Endpoint security tools play a critical role in protecting enterprise networks and data. CrowdStrike's Falcon platform is widely recognized for its cloud-native architecture, AI-driven threat detection, and comprehensive XDR capabilities.
However, this major brand isn't for every company. If you are looking for a more cost-effective or better-suited endpoint security solution for your organization, this article is for you. We've selected 10 noteworthy CrowdStrike competitors in 2026 to help you make an informed decision.

Top 10 CrowdStrike Competitors and Alternatives in 2026
Quick Guide: 10 CrowdStrike Competitors and Their Core Use Cases
| Tool Name | Core Purpose |
|---|---|
| SentinelOne | Autonomous, offline-capable endpoint protection with built-in ransomware rollback. |
| Microsoft Defender for Endpoint | Best choice for Microsoft 365 environments with built-in, low-cost EDR. |
| AnySecura | Best for protecting sensitive documents, preventing insider risk, and controlling data after sharing |
| Palo Alto Cortex XDR | Deep endpoint-network correlation for Palo Alto security stacks |
| Sophos | Cloud-based UEM/MDM for securing and managing remote and mobile devices |
| Cisco Secure Endpoint | Tight endpoint and network integration for Cisco-centric environments. |
| Carbon Black | Deep endpoint telemetry for advanced forensics and customization. |
| Trend Micro Vision One | True XDR visibility across endpoint, email, network, and cloud. |
| Fortinet FortiEDR / FortiXDR | Endpoint protection integrated into Fortinet's Security Fabric, including on-prem support. |
| Bitdefender GravityZone | High-quality endpoint protection at a much lower cost |
SentinelOne
SentinelOne Singularity is an endpoint security tool that uses AI to find and stop threats in real time. Like CrowdStrike, it combines next-generation antivirus with full EDR features. This is why it's often seen as a direct CrowdStrike competitor. SentinelOne has done well in independent tests. It got perfect detection and protection results in MITRE ATT&CK evaluations. Detailed performance reports are available on its website.

SentinelOne stands out because it relies on its endpoint agent and on-device AI. The agent makes security decisions on the device itself, so it can detect, block, and fix threats even when the device is offline. This enables fast, automatic actions, such as stopping malicious processes or undoing ransomware changes, without waiting for a security analyst. SentinelOne also includes longer EDR data retention by default and requires fewer paid add-ons, which helps organizations control costs and protect systems in environments with limited or unstable connectivity.
That same design comes with some trade-offs compared to CrowdStrike. CrowdStrike operates one of the largest threat intelligence networks in the industry and offers a mature, human-led threat hunting service that SentinelOne doesn't fully match at the same scale. SentinelOne can also require more tuning and policy setup in complex environments, which may feel less straightforward for smaller security teams looking for a more hands-off experience.
 Choose SentinelOne If
Choose SentinelOne If- You need strong offline or air-gapped protection, where endpoints must defend themselves without cloud access.
- You want automatic remediation, such as killing attacks and rolling back ransomware with little human effort.
- You prefer simpler pricing for EDR data retention and want to avoid paying extra for telemetry storage.
 Choose CrowdStrike If
Choose CrowdStrike If- You rely heavily on advanced threat intelligence and human-driven threat hunting.
- You want a very mature, easy-to-use platform with minimal tuning and fast deployment.
- You prefer a single, unified security platform that covers endpoint, identity, cloud, and more.
Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is part of Microsoft's broader security stack, not a standalone tool. It builds on Windows' built-in security features, adds cloud-based threat intelligence, and connects with Microsoft 365 services like email, identity, and cloud apps. This lets teams manage endpoint security as part of a wider security picture rather than in isolation.
Microsoft Defender for Endpoint covers the same core areas as CrowdStrike, including next-generation malware protection, behavioral detection, and automated investigation and remediation. Because of this, it's widely regarded as a leading enterprise endpoint security platform and is often positioned alongside CrowdStrike as a Leader in Gartner's Endpoint Protection Platforms Magic Quadrant.
