- Chapter 1: Introduction
- Chapter 2: Installation and Deployment
- Chapter 3: Console
- Chapter 4: Statistics
- Chapter 5: Logs
- Chapter 6: Policies
- Chapter 7: Monitoring
- Chapter 8: Remote Maintenance
- Chapter 9: Security Monitoring
- Chapter 10: Sensitive Information
- Chapter 11: Visual Perception
- Chapter 12: Watermarks
- Chapter 13: Asset Management
- Chapter 14: Category Management
- Chapter 15: Request Management
- Chapter 16: Network Access Detection
- Chapter 17: Data Backup
-
Chapter 18: Tools
- 18.1 Account Management
- 18.2 Computer Management
- 18.3 USB Encryption Client Management
- 18.4 Alert Messages
- 18.5 Mail Report Settings
- 18.6 Policy Application Query
- 18.7 Client Tools
- 18.8 Server Time
- 18.9 Relay Server Management
- 18.10 Policy and Library Synchronization Management
- 18.11 Organizational Structure Synchronization
- 18.12 Client Upgrade Management
- 18.13 Options
- Chapter 19: User System Management
- Chapter 20: Audit Console
- Chapter 21: Document Security Management
- Chapter 22: Windows Encrypted Client
- Chapter 23: Linux Encrypted Client
- Chapter 24: Mac Encrypted Client
- Chapter 25: USB Encrypted Client
- Chapter 26: External Viewer
- Chapter 27: Backup Encryption Server
- Chapter 28: Document Storage Request
- Chapter 29: Cloud Document Backup Server
- Chapter 30: Reporting System
- Chapter 31: WEB Console
- Chapter 32: WEB Approval
- Chapter 33: WEB Reports
- Chapter 34: Software Center
- [email protected]
- 15 Scotts Road, #03-12, Singapore
18.1 Account Management
The system administrator has the highest level of privileges and can access all system functions. By creating additional administrator accounts, the system administrator can delegate certain management tasks to other administrators.
Select Tools → Accounts to view administrator information. Here, administrators can add or delete accounts, enable or disable accounts, and change administrator passwords. When creating a new administrator account, clicking Save allows you to continue adding passwords and accounts directly on the Accounts page.
| Icon / Button | Action |
|---|---|
| Add an administrator account and optionally enter a description. | |
| Delete an administrator account. The system administrator Admin cannot be deleted. | |
| Change the login password for an administrator account. The default password is blank. | |
| Expand additional function options. | |
| Enable | Enable a disabled administrator account. |
| Disable | Disable an administrator account. The system administrator Admin cannot be disabled. |
| Move to | Moving administrators can be done in three ways:
|
| Importing Accounts | Using a CSV file exported via the Export Account Permissions feature, administrators can import accounts. The import only updates the administrator name, email, and notes; other permissions remain unchanged.
|
| Copy Permissions To | Select an administrator A and copy their permissions to another administrator B. Administrator B will retain their original permissions while gaining all of administrator A's permissions. |
| Export Account Permissions | Export the permissions of all current administrators for review. In the exported file, a checked permission is marked with "√", and an unchecked permission is marked with "×". The export also includes notes and email information. |
Note:
- Notes on "Copy Permissions To":
- 1. System administrator permissions cannot be copied to a non-system administrator who already has sub-administrators, nor to any sub-administrator.
- 2. To copy permissions from a non-system administrator A to a sub-administrator (whose parent is B), there are two scenarios:
- If A's permissions are within B's permission scope, A must have no sub-administrators for the copy to succeed. If A has sub-administrators, the copy will fail.
- If A's permissions exceed B's permission scope, the copy will fail.
18.1.1 Administrator Password Security Verification
Administrator password security verification enforces password complexity and limits on incorrect attempts to enhance protection against malicious password-cracking attempts. By default, this feature is disabled. The system administrator can enable and configure it by clicking Administrator Password Security Verification in the lower-left corner of the Account Management interface.
