Keystroke loggers, also known as keyloggers, are often mentioned in discussions about security, employee monitoring, and data protection. Some organizations encounter them as malicious software, while others actively search for keystroke logging tools to gain more visibility into employee activity.
Are keystroke loggers a security threat, a monitoring solution, or both? And more importantly, do organizations really need to record every keystroke to protect data and manage risk?
In this article, we explain what a keystroke logger is, how malicious keyloggers can be detected and removed, why some organizations choose to use keystroke logging, and the risks that come with it.

What Is a Keystroke Logger?
A keylogger, also known as keystroke logger or keyboard logging software, is a tool designed to record every keystroke typed on a device. This includes emails, messages, passwords, and form inputs. Keyloggers often run continuously and may operate in the background without obvious signs to the user.
Keyloggers can exist as software installed on a computer or as hardware devices physically connected to a keyboard. In both cases, the core function is the same: capturing raw keyboard input without distinguishing between work-related activity and private information.
Keystroke logging can be used for legitimate purposes, such as troubleshooting or limited security monitoring, but it is also commonly associated with malicious activity, including credential theft and surveillance.
How to Detect and Remove KeyStroke Logger
When keystroke logger malware is present inside a company, it can create serious security and business risks. These tools can silently record what employees type, including passwords, internal messages, and access to sensitive systems. Over time, this can lead to stolen credentials, data leaks, and unauthorized access without anyone noticing.
Because keystroke logger malware often runs quietly in the background, it may remain undetected for long periods. For this reason, companies need a clear and structured way to identify and remove it before real damage occurs.
How Organizations Can Detect Keystroke Logger Malware?
Detecting keystroke logger malware usually requires an enterprise-level endpoint management tool. In large organizations, it is not practical to rely on manual checks or individual user reports. A centralized system helps IT and security teams see what is happening across all company devices from one place.
Detection usually starts with having basic visibility into company devices. IT and security teams should regularly check what software is running on employee computers and compare it with approved applications. It is also important to keep track of company hardware.
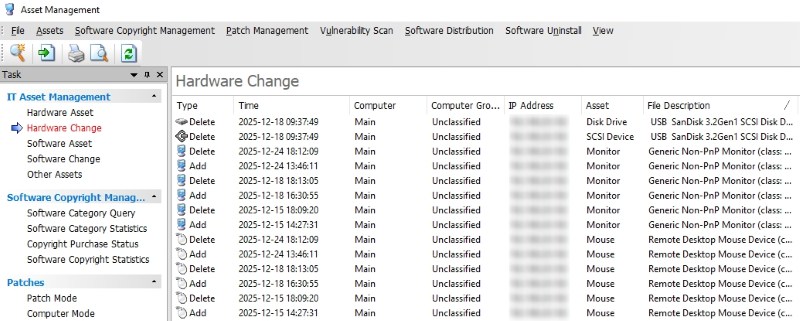
One common warning sign of keystroke logger malware is the presence of programs or background processes that no one recognizes. These may not appear on the desktop but can still be active in the system.
IT teams can check keylogger malware by reviewing the list of running programs and startup items on company devices, as well as the installed software list managed by the operating system or endpoint tools.
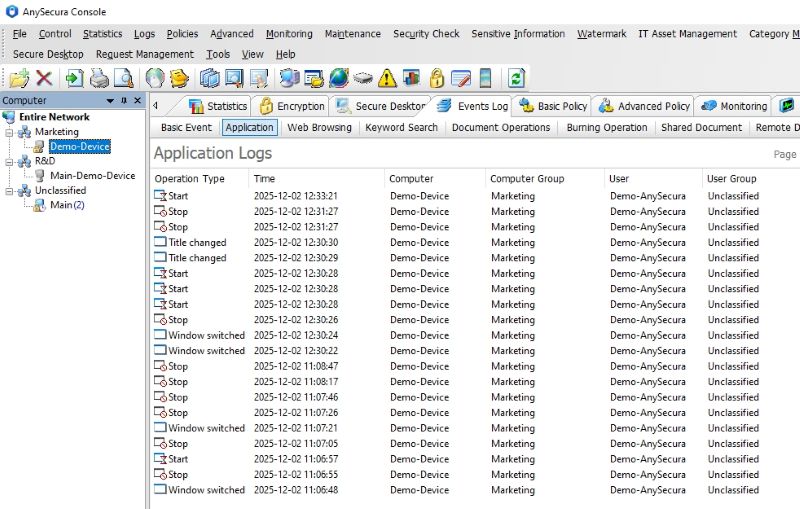
Using a central software center makes detection much easier. When employees install software only through approved company channels, any unknown application stands out quickly. This reduces blind spots and limits how malware enters the environment.