Microsoft Defender is the best CrowdStrike competitor when you're already deep in the Microsoft world. If your team is using Microsoft 365, Azure AD, Intune, and Microsoft's security tools, Defender works with your current setup. You get visibility across endpoints, identities, email, and cloud services without having to stitch multiple tools together. For many organizations, Defender for Endpoint is already covered by their Microsoft 365 licenses. So it's much cheaper than buying CrowdStrike as a separate product. And because Defender can also automatically investigate and fix certain issues on its own, it takes a lot of pressure off smaller security teams that don't have the time or headcount to adjust everything manually.
Microsoft Defender is still fundamentally built around Windows. While Microsoft has made solid progress supporting macOS, Linux, and mobile devices, the experience isn't as consistent as what CrowdStrike delivers across platforms. Managing security in Microsoft’s ecosystem can be confusing, with alerts and controls in different places. By contrast, CrowdStrike centralizes everything in a single and cloud-native console. On top of that, CrowdStrike's focus as a pure-play cybersecurity company gives it an advantage in areas like advanced threat hunting and managed detection, capabilities many organizations consider more mature than Microsoft's add-on security services.
 Choose Microsoft Defender If
Choose Microsoft Defender If
- Your organization already uses Microsoft 365, Azure, and Intune, and wants tight, native integration.
- You want to reduce costs by using security tools included in existing Microsoft licenses.
- You have a small security team and need strong automated investigation and remediation.
 Choose CrowdStrike If
Choose CrowdStrike If
- You run a mixed or non-Microsoft environment and want equal support across all operating systems.
- You prefer a single, simple security console with minimal portal switching.
- You need advanced threat hunting, MDR services, and deep adversary intelligence from a security-focused vendor.
AnySecura
AnySecura competes with CrowdStrike from a different but increasingly critical angle: data protection rather than endpoint threat detection. While CrowdStrike focuses on stopping malware, exploits, and adversaries at the device level, AnySecura addresses a gap that endpoint security does not solve, how sensitive documents are accessed, used, and shared by trusted users.
It's mainly targeted at security-conscious organizations that want a single tool to both manage and monitor remote endpoints across Windows networks. Its agent-based model makes it especially useful for mid-sized enterprises or teams with distributed employees using company devices.
For companies whose biggest risk comes from internal misuse, overexposure of files, or compliance-driven data leakage, AnySecura is often evaluated instead of adding another EDR layer.

AnySecura's key differentiation is persistent, file-level protection that travels with the document itself, not the device.
- Granular file-level access control: Define who can open, edit, copy, print, or share a document, regardless of where it's stored or who receives it.
- Full document operation audit trail: Every action, open, modify, copy, rename, delete, is logged and traceable for compliance and investigations.
- Persistent protection after sharing: Files remain encrypted and policy-controlled even after being emailed, uploaded to cloud storage, or copied to external devices.
This data-centric approach directly addresses scenarios where CrowdStrike has limited visibility, authorized users misusing data, sensitive documents leaving managed endpoints, or compliance audits requiring detailed file activity records.
AnySecura is not an EDR or malware prevention platform. It does not replace CrowdStrike's ability to detect exploits, ransomware execution, or nation-state attackers at the endpoint level.
Organizations facing high volumes of external threats, advanced malware campaigns, or requiring SOC-driven threat hunting will still need an endpoint security solution like CrowdStrike alongside, or in addition to, AnySecura.
 Choose AnySecura If
Choose AnySecura If
- Your primary concern is data leakage, insider risk, or compliance, not malware
- Sensitive documents must remain protected after sharing or leaving the company network
- You need auditable, file-level visibility for regulations, IP protection, or legal defense
 Choose CrowdStrike If
Choose CrowdStrike If
- Your top priority is preventing external attacks and endpoint compromise
- You operate a SOC that relies on threat intelligence and behavioral detection
- Data exposure is a secondary concern compared to malware and intrusion prevention

Discover how DLP software delivers compliance, prevents insider threats, and secures sensitive information across endpoints, cloud services, and networks. Learn more>>
Palo Alto Cortex XDR
Cortex XDR is a detection and response platform from Palo Alto Networks. It collects data from endpoints, networks, and cloud systems to find and stop attacks. It uses Palo Alto's analytics and threat intelligence from Unit 42. Unlike tools that focus only on endpoints, Cortex XDR links activity from endpoints, firewalls, cloud workloads, and other sources. This gives security teams a wider view of attacks that move across different systems, which puts it in direct competition with CrowdStrike.
