Gaining a basic understanding of cybersecurity is also key to ensuring a company's continuous operation and protecting its information assets. In this article, we'll break down cybersecurity from several perspectives:
What is Cyber Security?
Cyber Security, also known as information security, is the practice of protecting computers, networks, servers, mobile devices, and data from digital attacks. Simply put, it's about keeping your digital world safe, just like locking your door to protect your home. The goal of cyber security is to prevent unauthorized access, data theft, and damage to systems that we rely on every day.
The classic foundation of cybersecurity lies in the CIA Triad:
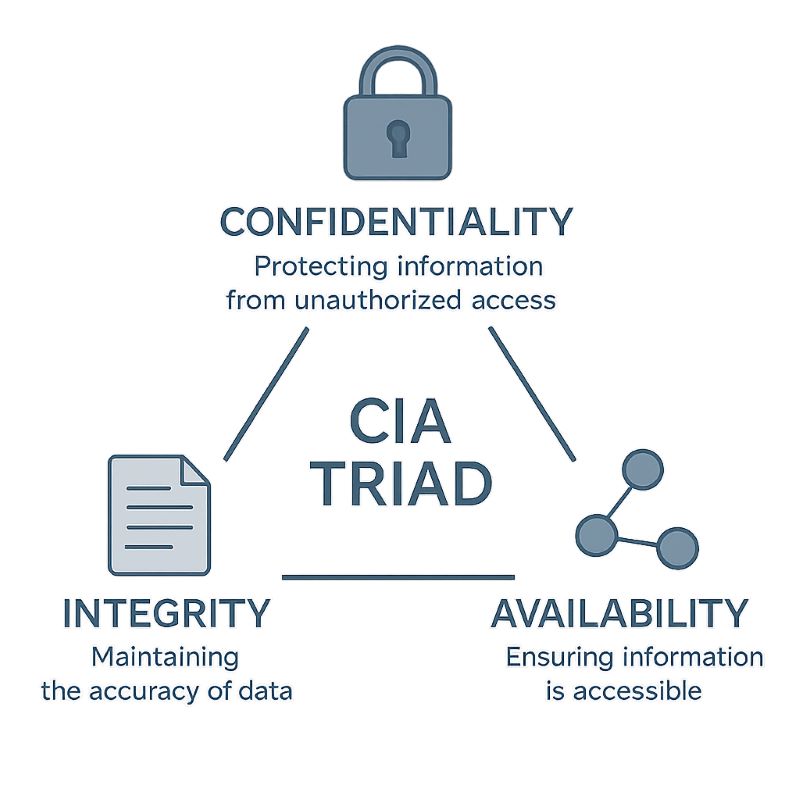
- Confidentiality: Only the right people see the right data.
- Integrity: Data isn't altered or corrupted, whether by accident or on purpose.
- Availability: Systems and information are accessible when needed.
Whether through technology, strategy, or management practices, all cybersecurity practices ultimately align with these three core objectives. If a system fails across these three areas, no amount of security tools can truly protect the business. Therefore, many international security standards, such as ISO/IEC 27001, NIST, and CIS Controls, are built on the CIA Triad. Without a proper balance among the three, there is no truly meaningful information security.
in 2026, as remote work, AI integration, and cloud computing continue to expand, digital risks are multiplying. Cyber security isn't just a technical topic anymore, it's a core business priority.
You may also want to know: What Does DRP Mean? A Complete Guide to Disaster Recovery Plans
Why Cyber Security Matters for Business?
Prevents Multi-Million-Dollar Losses
Cyber attacks are no longer rare, they're an everyday threat. The average data breach now costs around $4.88 million, not to mention the blow to a company's reputation or the legal mess that often follows.
What's even trickier is that many breaches don't start inside your walls. They come through third-party vendors, your software suppliers, cloud providers, or partners. So even if your system is locked down, someone else's mistake could still expose your business.
That's why more companies are using ROI-based risk models to put a number on cyber threats. The results are clear: spending on prevention almost always costs less than dealing with the fallout of an attack.
Avoids Catastrophic Fines
Cyber regulations are tightening fast. Frameworks like NIS2 in Europe, GDPR, and China's Cybersecurity Law now impose steep penalties on companies that fail to protect user data, sometimes even threatening their ability to operate.