Network behavior can offer another clue. If a device starts sending data outside the company network more frequently than usual, especially in small and repeated amounts, it may indicate that typed information is being recorded and transmitted.
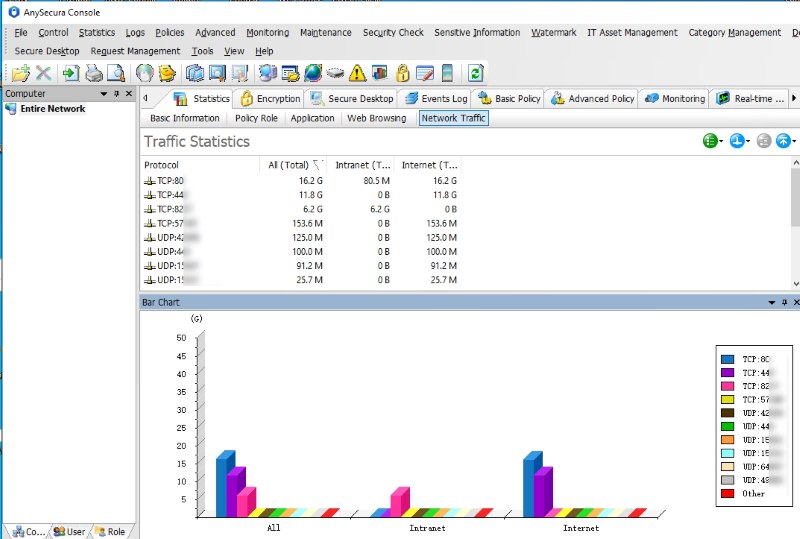
When several of these signs appear at the same time, the device should be treated as potentially infected and investigated further.

Compare top endpoint management software in 2026, including Intune, Workspace ONE, ManageEngine, Ivanti, and AnySecura, for secure device management and DLP.Learn more>>
How to Remove Keystroke Logger Malware
Once a keystroke logger malware is confirmed or strongly suspected, it should be handled as a security incident.
The first step is usually to run a full security scan on the affected device using company-approved security tools. Any unauthorized or suspicious software should be removed. Security teams may also need to review recent system changes to understand how the malware was introduced.
If the infection is severe or the source is unclear, the safest option is often to reset the device or reinstall the operating system. While this may take more time, it helps ensure that hidden components of the malware are fully removed and cannot return.
After the device is cleaned, all passwords must be changed. Because keystroke loggers record everything typed, login credentials, internal system passwords, and even personal account details may have been captured. Password changes should be done as soon as possible and, when available, combined with multi-factor authentication.
Organizations should review how the malware entered the system. This may involve tightening software controls, improving employee guidance, or updating security policies. Removal fixes the immediate problem, but prevention reduces the chance of it happening again.
Why Organizations Use Keystroke Loggers
Not all keystroke loggers are introduced as malware. In some cases, organizations actively look for keystroke logging tools as part of their own monitoring or risk management efforts. It's not because they want to spy on employees. They are trying to gain clearer visibility into employee activity or reduce specific risks.
Many employee monitoring and insider risk products include keystroke logging as a feature. These tools are often marketed as a way to "see everything," confirm whether work is being done, or collect detailed evidence during investigations.
In these moments, keystroke logging can feel like a simple answer.
