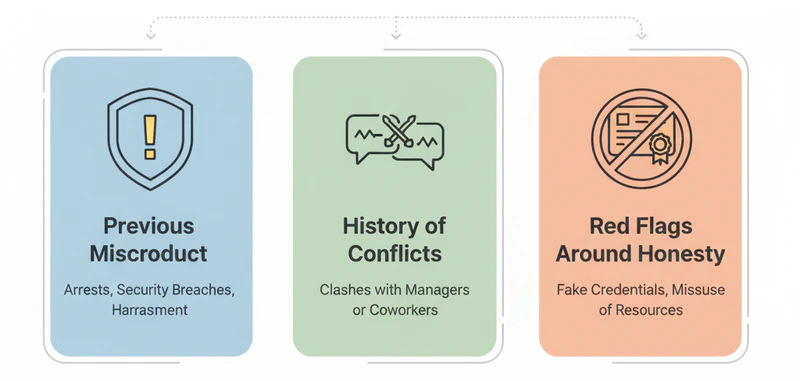
When you’re hiring, a candidate’s past can sometimes offer clues about future behavior. Taking a close look at their work history and overall integrity helps companies spot patterns that could create problems down the road.
- Previous misconduct at other jobs—things like arrests, security breaches, or harassment issues.
- A history of frequent clashes with managers or coworkers.
- Red flags around honesty, like fake credentials or misuse of resources at a past job.
After Onboarding / Once They’re Part of the Team
Even after someone joins, it’s worth paying attention to how they work and interact. Most of the time it’s nothing, but certain patterns can signal bigger issues if left unchecked.
- Never taking breaks or vacation—working nonstop for long stretches.
- Ongoing poor performance or repeated rule-breaking.
- Frequent conflicts with teammates or supervisors.
- Digging into projects or data that don’t relate to their job.
- Lots of unexplained sick days or absences.
When these behaviors show up, HR should step in early. In some cases, it may also make sense to loop in the security team for a closer look. Even if nothing “big” is happening, keeping an eye on unusual activity can prevent surprises later.
Technical and Digital Warning Signs
Since most of our work happens online now, the way people use systems can be just as telling as their behavior in the office. Watching for unusual system activity helps spot problems before they snowball.
- Trying to access files or systems outside of their role.
- Downloading or copying large amounts of sensitive data.
- Odd login activity—like logging in at strange hours, from unusual locations, or in multiple places at once.
- Installing unauthorized software or using remote access tools without approval.
- Messing with security protections, like turning off antivirus or firewalls.
- Covering tracks—deleting logs, creating hidden accounts, or altering system files.
- Sending company files to personal emails, outside cloud storage, or even competitors.
- Suspicious device use, like taking company hardware home or plugging in unapproved USB drives.
Because technically skilled insiders know how to hide what they’re doing, their activities can be harder to catch— and the damage, from data theft to financial losses, can be significant.
Data Theft Signals
The way employees handle company data can also raise flags. Tracking how files are moved, shared, or stored can go a long way in protecting sensitive information.

- Sending big attachments to personal or competitor email addresses.
- Accessing company systems remotely in unusual ways, like odd VPN activity.
- Looking at files that have nothing to do with their job.
- Printing or downloading large amounts of sensitive information.
- Using personal devices or cloud services to store or transfer company data.
By combining these technical red flags with everyday behavioral observations, you can catch insider risks early—before they turn into real damage.

Discover how DLP software delivers compliance, prevents insider threats, and secures sensitive information across endpoints, cloud services, and networks. Learn more>>
How to Spot and Prevent Malicious Insider Threats
Stopping insider threats isn’t about a single solution—it takes a layered approach. By combining access control, monitoring, data protection, analytics, and a security-aware culture, you can catch risky behavior early and reduce potential damage. While this may sound complex, the solution is simple: AnySecura.
AnySecura is an all-in-one insider threat prevention platform that brings monitoring, access control, and data protection together. It helps organizations improve security, boost productivity, and stay compliant—all without adding extra complexity.