| Setting | Description |
|---|---|
| Enable Administrator Password Security Verification | Check this option to activate password security verification; the settings below will take effect only when enabled. |
| Password Complexity | Configure rules for administrator password complexity. |
| Password Cannot Be Empty | When checked, administrators with empty passwords will be required to set a non-empty password; otherwise, they cannot log in. |
| Minimum Password Length | When checked, set the minimum password length. Administrators whose passwords are shorter than this length will be forced to update their password to meet the requirement; otherwise, they cannot log in. |
| Password Complexity Verification | Check this option to enforce password complexity. If an administrator's password does not meet the complexity requirements when logging in, they will be forced to change it; otherwise, the account cannot access the console.Click the icon |
| Incorrect Password Attempts Verification | This setting defines rules for handling the number of incorrect administrator password attempts. |
| Enable Incorrect Password Attempts Verification | Check this option and configure the time window, maximum allowed incorrect attempts, and account lock duration. If an administrator exceeds the specified number of incorrect password attempts within the set time, the account will be locked. During the lock period, the account cannot log in—even with the correct password. |
| Timeout Lock | Settings related to automatically locking the administrator console after a period of inactivity. |
| Lock Console After Inactivity | Check this option and set the idle time limit. Once the console remains idle for the specified duration, it will automatically lock, requiring the administrator password to log back in.This setting also applies when an administrator logs into a proxy console. The console’s timeout lock takes precedence over the proxy console lock settings. |
| Periodic Password Change | Settings for enforcing a maximum usage period for administrator passwords. |
| Maximum Password Age (Days) | Check this option and set the maximum number of days a password can be used, defaulting to 30 days. Starting from the configuration date, once the password reaches the specified duration, the administrator must change it. |
| Password Expiration Reminder (Days) | Check this option and set the reminder period in days, defaulting to 3 days. Once the remaining password validity reaches this period, a reminder will appear daily at 10:00.The reminder period cannot exceed the maximum password age. |
When an administrator account is locked after exceeding the allowed number of incorrect password attempts, an audit log is generated and can be viewed in the Audit Console.
Note:
- 1. The Administrator Password Security Verification settings apply to all administrator accounts.
- 2. To prevent malicious lockouts of the Admin or Audit accounts, their login attempts on the server machine are not limited.
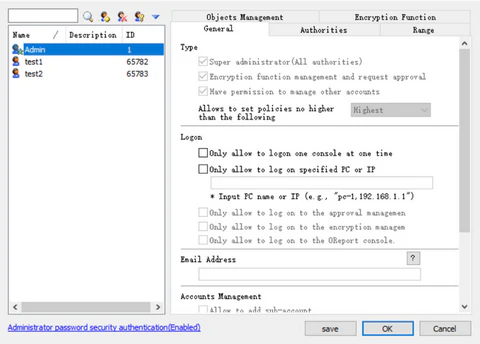
18.1.2 Administrator Permissions
Administrator permissions are divided into four main modules: General, Functional Permissions, Management Scope & Object Management, and Encryption Features.
| Module | Description |
|---|---|
| General | Specifies the administrator type and login mode. |
| Functional Permissions | Defines the administrator's functional privileges, such as managing client logs, setting various policies, performing remote client maintenance, and patch management. |
| Management Scope | Determines the scope of management for non-system administrators. They can manage all computers and users, or select specific computers and users. |
| Object Management | Specifies the range of removable storage groups that non-system administrators can view. |
| Encryption Features | Grants non-system administrator accounts permissions for encryption functions, including management rights and secure areas. |
General Permissions:
| Permission | Description |
|---|---|
| Type | |
| System Administrator | Only system administrators can view and manage authorized software and secure areas. System administrator icons display a five-pointed star; non-system administrators’ icons do not. |
| Encryption Management & Approval | Grants the ability to manage the encryption system, including approving encryption requests. |
| Can Manage Other Accounts | Allows creating and modifying permissions for other non-system administrators (modified permissions can exceed the administrator’s own), but cannot change their own permissions. |
| Allowed Policy Level | Specifies the maximum policy level the administrator can set, including Normal, Priority, and Highest. System administrators have full access by default; other administrators default to Normal level, which can be adjusted here. |
| Login | |
| Single Console Login Only | Prevents simultaneous logins to multiple consoles. |
| Login Only on Specified | Restricts login to designated computer names or IP addresses. |
| Proxy-Only Login | Allows login only as a proxy administrator on the encryption client; console login is not permitted. |
| Login to Encryption Management Only | Allows login from the console directly to the encryption management system interface, without access to other AnySecura console functions. |
| Account Management | |
| Allow Creating Sub-Accounts | Checking this option grants the administrator permission to create sub-administrators. Administrators with this permission can go to Tools → Accounts in the console to create sub-administrators, whose permissions cannot exceed those of the parent administrator. Only regular administrators can create sub-administrators; system administrators, as well as the Admin and Audit accounts, cannot enable this option. |
Note:
- The "Allow Creating Sub-Accounts" option is available only for non-system administrators. System administrators, as well as the Admin and Audit accounts, cannot enable this option.