Risks of Using a Keystroke Logger
The sense of control when using keystroke logger is often misleading. Recording everything also means collecting large amounts of sensitive and personal data, much of which has nothing to do with real risk. In fact, they usually create new ones.
The first and most obvious risk is overcollection. Keystroke loggers do not distinguish between what is important and what is not. They record everything that is typed. This can include situations where an employee is entering a password, logging into a personal account, or typing private information that is unrelated to work.
Once this data exists, the organization becomes responsible for storing it securely, limiting access, and explaining why it was collected. In this case, Keystroke logs themselves become sensitive assets. If they are accessed by the wrong people, misconfigured, or leaked, the impact can be severe. In some cases, the data collected by keystroke loggers is more sensitive than the data the organization was trying to protect in the first place.
Keystroke logging can damage trust and workplace culture. Employees who know or suspect that every key they type is recorded may feel monitored rather than supported. This can lower morale, reduce engagement, and push people to change their behavior in unproductive ways. Instead of working better, they may work around the system.
Alternatives to Keystroke Loggers (And a Less Invasive Approach)
Many organizations are ditching the "more data = better control" mindset. The goal isn’t to monitor less, it’s to monitor the right things.
Instead of recording every keystroke, modern solutions track high-impact business outcomes: how sensitive data is accessed, shared, and whether actions violate policies. When you can see these critical signals clearly, keystroke logging becomes obsolete.
The best alternatives answer three key questions: what happened, when it happened, and whether it created risk.
AnySecura: A Less Invasive Alternative to Keystroke Logging
AnySecura avoids logging raw keystrokes altogether, making it a less invasive alternative to keystroke logging. Instead of secretly recording every letter typed, AnySecura focuses on what employees do, their actions and behaviors, without prying into the exact content they type.
What AnySecura Monitors Instead of Keystrokes
AnySecura replaces keylogging with tracking of important activities, and scans for specific risk indicators. For example,
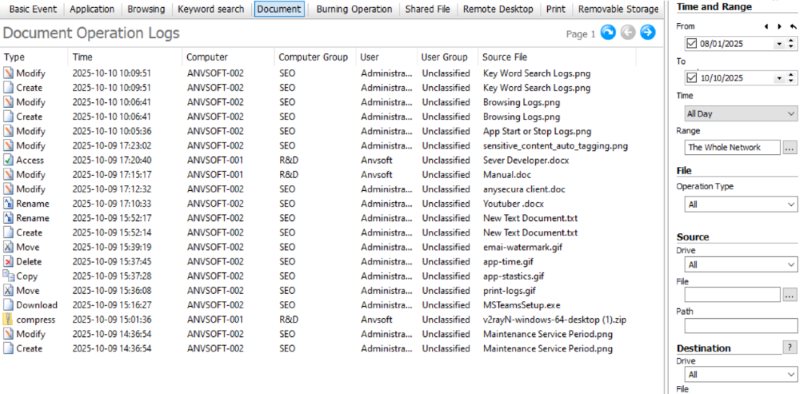
- Watches file actions (when files are opened, copied, edited, or deleted) and keeps context like who did it and when.
- Tracks application and web usage, noting which programs are run and which websites are visited.
- Monitors communications on work channels, logging work emails and chat messages and who they’re sent to, to catch any unauthorized sharing of information.
If a document or email contains certain sensitive keywords or data (like confidential project names or customer info), AnySecura will flag that action. It even watches for physical data movement: if someone tries to copy data onto a USB drive or print a confidential file, AnySecura will log it and can alert managers in real time.
