In day-to-day enterprise operations, email has long been one of the most critical channels for business communication.From internal management directives and IT access requests to contract confirmations and payment approvals,a large proportion of business activities rely on email exchanges. However, this high level of reliance and implicit trust has also created ideal conditions for a low-tech yet highly destructive attack technique that continues to surge worldwide—Business Email Compromise (BEC).
Unlike traditional cyberattacks, BEC does not disrupt systems or interfere with business operations. Instead, it disguises itself as legitimate business communication,quietly manipulating employees into executing high-risk actions.By the time funds are transferred or sensitive information is disclosed, organizations often realize the breach only after the damage has already been done.
What Is BEC?
Business Email Compromise (BEC) is a form of social engineering attack involving the forgery, impersonation, or hijacking of corporate email communications. Rather than relying on malware or technical exploits, attackers exploit human trust and established business workflows. Attackers typically impersonate high-trust roles such as executives, finance staff, suppliers, customers, or even legal counsel. They send seemingly legitimate business instructions that prompt employees to transfer funds, disclose sensitive information, or grant system access.
Unlike traditional phishing or malicious emails, BEC attacks usually exhibit the following characteristics:
- They contain no malicious links or attachments, evading detection by traditional security tools.
- The email content is highly tailored to genuine business scenarios, aligning with the company's daily operational norms.
- The messages appear entirely reasonable and often convey urgency, creating pressure to force employees into making quick decisions.
When these conditions are met, even experienced employees may unknowingly become part of the attack chain.
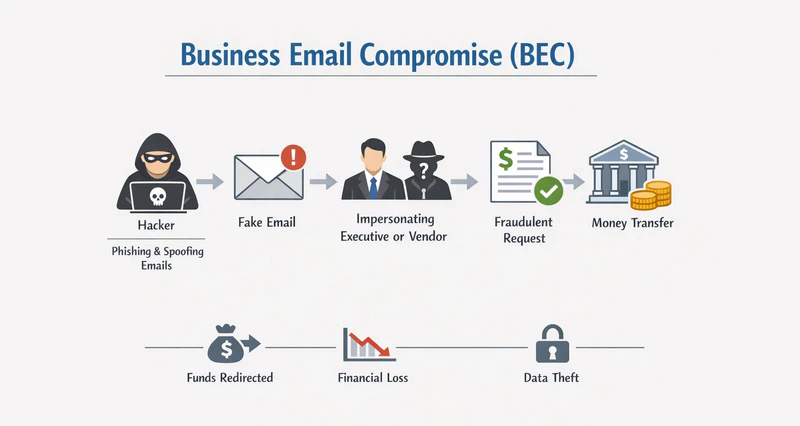
Common Types of BEC Attacks
Although tactics continue to evolve, BEC attacks consistently focus on high-value business targets—funds,access rights, and sensitive information. The following are the most common and successful BEC attack scenarios seen in enterprises today:
1. Executive Impersonation
Attackers impersonate high-level decision-makers such as the CEO, CFO, or General Manager and send emails to finance staff, demanding urgent execution of transfers or payments, often emphasizing confidentiality and time sensitivity. Due to the inherent authority of executive instructions and the pressure to act quickly, employees may execute the request without secondary verification, resulting in significant financial loss.
2. Supplier Email Account Compromise
In supplier hijacking attacks, attackers first gain unauthorized access to a legitimate supplier’s email account. They then monitor ongoing communications, payment schedules, and writing styles. At a critical payment stage, the attacker inserts fraudulent payment instructions. Because these emails originate from authentic accounts and maintain contextual consistency, employees are highly likely to misinterpret them as normal business correspondence, thereby falling into the trap.
3. Financial Instruction Manipulation
This is one of the most subtle and frequently overlooked forms of BEC. Instead of requesting an immediate transfer, attackers use emails to modify existing recipient account details, payment routes, or banking information. Common pretexts include:
- "The original account will be deactivated. Please update the information."
- "The supplier has switched to a new payment method. Please use the new details for subsequent payments."
- "Payment details have been adjusted due to audit or tax requirements."
Once the account information is successfully changed, subsequent payments are automatically redirected to attacker's account. Companies often only detect irregularities after multiple transfers have been processed.
4. HR and Payroll Fraud
These attacks target HR or finance teams by exploiting internal processes and employee data. Common tactics include:
- Impersonating employees to request payroll or reimbursement account changes
- Forging management instructions to urgently process employee data
- Targeting onboarding or offboarding periods
Beyond financial loss, such attacks may lead to personal data exposure,compliance violations, and internal trust issues.
5. Legal and Contract-Related Fraud
Attackers impersonate legal counsel or business partners and send emails involving contract amendments, supplemental agreements, or legal notices. These messages typically use formal, professional language and stress compliance deadlines or legal risks. Under time pressure, recipients may prioritize execution over verification, falling victim to the attack.
Real Risks and Impacts of BEC
The harm caused of BEC go far beyond a single “mistaken transfer.” Because these attacks directly targets core business processes, a successful incident can trigger cascading effects:
1. Financial Loss
The most immediate outcome of BEC is corporate financial loss. Once funds enter an account controlled by attackers, they are often split, transferred across multiple accounts, or even moved overseas within a very short period. By the time discrepancies are discovered during reconciliation or vendor follow-ups, recovery rates are extremely low, leaving the organization to bear the loss.
