Information technology (IT) has transformed our daily lives—bringing entertainment, convenience, and efficiency to almost everything we do. However, operational technology (OT) security—the protection of the systems and infrastructure that keep our world running—often remains overlooked, even though it plays a vital role in our everyday safety.
Imagine the massive disruption if systems for water and electricity supply, financial transactions, or transportation operations suddenly failed. OT security ensures that these critical systems continue to operate reliably, preventing interruptions that could affect both daily life and industrial operations.
What is OT and OT Security?
In simple terms, OT refers to the hardware and software systems used to monitor or control physical equipment, processes, and events.
OT security encompasses the technologies and practices that ensure the safe, stable, and reliable operation of OT systems. Unlike IT security, which primarily focuses on protecting data, communications, servers, and applications, OT security directly safeguards industrial machines and the physical processes they drive. Failures in OT systems can have real-world consequences, not just digital losses.
OT vs. IT Security: What’s the Difference?
Both OT Security and IT Security fall under the broad umbrella of "Cybersecurity"—so why is "OT Security" often highlighted separately? Keep reading to uncover the key differences.
Different Focus
IT security typically emphasizes data confidentiality, integrity, and availability. OT security, in contrast, focuses on "the safe and reliable operation of physical processes," ensuring uninterrupted equipment operation, continuous production, and preventing physical damage. In short, OT security is more concerned with the physical world.
Different Device and System Requirements
To ensure stability, OT security relies on legacy systems and custom-built protocols designed for decades of continuous operation—many of which were never built with security in mind because they operated on physically isolated networks. By comparison, IT systems are updated more frequently and incorporate mature security mechanisms.
Different Consequences of Disruption
If an IT system crashes, the most common outcomes are website downtime and data loss. In contrast, an OT system failure can damage equipment, disrupt production, and in severe cases, pose safety risks to people and the environment.

Different Network Environments
IT systems are generally connected to the Internet, whereas most OT systems operate on air-gapped, isolated networks to achieve “absolute” security. However, with the rise of digital transformation and the Industrial Internet of Things (IIoT), many OT systems are now connected to IT networks and the Internet, introducing new vulnerabilities.
Only by fully understanding the differences between OT security and IT security can you implement effective measures to address OT security risks.
Why OT Security Matters More Than Ever?
Today, OT security must be a key focus, driven by four significant real-world challenges, each of which directly impacts the safety of industrial operations and can have real-world consequences for people’s lives.
Attack Surface Expansion
Historically, OT systems were mostly physically isolated and "insulated" from the Internet. Today, however, IoT, cloud platforms, and remote monitoring have connected them to IT networks. Production workshops and dispatch centers that were once offline can now be targeted by hackers through IT networks, blurring traditional security boundaries and increasing vulnerability.
Legacy Systems and Weak Security Mechanisms
Many OT devices are designed to operate for 10-20 years and were not built with modern network security in mind. They often lack patch updates, data encryption, and strong access controls—for example, default passwords that remain unchanged for long periods. These devices are difficult to integrate with modern security tools, creating significant vulnerabilities.
Mandatory OT Security through Compliance
As the security of critical infrastructure gains prominence, governments and industry regulators are issuing more rules and standards that explicitly require companies to ensure OT (Operational Technology) security. Security is no longer optional; it has become a mandatory requirement that must be actively addressed.
How to Strengthen OT Security
Now that you have a comprehensive understanding of OT security, here are some recommended steps to help maintain and strengthen it.
Asset Inventory and Visualization
Understanding the complete scope of OT devices and dynamically monitoring their status is the first step in OT security.
Start by counting all OT devices, identifying which are connected to the network, and recording the industrial protocols they use. Establish an asset inventory, classifying devices by function (e.g., control or sensing) and by production impact (e.g., core or general). Using passive monitoring and network traffic analysis, you can observe device behavior in real time, turning a static list into a dynamic, visualized management system that promptly highlights anomalies.
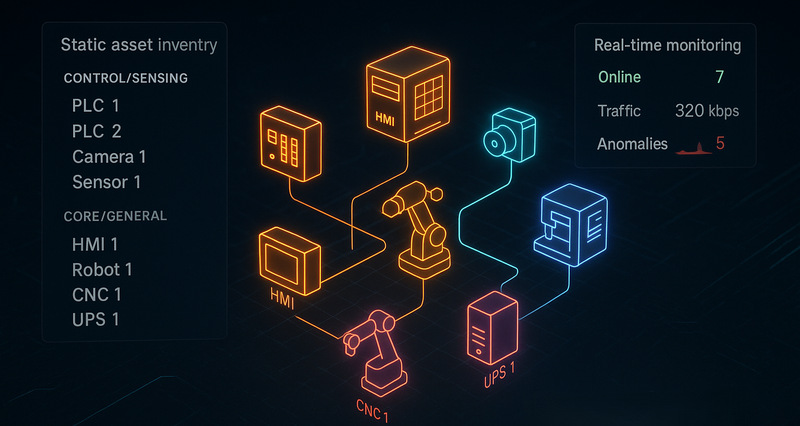
For a complete solution, AnySecura's Asset Management helps unify the management of both hardware and software assets.
Network Segmentation and Isolation
Use firewalls, static whitelists, and data diodes to isolate the OT network from IT networks and the Internet, reducing risks from external threats.
Device Control
After network segmentation and isolation, controlling device access is essential to mitigate threats from peripherals. For example, block USB devices such as flash drives or mobile storage, as they are common entry points for malware.
AnySecura's Device Control supports not only USB management but also controls communication devices, network-connected devices, and any new devices connecting to endpoints for the first time. This ensures a stable and controlled hardware environment for the OT system.
Monitoring and Response
Continuously monitor system and event logs to detect abnormal behaviors in the OT environment, such as unapproved device access, unusual industrial protocol communications, or sudden changes in equipment parameters.
When anomalies are detected, pre-set response mechanisms should immediately trigger: first isolate the affected device or network segment to prevent the risk from spreading; then trace the root cause (e.g., misoperation or cyberattack); finally, log the entire process for review and strategy optimization. This "monitoring-detection-response" loop ensures OT incidents are handled quickly, minimizing potential losses.
Continuous Learning and Training
OT security evolves continuously with new technologies and concepts. Staying up to date through news, blogs, and relevant materials is essential. Targeted training enhances risk-handling capabilities, helping prevent OT risks before they occur and ensuring a calm, effective response when threats arise.
FAQs About OT Security
Why can't IT security solutions be directly applied to OT environments?
IT security typically mitigates risks by disconnecting networks or rebooting devices. However, OT equipment requires 24/7 continuous operation, and such actions could halt production lines. Additionally, OT systems rely on industrial-specific protocols such as Modbus, which IT security tools are generally unable to monitor for anomalies.
How can viruses from peripherals like USB drives be prevented?
First, disable unnecessary USB ports on OT devices and only enable essential interfaces. Second, use security management tools such as AnySecura's Device Control to manage peripheral access, allowing only whitelisted devices to connect.

Discover how DLP software delivers compliance, prevents insider threats, and secures sensitive information across endpoints, cloud services, and networks. Learn more>>
Conclusion
OT security is a fundamental safeguard for industrial stability, critical infrastructure, and everyday life—it is not merely an extension of cybersecurity. With the increasing convergence of OT and IT networks, the attack surface has expanded, and the combination of aging equipment and regulatory compliance requirements makes OT security an essential responsibility for every enterprise.
If you need support in strengthening your OT security, AnySecura is ready to assist you.