Administrator Functional Permissions
| Function Permissions | Description |
|---|---|
| Files | Grants permissions for operations on the computer and user trees, such as creating groups, moving, renaming, deleting, as well as exporting data and printing. |
| Control | Grants permissions to control clients, including lock/unlock, sending notifications, logging off computer accounts, startup/shutdown, remote wake-up, and client uninstallation. |
| Statistics | Grants permissions to query statistical records, including application statistics, web browsing statistics, and network traffic statistics. |
| Logs | Grants permissions to query log records, including basic logs, application logs, web browsing logs, document operation logs, shared document logs, document printing logs, asset change logs, policy logs, system logs, backup document logs, and removable storage logs. |
| Policies | Primarily manages permissions for querying and modifying policies, including: viewing and configuring basic policies, application policies, web browsing controls, device controls, print controls, screen recording, log management, remote control, traffic management, network controls, email controls, instant messaging file controls, upload controls, document controls, system alerts, removable media authorization, custom configurations, software installation management, and cloud document backup policies. |
| Monitoring | Grants permission to query and export records such as screen activity, emails, and instant messages,including viewing live screens, checking email and instant messaging logs, reviewing screen history, and exporting screen history. |
| Maintenance | Primarily refers to permissions for maintaining remote computers,including viewing and managing remote information, performing remote control, and transferring files remotely. |
| IT Asset Management | Primarily refers to permissions for managing assets, including viewing asset information, configuring asset categories and attributes, and editing custom categories and attributes. |
| Patch Management | Primarily refers to permissions for managing system patches, including viewing patch information, configuring patch settings, and installing patches. |
| Vulnerability Management | Primarily refers to permissions for managing system vulnerabilities, including reviewing vulnerability scan results and configuring scan settings. |
| Software Distribution | There are two parts: permissions for managing distribution packages, including viewing and configuring packages; and permissions for managing distribution tasks, including checking task status and installation results, setting up tasks, and executing them. |
| Software Uninstallation Management | Primarily refers to permissions for managing software uninstallation, including viewing and configuring uninstallation tasks. |
| Network Access Control | Primarily refers to permissions for network access control, including viewing access status, configuring access settings, and managing related policies. |
| All Category Management | Primarily refers to permissions for managing various categories, including application categories, website categories, time categories, network address categories, network port categories, removable storage, software distribution package library, software uninstallation library, email categories, watermark template library, and sensitive information library.
|
| Desktop Security Management | Primarily refers to permissions for managing desktop security functions, including viewing standard and approval requests, deleting requests, rejecting approvals, delegating approval permissions, viewing and configuring standard module approval workflows, and viewing and setting request permissions. |
| Deletion | primarily refers to permissions specifying which records can be deleted, including statistics, logs, emails, and instant messages. |
| Data Backup | Primarily refers to permissions for backing up and viewing data, including backing up logs and accessing data. |
| Parameter Settings | Primarily for configuring the server and mail report server, including server settings and mail report server settings. |
| Security Check | Primarily controls access to security check functions, including security check conditions, settings, logs, and status. |
| Relay Server Management | Primarily manages permissions for relay server functions, including viewing and configuring relay servers. |
| Roles | Primarily manages permissions for policy roles, including viewing, configuring, and assigning roles. |
| Document Cloud Backup Server | Primarily manages permissions for document cloud backup functions, including managing document permissions, configuring settings, viewing scan tasks and logs, and scheduling scan tasks. |
| Sensitive Information | Permissions for querying and modifying policies and logs.Includes: Granting/revoking sensitive content identification permissions, viewing full-disk scan tasks and logs for sensitive information, configuring full-disk scan tasks for sensitive information, viewing/setting outbound control policies for sensitive information, viewing/setting sensitive information landing control policies for sensitive information, and viewing/deleting logs related to sensitive information. |
| Watermark | Permissions to configure and view screen, print, and document watermarking features.Includes: Viewing/setting screen watermark policies, viewing/setting print watermark policies, viewing/setting document watermark policies, viewing/setting traceability policies for document circulation, viewing/setting document watermark permissions, viewing/deleting document watermark logs, viewing/deleting document circulation logs, querying watermark codes, using the document watermark extraction tool, viewing document numbering scan tasks and logs, and configuring document numbering scan tasks. |
| AI Visual Perception | ermissions related to visual awareness features.Includes: Authorizing/revoking visual awareness access, viewing/configuring visual awareness settings, viewing capture logs, deleting capture logs, reviewing capture history, and exporting capture history. |
| Application Permissions | Permissions for the desktop request feature.Includes: Viewing/setting request approval permissions, viewing/setting self-filing permissions, and viewing/deleting self-filing logs. |
| Server Management | Permissions for configuring server-related functions.Includes: Managing domain organizational structures, administering distributed servers, performing remote server checks, and managing email reports. |
| Client Management | Permissions for managing client operations.