2. Reputational Damage
When BEC incidents involve suppliers, customers, or business partners, the impact extends beyond internal operations. Trust built over long-term cooperation can be undermined, forcing organizations to invest additional time and effort to rebuild trust, adversely affecting operational efficiency and the stability of collaborations.
3. Internal Trust Erosion
After an incident, employees may begin to question the reliability and security of management instructions, sometimes becoming overly cautious. This can erode the efficiency of internal collaboration and disrupt the overall functioning and decision-making pace of the organization.
4. Legal and Compliance Exposure
BEC incidents often expose weaknesses in internal controls, approval workflows, and risk management practices. In the aftermath, the organization may face audits, compliance inquiries, or even liability investigations. In such scenarios, even as the victim, the company could be held accountable for failing to implement adequate protective measures.
Common Misconceptions in BEC Prevention
Despite growing awareness, many organizations still fall into these common traps:
1. Relying Solely on Anti-Spam or Anti-Phishing Tools
Traditional email security tools focus on detecting malicious content. BEC attacks, however, leverage legitimate identities and compliant content, allowing them to bypass these defenses entirely.
2. Assuming Small Companies Are Not Targets
BEC is not limited to large enterprises. Small and mid-sized organizations are often easier targets due to simplified workflows, weaker verification processes, and limited security investment.
3. Overlooking Internal User Actions
Employees are rarely malicious actors, but they are often the critical execution point of BEC attacks. Without proper behavioral controls, auditing, and risk prompts, users may unknowingly carry out high-risk actions under abnormal conditions.
Ultimately, the core challenge of BEC prevention lies not in tool deployment alone, but in whether organizations treat business processes and human actions as part of their security perimeter.

Worried your staff might be moonlighting? This 2026 guide explains how to detect, confirm moonlighting with smart tools. Learn more>>
How to Effectively Prevent BEC Attacks
There is no single solution for BEC. Because these attacks exploit trust and workflow exceptions, effective prevention requires coordination across people, processes, and technology.
1. Strengthen Employee Security Awareness
The focus of security awareness training for employees is not merely to "remind them that risks exist", but to help them understand when to pause and verify. Companies can strengthen the following areas in particular:
- Define which urgent requests must always be verified through secondary channels
- Educate staff on common BEC tactics and psychological pressure techniques
- Provide targeted training for finance, HR, legal, and executive teams
When verification is encouraged and supported, employees are far less likely to act impulsively.
2. Enforce Verification Processes
BEC attacks succeed by exploiting “exceptions” and “urgent overrides”. Organizations should reinforce controls at high-risk stages:
- Require multi-channel verification for payments, account changes, and payment routing updates
- Introduce delay or escalation mechanisms for anomalous transactions
- Assess risk for “urgent” requests instead of bypassing established workflows
Well-designed verification processes significantly reduce the likelihood of fraudulent execution.
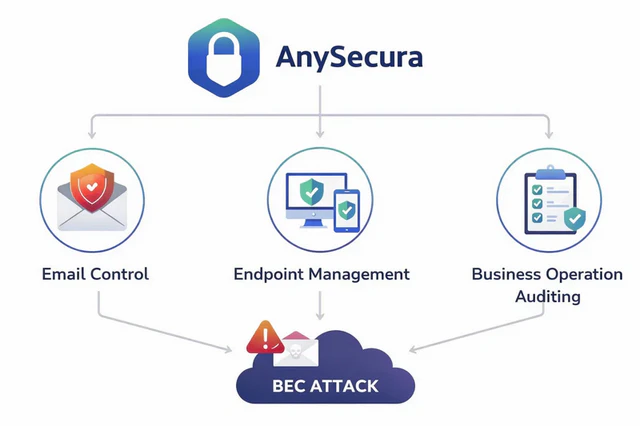
3. Apply Layered Technical Controls
In BEC defense, technology should extend beyond email detection to continuous monitoring of risky behavior. AnySecura integrates email control, endpoint management, and business operation auditing to provide end-to-end protection:
- Email outbound control: Restrict sending privileges for high-risk roles, define recipient scopes, standardize attachment rules, and enforce mandatory CC policies. Emails containing sensitive financial or business data can be intercepted in real time to prevent exposure.
- Sensitive operation auditing and traceability: Record file access, data transfers, and critical actions, ensuring high-risk operations are auditable and traceable for investigation and accountability.
- Risk alerts for critical actions: Automatically trigger warning prompts during abnormal or high-risk actions—such as external email sending or sensitive data transmission—giving teams time to intervene.
Related article: Stop Data Leaks at Every Endpoint: Control Transfers, Track Every Move
Conclusion
Business Email Compromise is not merely a technical issue—it is the result of long-standing tensions between trust, efficiency, and security. As digital collaboration and remote work continue to expand, BEC prevention is no longer a question of whether organizations should act, but how systematically and sustainably they do so.
Only by embedding security controls directly into business workflows—and aligning people, processes, and technology—can organizations effectively mitigate this covert yet high-impact threat.


