In the field of information security, organizations across industries face countless security incidents every day—including login failures, system alarms, network anomalies, system vulnerabilities, and more. These fragmented data points create a "mountain of noise," beneath which true threat signals are often hidden. The ability to extract potential attack indicators from this complex data, enabling security managers to "see" ongoing risks, is exactly what SIEM (Security Information and Event Management) is designed to do.

What is SIEM?
Initially, SIEM started as a simple log management tool. As security threats evolved and organizational demands increased, it developed into a comprehensive, centralized system combining the functions of Security Information Management (SIM) and Security Event Management (SEM). By centrally collecting, analyzing, and correlating security logs and events, SIEM enables organizations to implement real-time monitoring, threat forensics, and immediate response to incidents.
In short, SIEM acts like the "central nervous system" of an organization’s security infrastructure. It "listens" to data signals from devices and systems, "analyzes" the potential threats behind those signals, and "directs" security personnel or automated defenses to respond accordingly.
Why is SIEM Necessary?
In the early days of security, most organizations relied on point-to-point protection measures such as firewalls and antivirus software. While these measures performed well initially, they often created single points of failure, leaving systems vulnerable to breaches. At the time, point-to-point protection was sufficient for the prevailing security landscape.
However, as security threats have evolved and become more sophisticated, point-to-point protection alone is no longer enough. Hackers can infiltrate systems via legitimate accounts or exploit supply chain vulnerabilities—activities that often go unnoticed by isolated defense mechanisms. These threats leave subtle clues scattered across multiple sources of logs, forming a "jigsaw puzzle" that SIEM is specifically designed to analyze. By correlating this data, SIEM effectively addresses the limitations of traditional defenses. Its key functions include:
- Breaking down data silos: Unifies security log collection from network devices, operating systems, and applications to form an interconnected data network that minimizes overlooked risks.
- Intelligent anomaly detection: Detects unusual activity using predefined rules or machine learning algorithms.
- Compliance and audit support: Meets regulatory requirements for security incident tracing and log retention.
- Improved response efficiency: Automates alerts and remediation to address threats before they escalate.
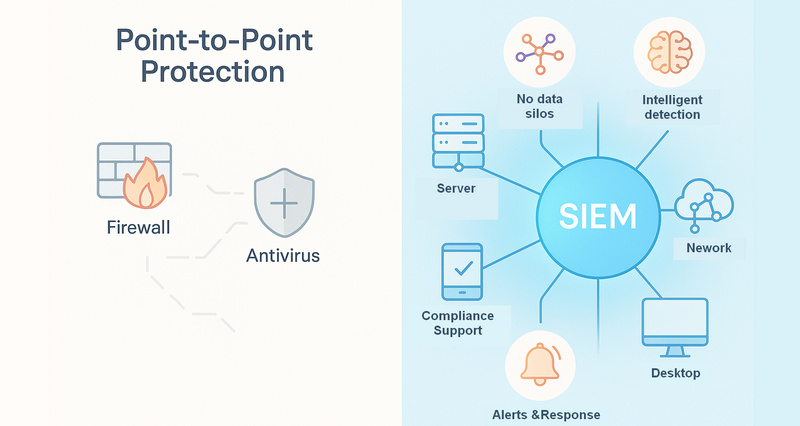
In essence, SIEM complements and enhances existing security measures rather than replacing them. Its primary function is to centralize security management, transforming fragmented, partial visibility into comprehensive, organization-wide transparency.