Cortex XDR works best in environments that already use Palo Alto security products. If an organization runs Palo Alto firewalls or cloud security tools, Cortex XDR can connect endpoint activity with network traffic and firewall data. This helps teams see how an attack starts, spreads, and moves between systems. It also allows automatic actions across layers, such as isolating an endpoint while blocking a malicious IP address at the firewall. In CrowdStrike deployments, this type of network response usually depends on separate integrations.
Cortex XDR delivers less value outside a Palo Alto–focused setup. Without Palo Alto firewalls or related tools, its network-level visibility and response are limited. Setup and configuration can also take more effort than CrowdStrike's cloud-first approach, especially when adding network devices and log sources. For teams that mainly want endpoint protection and threat hunting, Cortex XDR may feel complex, while CrowdStrike remains easier to use for endpoint-focused security.
 Choose Cortex XDR If
Choose Cortex XDR If- You already use Palo Alto firewalls or security products and want deep, native integration.
- You need endpoint + network visibility in one platform to detect multi-stage attacks.
- You want automated response across endpoints and network controls, not just endpoint isolation.
 Choose CrowdStrike If
Choose CrowdStrike If- You want a vendor-neutral, endpoint-first solution that works well with any network stack.
- You value fast deployment and ease of use with a single cloud-native console.
- Your priority is best-in-class endpoint detection and threat hunting, without needing built-in network telemetry.
Sophos
Sophos Intercept X mixes traditional antivirus with newer detection methods and can restore files after a ransomware attack. Teams manage it through the Sophos Central cloud dashboard, and Sophos also offers an optional monitoring service called Sophos MTR. Sophos is widely used by small and mid-sized businesses and schools, and it competes with CrowdStrike by offering solid protection in a product that is easier to set up and run.
Sophos Intercept X focuses on stopping problems directly on the device. Its agent runs on the computer and looks for suspicious behavior to block malware, exploits, and ransomware before damage happens. It does not depend heavily on constant cloud checks. The same agent also handles basic controls like website blocking, app blocking, USB and device control, and network threat detection. When used with Sophos firewalls and email tools, all of this information shows up in one place.
By contrary, CrowdStrike is usually a better fit for teams that spend a lot of time investigating attacks. It gives more detailed data and tools for deep analysis. Sophos's strict blocking can need extra adjustment and may sometimes stop normal activity in complex setups. Large companies often choose CrowdStrike for scale and advanced analysis, while Sophos is more often chosen by smaller teams that want simpler tools and fewer systems to manage.
 Choose Sophos Intercept X If
Choose Sophos Intercept X If
- You want strong on-device prevention that stops threats instantly, including ransomware rollback.
- You prefer an all-in-one security suite with endpoint, firewall, email, and XDR tightly integrated.
- You have a small or mid-sized IT team and want simpler, more guided day-to-day management.
 Choose CrowdStrike If
Choose CrowdStrike If
- You need advanced EDR, threat hunting, and detailed endpoint telemetry.
- You want very low false positives and highly refined detection accuracy.
- You are a large or complex enterprise that prefers a best-of-breed, endpoint-focused solution with broad third-party integrations.
Cisco Secure Endpoint
Cisco Secure Endpoint is Cisco's cloud-based tool for protecting computers and servers. It looks for malware, tracks suspicious activity, and analyzes unknown files using Cisco Threat Grid. It connects with Cisco SecureX, which links endpoint security with Cisco's network, email, web, and cloud tools. Cisco Talos provides the threat data behind it. Compared to CrowdStrike, Cisco Secure Endpoint takes a more network-focused approach to endpoint security.
