In today’s enterprise security environment, cyberattacks are no longer a question of if they will happen, but when and in what form. No matter how comprehensive preventive controls may be, risks such as exploited vulnerabilities, stolen credentials, or internal operational mistakes can never be fully eliminated.
When an attack actually occurs, the challenge for businesses isn’t just dealing with the attack itself. It’s figuring out where it came from, stopping the risk from getting worse, and checking if business systems or important data have taken permanent damage. DFIR (Digital Forensics and Incident Response) is designed precisely to address these challenges.
What Is DFIR
DFIR is the combination of Digital Forensics and Incident Response. It is not a single tool or technology, but a comprehensive methodology centered on security incidents. Its purpose is to help organizations quickly control risks and clearly figure out what happened when an attack has already occurred or is still ongoing.
The Two Core Components of DFIR
DFIR consists of two complementary pillars: Digital Forensics and Incident Response. Together, they allow enterprises to both control risks quickly and figure out exactly how the attack happened, providing a solid foundation for future improvement.
1. Digital Forensics
Digital Forensics focuses on "what exactly happened". Through the analysis of systems, logs, and data, it helps answer questions such as:
- Where did the attack originate (phishing emails, system vulnerabilities, abuse of internal privileges, etc.)?
- What actions did the attacker take (including file operations, account misuse, network access, or privilege escalation)?
- Whether critical data such as customer information or proprietary business data was leaked, tampered with, or deleted?
- Whether the incident involved insider threats or management process issues, supporting organizational improvements?
Common forensic data sources include:
- Host disks and memory: analyzing runtime behavior and recovering deleted files.
- System and application logs: recording logins, operations, and abnormal events to reconstruct timelines.
- Network traffic and communication records: identifying data transfers, exfiltration, or external communications.
- Email, file, and account activities: tracing data movement paths, abnormal actions, and internal policy violations.
2. Incident Response
Incident Response focuses on "what should be done right now". Its goal is to quickly regain control, minimize damage, and restore business operations. Key activities include:
- Confirming whether an actual attack has occurred, distinguishing real threats from system failures.
- Rapidly identifying affected systems and accounts to define the scope of impact.
- Isolating compromised devices by disconnecting networks, disabling abnormal accounts, or closing suspicious ports.
- Removing malicious programs and abnormal privileges by cleaning malware, fixing system configurations, and restoring proper access controls.
- Restoring business systems after ensuring the environment is safe and controllable.
Typical scenarios where DFIR is applied include:
- Ransomware attacks: stopping further spread and assessing whether data was exfiltrated.
- Account compromise and privilege abuse: locking down stolen accounts used to access internal systems.
- Malware outbreaks: containing and eradicating rapidly spreading malicious software.
The Complete DFIR Process
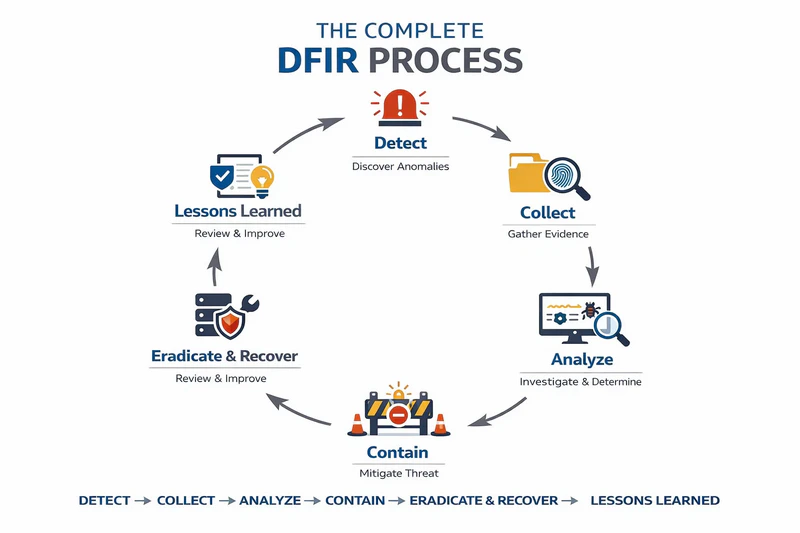
DFIR is not a one-time action, but a cyclical and progressive process. From anomaly detection to post-incident review, each step builds on the previous one. It ensures businesses not only respond quickly but also keep improving their security defenses.
1. Detection
The goal is to identify potential security incidents as early as possible. Enterprises continuously monitor system operations and analyze logs, while also collecting reports from employees or administrators about things like repeated failed logins or odd data transfers to catch suspicious behavior right away.