|
| Access Gateway | Permissions related to connecting the AnySecura server to the access control server.Includes: Viewing access control devices and configuring access control devices. |
| Reporting System | Permissions to access the reporting system. |
| Auxiliary Functions | Permissions to use auxiliary tools.Includes: Generating client confirmation codes, creating client offline assistant tools, and generating client offline data collection tools. |
| Product Upgrade | Permissions for product maintenance and upgrade management, including updating maintenance codes, checking and downloading new versions, and receiving maintenance service expiration reminders. |
| Software Center Server | Permissions to access the Software Center Server. |
Object Management:
| Management Permission | Description |
|---|---|
| Removable Media Library | Permissions to manage the removable media library. During permission assignment, only the "Registered" group is available for selection.Administrators can only manage removable media classifications within their own object scope. Administrators with full management permissions for the entire removable media library will also have permissions for the "Uncategorized" group. |
Encryption Features:
| Management Permission | Description |
|---|---|
| Document Encryption & Sharing | Permissions for document encryption, decryption, and external sharing.Includes: Enabling/disabling encryption, remote management of encrypted documents, encrypting/decrypting documents, external document sharing, and configuring document encryption algorithms. |
| Authorized Software | Permissions to manage the authorized software library. |
| Security Zones | Permissions to add, modify, and delete security zones. |
| External Sharing Objects | Permissions to configure external sharing objects and authorized external computers. |
| Permission Settings | Permissions to configure encryption policies on clients.Includes: Viewing encryption permissions, setting encryption permissions, managing encryption system login/logout, viewing encryption parameters, configuring encryption parameters, viewing document backup policies, setting document backup policies, viewing long-term offline authorization, and setting long-term offline authorization. |
| Encrypted Document Operation Logs | Permissions to manage operation logs for encrypted documents.Includes: Viewing encrypted document operation logs, viewing backed-up encrypted documents, and deleting encrypted document operation logs. |
| Task Management | Permissions to operate the full-disk scan feature.Includes: Viewing full-disk scan tasks and logs, configuring encryption tasks, and configuring decryption tasks. |
| Workflow Management | Permissions for managing various types of requests.
|
| Standby Server | Permissions to manage the standby server.Includes: Viewing standby server details and configuring standby server settings. |
| Document Backup Server | Permissions to manage the document backup server.Includes: Viewing document backup server details and configuring document backup server settings. |
| USB Key Management | Permissions to manage USB Key functionality.Includes: Adding/removing USB Key information, modifying USB Key information, viewing USB Key logs, and deleting USB Key logs. |
| Smart Device Management | Permissions to use smart device management features.Includes: Viewing smart devices, modifying smart device settings, and authorizing smart devices. |
Security Zones
| Security Zones | Description |
|---|---|
| All Zones & All Levels | Allows management of documents across all security zones and all classification levels. |
| All Zones, Specified Level | Allows management of documents in all security zones, but only those at or below a specified classification level.There are five security levels: Non-sensitive, Internal, Confidential, Secret, and Top Secret. Example: If the specified level is "Secret", the administrator can manage documents classified as Non-sensitive, Internal, Confidential, and Secret. |
| Specified Zones & Levels | Allows management of documents only within specified security zones and at or below their corresponding classification levels. |
Administrators should assign security permissions based on actual needs and avoid granting unnecessary privileges.
Note:
- When configuring policies or creating new workflows through the console, administrators are not restricted by their own security zone or clearance level assignments.