Cisco Secure Endpoint works best in environments that already use Cisco security products. When the system detects a problem on a device, it can trigger actions on the network, such as cutting the device off using Cisco ISE or blocking traffic with Cisco firewalls or Umbrella. Cisco also scores devices based on risk, such as missing updates or unsafe software, which helps teams decide what to fix first. For organizations already paying for Cisco security tools, Secure Endpoint often fits in easily and keeps costs predictable.
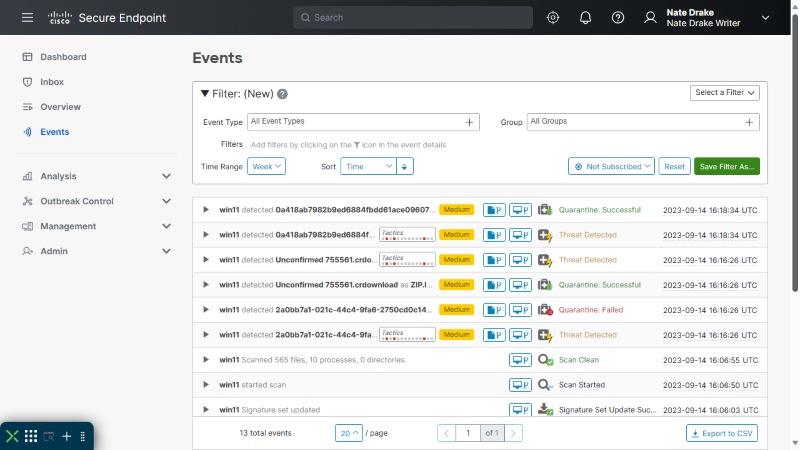
When dealing with more serious or complex attacks, many teams find CrowdStrike works better. CrowdStrike often detects threats faster, gives clearer investigation data, and handles ransomware and advanced attacks more effectively. Cisco Secure Endpoint is often seen as acceptable, but not the top choice. Its setup and management can also feel spread out across several tools. CrowdStrike's agent is usually lighter on system performance, while Cisco's agent does more work on the device. For teams that focus on deep investigation and endpoint-only security, CrowdStrike is usually the easier choice.
 Choose Cisco If
Choose Cisco If
- You already use Cisco firewalls, identity, or security tools and want tight endpoint–network integration.
- You value built-in vulnerability and risk scoring alongside endpoint protection.
- You want a cost-effective option through Cisco bundles or managed services, with simpler EDR needs.
 Choose CrowdStrike If
Choose CrowdStrike If
- You need best-in-class threat detection and response, especially for ransomware and advanced attacks.
- You want a single, modern cloud console that is easy to use and purpose-built for EDR.
- You require advanced threat hunting, strong incident response support, and low endpoint performance impact across many operating systems.

Compare top endpoint management software in 2026, including Intune, Workspace ONE, ManageEngine, Ivanti, and AnySecura, for secure device management and DLP. Learn more>>
Carbon Black
VMware Carbon Black is an endpoint security tool that combines antivirus, threat detection, and investigation features. It was one of the early tools in the EDR space and is now offered through the Carbon Black Cloud as part of VMware's security products. Carbon Black records activity on endpoints and uses behavior patterns to find threats. Because it keeps detailed records, it often competes with CrowdStrike for teams that want to understand exactly what happened during an attack.
Carbon Black stands out because it collects a lot of activity data from each endpoint. This lets security teams replay attacks, see how processes started and spread, and investigate incidents even days or weeks later. Teams can also adjust rules and controls to match their own needs. Carbon Black often bundles antivirus and EDR into a single license, which some organizations find easier to plan for than CrowdStrike's add-on pricing. For companies already using VMware systems, Carbon Black usually fits well into their virtual and cloud setups.