Following the rules isn't only for avoiding fines or legal issues. Customers, partners, and investors increasingly expect transparency in how companies handle security. Cyber protection has become part of ESG standards, and a strong security record can build trust, attract investors, and keep a company's market value steady.
Prevents Operational Shutdowns
A single ransomware attack can halt production lines. A cloud outage can freeze online stores or delivery systems. Even one misconfigured setting can ripple through and break an entire supply chain.
That's why cybersecurity today is considered a core business utility, just like power or internet connectivity. Without it, everything can stop in an instant.
Protects Reputation and Customer Loyalty
In an age where people care more than ever about privacy and data protection, trust is everything. One leak can shatter that trust overnight, leading to angry customers, social media backlash, and falling stock prices.
For B2B companies, the stakes are even higher. Many clients will only work with partners who can prove they take cybersecurity seriously. In short: trust drives business, and cybersecurity is what makes that trust possible.

Learn the key differences between Cybersecurity and Network Security, their scopes, objectives, threats, and how AnySecura's solutions protect your digital assets comprehensively. Learn more>>
How Cyber Security Works?
Cybersecurity isn't just about fancy software or tech tools. It's really about people, technology, and smart habits all working together to keep information safe. Without one of these parts, the system becomes much weaker.
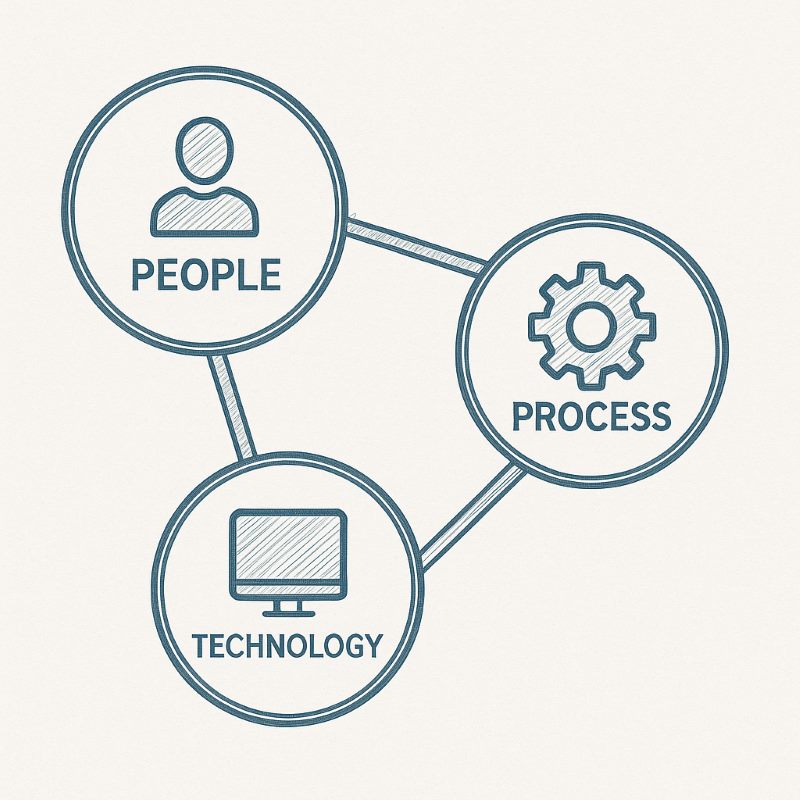
Technology
To start with, technology forms the first line of defense. Think of firewalls as digital gates that block unwanted visitors.Antivirus software hunts down harmful files before they can cause damage, and encryption scrambles information so only the right people can read it.
These tools handle a lot of protection automatically, but they can't do everything on their own. That's where people come in.
People
Technology is powerful, but it depends on the people who use it. Even the best tools can't stop a simple human mistake. This is why training and awareness are so important.
Everyone, employees, students, or regular users, needs to know how to spot fake emails, create strong passwords, and handle private information carefully. When people make safe choices, they turn technology into a much stronger shield.
Processes
Still, good habits and tools aren't enough without structure. That's where processes come in. Every organization needs clear rules and step-by-step plans.
For example, they decide who can access certain files, make regulardata backups in case something is lost, and write incident response plans so everyone knows what to do during an emergency.