2. Collection
The objective is to gather complete and reproducible evidence to support subsequent analysis and response. This includes collecting logs, memory data, and disk data from endpoints and servers, as well as network traffic records, cloud service operation logs, and email records. Special care must be taken to ensure evidence integrity and prevent tampering.
3. Analysis
This stage focuses on understanding how the attacker breached defenses, which systems and data were affected, and whether hidden risks remain. Analysts build a detailed timeline of events, examine attack techniques such as malware, phishing, or insider threats, and determine the scope of data leakage or tampering to support recovery and future defense planning.
4. Containment
The objective is to quickly stop the spread of the attack and protect critical systems and data. Typical actions include isolating infected devices, freezing abnormal accounts, blocking malicious IPs or domains, and adjusting firewall rules or access controls to prevent further propagation.
5. Eradication & Recovery
The goal is to fully remove security threats and restart business systems safely, ensuring the company can operate normally again. At this stage, you need to completely wipe out malware from devices and close any backdoors attackers left behind. You’ll also patch system vulnerabilities, fix misconfigurations, and seal up all security gaps. Then restore affected data and systems in order of priority. After restoration, verify everything is secure and intact to make sure business operations can run smoothly again.
6. Lessons Learned
At this stage, you need to figure out why the incident happened and where the response process fell short. Update your security policies, share what you’ve learned with management and the team, raise everyone’s security awareness, and prevent similar issues from happening again.
Which Organizations Need DFIR
Not every organization gets the same value from DFIR when facing a security incident. But in the following scenarios, DFIR is absolutely essential:
High-Value Target Industries
Industries such as finance, manufacturing, and healthcare manage highly sensitive data and critical systems. A breach can lead to financial losses, regulatory penalties, and serious reputational damage. Here are some examples:
- Financial institutions: Stolen transaction data or customer information can result in heavy fines and regulatory action.
- Manufacturers: Leaked core product designs blueprints can severely undermine company’s market competitiveness.
- Healthcare organizations: Breached patient health data can lead to legal disputes and seriously damage the hospital’s reputation.
Data-Sensitive Organizations with High Breach Costs
Internet platforms, cloud service providers, and research institutions treat data as a core asset. A data breach can lead to immediate financial losses, compliance fines, and a sharp drop in brand reputation. DFIR helps them quickly find out whether data was leaked, how much was affected, and the scope of impact, enabling timely remediation.
Organizations with Compliance and Regulatory Requirements
In regulated industries, organizations must strictly follow laws, regulations, or industry standards. After a security incident, these businesses don’t just need to resolve the attack. They also have to submit complete, verifiable investigation reports to regulators. DFIR provides clear evidence chains and analysis results to meet audit and regulatory expectations.
The Value of AnySecura in DFIR
As an enterprise-oriented security management platform, AnySecura provides strong support for DFIR across multiple dimensions:
- Endpoint behavior control: records document operations, software usage, network access, and peripheral activity, while restricting high-risk programs and external devices to reduce attack surfaces.
- Document operation auditing: tracks document creation, modification, copying, deletion, and external sharing, forming traceable evidence chains for digital forensics and compliance.
- Sensitive content detection & blocking: identifies sensitive information and blocks unauthorized transfers via email, cloud storage, or IM channels.
- Screen monitoring & watermarking: supports real-time screen monitoring and playback, with dynamic watermarks applied to screens and sensitive documents for forensic evidence.
- Transparent encryption & data protection: enforces encryption for critical documents, preventing access outside authorized environments and stopping secondary data leakage.
With these capabilities, AnySecura not only helps detect risks early and prevent data leaks, but also preserve complete data records, respond to incidents quickly and support post-incident reviews. It enables full-cycle DFIR management, helping businesses turn security incidents from something unmanageable into a closed loop that is controllable, traceable and reviewable.

Compare top endpoint management software in 2026, including Intune, Workspace ONE, ManageEngine, Ivanti, and AnySecura, for secure device management and DLP.Learn more>>
Conclusion
In real-world enterprise environments, security incidents are no longer a question of whether they will occur, but when they will occur and how organizations will respond. Relying solely on preventive controls and alerts may indicate that "something went wrong", but often fails to explain what happened, how severe the impact was, or whether the issue has been fully resolved.
The true value of DFIR lies in providing a structured, verifiable, and reviewable methodology—from early detection and evidence preservation, to root-cause analysis, risk containment, business recovery, and continuous improvement. This capability allows enterprises to move beyond confusion and uncertainty and is becoming an essential component of modern enterprise security.