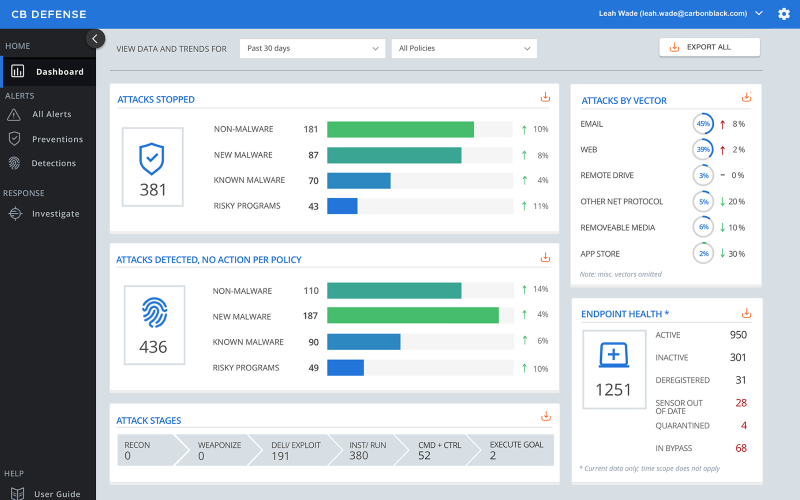
CrowdStrike is usually quicker to set up and easier to run, especially for smaller teams or teams with less security experience. Carbon Black produces a lot of raw data, which can be hard to manage without dedicated analysts. CrowdStrike filters alerts more aggressively, which helps teams focus on what matters day to day. CrowdStrike's agent also tends to use fewer system resources, while Carbon Black's constant data collection can slow devices down. CrowdStrike's managed security service is also more established, making it a better choice for organizations that want expert support with less internal effort.
 Choose Carbon Black If
Choose Carbon Black If
- You need deep endpoint telemetry and forensic detail for investigations and custom detection.
- You want simpler, bundled pricing that includes core NGAV and EDR features.
- You already use VMware infrastructure and want tight integration with virtualized and cloud workloads.
 Choose CrowdStrike If
Choose CrowdStrike If
- You want a simpler, more intuitive EDR platform with less noise and faster analyst workflows.
- Endpoint performance and lightweight agents are a top priority.
- You need mature MDR services, strong vendor support, and a security-first company focus.
Trend Micro Vision One
Trend Micro Vision One brings security data from many places into one view, including computers, email, servers, cloud systems, and networks. It is built by Trend Micro and pulls information from its endpoint tool, Apex One, along with other Trend Micro products. Vision One uses automation and Trend Micro's threat data to help teams see problems that span more than one system. Compared to CrowdStrike, it focuses more on the full picture of an attack, not just what happens on the endpoint.
Vision One is strongest when teams want to connect events across different systems. It can link a phishing email to activity on a computer and then to unusual network traffic, helping teams understand how an attack moves step by step. It also helps teams spot risks such as unsafe settings, unpatched devices, or risky user behavior, not just active attacks. For organizations already using Trend Micro tools, Vision One adds this broader view without needing to install another endpoint agent, which makes rollout simpler and keeps costs down.
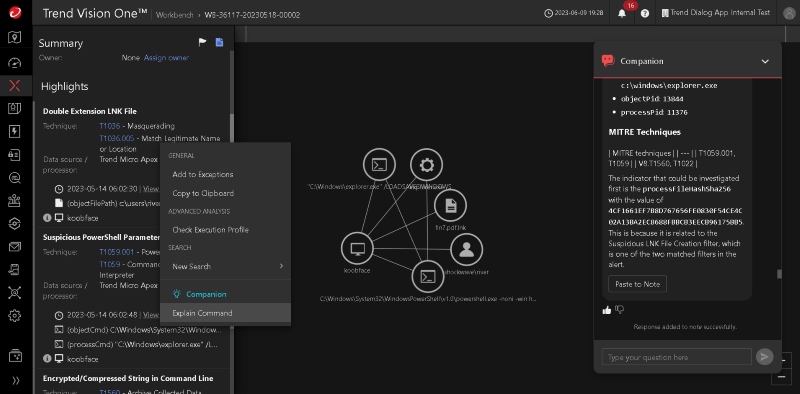
CrowdStrike is often a better fit when teams care most about endpoint speed and ease of use. Its agent is known for having little impact on system performance, while Trend's endpoint agent has traditionally used more resources, even though it has improved over time. CrowdStrike also offers a cleaner and more focused interface for day-to-day work. If a team does not plan to actively use security data from email, network, and cloud systems, Trend Micro's broader platform can feel more complicated than necessary compared to CrowdStrike's endpoint-first approach.