These processes connect people and technology, turning individual actions into a smooth, coordinated system.
Main Types of Cyber Security
There are several branches of cyber security, each protecting a different part of our digital life:







Each type addresses a different "door" into your business. Together, they create a multi-layered shield against modern cyber threats.
How AnySecura Helps Protect Your Cybersecurity
Let's look at how AnySecura puts cybersecurity into practice for your organisation. AnySecura is an all-in-one platform that combines network defense, file protection, device control, and backup into one unified platform—reducing complexity and giving leaders complete visibility over their security posture.
1. Strengthening Network Security
The network is often the first target for cyberattacks—it's where your data travels and where most connections happen. AnySecura strengthens this layer by:
- Continuously monitoring network activity to quickly detect anything unusual.
- Controlling who can access the network, from where, and on which devices.
- Applying consistent security policies across all connected endpoints.
2. Protecting Data at Rest and in Motion
Data protection is at the heart of AnySecura's platform. Whether your files are stored locally or in the cloud, they stay secure through:
- Automatic encryption so only approved people can open or share sensitive files.
- Unified rules that follow the file across local storage and cloud.
- Real-time and scheduled cloud document backups for quick, reliable recovery.
3. Secure Every Device and Guide User Behavior
Remember how we listed Endpoint Security and End-User Security? AnySecura doesn't treat these as after-thoughts; they are built into the platform:
- Device tracking plus remote lock/wipe for lost or risky endpoints.
- User activity insights (open, print, share, move) to spot risky patterns early.
- Focused awareness and coaching based on real usage signals.
4. One Dashboard. Clear Reports. Easier Compliance.
Security should be visible and measurable. AnySecura centralizes:
- Manage encryption, devices, backups, and logs in a single console.
- Automated reporting to support GDPR, ISO 27001, and internal audits.
- Policy enforcement and routine automation to cut manual work.
5. Built-in Resilience: Backup and Fast Recovery
Even the best-secured organisation can face incidents: system failures, natural disasters, internal mistakes, or sophisticated attacks. AnySecura supports return to operation by:
- Up-to-date backups across cloud and local data.
- Encrypted files stay accessible to authorized users during recovery.
- Policy-driven recovery workflows so operations resume quickly.

Your biggest cybersecurity threat may come from inside—your own employees or contractors. Read this guide to find out what a malicious insider is, the behaviors to watch for, and how to spot them before they can cause serious harm.Learn more >>
FAQs about Cyber Security
What is phishing in cyber security?
Phishing in cybersecurity is a type of scam in which attackers disguise themselves as trusted entities and use emails, text messages, or other channels to trick you into revealing information or performing risky actions, ultimately leading to stolen money or compromised accounts.
What is tailgating in cyber security?
Tailgating is part of an important branch of cybersecurity—Physical Security. It occurs when an attacker follows an authorized person (such as an employee) into a restricted area (such as an office, data center, or server room) without proper verification, in order to steal data, install malicious devices, or cause damage.
What is smishing in cyber security
Smishing is a type of scam where criminals impersonate trusted entities—such as banks, mobile carriers, or official platforms—and send text messages with urgent or enticing language to trick you into clicking unknown links, replying with sensitive information (like verification codes or bank card numbers), or even making direct transfers.
Is cyber security only for big companies?
No. Small and mid-size firms are often targeted too; one breach can stop operations. Basic protection and backups are essential for every business.
How can individuals improve their cyber security?
Use strong unique passwords (or a manager), turn on 2FA, update software, think before you click links/attachments, and back up important data.
What is DLP in cyber security?
DLP (Data Loss Prevention) stops sensitive data from leaving your company by monitoring, blocking risky transfers, and encrypting when needed. Click here to learn more about how DLP keeps your information secure.
Conclusion
Cyber security is no longer just an IT concern, it's a business essential. As digital operations expand, every organization, no matter its size, faces constant risks from data theft, system disruption, and human error.
The good news? Protection doesn't have to be complicated. By combining the right technology, clear processes, and security-aware people, you can build a strong foundation that keeps your data and your reputation safe.
With solutions like AnySecura, companies can take a smarter, more automated approach: one that detects threats early, protects sensitive information everywhere, and helps the business stay resilient through any challenge.