What Is a malicious insider? Learn how to identify different types, spot warning signs, and use effective strategies to protect your organization’s data and systems. Learn more>>
What Makes a SIEM Solution Stand Out?
Once you understand the severity of security threats and the value of SIEM, adopting a robust SIEM solution adds a critical layer of protection to your organization. But what are the key features that make a SIEM truly effective?
- Intelligence: A top-tier SIEM integrates with UEBA (User and Entity Behavior Analytics) and AI-based detection algorithms to enhance its analytical capabilities, enabling more accurate alerts and threat identification.
- Automation: Enhancing protection alone is not enough. A strong SIEM must also improve the efficiency of threat detection and response while reducing the operational burden on security teams. This is often achieved through integration with SOAR (Security Orchestration, Automation, and Response) systems, which can automatically execute actions such as blocking or isolating threats.
- Scalability: To support complex business operations, a SIEM must handle multi-cloud and multi-platform environments without compromising performance or coverage.
A SIEM that combines these capabilities is considered highly effective. For example, AnySecura leverages AI Visual Perception to continuously learn end-users’ behaviors and improve its intelligence. It can detect abnormal activities in real time—such as photographing classified documents—automatically lock the computer to block the behavior, and alert administrators immediately. Even across endpoints running different operating systems, AnySecura enables real-time risk detection and response wherever it is installed.
In essence, an excellent SIEM is not just a "monitoring platform," but a "security brain" capable of learning, adapting, and proactively defending your organization.
Key Steps to Implement SIEM Functions
Before deploying a SIEM system, it is essential to understand how it works to effectively secure your organization. Typically, unlocking the full capabilities of SIEM involves five key steps.
Log Collection
Serving as the "data entry point" for the entire process, SIEM connects to various data sources across the enterprise IT architecture to capture logs and event information comprehensively. This includes traditional servers, firewalls, and endpoints, as well as database operation records, cloud platform access logs (e.g., AWS, Google Cloud), and even employee office software activity traces—ensuring no critical data is missed and providing a complete dataset for subsequent analysis.
Normalization & Storage
Log formats vary widely across devices and platforms (e.g., firewall logs in code format versus terminal logs in text). SIEM standardizes the data by unifying field definitions and converting formats, ensuring consistency and analyzability. The system then encrypts and stores the normalized logs in a secure database, meeting compliance requirements (e.g., retaining logs for 6+ months) and ensuring data integrity for easy retrieval and auditing.
Correlation Analysis
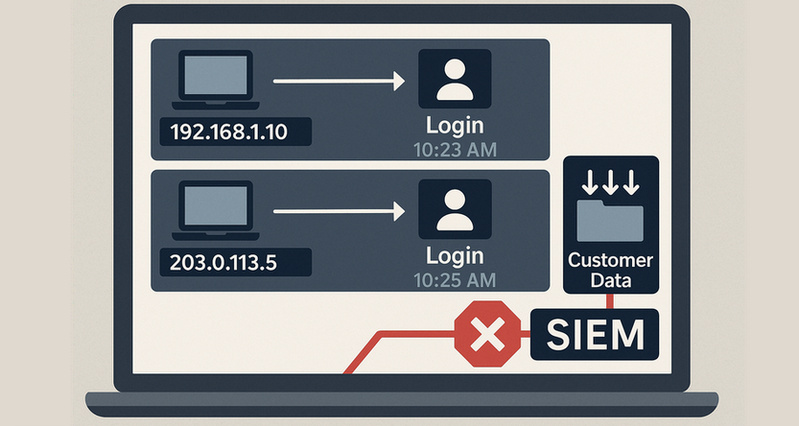
This step enables intelligent anomaly detection. Using preset rules and AI algorithms, SIEM identifies logical relationships between events to uncover potential threats. For example, if it detects both "the same account logging in from Paris and New York within 10 minutes" and "an immediate attempt to download the core customer database," SIEM flags this as high-risk behavior. By correlating events rather than examining them in isolation, the system significantly improves threat detection accuracy.
Visualization & Alerting
SIEM provides a clear security overview through visual dashboards, displaying charts of key metrics such as real-time threat counts, high-risk event distribution, and core asset security status. This allows administrators to quickly assess the organization’s security posture.
For risks identified through correlation analysis, the system sends tiered alerts (e.g., high-risk, medium-risk) to administrators. Alerts include key incident details and are delivered via email, SMS, or platform notifications to ensure timely response.
Response & Forensics
Once an alert is triggered, SIEM closes the "response-attribution" loop. It can integrate with SOAR tools to automatically perform basic responses, such as blocking abnormal IPs and isolating affected endpoints. Simultaneously, administrators can investigate event attribution: retrieve full log chains, reconstruct attack paths (e.g., entry point, firewall bypass, affected files), and assess the incident’s impact. This provides the basis for refining security strategies.
With a clear understanding of what SIEM is, why it matters, and how it operates, you now have a comprehensive view of its value. Keep reading to explore more advanced insights and practical applications.

Discover how DLP software delivers compliance, prevents insider threats, and secures sensitive information across endpoints, cloud services, and networks. Learn more>>
FAQs About SIEM
How does SIEM differ from firewalls and antivirus software?
Firewalls and antivirus software act as the "frontline defenses," whereas SIEM serves as the "command center." It aggregates and analyzes logs from these protection points to provide a comprehensive, organization-wide view of risks.
Is SIEM suitable for small and medium-sized enterprises?
While SIEM used to be costly and complex, modern lightweight and cloud-based solutions make it feasible for businesses of all sizes, allowing deployment according to specific needs.
Can SIEM automatically block attacks?
Traditional SIEM systems focus mainly on detection and alerting. However, when integrated with SOAR or UEBA, they can support automated responses and active defense measures.
What role does SIEM play in compliance audits?
SIEM records complete security logs and event chains, providing organizations with reliable audit evidence that meets regulatory standards such as GDPR, ISO27001, and other cybersecurity laws.
Conclusion
The value of SIEM goes beyond threat detection—it enables enterprises to truly "understand risks." In today’s era of zero trust and heightened data security, SIEM is evolving from a behind-the-scenes "analyst" into a proactive "commander." Looking forward, it will increasingly integrate with AI, UEBA, and SOAR to form an intelligent enterprise security brain, allowing organizations to shift from "post-incident response" to "pre-incident insight and prevention."
If you need a SIEM solution urgently, you are welcome to download AnySecura and try it for free!