 Choose Trend Micro If
Choose Trend Micro If
- You want broad XDR visibility across endpoint, email, network, and cloud in one platform.
- You value built-in cyber risk and exposure assessment, not just threat detection.
- You already use Trend Micro endpoint or cloud products and want to extend them with XDR.
 Choose CrowdStrike If
Choose CrowdStrike If
- You want best-in-class, endpoint-first protection with top detection accuracy.
- Endpoint performance and lightweight agents are a major concern.
- You prefer a simpler UI and focused EDR workflow, or use best-of-breed tools for email and network security.
Fortinet FortiEDR / FortiXDR
FortiEDR is Fortinet's advanced endpoint protection solution, with FortiXDR expanding its capabilities by correlating security telemetry across Fortinet's broader Security Fabric. FortiEDR focuses on real-time endpoint threat detection and automated response, with strong emphasis on pre-execution prevention and rapid containment of suspicious activity. Together, FortiEDR and FortiXDR position Fortinet as a direct competitor to CrowdStrike through a tightly integrated, platform-based security approach.
Where Fortinet FortiEDR stands out is its native integration with Fortinet's Security Fabric. Endpoint detections can be shared with FortiGate firewalls, FortiAnalyzer, and other Fortinet tools to enable coordinated response across the network. FortiEDR also supports on-premises deployment, making it suitable for organizations with strict data sovereignty, regulatory, or air-gapped requirements, an area where CrowdStrike's cloud-only model may not fit. For companies that prefer a network-centric, converged security architecture, Fortinet offers a compelling alternative that extends protection from the network edge to the endpoint.
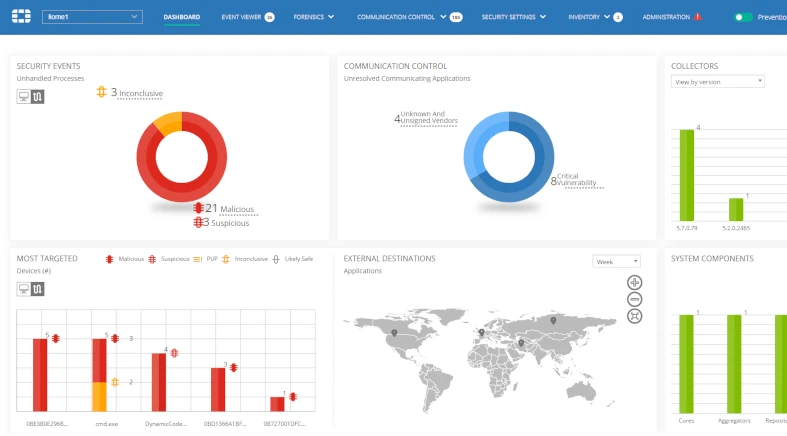
At enterprise scale, the differences between FortiEDR and CrowdStrike become more apparent. CrowdStrike generally leads in endpoint maturity, depth of analytics, and ecosystem breadth, and it is more widely adopted in large enterprises and high-security environments. Falcon's cloud-native design allows for faster deployment and easier global scaling, while FortiEDR, especially in on-prem setups, can require more infrastructure and ongoing maintenance. CrowdStrike also provides richer endpoint-focused capabilities, such as advanced threat hunting, detailed adversary intelligence, and a broader range of modular add-ons, whereas FortiEDR prioritizes prevention and cross-product integration over deep endpoint analytics.
 Choose Fortinet If
Choose Fortinet If
- You already use Fortinet firewalls or security products and want a unified Security Fabric.
- You need on-premises or air-gapped EDR for regulatory, government, or OT environments.
- You want lower total cost or simpler licensing, especially as an existing Fortinet customer.
 Choose CrowdStrike If
Choose CrowdStrike If
- You want best-in-class, endpoint-first detection and response with a long enterprise track record.
- You value cloud-native simplicity, fast global deployment, and minimal infrastructure to manage.
- You prefer a vendor-agnostic EDR platform that integrates easily into mixed security environments.