Flexible Control, Not Over-Monitoring
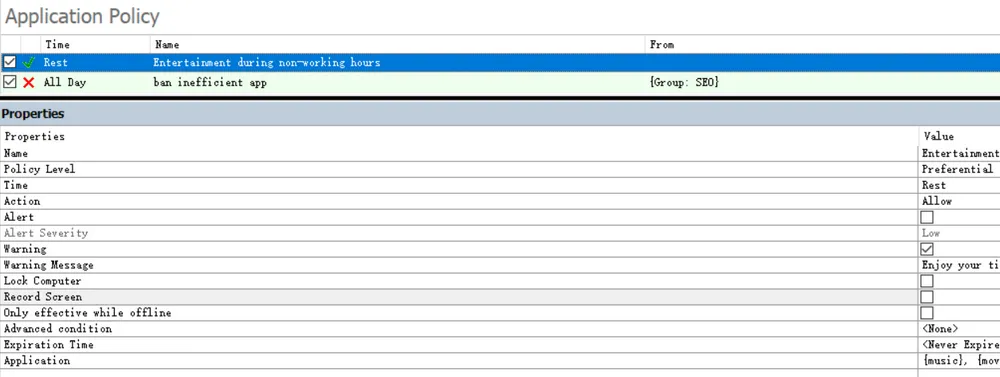
Beyond visibility, AnySecura gives organizations direct control. With AnySecura, administrators can enforce policy-based controls, for example, restricting file transfers, applications, or website access during inappropriate working hours.
Rather than spending time watching employees, companies can manage risk more effectively by applying a single policy across the entire organization, achieving better security and higher operational efficiency.
More Manageable and Proactive
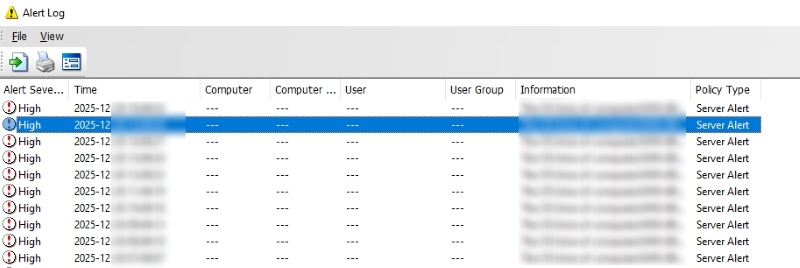
AnySecura organizes all collected data into structured reports and real-time alerts. Managers are notified only of meaningful events, such as forbidden file transfers or visits to high-risk websites, without having to sift through thousands of keystrokes. Powerful search and filtering tools make it easy to focus on what truly matters, enabling security teams to respond faster and concentrate on genuine threats instead of trivial details.
With AnySecura, employees are less likely to feel "watched" by an invasive spy program, managers also feel easier to comply with privacy laws and policies. AnySecura adheres to strict data privacy regulations like GDPR, helping you builds trust and transparency across your team.
FAQs about Keystroke Logger
Is a keystroke logger legal?
The legality of keystroke loggers depends on local laws and how they are used. In many regions, employers must clearly inform employees and explain what is being recorded and why. Even when keystroke logging is technically legal, companies may still face compliance and privacy risks if the data collected is broader than necessary.
Can keystroke loggers record passwords?
Yes. Keystroke loggers record everything that is typed on a keyboard. This can include login credentials, passwords, personal messages, and other sensitive information, even when it is unrelated to work. This is one of the main reasons keystroke logging is considered high risk.
Are keystroke loggers ethical in the workplace?
Many organizations consider keystroke logging unethical because it records private and personal information without context. Employees may feel constantly monitored rather than supported, which can damage trust and workplace culture. For this reason, many companies now prefer less invasive monitoring approaches that focus on work-related actions instead of raw typing data.
Conclusion
Keystroke loggers promise full visibility by recording everything an employee types. In practice, this approach often creates more risk than clarity. Malicious keyloggers can expose credentials and sensitive data, while intentional keystroke logging raises serious privacy, compliance, and trust concerns.
As organizations mature, many realize that effective monitoring does not require capturing every keystroke. What matters is understanding what happened, when it happened, and whether it created risk. When those questions can be answered without collecting raw typing data, keystroke logging becomes unnecessary.
If your organization is rethinking keystroke logging and looking for a more balanced way to manage risk, AnySecura provides a less invasive employee monitoring approach focused on actions that matter, without recording every keystroke.