How AnySecura Helps Prevent Insider Threats
With over 20 integrated modules—including control tools, encryption, data loss prevention, real-time monitoring, and risk alerts—AnySecura helps you secure sensitive information, monitor employee activity, and prevent insider threats, while keeping full control over your digital assets. Here’s a full overview of AnySecura’s modules:
| AnySecura Modules Overview |
|---|
|
|
1. Control Who Can Access Critical Systems
AnySecura helps you ensure the right people access the right resources—nothing more, nothing less. This includes Application Control, Device Control, Network Access Control, and so on.
- Allow employees to access only approved apps, websites, and networks.
- Automatically block unauthorized USB devices and external drives.
- Require step-by-step approvals before accessing sensitive systems.
- Apply the same access rules to vendors and contractors to reduce third-party risks.
2. Get Complete Visibility into User Activity
With Security Audit Reports, Network Traffic Control, and IT Asset Management, AnySecura gives you a clear picture of what’s happening across your systems.
- Record logins, file activity, emails, and app usage in one place.
- See who opened, edited, or transferred sensitive files.
- Detect unusual behavior early with automated pattern analysis.
3. Protect Sensitive Data from Leaks
AnySecura combines Document Control, Sensitive Content Inspection, and Transparent Encryption to prevent sensitive data from leaving your organization.
- Classify and label confidential documents for easier tracking.
- Block printing, emailing, or uploading sensitive files without approval.
- Prevent copying of company data to USB drives or cloud storage.
- Trace documents with watermarks and recover them from secure cloud backups.
You may also feel interested in: How to Add Watermark to PDF (Comprehensive Guide)
4. Detect Suspicious Behavior in Real Time
Through Instant Messaging Monitoring, Email Control, AI Visual Perception, and Proactive Risk Alerts, AnySecura helps you monitor continuously and react instantly.
- Flag inappropriate or unauthorized chats and emails.
- Spot suspicious behavior like mass downloads or after-hours access.
- Receive immediate alerts when risky activity occurs.
- Visualize user activity in dashboards for faster investigation.
5. Continuously Test and Strengthen Security
With Security Audit Reports, Remote Maintenance, and the Software Center, AnySecura helps you regularly check and improve security defenses.
- Run scheduled audits to find gaps before attackers do.
- Simulate insider threat scenarios to ensure monitoring works effectively.
- Keep software updated and patch systems remotely to close vulnerabilities.
Additional Tips to Prevent Insider Threats
Security isn’t just IT’s job—everyone has a role. Education and awareness help employees recognize risks and act responsibly.
- Teach staff how to identify insider threat signals and understand their role in protecting data.
- Provide secure and anonymous channels to report suspicious behavior.
- Encourage a culture of transparency, vigilance, and shared responsibility.
Even with precautions, incidents may occur. Clear response procedures and backup plans minimize disruption.
- Have clear steps to isolate accounts, investigate issues, and notify stakeholders.
- Maintain strong backup and recovery plans to prevent lasting damage from insider incidents.
FAQs about Malicious Insider
What is an example of a malicious activity?
A classic example of malicious activity is your employee intentionally copying sensitive company data onto a personal USB drive to sell it to your competitor.
What is a non-malicious insider?
A non-malicious insider is someone within an organization—like an employee, contractor, or partner—who has access to company systems and data but does not intend to cause harm.
Even though their actions might occasionally create security risks, these are usually accidental or unintentional, not deliberate.
Conclusion
Malicious insiders can cause serious damage—from stealing sensitive data to disrupting critical systems. The challenge is that their actions often look like normal work, making them hard to spot. By keeping an eye on behavioral and technical warning signs, fostering a security-aware culture, and using tools like AnySecura to monitor and protect sensitive information in real time, organizations can catch risks early and prevent serious harm. Anyway, staying proactive is the best way to protect your business from threats that come from within.