A practical 2025 guide for tech decision makers to choose the right network monitoring software based on scale, needs, and business goals. Learn more >>
Bitdefender GravityZone
Bitdefender GravityZone best known for its industry-leading anti-malware engine and broad endpoint protection capabilities. It offers layered security ranging from antivirus and device control to full EDR, XDR, risk analytics, patch management, and optional managed detection and response. With a long track record of top scores in independent malware tests and a massive global install base, Bitdefender competes directly with CrowdStrike by delivering strong prevention and detection capabilities at a more accessible price point.
Where Bitdefender GravityZone stands out is its cost efficiency and all-in-one design. It provides machine-learning malware detection, behavior monitoring, anti-exploit protection, sandboxing, EDR, and MDR features similar to CrowdStrike, but typically with simpler and lower-cost licensing. GravityZone also functions as a consolidated security suite, combining endpoint protection with device control, firewall management, patch management, and optional encryption in a single console. This makes Bitdefender especially appealing to organizations that want enterprise-grade protection without enterprise-level pricing.
Bitdefender has limitations when compared to CrowdStrike. CrowdStrike generally leads in advanced threat hunting, elite threat intelligence, and large-enterprise workflows. Falcon's managed hunting services, adversary intelligence, and incident response reputation are more established, particularly in high-stakes or highly regulated environments. CrowdStrike also offers deeper analyst tooling, including real-time remote response, extensive APIs, and strong integration with SOAR and zero-trust architectures. While Bitdefender is technically capable, CrowdStrike often carries greater market confidence and validation for organizations that prioritize best-of-breed security and brand assurance.
 Choose Bitdefender If
Choose Bitdefender If- You need strong endpoint protection at a lower cost, with simpler licensing.
- You want an all-in-one security platform (EDR plus firewall, patching, device control).
- You are a small or mid-sized business, MSP, or multi-tenant environment where CrowdStrike feels too expensive or complex.
 Choose CrowdStrike If
Choose CrowdStrike If
- You need elite threat hunting, advanced threat intelligence, and MDR services.
- You operate at large enterprise scale and require deep integrations, APIs, and analyst tooling.
- You want a best-of-breed, premium endpoint platform that signals top-tier security to customers or stakeholders.
Which CrowdStrike Competitor Is Right for Your Use Case?
Endpoint Security Buyer Cheat Sheet (Budget → Enterprise)
Choosing a CrowdStrike competitor isn't about finding a better product, it's about finding the right one for your environment. Different tools are built for different teams, budgets, and risk priorities.
The cheat sheet below maps common use cases to the tools that fit them best, from budget-conscious SMBs to security-first enterprises, so you can narrow down your options quickly.
How to Choose CrowdStrike Competitor in 10 Seconds
- Lowest cost, good protection: Bitdefender
- Protect sensitive documents and insider risk: AnySecura
- Already paying Microsoft: Defender for Endpoint
- Small team, easy ops: Sophos
- Match your firewall stack: Cisco / Fortinet / Palo Alto
- Need deep investigation: Carbon Black
- Want one big XDR view: Trend Micro Vision One
- Want the “gold standard”: CrowdStrike
FAQs about CrowdStrike Competitors
Who are CrowdStrike's biggest competitors?
CrowdStrike's biggest competitors include SentinelOne, Microsoft Defender for Endpoint, Palo Alto Cortex XDR, Sophos, Trend Micro, Cisco Secure Endpoint, and Tanium.
Is there a cheaper alternative to CrowdStrike?
Yes. Microsoft Defender for Endpoint, Sophos, and Trend Micro are often more affordable, especially for SMBs or Microsoft-centric organizations.
Conclusion
CrowdStrike is a strong security platform, but it's not the right fit for every organization. As this comparison shows, there are many CrowdStrike competitors, each designed to solve a different problem.
Some tools focus on stopping malware and endpoint attacks. Others are built for cloud posture, visibility, or large-scale device management. And some, like AnySecura, focus on a problem endpoint security doesn't fully solve: protecting sensitive documents and data from misuse.
There's no one-size-fits-all answer. The right decision starts with understanding your real security priorities, not just choosing the most well-known vendor.


